Basics on Cyber Threat Intelligence Collection and Information Sharing
•
0 likes•152 views
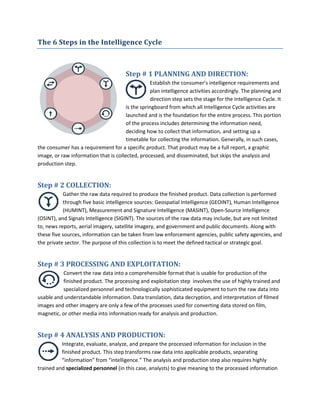
The 6 steps in the intelligence cycle are: 1. Planning and direction which establishes requirements and plans activities. 2. Collection of raw data from sources like HUMINT, SIGINT, and open sources. 3. Processing and exploitation which converts raw data into a usable format. 4. Analysis and production which evaluates information to create actionable intelligence products. 5. Dissemination which delivers finished products to customers. 6. Evaluation which acquires feedback to refine each step and the cycle as a whole.
Report
Share
Report
Share
Recommended
Social Media Monitoring tools as an OSINT platform for intelligence

This whitepaper discusses how social media monitoring tools can be applied as powerful and cost effective Open Source Intelligence (OSINT) platforms; and how they can support collection and analysis of relevant and targeted information relating to counter-terrorism, criminal and political open sources.
Analysis and ProductionInformation collected in the previous ste.docx

Analysis and Production
Information collected in the previous steps will be analyzed, validated, and fused into intelligence in the analysis process to be included into finished intelligence products. Analysis is defined by the ODNI as “The process by which information is transformed into intelligence; a systematic examination of information to identify significant facts, make judgments, and draw conclusions.” (ODNI, 2013) This transformation occurs when All-Source Analysts use all the Single Source INTs to create a fused intelligence product.
Single Source INT
We learned about “Single Source INTs” in Module three and they are HUMINT, SIGINT, GEOINT, OSINT, and MASINT. They are referred to as single source because they are derived from a single type of INT. You may hear of a single source SIGINT analyst, who is an expert in signals intelligence collection, or a single source IMINT analyst, who is an expert in imagery intelligence collection.
All-Source INT
The All-Source Analyst is not an expert in collection of the single sources, but is instead an expert in a region or intelligence function (terrorism, counter-drug, crime, etc.) that is the consumer of the raw single source information from all INTs. Analysts receive incoming information, evaluate it, test it against other information and against their personal knowledge and expertise, produce an assessment of the current status of a particular area under analysis, and then forecast future trends or outcomes. The analyst also develops requirements for the collection of new information. (ODNI, 2013) The All-Source Analyst will learn through experience to validate information using multiple INTs to confirm information collected through a single source INT. For example, if information is collected from a HUMINT source, the All-Source Analyst will look for another HUMINT source to collaborate that information or possibly validate the original HUMINT source through SIGINT sources.
Validation
Validation is important to also counter an adversary’s attempts to conduct deception; however, the well-organized adversary will release multiple pieces of information through various INTs to mislead All-Source Analysts. A good adversarial deception plan will not only allow deceptive pieces of information to be collected to attempt to fool our intelligence analysts, but will also play into an analyst’s bias. The common biases of an analyst are mirror imaging (thinking the adversary will act the same way Americans do), cry-wolf syndrome (conducting an action multiple times so that when the adversary truly intends to act, our analysts do not take it seriously), and mission-creep/new normal (an adversary slowly changes tactics so that our analysts do not suspect nefarious activities).
It is important for All-Source Analysts to be confident in their assessments,
but they should be wary of overconfidence
Many think that the job of an intelligence analyst is to predict the future. In fact, many early analytic.
Intelligence cycle

The intelligence cycle is a set of processes used to provide useful information for decision-making. The cycle consists of several processes. The related counter-intelligence area is tasked with preventing information efforts from others. A basic model of the process of collecting and analyzing information is called the "intelligence cycle". This model can be applied, and, like all the basic models, it does not reflect the fullness of real-world operations. Through intelligence cycle activities, information is collected and assembled, raw information is transformed into processed information, analyzed and made available to users.
DOI: 10.13140/RG.2.2.25665.81760
Mapping the Enterprise Threat, Risk, and Security Control Landscape with Splunk

As threats evolve, it is essential to move beyond looking at events toward developing behavioral analysis capabilities. Knowing not only the components but also the rhythms of your environment becomes crucial to enable earlier detection of attackers. This session will review the threat and risk landscape today, recommend approaches to bolster your security control monitoring, apply situational awareness and kill chain techniques, and walk through the construction of two specific use cases. They are 1) detecting compromised accounts via remote access behavior analysis and 2) detecting malicious activity (attacker or insider) by detecting and tracing network jumpers from corporate to guest networks. The session will discuss the design approach and searches used in these two use cases so that you can build other use cases to improve your security capability and posture.
Risks, Harms and Benefits Assessment Tool (Updated as of Jan 2019)

The Data Innovation Risk Assessment Tool is an initial assessment of potential risks for data use that includes seven guiding checkpoints to understand: the "Data Type" involved in the data analytics process, the "Risks and Harms" of data use, the mode and legitimacy of "Data Access", the "Data Use", the adequacy of "Data Security", the adequate level of "Communication and Transparency" and the due diligence on engagement of "Third Parties". The Assessment contains guiding comments for each checkpoint and its questions are grounded in the key international data privacy and data protection principles and concepts such as Purpose Specification, Purpose Compatibility, Data Minimization, Consent Legitimacy, Lawfulness and Fairness of data access and use.
Recommended
Social Media Monitoring tools as an OSINT platform for intelligence

This whitepaper discusses how social media monitoring tools can be applied as powerful and cost effective Open Source Intelligence (OSINT) platforms; and how they can support collection and analysis of relevant and targeted information relating to counter-terrorism, criminal and political open sources.
Analysis and ProductionInformation collected in the previous ste.docx

