The document discusses authentication, authorization, and auditing for access to patient medical records. It involves:
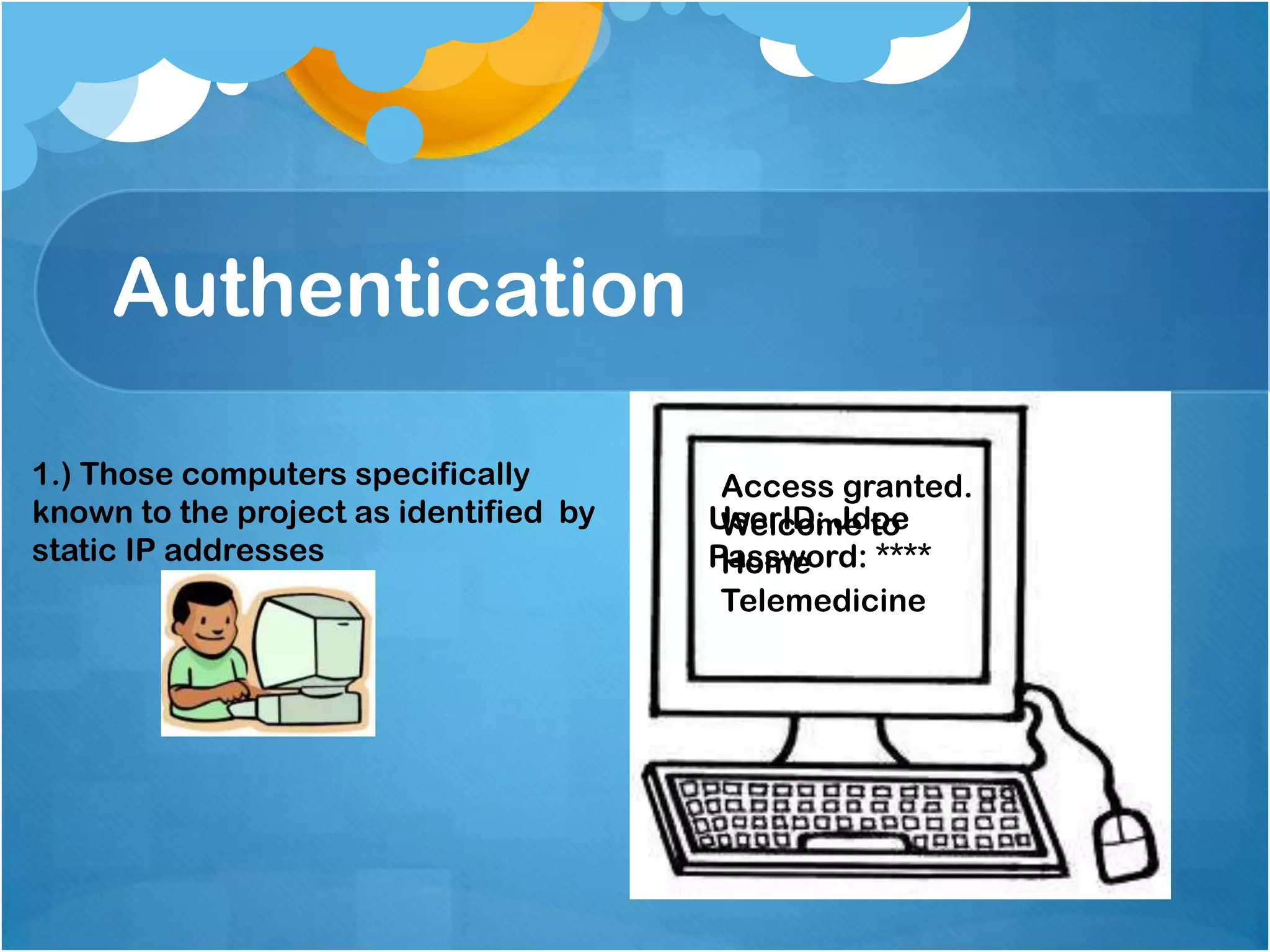
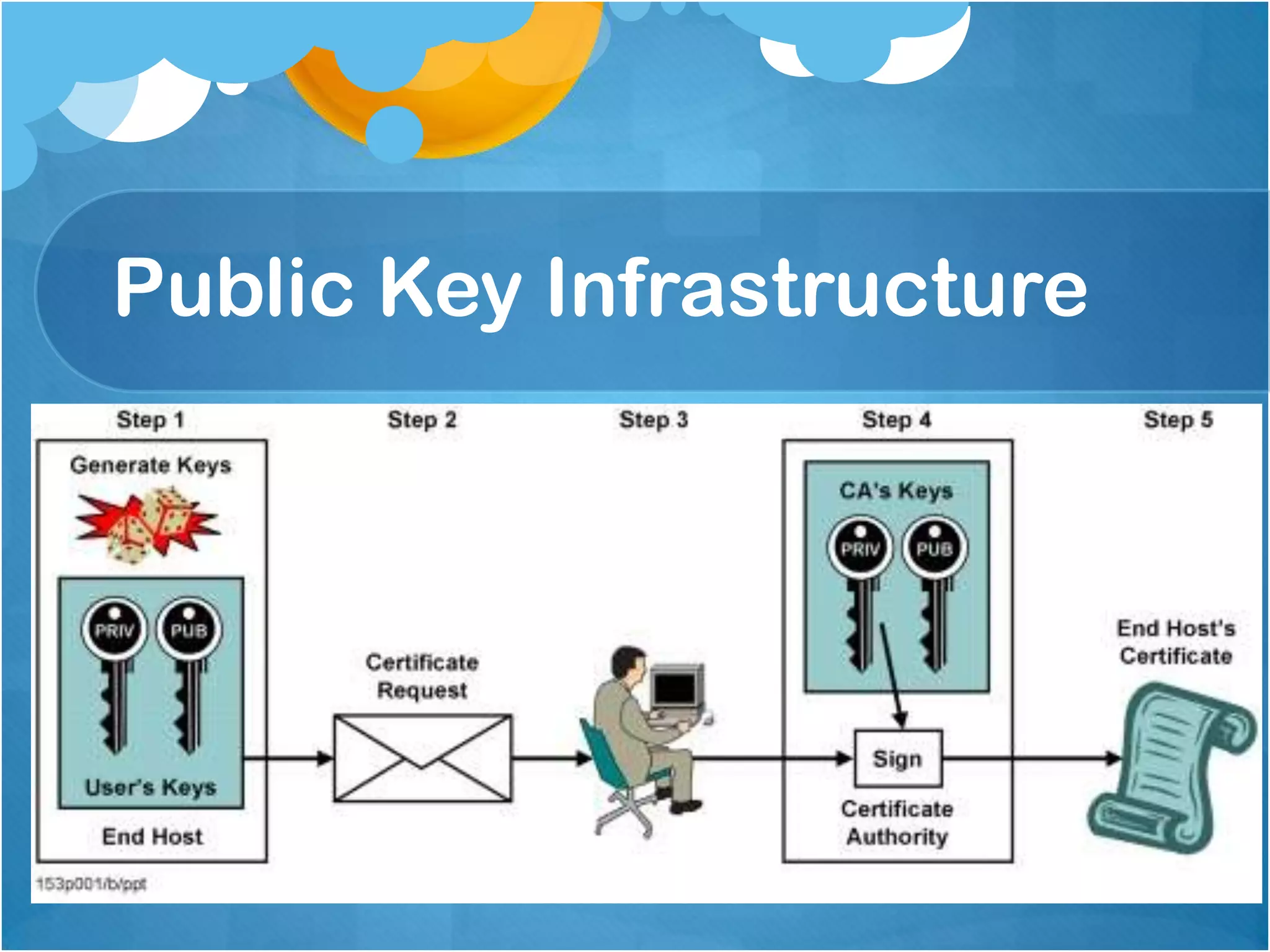
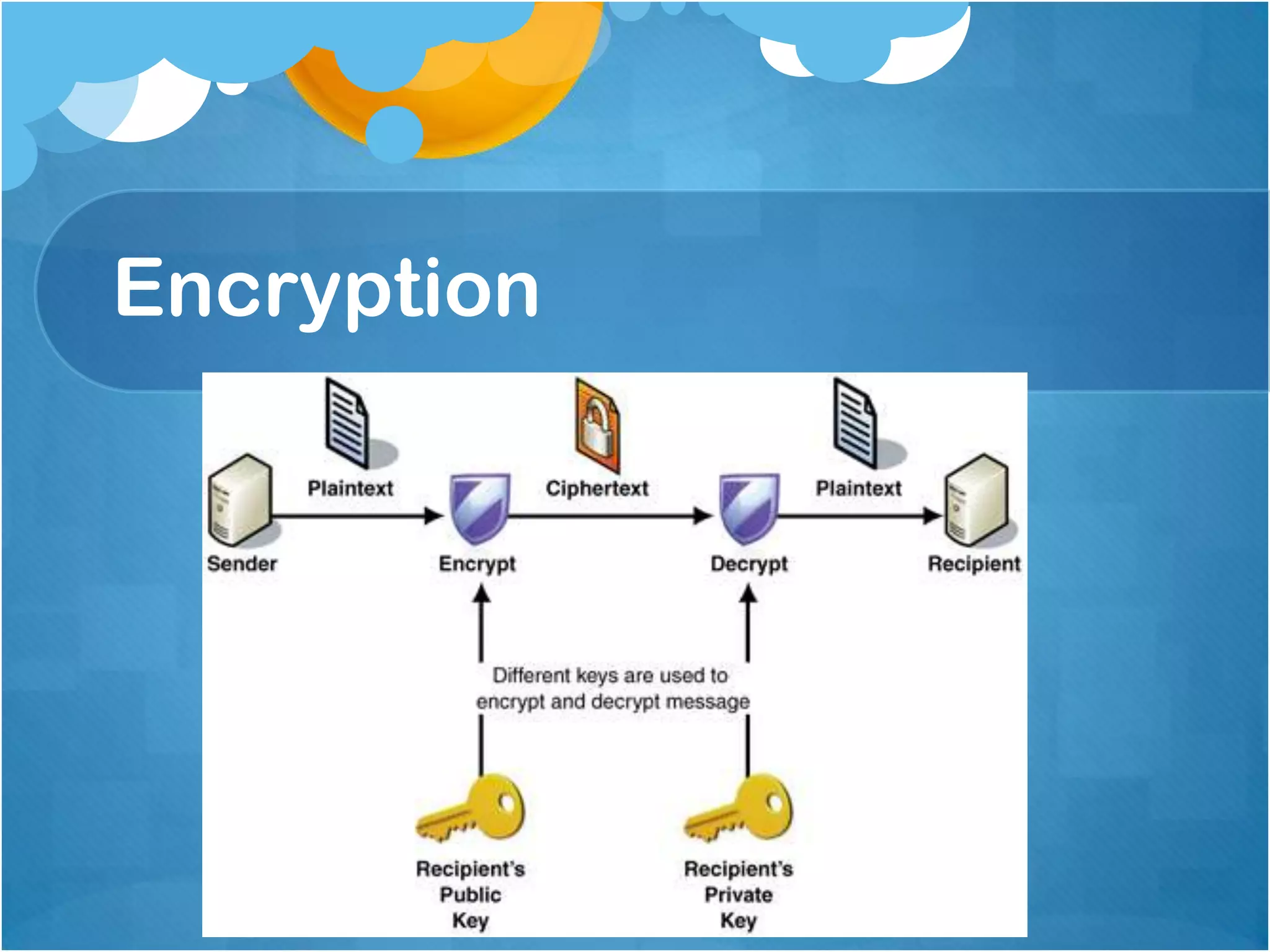
