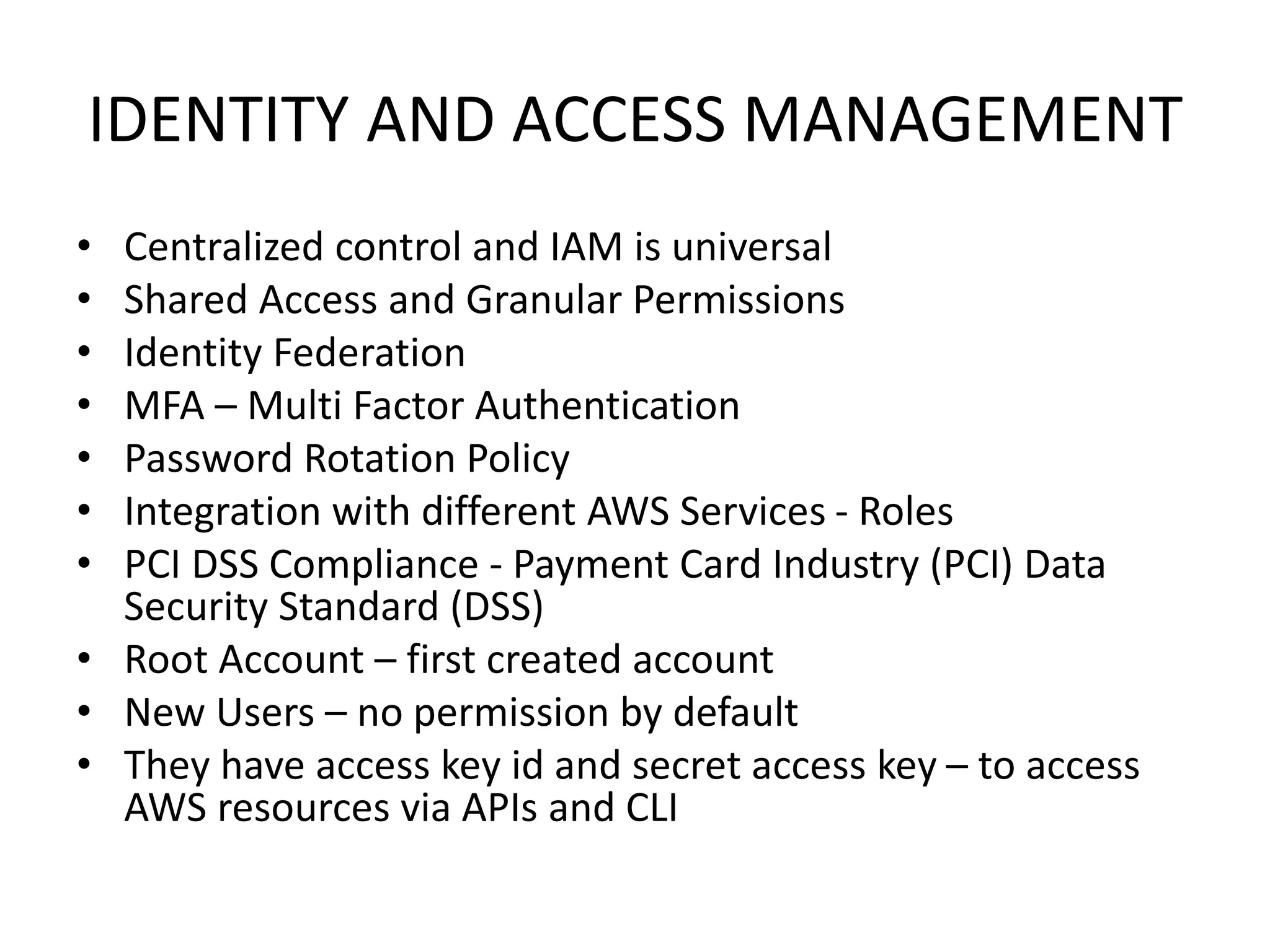
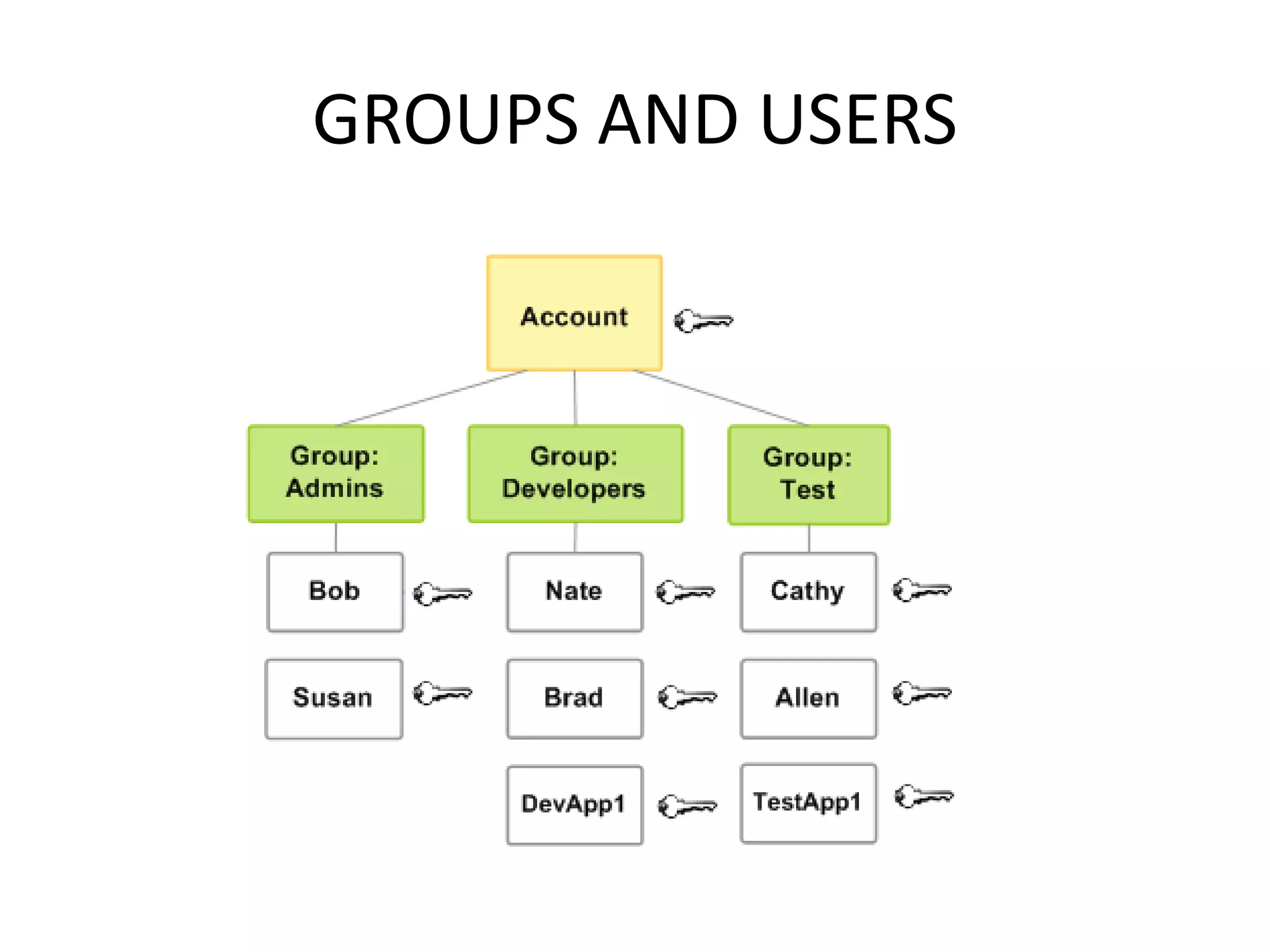
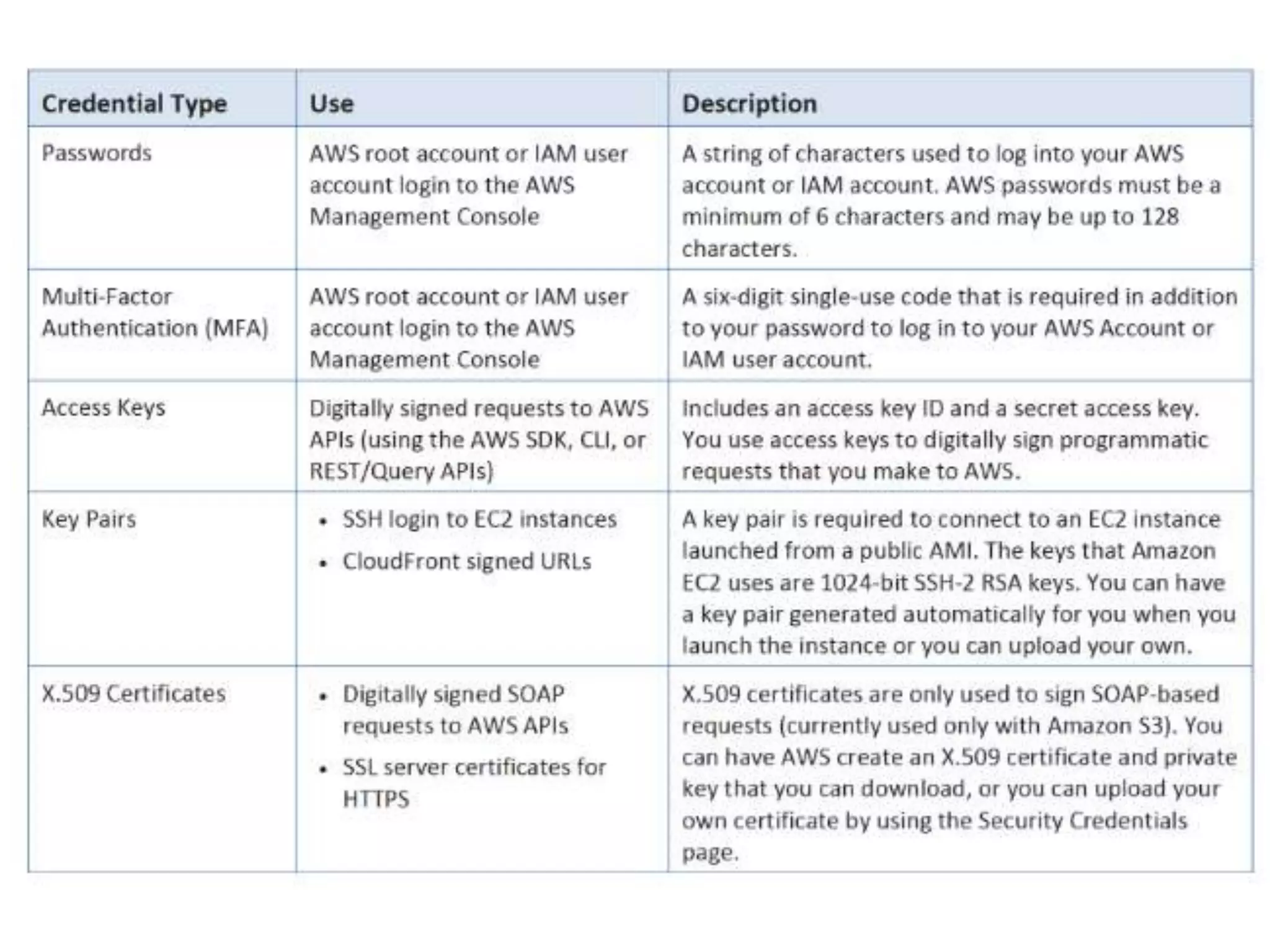
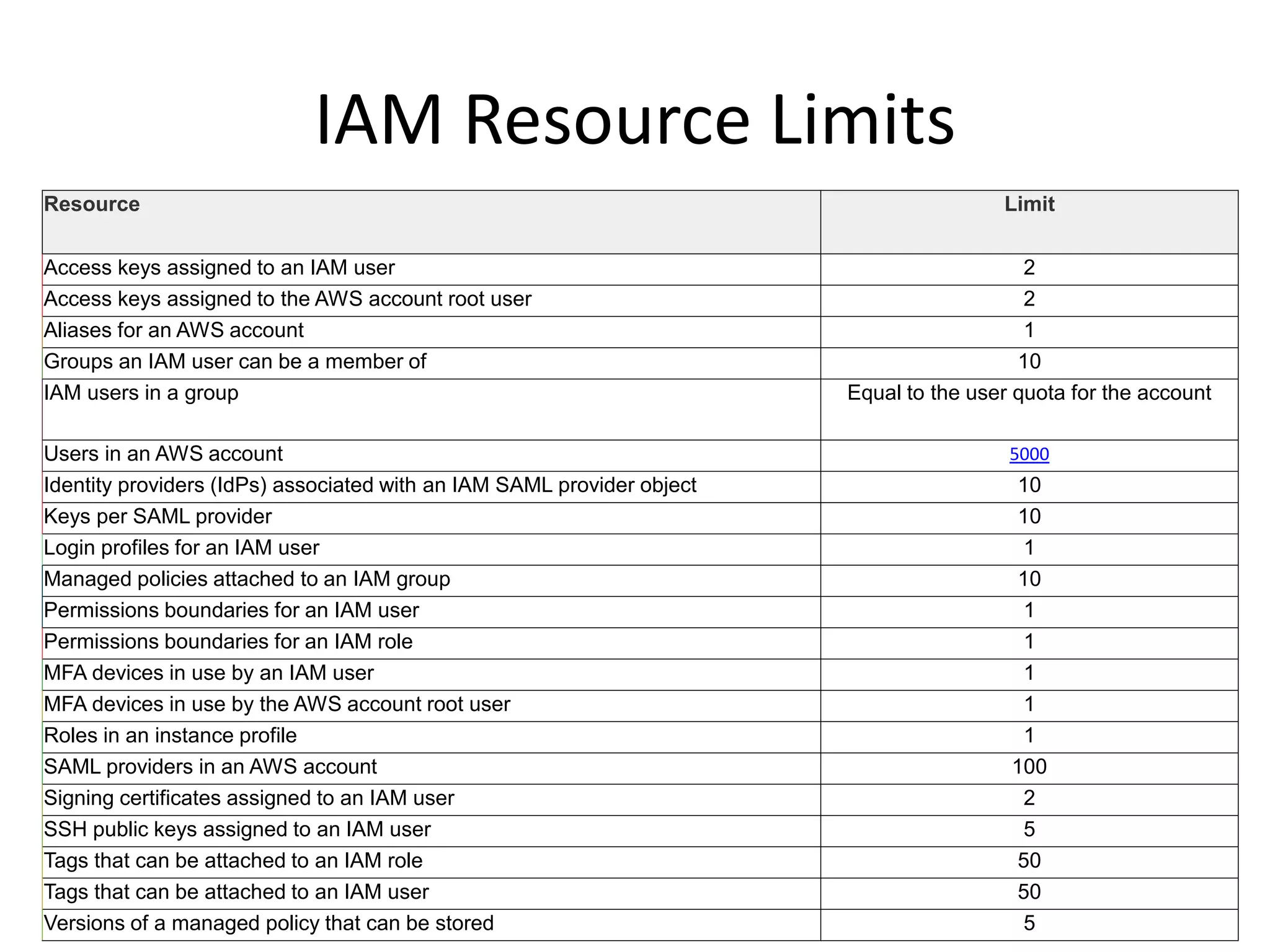
This document summarizes ways to access AWS and manage identity and access. It discusses the AWS Management Console, AWS CLI, SDKs, and IAM API for accessing AWS. It then covers key aspects of IAM including centralized control, shared access, granular permissions, identity federation, MFA, password policies, integration with AWS services, and resource limits. It also discusses managed policies, inline policies, and resource-based policies for controlling access and permissions.