Analysis and Production
Information collected in the previous steps will be analyzed, validated, and fused into intelligence in the analysis process to be included into finished intelligence products. Analysis is defined by the ODNI as “The process by which information is transformed into intelligence; a systematic examination of information to identify significant facts, make judgments, and draw conclusions.” (ODNI, 2013) This transformation occurs when All-Source Analysts use all the Single Source INTs to create a fused intelligence product.
Single Source INT
We learned about “Single Source INTs” in Module three and they are HUMINT, SIGINT, GEOINT, OSINT, and MASINT. They are referred to as single source because they are derived from a single type of INT. You may hear of a single source SIGINT analyst, who is an expert in signals intelligence collection, or a single source IMINT analyst, who is an expert in imagery intelligence collection.
All-Source INT
The All-Source Analyst is not an expert in collection of the single sources, but is instead an expert in a region or intelligence function (terrorism, counter-drug, crime, etc.) that is the consumer of the raw single source information from all INTs. Analysts receive incoming information, evaluate it, test it against other information and against their personal knowledge and expertise, produce an assessment of the current status of a particular area under analysis, and then forecast future trends or outcomes. The analyst also develops requirements for the collection of new information. (ODNI, 2013) The All-Source Analyst will learn through experience to validate information using multiple INTs to confirm information collected through a single source INT. For example, if information is collected from a HUMINT source, the All-Source Analyst will look for another HUMINT source to collaborate that information or possibly validate the original HUMINT source through SIGINT sources.
Validation
Validation is important to also counter an adversary’s attempts to conduct deception; however, the well-organized adversary will release multiple pieces of information through various INTs to mislead All-Source Analysts. A good adversarial deception plan will not only allow deceptive pieces of information to be collected to attempt to fool our intelligence analysts, but will also play into an analyst’s bias. The common biases of an analyst are mirror imaging (thinking the adversary will act the same way Americans do), cry-wolf syndrome (conducting an action multiple times so that when the adversary truly intends to act, our analysts do not take it seriously), and mission-creep/new normal (an adversary slowly changes tactics so that our analysts do not suspect nefarious activities).
It is important for All-Source Analysts to be confident in their assessments,
but they should be wary of overconfidence
Many think that the job of an intelligence analyst is to predict the future. In fact, many early analytic.
Intelligence cycle

The intelligence cycle is a set of processes used to provide useful information for decision-making. The cycle consists of several processes. The related counter-intelligence area is tasked with preventing information efforts from others. A basic model of the process of collecting and analyzing information is called the "intelligence cycle". This model can be applied, and, like all the basic models, it does not reflect the fullness of real-world operations. Through intelligence cycle activities, information is collected and assembled, raw information is transformed into processed information, analyzed and made available to users.
DOI: 10.13140/RG.2.2.25665.81760
Mapping the Enterprise Threat, Risk, and Security Control Landscape with Splunk

As threats evolve, it is essential to move beyond looking at events toward developing behavioral analysis capabilities. Knowing not only the components but also the rhythms of your environment becomes crucial to enable earlier detection of attackers. This session will review the threat and risk landscape today, recommend approaches to bolster your security control monitoring, apply situational awareness and kill chain techniques, and walk through the construction of two specific use cases. They are 1) detecting compromised accounts via remote access behavior analysis and 2) detecting malicious activity (attacker or insider) by detecting and tracing network jumpers from corporate to guest networks. The session will discuss the design approach and searches used in these two use cases so that you can build other use cases to improve your security capability and posture.
Risks, Harms and Benefits Assessment Tool (Updated as of Jan 2019)

The Data Innovation Risk Assessment Tool is an initial assessment of potential risks for data use that includes seven guiding checkpoints to understand: the "Data Type" involved in the data analytics process, the "Risks and Harms" of data use, the mode and legitimacy of "Data Access", the "Data Use", the adequacy of "Data Security", the adequate level of "Communication and Transparency" and the due diligence on engagement of "Third Parties". The Assessment contains guiding comments for each checkpoint and its questions are grounded in the key international data privacy and data protection principles and concepts such as Purpose Specification, Purpose Compatibility, Data Minimization, Consent Legitimacy, Lawfulness and Fairness of data access and use.
Data Analytics in Industry Verticals, Data Analytics Lifecycle, Challenges of...

Banking and securities
Challenges
Early warning for securities fraud and trade visibilities
Card fraud detection and audit trails
Enterprise credit risk reporting
Customer data transformation and analytics.
The Security Exchange commission (SEC) is using big data to monitor financial market activity by using network analytics and natural language processing. This helps to catch illegal trading activity in the financial markets.
The Data Analytics Lifecycle is designed specifically for Big Data problems and data science projects. The lifecycle has six phases, and project work can occur in several phases at once. For most phases in the lifecycle, the movement can be either forward or backward. This iterative depiction of the lifecycle is intended to more closely portray a real project, in which aspects of the project move forward and may return to earlier stages as new information is uncovered and team members learn more about various stages of the project. This enables participants to move iteratively through the process and drive toward operationalizing the project work.
Phase 1—Discovery: In Phase 1, the team learns the business domain, including relevant history such as whether the organization or business unit has attempted similar projects in the past from which they can learn. The team assesses the resources available to support the project in terms of people, technology, time, and data. Important activities in this phase include framing the business problem as an analytics challenge that can be addressed in subsequent phases and formulating initial hypotheses (IHs) to test and begin learning the data.
Phase 2—Data preparation: Phase 2 requires the presence of an analytic sandbox, in which the team can work with data and perform analytics for the duration of the project. The team needs to execute extract, load, and transform (ELT) or extract, transform and load (ETL) to get data into the sandbox. The ELT and ETL are sometimes abbreviated as ETLT. Data should be transformed in the ETLT process so the team can work with it and analyze it. In this phase, the team also needs to familiarize itself with the data thoroughly and take steps to condition the data.
Data analysis step by step guide

This ebook is all about data analysis, what are the steps involved in data analysis and what are the techniques. We will bring out a detailed course very soon. pls register https://excelfinanceacademy.zenler.com/ to save over 80% cost
DATA PROTECTION IMPACT ASSESSMENT TEMPLATE (ODPC).docx

The data protection impact assessment for a cloud based project aims to provide financial inclusion for the unbanked population through its three modules, i.e., wallet, social banking and marketplace/business hub. The primary goal is to enable individuals without access to traditional banking services to engage in financial transactions.
The processing involves the collection, storage, and utilization of personal data for various purposes, such as creating digital wallets, facilitating social banking interactions, and delivering targeted marketing content. The platform will manage user information to enable secure and seamless financial transactions.
The targeted data subjects are individuals and entities within the unbanked population who lack access to traditional financial services. These individuals include low-income earners, marginalized communities and those residing in areas with limited banking infrastructure.
The primary class of data subjects includes the unbanked population seeking financial inclusion. Within this group, there may be subcategories, such as individuals with limited financial literacy or those residing in remote areas, and any vulnerable groups, such as elderly users or minors, who are part of the targeted data subjects.
Big data analytics for life insurers

Big data analytics for life insurers- a whitepaper from Capgemini global insurance Centre of excellence
Smartphones in Healthcare

Any meaningful analysis of data depends entirely on the quality of data that is captured. And the method to capture data, which is still quite common in fieldwork, is the paper form.
Even where technology is deployed, the process is brought with vulnerabilities making the data either stale or inaccurate. Mobile viz, using smart devices to replace incumbent methods promises to solve all problems in a single shot.
Ideafarms's Heathwatch is a prototype solution that shows the power of this idea in the area of Disease Surveillance and Proactive Management of Epidemics.
Password Management Market - Outlook (2017-21) for APAC