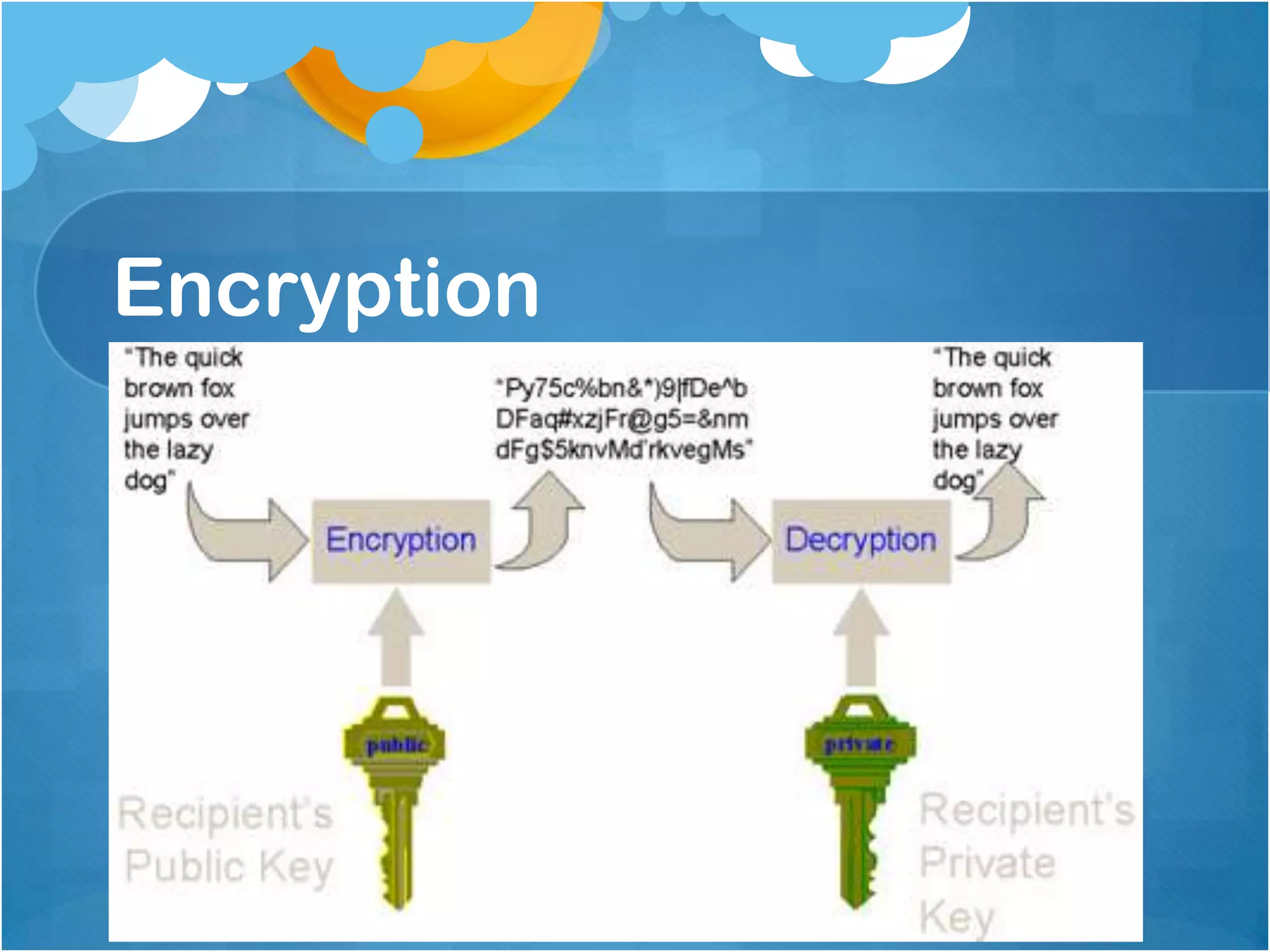
1) Authenticating users based on their computer's IP address, with static addresses having full access and others requiring additional authentication like public key infrastructure.
