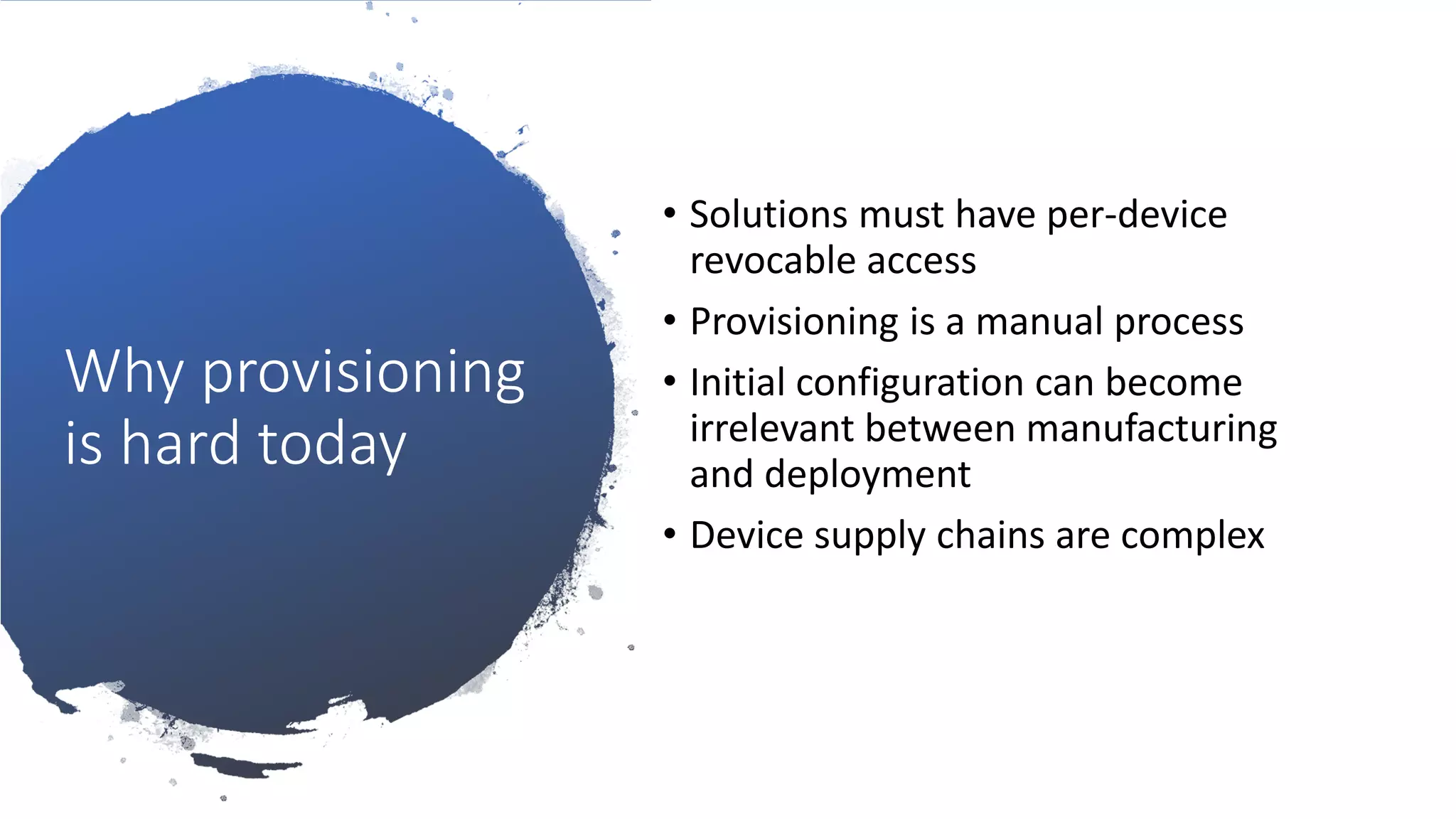
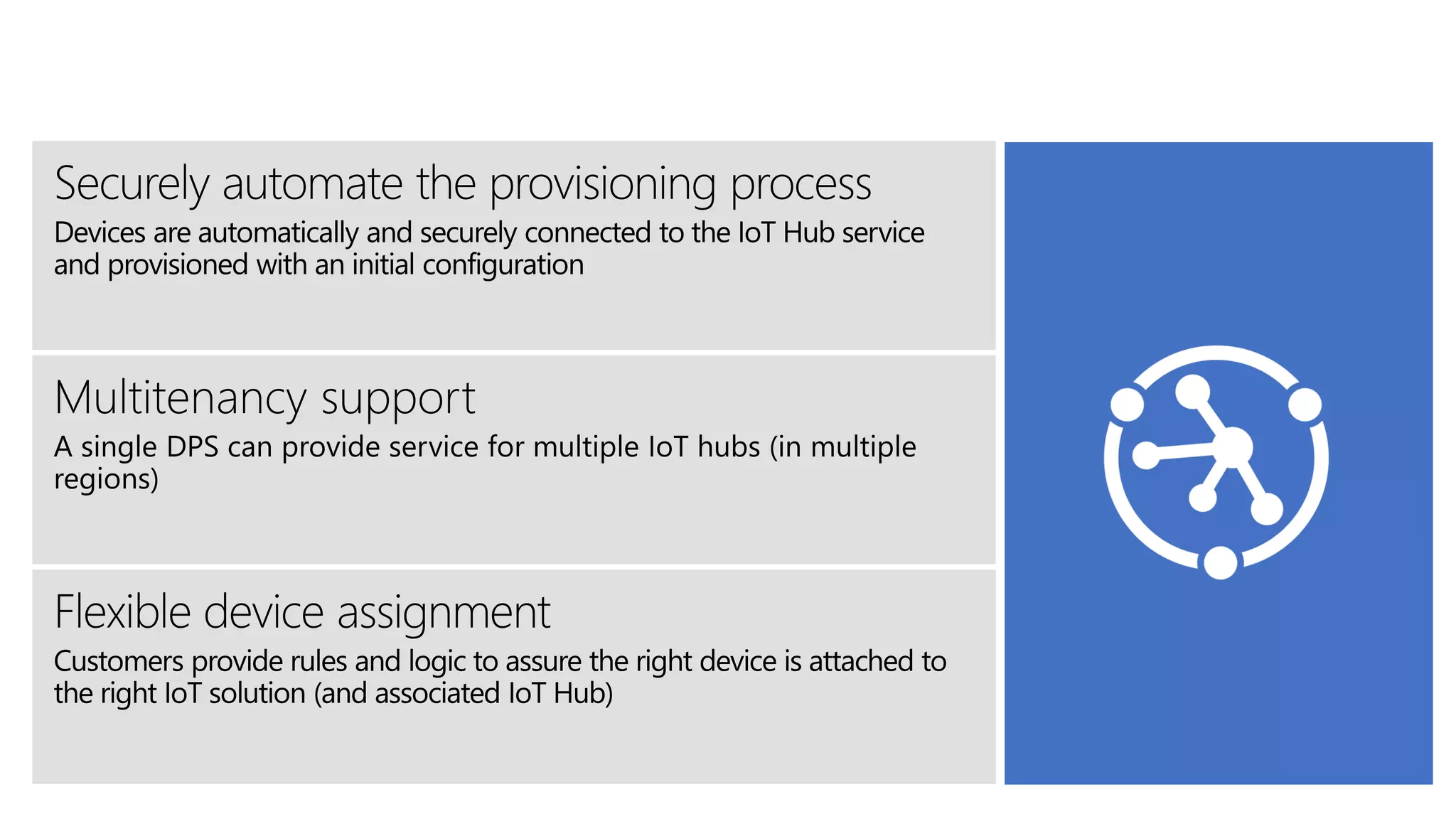