Increased competition among businesses has forced businesses to become more customer friendly and as a part of this, businesses have started using multiple applications to address customer issues. In order to handle multiple applications, employees of these organizations require managing more passwords and usernames. Beyond one point, managing of these passwords becomes a complex task and time consuming thereby employees losing their productivity. This in-turn will lead to monetary losses to the organizations. In order to make sure that the employees concentrate on their core activities and do not spend much of their time managing passwords, businesses implement solutions like password management which ensures that the passwords are safe and at the same time do not cost a bomb to the companies. This report presents interpretative and easy-to-understand facts on how the current password management market is segmented based on end-user, verticals, deployment type and geographies. It cuts through several facets of the password management market such as market size, market share for each segment, the drivers and constraints of password management marketplace. It also throws light on various verticals where password management is being rigorously implemented and the deployment type that is being preferred. Report also provides information on the challenges and opportunities that lie ahead for these solutions.
Proceedings on Privacy Enhancing Technologies ; 2016 (3)96–11

Proceedings on Privacy Enhancing Technologies ; 2016 (3):96–116
Chad Spensky, Jeffrey Stewart, Arkady Yerukhimovich, Richard Shay, Ari Trachtenberg, Rick
Housley, and Robert K. Cunningham
SoK: Privacy on Mobile Devices – It’s Complicated
Abstract: Modern mobile devices place a wide variety
of sensors and services within the personal space of their
users. As a result, these devices are capable of transpar-
ently monitoring many sensitive aspects of these users’
lives (e.g., location, health, or correspondences). Users
typically trade access to this data for convenient appli-
cations and features, in many cases without a full appre-
ciation of the nature and extent of the information that
they are exposing to a variety of third parties. Never-
theless, studies show that users remain concerned about
their privacy and vendors have similarly been increas-
ing their utilization of privacy-preserving technologies
in these devices. Still, despite significant efforts, these
technologies continue to fail in fundamental ways, leav-
ing users’ private data exposed.
In this work, we survey the numerous components of
mobile devices, giving particular attention to those that
collect, process, or protect users’ private data. Whereas
the individual components have been generally well
studied and understood, examining the entire mobile de-
vice ecosystem provides significant insights into its over-
whelming complexity. The numerous components of this
complex ecosystem are frequently built and controlled
by different parties with varying interests and incen-
tives. Moreover, most of these parties are unknown to
the typical user. The technologies that are employed to
protect the users’ privacy typically only do so within
a small slice of this ecosystem, abstracting away the
greater complexity of the system. Our analysis suggests
that this abstracted complexity is the major cause of
many privacy-related vulnerabilities, and that a funda-
mentally new, holistic, approach to privacy is needed
going forward. We thus highlight various existing tech-
nology gaps and propose several promising research di-
rections for addressing and reducing this complexity.
Keywords: privacy-preserving technologies, mobile, An-
droid, iOS
DOI 10.1515/popets-2016-0018
Received 2015-11-30; revised 2016-03-01; accepted 2016-03-02.
Chad Spensky: University of California, Santa Barbara,
[email protected]
Jeffrey Stewart: MIT Lincoln Laboratory,
[email protected]
1 Introduction
The rapid proliferation of mobile devices has seen them
become integral parts of many users’ lives. Indeed, these
devices provide their users with a variety of increasingly
essential services (e.g., navigation, communication, and
Internet connectivity), as well as useful functionality
(e.g., entertainment and photography). To accommo-
date these services, modern mobile devices are equipped
with various sensors, capable of collecting extremely rich
information about their users and their surroundings.
Users and de ...
Password Management Market - Outlook (2017-21) for Europe

Increased competition among businesses has forced businesses to become more customer friendly and as a part of this, businesses have started using multiple applications to address customer issues. In order to handle multiple applications, employees of these organizations require managing more passwords and usernames. Beyond one point, managing of these passwords becomes a complex task and time consuming thereby employees losing their productivity. This in-turn will lead to monetary losses to the organizations. In order to make sure that the employees concentrate on their core activities and do not spend much of their time managing passwords, businesses implement solutions like password management which ensures that the passwords are safe and at the same time do not cost a bomb to the companies. This report presents interpretative and easy-to-understand facts on how the current password management market is segmented based on end-user, verticals, deployment type and geographies. It cuts through several facets of the password management market such as market size, market share for each segment, the drivers and constraints of password management marketplace. It also throws light on various verticals where password management is being rigorously implemented and the deployment type that is being preferred. Report also provides information on the challenges and opportunities that lie ahead for these solutions.
Data protection: Steps Organisations can take to ensure compliance

This presentation highlights the major principles and rights enshrined in the General Data Protection Regulations (GDPR) as well as 10 steps organisations (whether large or small) can take to ensure compliance.
Please read the instructions and source that provided, then decide.docx

Please read the instructions and source that provided, then decide if you can do it or not!
Due Date: June 24, 2015 12:00 PM, Chicago Time !
The final paper will run from 4 to 6 pages long, double spaced with appropriate citations and will be due during the final week of the course. The paper is to be written in either the APA or MLA format and will include a cover page and a works cited page. The cover page and the references page do not count toward the minimum page requirement.
Adoption of the Critical Security Controls is a hot topic in today’s organizations. Review the CSC survey document and provide at least one suggestion on three different controls for an organization to move from awareness of the CSC’s to implementation. Please feel free to make assumptions as needed for you to develop recommendations for a fictional company.
Note: please follow these instructions, Don’t use outside sources. You must just use the PDF file that I provided as resource.
SANS 2013 Critical Security Controls Survey:
Moving From Awareness to Action
June 2013
A SANS Whitepaper
Written by: John Pescatore
Advisor: Tony Sager
Level of Awareness PAge 5
Perceived Benefits and Barriers to Adoption PAge 7
Assessment: Identifying the Gaps PAge 9
Levels of Adoption PAge 11
Implementation Progress and Experience PAge 15
Measurement and Metrics PAge 17
Sponsored by
EiQ Networks, FireEye, IBM, Symantec and Tenable Network Security
©2013 SANS™ Institute
Over the years, many security standards and requirements frameworks have been developed in attempts
to address risks to enterprise systems and the critical data in them. However, most of these efforts have
essentially become exercises in reporting on compliance and have actually diverted security program
resources from the constantly evolving attacks that must be addressed. In 2008, the U.S. National Security
Agency (NSA) recognized the diversion of resources as a serious problem, and the agency began an effort
that took an “offense must inform defense” approach to prioritizing a list of the controls that would have the
greatest impact in improving risk posture against real-world threats.1 A consortium of U.S. and international
agencies quickly grew, and ultimately, recommendations for what were to become the Critical Security
Controls (CSCs) were coordinated through the SANS Institute.2
How well are the CSCs known in government and private industry, and how are they being used? More
importantly, what can we learn from CSC implementations to date? These and other questions were posed to
699 respondents to a recent online survey conducted by the SANS Institute.
This is what we found:
• The majority of respondents (73%) are aware of the CSCs and have adopted or are planning to adopt
them, while a further 15% are aware of the Controls, but have no plans to adopt them. Only 12% hadn’t
heard of the Controls before the survey.
• The respondents’ primary driver .
Your Supply Chain partner for electronic components.pdf

Origin Data is a leading independent distributor of electronic components. Our primary focus is assisting customers in sourcing obsolete, end-of-life, hard-to-find and commonly used parts. Drawing on our extensive network and industry expertise, Origin Data we provide timely, reliable quotes for hard-to-source electronic components and peripherals, ensuring fast delivery that our customers can rely on. For more information visit our website.
Mesos Meetup - Building an enterprise-ready analytics and operational ecosyst...