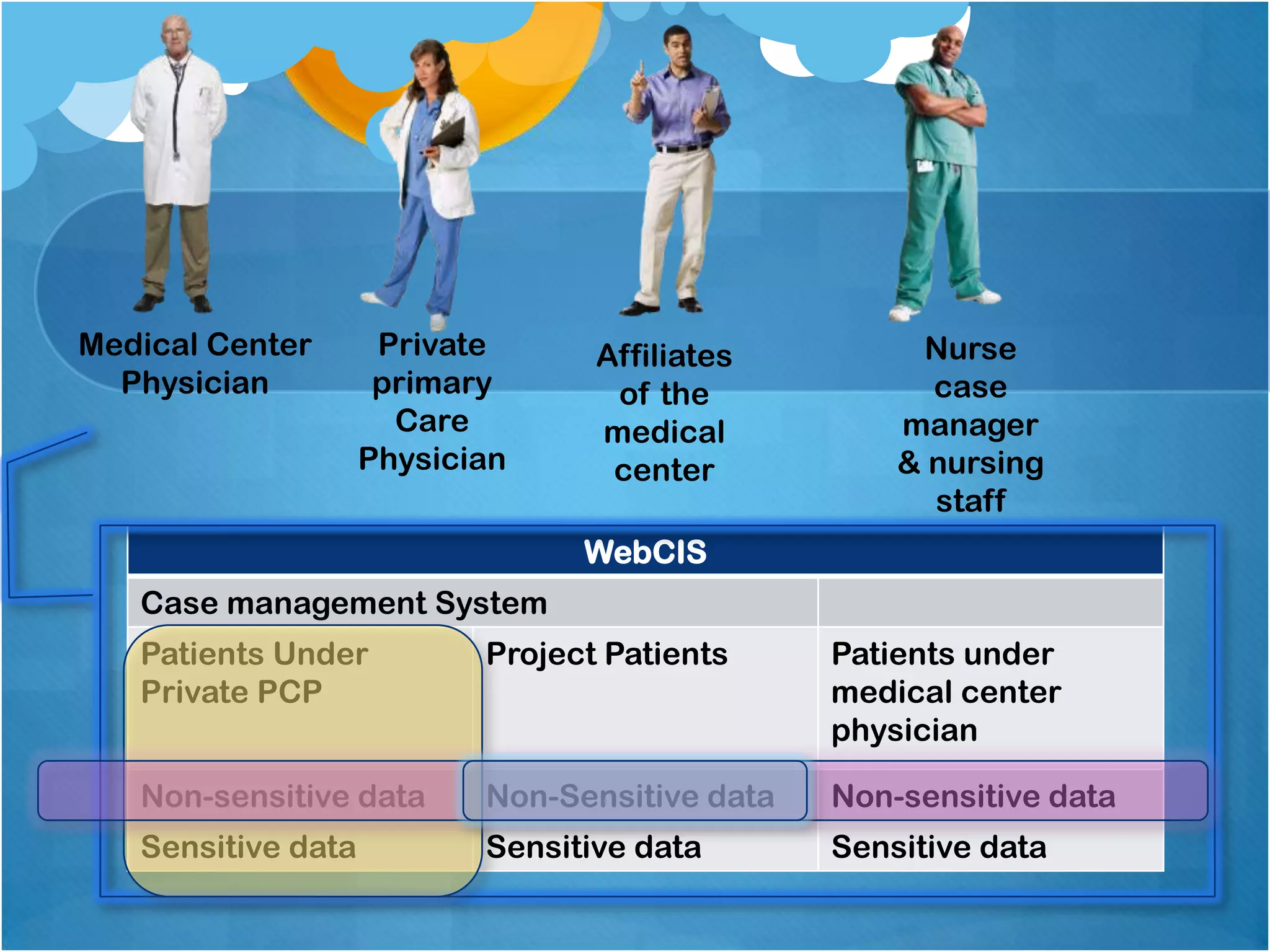
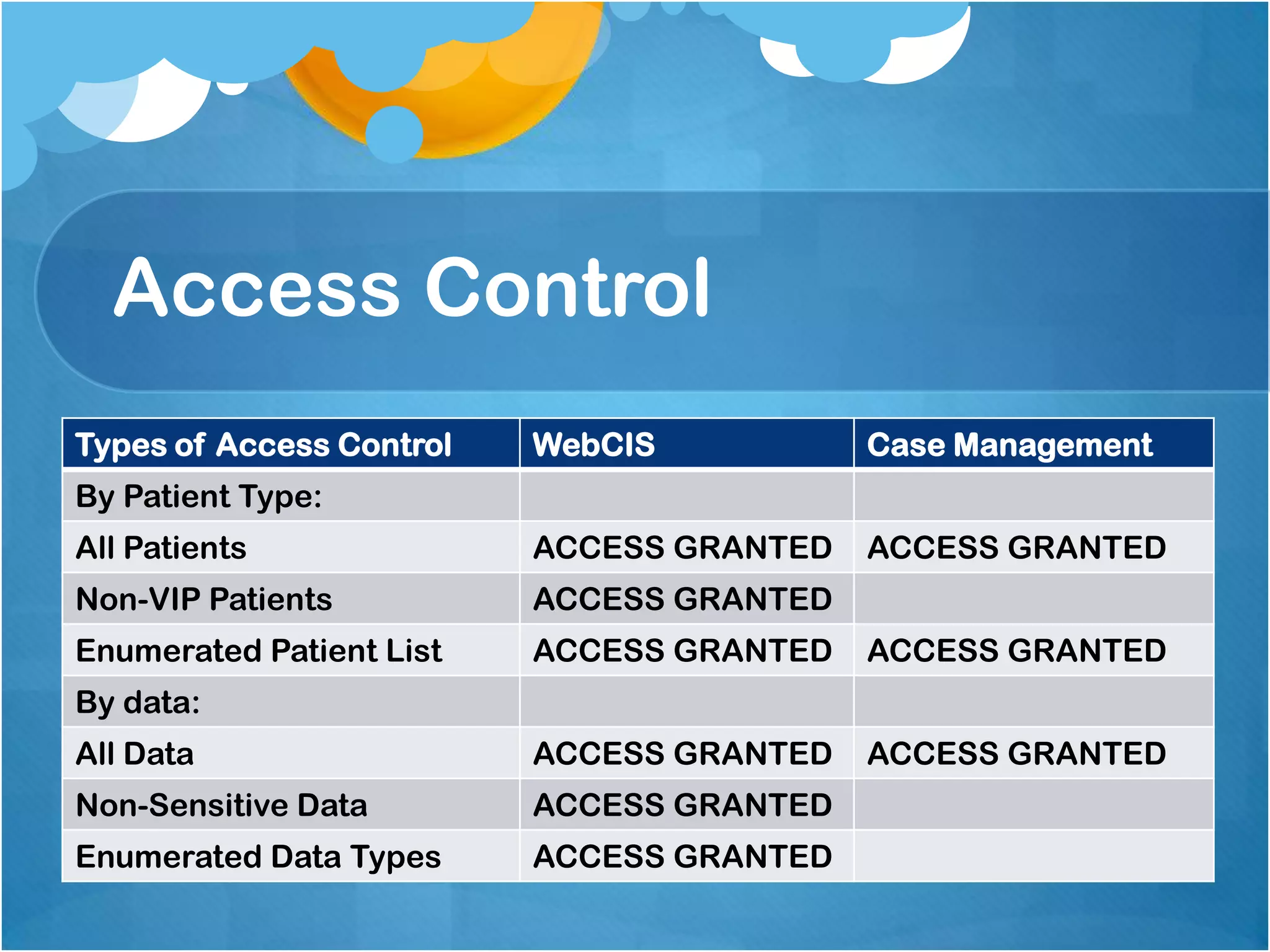
2) Authorizing access to patient data based on three criteria and the user's role, with physicians having full access, private physicians limited access to their patients, and nurses/staff having access only to non-sensitive data.