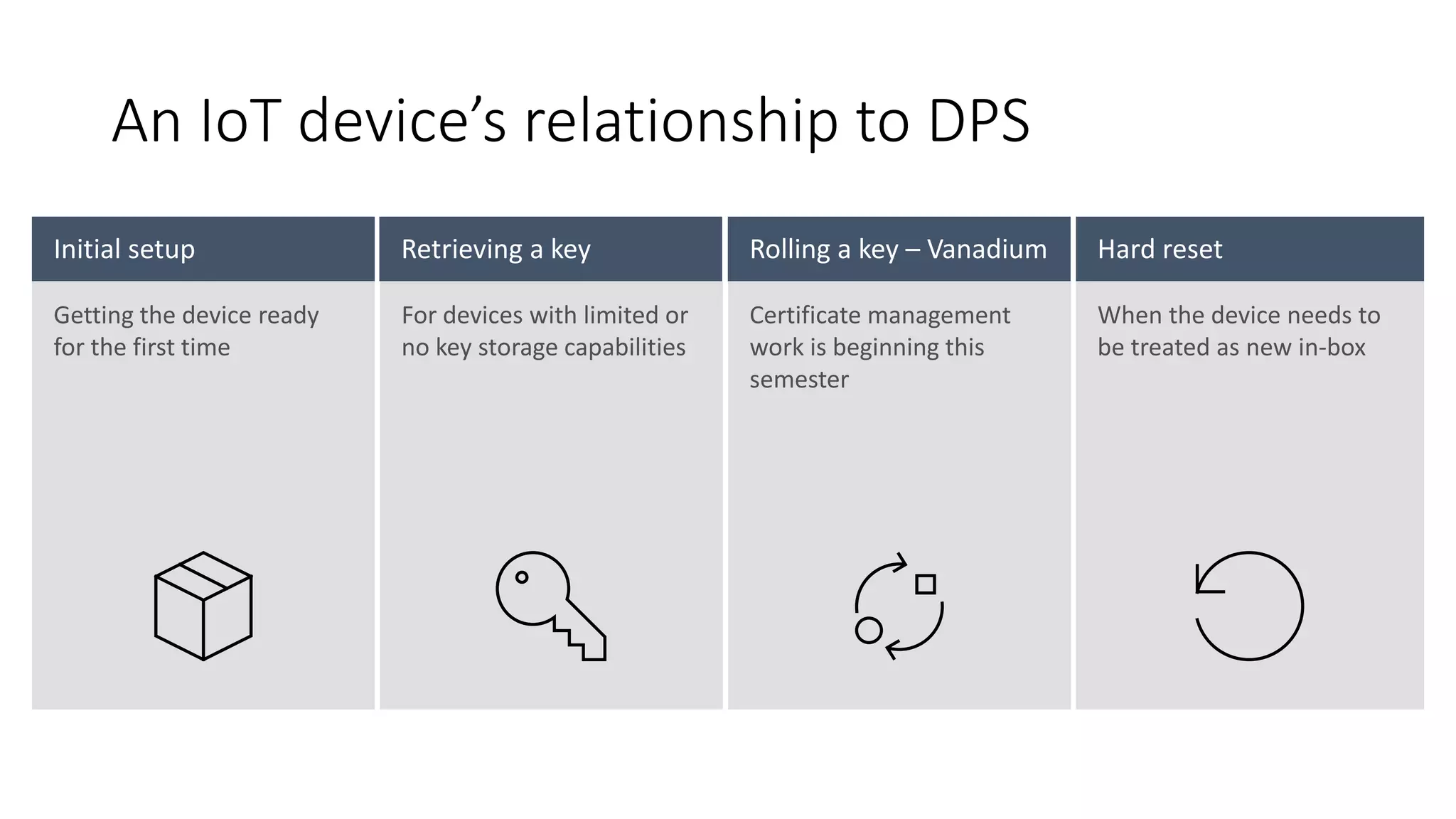
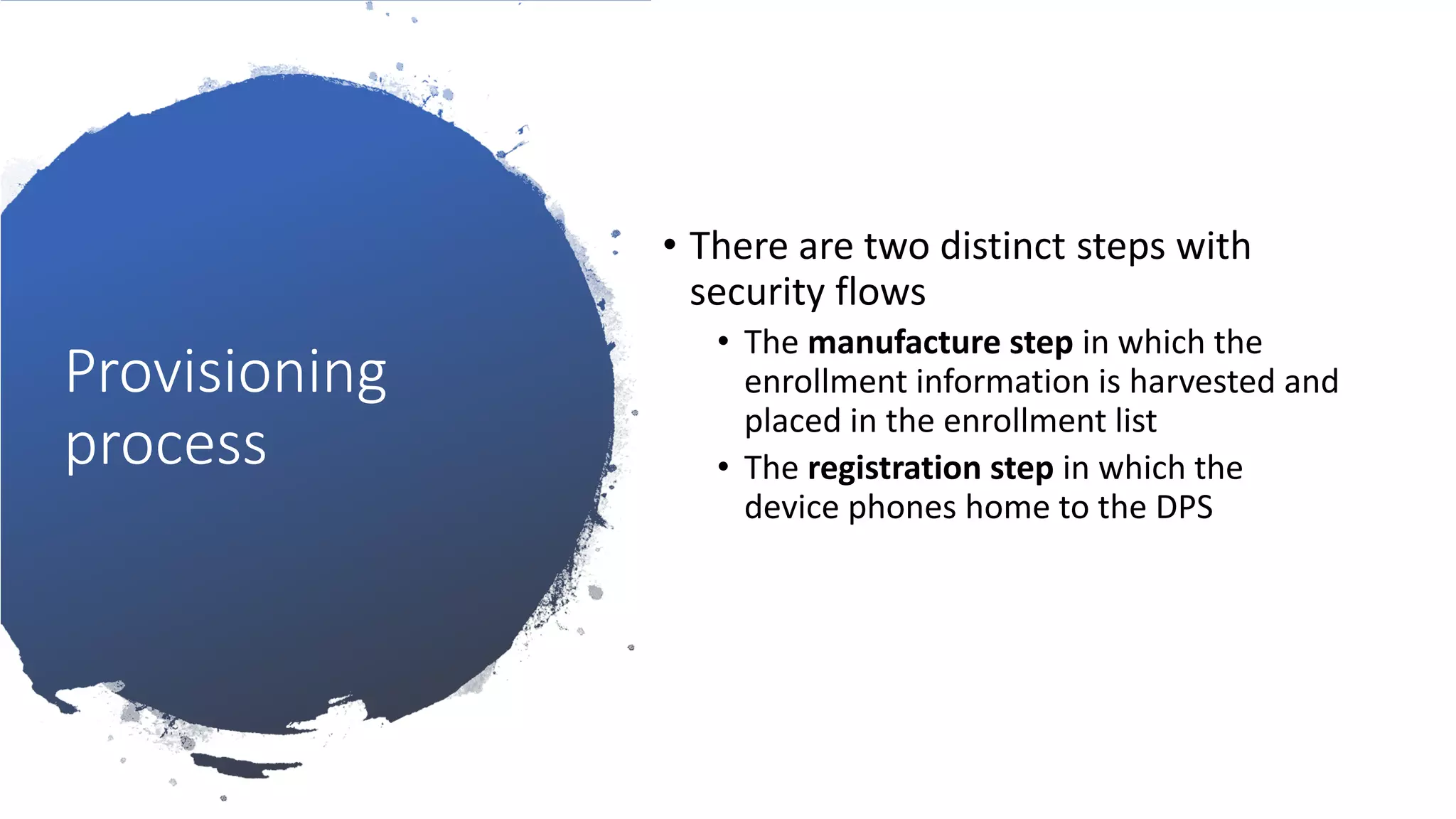
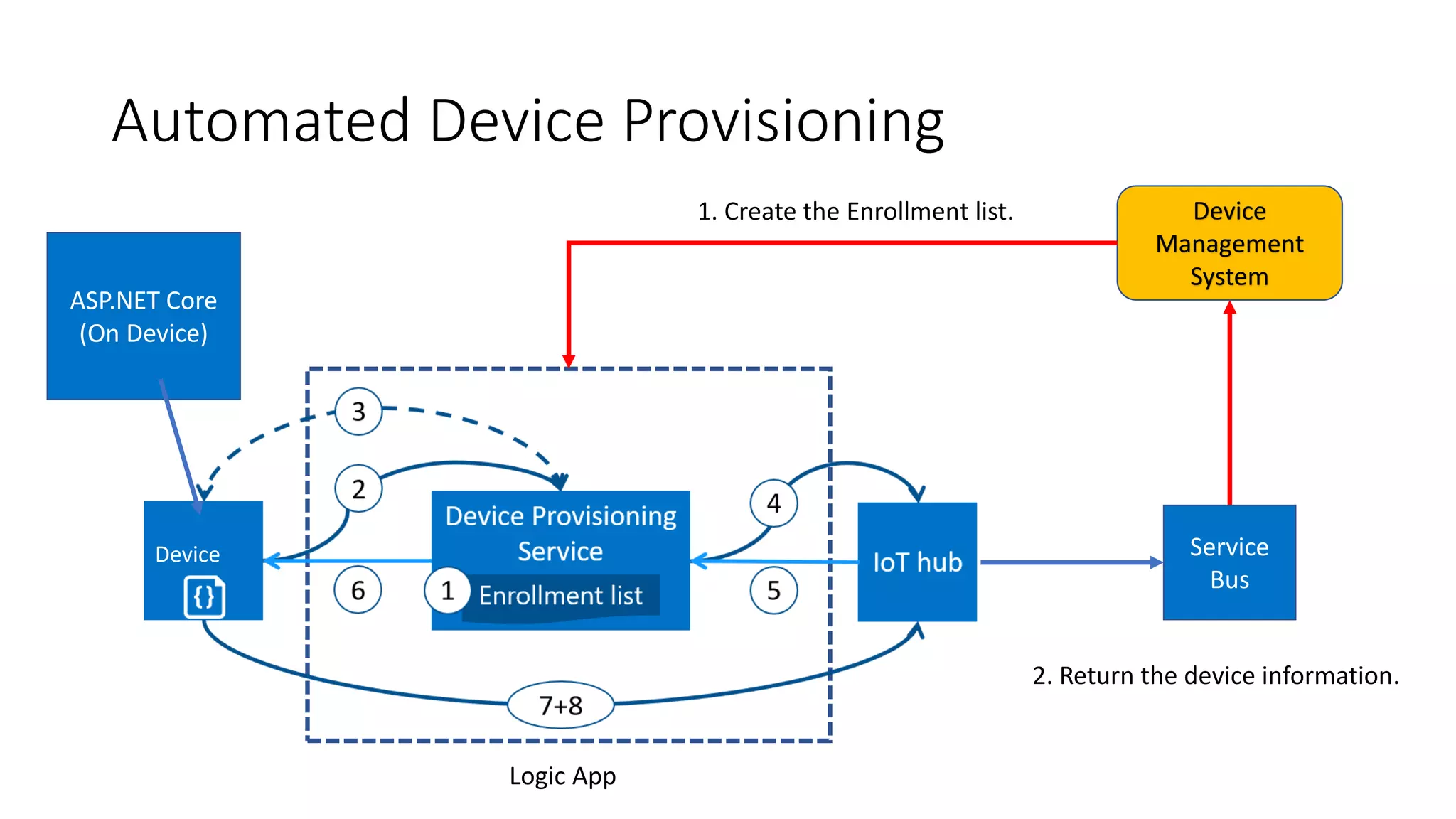