On November 6th, we got together at Google Campus to talk about Mesos and DC/OS.
Ignacio Mulas, Sparta & Spark Product Owner at Stratio, explained how to build an environment that can secure and govern its data for operational and analytical applications on top of DC/OS platform. He showed that analytical and machine learning pipelines can be combined with operational processes maintaining the security and providing governing tools to manage our data. He focused on the architecture and tools needed to achieve an ecosystem like this and we will show a demo of it. He also explained how we can develop our pipelines interactively with auto-discovered data catalogs and explore our results.
Find out more: https://www.stratio.com/events/discover-how-to-deploy-a-secure-big-data-pipeline-with-dcos/
The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)

An examination of emerging hacking groups that seek to promote "reality hacks" to bring about a super-intelligence convergence of man and machine.
More Related Content
Similar to Basics on Cyber Threat Intelligence Collection and Information Sharing
Data Analytics in Industry Verticals, Data Analytics Lifecycle, Challenges of...

Banking and securities
Challenges
Early warning for securities fraud and trade visibilities
Card fraud detection and audit trails
Enterprise credit risk reporting
Customer data transformation and analytics.
The Security Exchange commission (SEC) is using big data to monitor financial market activity by using network analytics and natural language processing. This helps to catch illegal trading activity in the financial markets.
The Data Analytics Lifecycle is designed specifically for Big Data problems and data science projects. The lifecycle has six phases, and project work can occur in several phases at once. For most phases in the lifecycle, the movement can be either forward or backward. This iterative depiction of the lifecycle is intended to more closely portray a real project, in which aspects of the project move forward and may return to earlier stages as new information is uncovered and team members learn more about various stages of the project. This enables participants to move iteratively through the process and drive toward operationalizing the project work.
Phase 1—Discovery: In Phase 1, the team learns the business domain, including relevant history such as whether the organization or business unit has attempted similar projects in the past from which they can learn. The team assesses the resources available to support the project in terms of people, technology, time, and data. Important activities in this phase include framing the business problem as an analytics challenge that can be addressed in subsequent phases and formulating initial hypotheses (IHs) to test and begin learning the data.
Phase 2—Data preparation: Phase 2 requires the presence of an analytic sandbox, in which the team can work with data and perform analytics for the duration of the project. The team needs to execute extract, load, and transform (ELT) or extract, transform and load (ETL) to get data into the sandbox. The ELT and ETL are sometimes abbreviated as ETLT. Data should be transformed in the ETLT process so the team can work with it and analyze it. In this phase, the team also needs to familiarize itself with the data thoroughly and take steps to condition the data.
Data analysis step by step guide

This ebook is all about data analysis, what are the steps involved in data analysis and what are the techniques. We will bring out a detailed course very soon. pls register https://excelfinanceacademy.zenler.com/ to save over 80% cost
DATA PROTECTION IMPACT ASSESSMENT TEMPLATE (ODPC).docx

The data protection impact assessment for a cloud based project aims to provide financial inclusion for the unbanked population through its three modules, i.e., wallet, social banking and marketplace/business hub. The primary goal is to enable individuals without access to traditional banking services to engage in financial transactions.
The processing involves the collection, storage, and utilization of personal data for various purposes, such as creating digital wallets, facilitating social banking interactions, and delivering targeted marketing content. The platform will manage user information to enable secure and seamless financial transactions.
The targeted data subjects are individuals and entities within the unbanked population who lack access to traditional financial services. These individuals include low-income earners, marginalized communities and those residing in areas with limited banking infrastructure.
The primary class of data subjects includes the unbanked population seeking financial inclusion. Within this group, there may be subcategories, such as individuals with limited financial literacy or those residing in remote areas, and any vulnerable groups, such as elderly users or minors, who are part of the targeted data subjects.
Big data analytics for life insurers

Big data analytics for life insurers- a whitepaper from Capgemini global insurance Centre of excellence
Smartphones in Healthcare

Any meaningful analysis of data depends entirely on the quality of data that is captured. And the method to capture data, which is still quite common in fieldwork, is the paper form.
Even where technology is deployed, the process is brought with vulnerabilities making the data either stale or inaccurate. Mobile viz, using smart devices to replace incumbent methods promises to solve all problems in a single shot.
Ideafarms's Heathwatch is a prototype solution that shows the power of this idea in the area of Disease Surveillance and Proactive Management of Epidemics.
Password Management Market - Outlook (2017-21) for APAC

Increased competition among businesses has forced businesses to become more customer friendly and as a part of this, businesses have started using multiple applications to address customer issues. In order to handle multiple applications, employees of these organizations require managing more passwords and usernames. Beyond one point, managing of these passwords becomes a complex task and time consuming thereby employees losing their productivity. This in-turn will lead to monetary losses to the organizations. In order to make sure that the employees concentrate on their core activities and do not spend much of their time managing passwords, businesses implement solutions like password management which ensures that the passwords are safe and at the same time do not cost a bomb to the companies. This report presents interpretative and easy-to-understand facts on how the current password management market is segmented based on end-user, verticals, deployment type and geographies. It cuts through several facets of the password management market such as market size, market share for each segment, the drivers and constraints of password management marketplace. It also throws light on various verticals where password management is being rigorously implemented and the deployment type that is being preferred. Report also provides information on the challenges and opportunities that lie ahead for these solutions.
Proceedings on Privacy Enhancing Technologies ; 2016 (3)96–11

