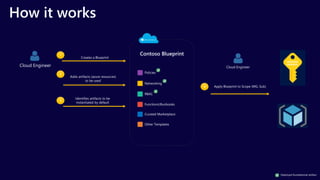
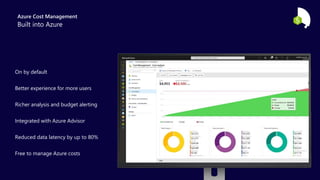
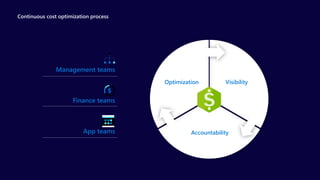
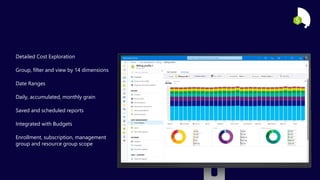
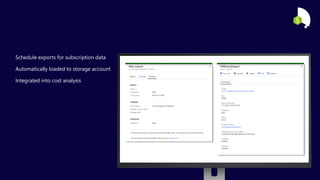
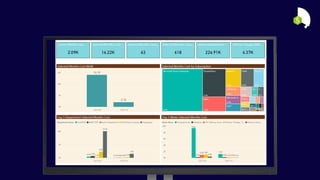
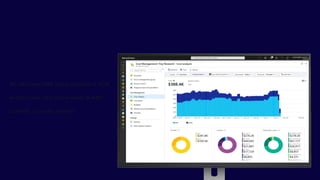
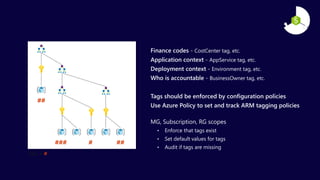
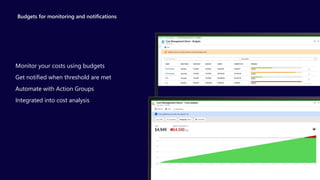
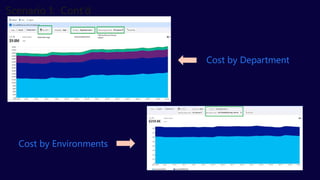
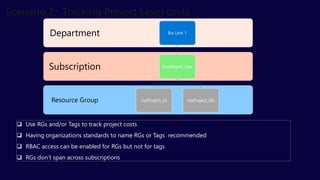
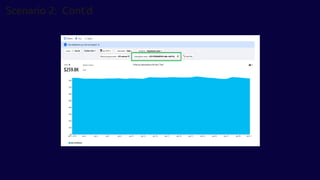
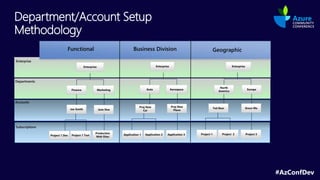
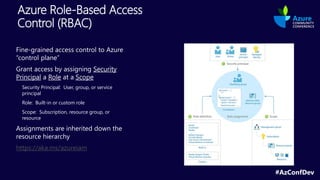
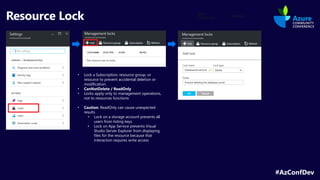
The document describes the Azure Community Conference 2021 in India. It provides an agenda for the conference including presentations on Azure governance at scale, management groups, role-based access control, Azure policy, Azure cost management, and optimization recommendations. The conference features Anant Maheshwari, President of Microsoft India, and covers how to setup governed Azure subscriptions using Azure Blueprints and other governance tools and best practices.












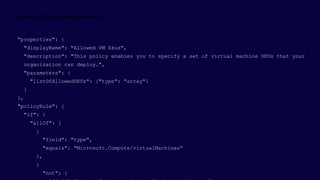
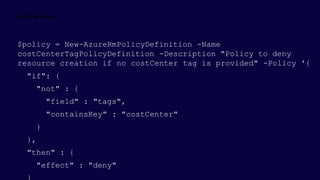
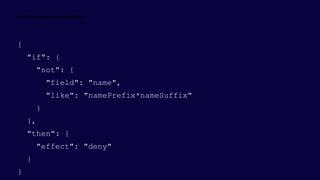
![{
"if": {
<accessor>, <condition> | <logical operator>
},
"then": {
"effect": “Disabled | append | deny | audit | auditIfNotExists | deployIfNotExists"
}
}
Operators
“not”: { … }
“allOf”: [ … ]
“anyOf”: [ … ]
Conditions
“equals”: “value”
“like”: “value”
“match”: “value”
“contains”: “value”
“in”: [“val1”, “val2”]
“containsKey”: “keyName”
“exists”: “bool”
+ “not*” variants
Accessors
“field”: “fieldname”
“source”: “action”
Fields
name
kind
type
location
fullName
tags
tags.*
aliases](https://image.slidesharecdn.com/azuregovernanceforenterprise-211028162334/85/Azure-Governance-for-Enterprise-20-320.jpg)
!["properties": {
"displayName": "Allowed VM Skus",
"description": "This policy enables you to specify a set of virtual machine SKUs that your
organization can deploy.“
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines“
},
{
"not": {
"field":"Microsoft.Compute/virtualMachines/sku.name",
"in": ["Basic_A0”,”Basic_A1”,”Basic_A2”,”Basic_A3”,”Basic_A4”]](https://image.slidesharecdn.com/azuregovernanceforenterprise-211028162334/85/Azure-Governance-for-Enterprise-23-320.jpg)