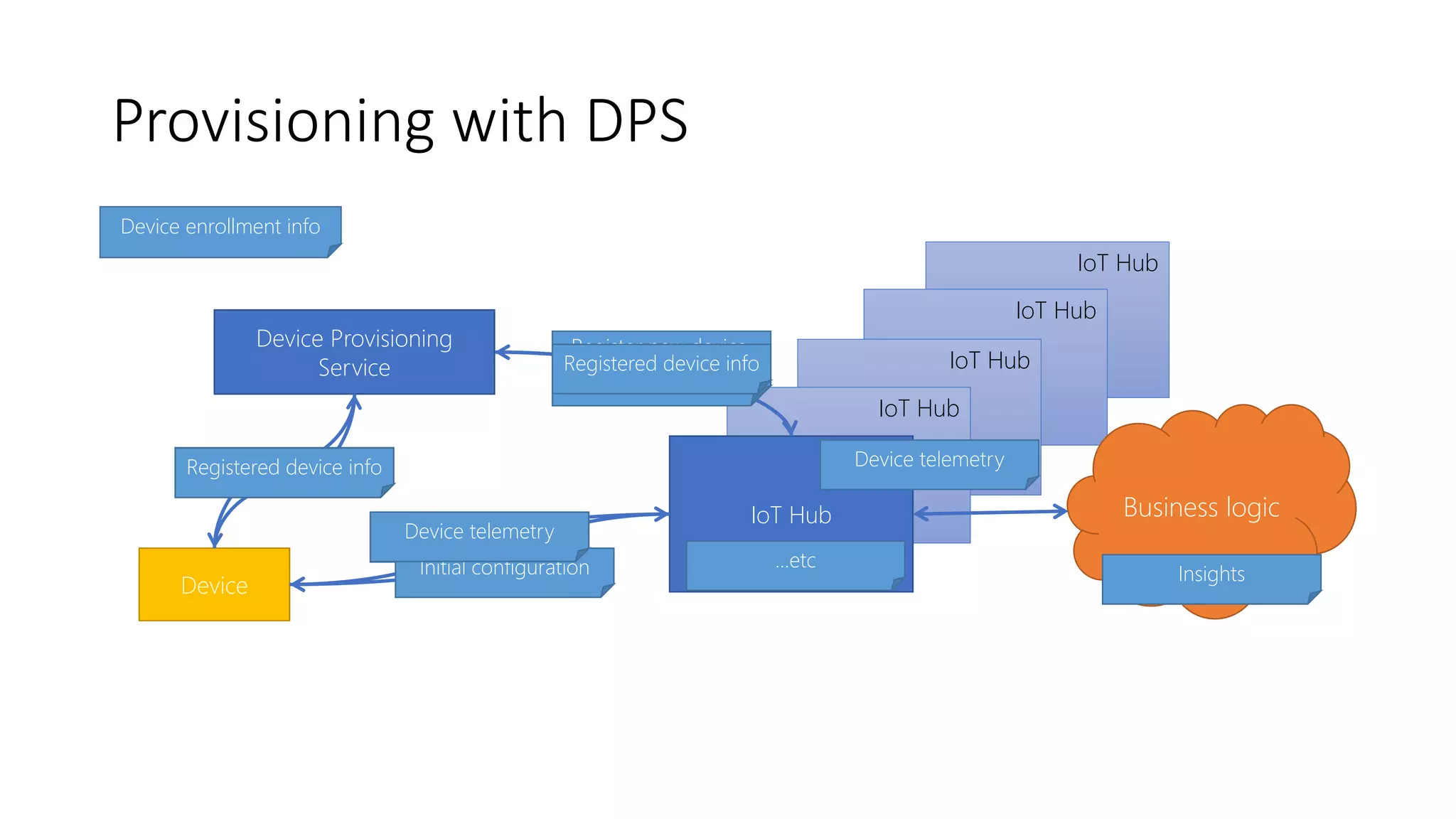
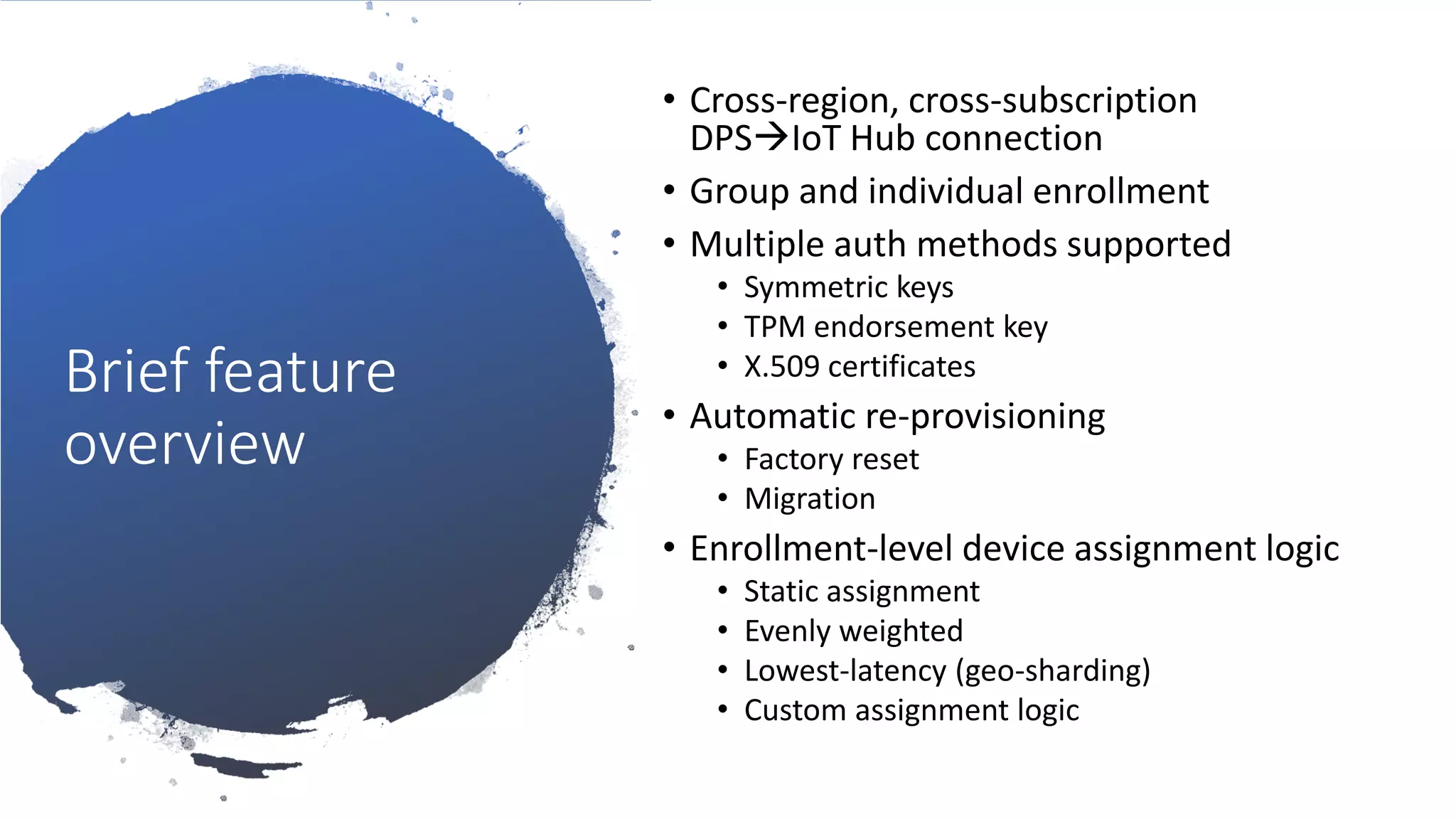