Proceedings on Privacy Enhancing Technologies ; 2016 (3):96–116
Chad Spensky, Jeffrey Stewart, Arkady Yerukhimovich, Richard Shay, Ari Trachtenberg, Rick
Housley, and Robert K. Cunningham
SoK: Privacy on Mobile Devices – It’s Complicated
Abstract: Modern mobile devices place a wide variety
of sensors and services within the personal space of their
users. As a result, these devices are capable of transpar-
ently monitoring many sensitive aspects of these users’
lives (e.g., location, health, or correspondences). Users
typically trade access to this data for convenient appli-
cations and features, in many cases without a full appre-
ciation of the nature and extent of the information that
they are exposing to a variety of third parties. Never-
theless, studies show that users remain concerned about
their privacy and vendors have similarly been increas-
ing their utilization of privacy-preserving technologies
in these devices. Still, despite significant efforts, these
technologies continue to fail in fundamental ways, leav-
ing users’ private data exposed.
In this work, we survey the numerous components of
mobile devices, giving particular attention to those that
collect, process, or protect users’ private data. Whereas
the individual components have been generally well
studied and understood, examining the entire mobile de-
vice ecosystem provides significant insights into its over-
whelming complexity. The numerous components of this
complex ecosystem are frequently built and controlled
by different parties with varying interests and incen-
tives. Moreover, most of these parties are unknown to
the typical user. The technologies that are employed to
protect the users’ privacy typically only do so within
a small slice of this ecosystem, abstracting away the
greater complexity of the system. Our analysis suggests
that this abstracted complexity is the major cause of
many privacy-related vulnerabilities, and that a funda-
mentally new, holistic, approach to privacy is needed
going forward. We thus highlight various existing tech-
nology gaps and propose several promising research di-
rections for addressing and reducing this complexity.
Keywords: privacy-preserving technologies, mobile, An-
droid, iOS
DOI 10.1515/popets-2016-0018
Received 2015-11-30; revised 2016-03-01; accepted 2016-03-02.
Chad Spensky: University of California, Santa Barbara,
[email protected]
Jeffrey Stewart: MIT Lincoln Laboratory,
[email protected]
1 Introduction
The rapid proliferation of mobile devices has seen them
become integral parts of many users’ lives. Indeed, these
devices provide their users with a variety of increasingly
essential services (e.g., navigation, communication, and
Internet connectivity), as well as useful functionality
(e.g., entertainment and photography). To accommo-
date these services, modern mobile devices are equipped
with various sensors, capable of collecting extremely rich
information about their users and their surroundings.
Users and de ...
Password Management Market - Outlook (2017-21) for Europe

Increased competition among businesses has forced businesses to become more customer friendly and as a part of this, businesses have started using multiple applications to address customer issues. In order to handle multiple applications, employees of these organizations require managing more passwords and usernames. Beyond one point, managing of these passwords becomes a complex task and time consuming thereby employees losing their productivity. This in-turn will lead to monetary losses to the organizations. In order to make sure that the employees concentrate on their core activities and do not spend much of their time managing passwords, businesses implement solutions like password management which ensures that the passwords are safe and at the same time do not cost a bomb to the companies. This report presents interpretative and easy-to-understand facts on how the current password management market is segmented based on end-user, verticals, deployment type and geographies. It cuts through several facets of the password management market such as market size, market share for each segment, the drivers and constraints of password management marketplace. It also throws light on various verticals where password management is being rigorously implemented and the deployment type that is being preferred. Report also provides information on the challenges and opportunities that lie ahead for these solutions.
Data protection: Steps Organisations can take to ensure compliance

This presentation highlights the major principles and rights enshrined in the General Data Protection Regulations (GDPR) as well as 10 steps organisations (whether large or small) can take to ensure compliance.
Please read the instructions and source that provided, then decide.docx

Please read the instructions and source that provided, then decide if you can do it or not!
Due Date: June 24, 2015 12:00 PM, Chicago Time !
The final paper will run from 4 to 6 pages long, double spaced with appropriate citations and will be due during the final week of the course. The paper is to be written in either the APA or MLA format and will include a cover page and a works cited page. The cover page and the references page do not count toward the minimum page requirement.
Adoption of the Critical Security Controls is a hot topic in today’s organizations. Review the CSC survey document and provide at least one suggestion on three different controls for an organization to move from awareness of the CSC’s to implementation. Please feel free to make assumptions as needed for you to develop recommendations for a fictional company.
Note: please follow these instructions, Don’t use outside sources. You must just use the PDF file that I provided as resource.
SANS 2013 Critical Security Controls Survey:
Moving From Awareness to Action
June 2013
A SANS Whitepaper
Written by: John Pescatore
Advisor: Tony Sager
Level of Awareness PAge 5
Perceived Benefits and Barriers to Adoption PAge 7
Assessment: Identifying the Gaps PAge 9
Levels of Adoption PAge 11
Implementation Progress and Experience PAge 15
Measurement and Metrics PAge 17
Sponsored by
EiQ Networks, FireEye, IBM, Symantec and Tenable Network Security
©2013 SANS™ Institute
Over the years, many security standards and requirements frameworks have been developed in attempts
to address risks to enterprise systems and the critical data in them. However, most of these efforts have
essentially become exercises in reporting on compliance and have actually diverted security program
resources from the constantly evolving attacks that must be addressed. In 2008, the U.S. National Security
Agency (NSA) recognized the diversion of resources as a serious problem, and the agency began an effort
that took an “offense must inform defense” approach to prioritizing a list of the controls that would have the
greatest impact in improving risk posture against real-world threats.1 A consortium of U.S. and international
agencies quickly grew, and ultimately, recommendations for what were to become the Critical Security
Controls (CSCs) were coordinated through the SANS Institute.2
How well are the CSCs known in government and private industry, and how are they being used? More
importantly, what can we learn from CSC implementations to date? These and other questions were posed to
699 respondents to a recent online survey conducted by the SANS Institute.
This is what we found:
• The majority of respondents (73%) are aware of the CSCs and have adopted or are planning to adopt
them, while a further 15% are aware of the Controls, but have no plans to adopt them. Only 12% hadn’t
heard of the Controls before the survey.
• The respondents’ primary driver .
Your Supply Chain partner for electronic components.pdf

Origin Data is a leading independent distributor of electronic components. Our primary focus is assisting customers in sourcing obsolete, end-of-life, hard-to-find and commonly used parts. Drawing on our extensive network and industry expertise, Origin Data we provide timely, reliable quotes for hard-to-source electronic components and peripherals, ensuring fast delivery that our customers can rely on. For more information visit our website.
Mesos Meetup - Building an enterprise-ready analytics and operational ecosyst...

On November 6th, we got together at Google Campus to talk about Mesos and DC/OS.
Ignacio Mulas, Sparta & Spark Product Owner at Stratio, explained how to build an environment that can secure and govern its data for operational and analytical applications on top of DC/OS platform. He showed that analytical and machine learning pipelines can be combined with operational processes maintaining the security and providing governing tools to manage our data. He focused on the architecture and tools needed to achieve an ecosystem like this and we will show a demo of it. He also explained how we can develop our pipelines interactively with auto-discovered data catalogs and explore our results.
Find out more: https://www.stratio.com/events/discover-how-to-deploy-a-secure-big-data-pipeline-with-dcos/
Similar to Basics on Cyber Threat Intelligence Collection and Information Sharing (20)
Data Analytics in Industry Verticals, Data Analytics Lifecycle, Challenges of...

Data Analytics in Industry Verticals, Data Analytics Lifecycle, Challenges of...
DATA PROTECTION IMPACT ASSESSMENT TEMPLATE (ODPC).docx

DATA PROTECTION IMPACT ASSESSMENT TEMPLATE (ODPC).docx
Password Management Market - Outlook (2017-21) for APAC

Password Management Market - Outlook (2017-21) for APAC
Proceedings on Privacy Enhancing Technologies ; 2016 (3)96–11

Proceedings on Privacy Enhancing Technologies ; 2016 (3)96–11
Password Management Market - Outlook (2017-21) for Europe

Password Management Market - Outlook (2017-21) for Europe
Data protection: Steps Organisations can take to ensure compliance

Data protection: Steps Organisations can take to ensure compliance
Please read the instructions and source that provided, then decide.docx

Please read the instructions and source that provided, then decide.docx
Your Supply Chain partner for electronic components.pdf

Your Supply Chain partner for electronic components.pdf
Mesos Meetup - Building an enterprise-ready analytics and operational ecosyst...

Mesos Meetup - Building an enterprise-ready analytics and operational ecosyst...
More from David Sweigert
The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)

An examination of emerging hacking groups that seek to promote "reality hacks" to bring about a super-intelligence convergence of man and machine.
Department of Defense standard 8570 - CompTia Advanced Security Practitioner 

Uploaded as a courtesy by:
Dave Sweigert
EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)

Uploaded as a courtesy by:
Dave Sweigert
Application of Racketeering Law to Suppress CrowdStalking Threats

Uploaded as a courtesy by:
Dave Sweigert
Canada Communications Security Establishment - Threat Vector Chart

Uploaded as a courtesy by:
Dave Sweigert
Port of Charleston evacuation case study: The cognitive threat of conspiracy ...

Uploaded as a courtesy by:
Dave Sweigert
Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT

Uploaded as a courtesy by:
Dave Sweigert
Cyber Risk Assessment for the Emergency Services Sector - DHS

Uploaded as a courtesy by:
Dave Sweigert
More from David Sweigert (20)
The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)

The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)
Sample Network Analysis Report based on Wireshark Analysis

Sample Network Analysis Report based on Wireshark Analysis
Department of Defense standard 8570 - CompTia Advanced Security Practitioner 

Department of Defense standard 8570 - CompTia Advanced Security Practitioner
National Cyber Security Awareness Month - October 2017

National Cyber Security Awareness Month - October 2017
California Attorney General Notification Penal Code 646.9

California Attorney General Notification Penal Code 646.9
Congressional support of Ethical Hacking and Cyber Security

Congressional support of Ethical Hacking and Cyber Security
EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)

EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)
Application of Racketeering Law to Suppress CrowdStalking Threats

Application of Racketeering Law to Suppress CrowdStalking Threats
Canada Communications Security Establishment - Threat Vector Chart

Canada Communications Security Establishment - Threat Vector Chart
Port of Charleston evacuation case study: The cognitive threat of conspiracy ...

Port of Charleston evacuation case study: The cognitive threat of conspiracy ...
Cyber Incident Response Team - NIMS - Public Comment

Cyber Incident Response Team - NIMS - Public Comment
National Incident Management System (NIMS) NQS DRAFT

National Incident Management System (NIMS) NQS DRAFT
National Incident Management System - NQS Public Feedback

National Incident Management System - NQS Public Feedback
Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT

Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT
Cyber Risk Assessment for the Emergency Services Sector - DHS

Cyber Risk Assessment for the Emergency Services Sector - DHS
Recently uploaded
The Importance of Community Nursing Care.pdf

NDIS and Community 24/7 Nursing Care is a specific type of support that may be provided under the NDIS for individuals with complex medical needs who require ongoing nursing care in a community setting, such as their home or a supported accommodation facility.
Navigating Challenges: Mental Health, Legislation, and the Prison System in B...

This conference will delve into the intricate intersections between mental health, legal frameworks, and the prison system in Bolivia. It aims to provide a comprehensive overview of the current challenges faced by mental health professionals working within the legislative and correctional landscapes. Topics of discussion will include the prevalence and impact of mental health issues among the incarcerated population, the effectiveness of existing mental health policies and legislation, and potential reforms to enhance the mental health support system within prisons.
Deep Leg Vein Thrombosis (DVT): Meaning, Causes, Symptoms, Treatment, and Mor...

Deep Leg Vein Thrombosis (DVT): Meaning, Causes, Symptoms, Treatment, and Mor...The Lifesciences Magazine
Deep Leg Vein Thrombosis occurs when a blood clot forms in one or more of the deep veins in the legs. These clots can impede blood flow, leading to severe complications.Leading the Way in Nephrology: Dr. David Greene's Work with Stem Cells for Ki...

Leading the Way in Nephrology: Dr. David Greene's Work with Stem Cells for Ki...Dr. David Greene Arizona
As we watch Dr. Greene's continued efforts and research in Arizona, it's clear that stem cell therapy holds a promising key to unlocking new doors in the treatment of kidney disease. With each study and trial, we step closer to a world where kidney disease is no longer a life sentence but a treatable condition, thanks to pioneers like Dr. David Greene.Medical Technology Tackles New Health Care Demand - Research Report - March 2...

M Capital Group (“MCG”) predicts that with, against, despite, and even without the global pandemic, the medical technology (MedTech) industry shows signs of continuous healthy growth, driven by smaller, faster, and cheaper devices, growing demand for home-based applications, technological innovation, strategic acquisitions, investments, and SPAC listings. MCG predicts that this should reflects itself in annual growth of over 6%, well beyond 2028.
According to Chris Mouchabhani, Managing Partner at M Capital Group, “Despite all economic scenarios that one may consider, beyond overall economic shocks, medical technology should remain one of the most promising and robust sectors over the short to medium term and well beyond 2028.”
There is a movement towards home-based care for the elderly, next generation scanning and MRI devices, wearable technology, artificial intelligence incorporation, and online connectivity. Experts also see a focus on predictive, preventive, personalized, participatory, and precision medicine, with rising levels of integration of home care and technological innovation.
The average cost of treatment has been rising across the board, creating additional financial burdens to governments, healthcare providers and insurance companies. According to MCG, cost-per-inpatient-stay in the United States alone rose on average annually by over 13% between 2014 to 2021, leading MedTech to focus research efforts on optimized medical equipment at lower price points, whilst emphasizing portability and ease of use. Namely, 46% of the 1,008 medical technology companies in the 2021 MedTech Innovator (“MTI”) database are focusing on prevention, wellness, detection, or diagnosis, signaling a clear push for preventive care to also tackle costs.
In addition, there has also been a lasting impact on consumer and medical demand for home care, supported by the pandemic. Lockdowns, closure of care facilities, and healthcare systems subjected to capacity pressure, accelerated demand away from traditional inpatient care. Now, outpatient care solutions are driving industry production, with nearly 70% of recent diagnostics start-up companies producing products in areas such as ambulatory clinics, at-home care, and self-administered diagnostics.
Demystifying-Gene-Editing-The-Promise-and-Peril-of-CRISPR.pdf