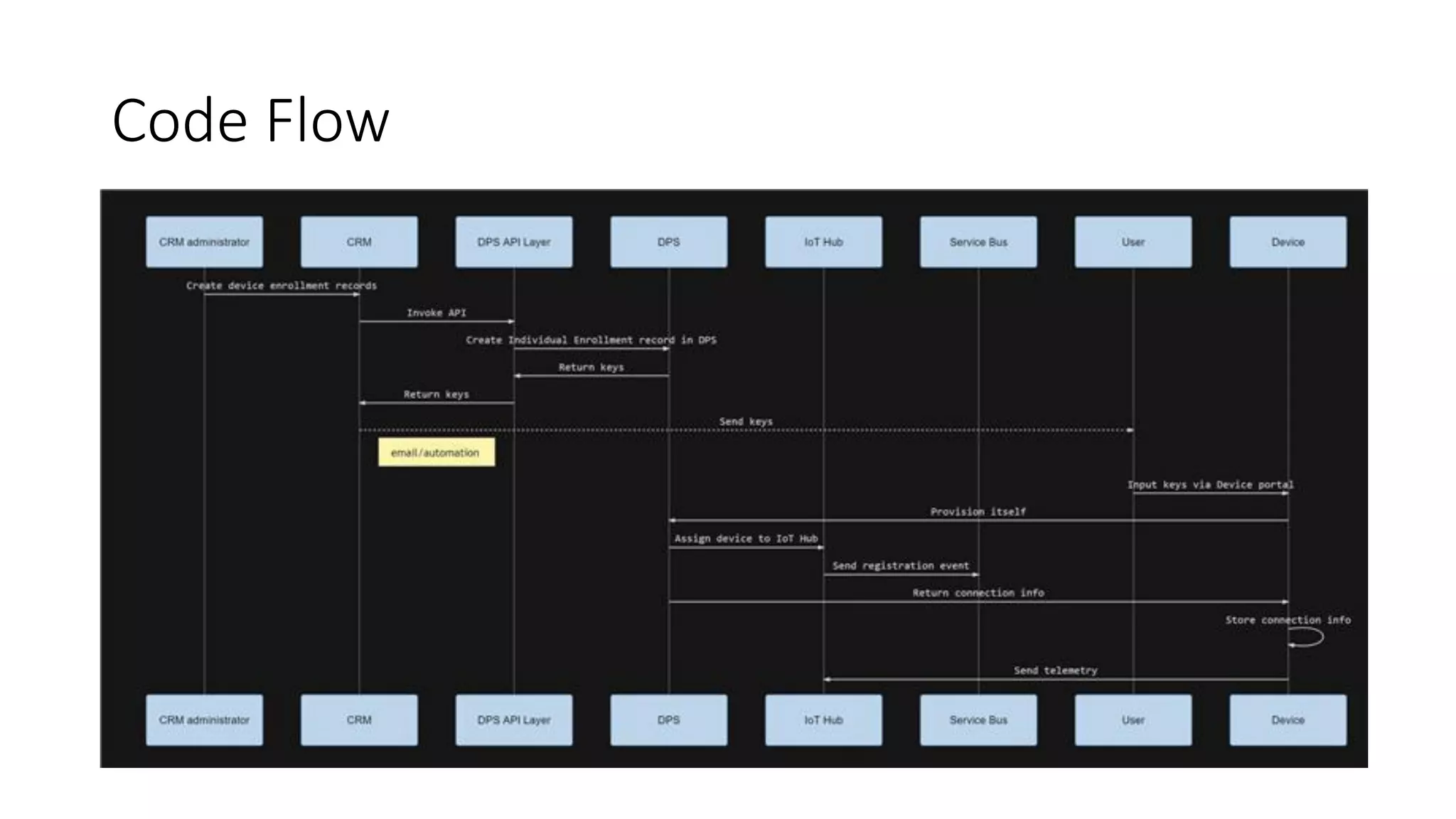
The document discusses the challenges of device provisioning in IoT, highlighting the complexities of supply chains and the manual nature of initial configurations. It describes a two-step provisioning process involving enrollment and registration, and outlines features of the Device Provisioning Service (DPS) such as support for multiple authentication methods and device management capabilities. Additionally, it offers a demo for provisioning a device using symmetric key attestation.