CRISPR-Cas9, a revolutionary gene-editing tool, holds immense potential to reshape medicine, agriculture, and our understanding of life. But like any powerful tool, it comes with ethical considerations.
Unveiling CRISPR: This naturally occurring bacterial defense system (crRNA & Cas9 protein) fights viruses. Scientists repurposed it for precise gene editing (correction, deletion, insertion) by targeting specific DNA sequences.
The Promise: CRISPR offers exciting possibilities:
Gene Therapy: Correcting genetic diseases like cystic fibrosis.
Agriculture: Engineering crops resistant to pests and harsh environments.
Research: Studying gene function to unlock new knowledge.
The Peril: Ethical concerns demand attention:
Off-target Effects: Unintended DNA edits can have unforeseen consequences.
Eugenics: Misusing CRISPR for designer babies raises social and ethical questions.
Equity: High costs could limit access to this potentially life-saving technology.
The Path Forward: Responsible development is crucial:
International Collaboration: Clear guidelines are needed for research and human trials.
Public Education: Open discussions ensure informed decisions about CRISPR.
Prioritize Safety and Ethics: Safety and ethical principles must be paramount.
CRISPR offers a powerful tool for a better future, but responsible development and addressing ethical concerns are essential. By prioritizing safety, fostering open dialogue, and ensuring equitable access, we can harness CRISPR's power for the benefit of all. (2998 characters)
Roti bank chennai PPT [Autosaved].pptx1![Roti bank chennai PPT [Autosaved].pptx1](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Roti bank chennai PPT [Autosaved].pptx1](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
One of the most developed cities of India, the city of Chennai is the capital of Tamilnadu and many people from different parts of India come here to earn their bread and butter. Being a metropolitan, the city is filled with towering building and beaches but the sad part as with almost every Indian city
Dimensions of Healthcare Quality

The dimensions of healthcare quality refer to various attributes or aspects that define the standard of healthcare services. These dimensions are used to evaluate, measure, and improve the quality of care provided to patients. A comprehensive understanding of these dimensions ensures that healthcare systems can address various aspects of patient care effectively and holistically. Dimensions of Healthcare Quality and Performance of care include the following; Appropriateness, Availability, Competence, Continuity, Effectiveness, Efficiency, Efficacy, Prevention, Respect and Care, Safety as well as Timeliness.
Telehealth Psychology Building Trust with Clients.pptx

Telehealth psychology is a digital approach that offers psychological services and mental health care to clients remotely, using technologies like video conferencing, phone calls, text messaging, and mobile apps for communication.
Health Education on prevention of hypertension

Hypertension is a chronic condition of concern due to its role in the causation of coronary heart diseases. Hypertension is a worldwide epidemic and important risk factor for coronary artery disease, stroke and renal diseases. Blood pressure is the force exerted by the blood against the walls of the blood vessels and is sufficient to maintain tissue perfusion during activity and rest. Hypertension is sustained elevation of BP. In adults, HTN exists when systolic blood pressure is equal to or greater than 140mmHg or diastolic BP is equal to or greater than 90mmHg. The
Navigating Women's Health: Understanding Prenatal Care and Beyond

Navigating Women's Health with Aboud Health Group. Explore comprehensive care options for women's wellness needs in Mississauga.
Antibiotic Stewardship by Anushri Srivastava.pptx

Stewardship is the act of taking good care of something.
Antimicrobial stewardship is a coordinated program that promotes the appropriate use of antimicrobials (including antibiotics), improves patient outcomes, reduces microbial resistance, and decreases the spread of infections caused by multidrug-resistant organisms.
WHO launched the Global Antimicrobial Resistance and Use Surveillance System (GLASS) in 2015 to fill knowledge gaps and inform strategies at all levels.
ACCORDING TO apic.org,
Antimicrobial stewardship is a coordinated program that promotes the appropriate use of antimicrobials (including antibiotics), improves patient outcomes, reduces microbial resistance, and decreases the spread of infections caused by multidrug-resistant organisms.
ACCORDING TO pewtrusts.org,
Antibiotic stewardship refers to efforts in doctors’ offices, hospitals, long term care facilities, and other health care settings to ensure that antibiotics are used only when necessary and appropriate
According to WHO,
Antimicrobial stewardship is a systematic approach to educate and support health care professionals to follow evidence-based guidelines for prescribing and administering antimicrobials
In 1996, John McGowan and Dale Gerding first applied the term antimicrobial stewardship, where they suggested a causal association between antimicrobial agent use and resistance. They also focused on the urgency of large-scale controlled trials of antimicrobial-use regulation employing sophisticated epidemiologic methods, molecular typing, and precise resistance mechanism analysis.
Antimicrobial Stewardship(AMS) refers to the optimal selection, dosing, and duration of antimicrobial treatment resulting in the best clinical outcome with minimal side effects to the patients and minimal impact on subsequent resistance.
According to the 2019 report, in the US, more than 2.8 million antibiotic-resistant infections occur each year, and more than 35000 people die. In addition to this, it also mentioned that 223,900 cases of Clostridoides difficile occurred in 2017, of which 12800 people died. The report did not include viruses or parasites
VISION
Being proactive
Supporting optimal animal and human health
Exploring ways to reduce overall use of antimicrobials
Using the drugs that prevent and treat disease by killing microscopic organisms in a responsible way
GOAL
to prevent the generation and spread of antimicrobial resistance (AMR). Doing so will preserve the effectiveness of these drugs in animals and humans for years to come.
being to preserve human and animal health and the effectiveness of antimicrobial medications.
to implement a multidisciplinary approach in assembling a stewardship team to include an infectious disease physician, a clinical pharmacist with infectious diseases training, infection preventionist, and a close collaboration with the staff in the clinical microbiology laboratory
to prevent antimicrobial overuse, misuse and abuse.
to minimize the developme
CHAPTER 1 SEMESTER V - ROLE OF PEADIATRIC NURSE.pdf

Pediatric nurses play a vital role in the health and well-being of children. Their responsibilities are wide-ranging, and their objectives can be categorized into several key areas:
1. Direct Patient Care:
Objective: Provide comprehensive and compassionate care to infants, children, and adolescents in various healthcare settings (hospitals, clinics, etc.).
This includes tasks like:
Monitoring vital signs and physical condition.
Administering medications and treatments.
Performing procedures as directed by doctors.
Assisting with daily living activities (bathing, feeding).
Providing emotional support and pain management.
2. Health Promotion and Education:
Objective: Promote healthy behaviors and educate children, families, and communities about preventive healthcare.
This includes tasks like:
Administering vaccinations.
Providing education on nutrition, hygiene, and development.
Offering breastfeeding and childbirth support.
Counseling families on safety and injury prevention.
3. Collaboration and Advocacy:
Objective: Collaborate effectively with doctors, social workers, therapists, and other healthcare professionals to ensure coordinated care for children.
Objective: Advocate for the rights and best interests of their patients, especially when children cannot speak for themselves.
This includes tasks like:
Communicating effectively with healthcare teams.
Identifying and addressing potential risks to child welfare.
Educating families about their child's condition and treatment options.
4. Professional Development and Research:
Objective: Stay up-to-date on the latest advancements in pediatric healthcare through continuing education and research.
Objective: Contribute to improving the quality of care for children by participating in research initiatives.
This includes tasks like:
Attending workshops and conferences on pediatric nursing.
Participating in clinical trials related to child health.
Implementing evidence-based practices into their daily routines.
By fulfilling these objectives, pediatric nurses play a crucial role in ensuring the optimal health and well-being of children throughout all stages of their development.
Essential Metrics for Palliative Care Management

Explore our infographic on 'Essential Metrics for Palliative Care Management' which highlights key performance indicators crucial for enhancing the quality and efficiency of palliative care services.
This visual guide breaks down important metrics across four categories: Patient-Centered Metrics, Care Efficiency Metrics, Quality of Life Metrics, and Staff Metrics. Each section is designed to help healthcare professionals monitor and improve care delivery for patients facing serious illnesses. Understand how to implement these metrics in your palliative care practices for better outcomes and higher satisfaction levels.
Artificial Intelligence to Optimize Cardiovascular Therapy

Presentation at the annual convention of the Philippine Heart Association, 31 May 2024. EDSA Shangrila Hotel, Manila.
Recently uploaded (20)
Navigating Challenges: Mental Health, Legislation, and the Prison System in B...

Navigating Challenges: Mental Health, Legislation, and the Prison System in B...
Deep Leg Vein Thrombosis (DVT): Meaning, Causes, Symptoms, Treatment, and Mor...

Deep Leg Vein Thrombosis (DVT): Meaning, Causes, Symptoms, Treatment, and Mor...
Leading the Way in Nephrology: Dr. David Greene's Work with Stem Cells for Ki...

Leading the Way in Nephrology: Dr. David Greene's Work with Stem Cells for Ki...
Medical Technology Tackles New Health Care Demand - Research Report - March 2...

Medical Technology Tackles New Health Care Demand - Research Report - March 2...
Demystifying-Gene-Editing-The-Promise-and-Peril-of-CRISPR.pdf

Demystifying-Gene-Editing-The-Promise-and-Peril-of-CRISPR.pdf
Telehealth Psychology Building Trust with Clients.pptx

Telehealth Psychology Building Trust with Clients.pptx
Navigating Women's Health: Understanding Prenatal Care and Beyond

Navigating Women's Health: Understanding Prenatal Care and Beyond
CHAPTER 1 SEMESTER V - ROLE OF PEADIATRIC NURSE.pdf

CHAPTER 1 SEMESTER V - ROLE OF PEADIATRIC NURSE.pdf
Artificial Intelligence to Optimize Cardiovascular Therapy

Artificial Intelligence to Optimize Cardiovascular Therapy
Surgery-Mini-OSCE-All-Past-Years-Questions-Modified.

Surgery-Mini-OSCE-All-Past-Years-Questions-Modified.
Basics on Cyber Threat Intelligence Collection and Information Sharing
- 1. The 6 Steps in the Intelligence Cycle Step # 1 PLANNING AND DIRECTION: Establish the consumer’s intelligence requirements and plan intelligence activities accordingly. The planning and direction step sets the stage for the Intelligence Cycle. It is the springboard from which all Intelligence Cycle activities are launched and is the foundation for the entire process. This portion of the process includes determining the information need, deciding how to collect that information, and setting up a timetable for collecting the information. Generally, in such cases, the consumer has a requirement for a specific product. That product may be a full report, a graphic image, or raw information that is collected, processed, and disseminated, but skips the analysis and production step. Step # 2 COLLECTION: Gather the raw data required to produce the finished product. Data collection is performed through five basic intelligence sources: Geospatial Intelligence (GEOINT), Human Intelligence (HUMINT), Measurement and Signature Intelligence (MASINT), Open-Source Intelligence (OSINT), and Signals Intelligence (SIGINT). The sources of the raw data may include, but are not limited to, news reports, aerial imagery, satellite imagery, and government and public documents. Along with these five sources, information can be taken from law enforcement agencies, public safety agencies, and the private sector. The purpose of this collection is to meet the defined tactical or strategic goal. Step # 3 PROCESSING AND EXPLOITATION: Convert the raw data into a comprehensible format that is usable for production of the finished product. The processing and exploitation step involves the use of highly trained and specialized personnel and technologically sophisticated equipment to turn the raw data into usable and understandable information. Data translation, data decryption, and interpretation of filmed images and other imagery are only a few of the processes used for converting data stored on film, magnetic, or other media into information ready for analysis and production. Step # 4 ANALYSIS AND PRODUCTION: Integrate, evaluate, analyze, and prepare the processed information for inclusion in the finished product. This step transforms raw data into applicable products, separating “information” from “intelligence.” The analysis and production step also requires highly trained and specialized personnel (in this case, analysts) to give meaning to the processed information
- 2. and to prioritize it against known requirements. Synthesizing the processed information into a finished, actionable intelligence product enables the information to be useful to the customer. The final result of this process should be information that will prevent terrorist attacks or other criminal activities. Step # 5 DISSEMINATION: Deliver the finished product to the consumer that requested it and to others as applicable. The consumer that requested the information receives the finished product, usually via electronic transmission in a timely and credible manner. Dissemination of the information typically is accomplished through such means as websites, email, Web 2.0 collaboration tools, and hardcopy distribution. The final, finished product is referred to as “finished intelligence.” After the product is disseminated, further gaps in the intelligence may be identified, and the Intelligence Cycle begins all over again. NOTE: DHS Intelligence and Analysis produces a variety of intelligence products for state, local, tribal and territorial partners: Daily Intelligence Highlights, Roll Call Releases, Homeland Security Notes, Homeland Security Reference Aids, Homeland Security Assessments, Homeland Security Monitor, Intelligence Notifications and Homeland Security State and Local Intelligence Community of Interest messages, and Suspicious Activity Reports trend analysis. Step # 6 EVALUATION: Continually acquire feedback during the Intelligence Cycle and evaluate that feedback to refine each individual step and the cycle as a whole. Constant evaluation and feedback from consumers are extremely important to enabling those involved in the Intelligence Cycle to adjust and refine their activities and analysis to better meet consumers’ changing and evolving information needs. This step helps assess current and new information found, recognize weak areas and potential threats, and eliminate those identified weakness. Here is a sample of the feedback form used by DHS Intelligence and Analysis. Similar forms are used by many fusion centers. For more information about the P/CRCL Officer Orientation visit www.it.ojp.gov/PrivacyLiberty Source: This section was primarily drawn from U.S .National Intelligence: An Overview 2013 published by the Office of the Director of National Intelligence with additional content from the Fusion Center Guidelines and the Baseline Capabilities.