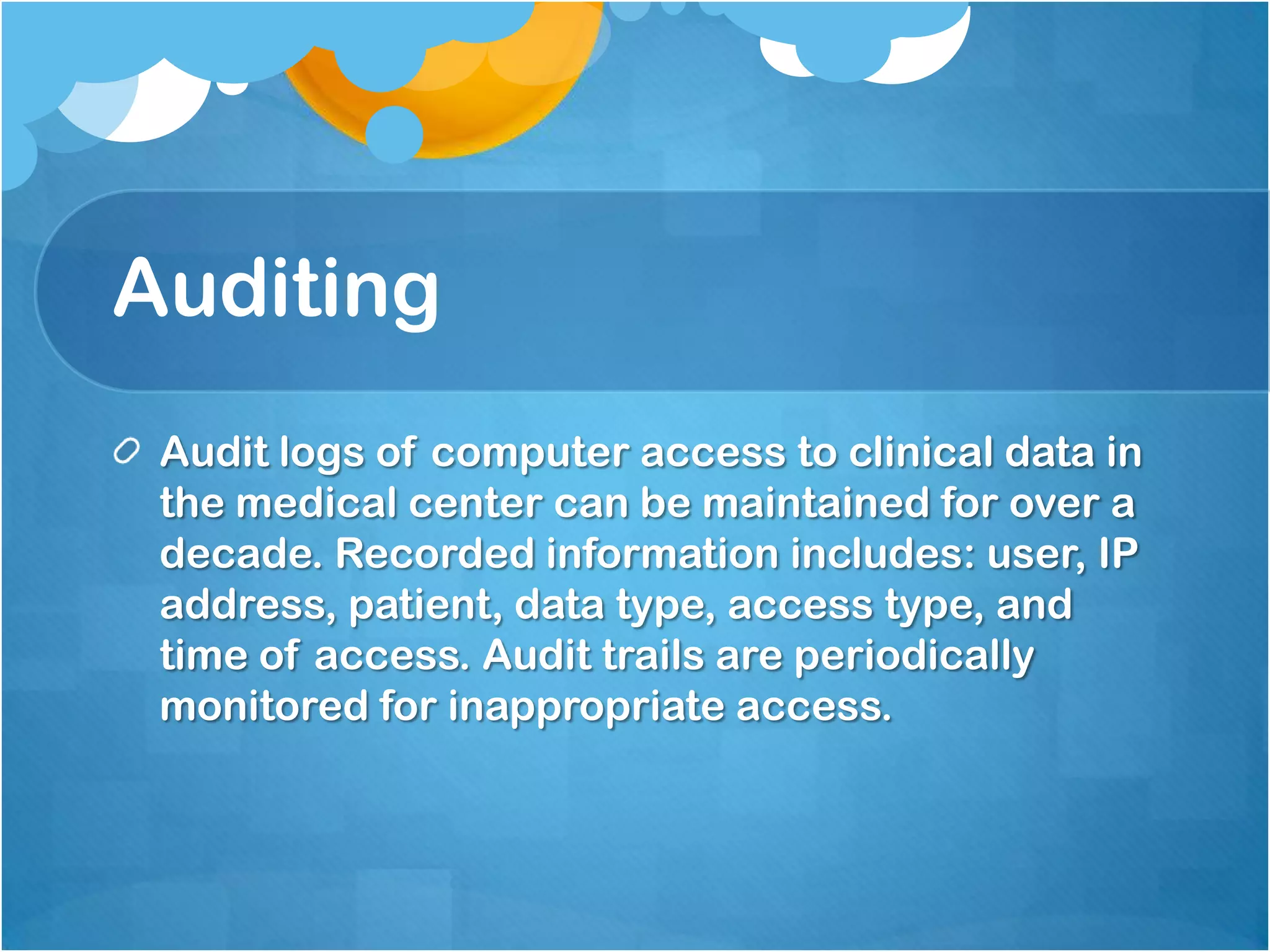
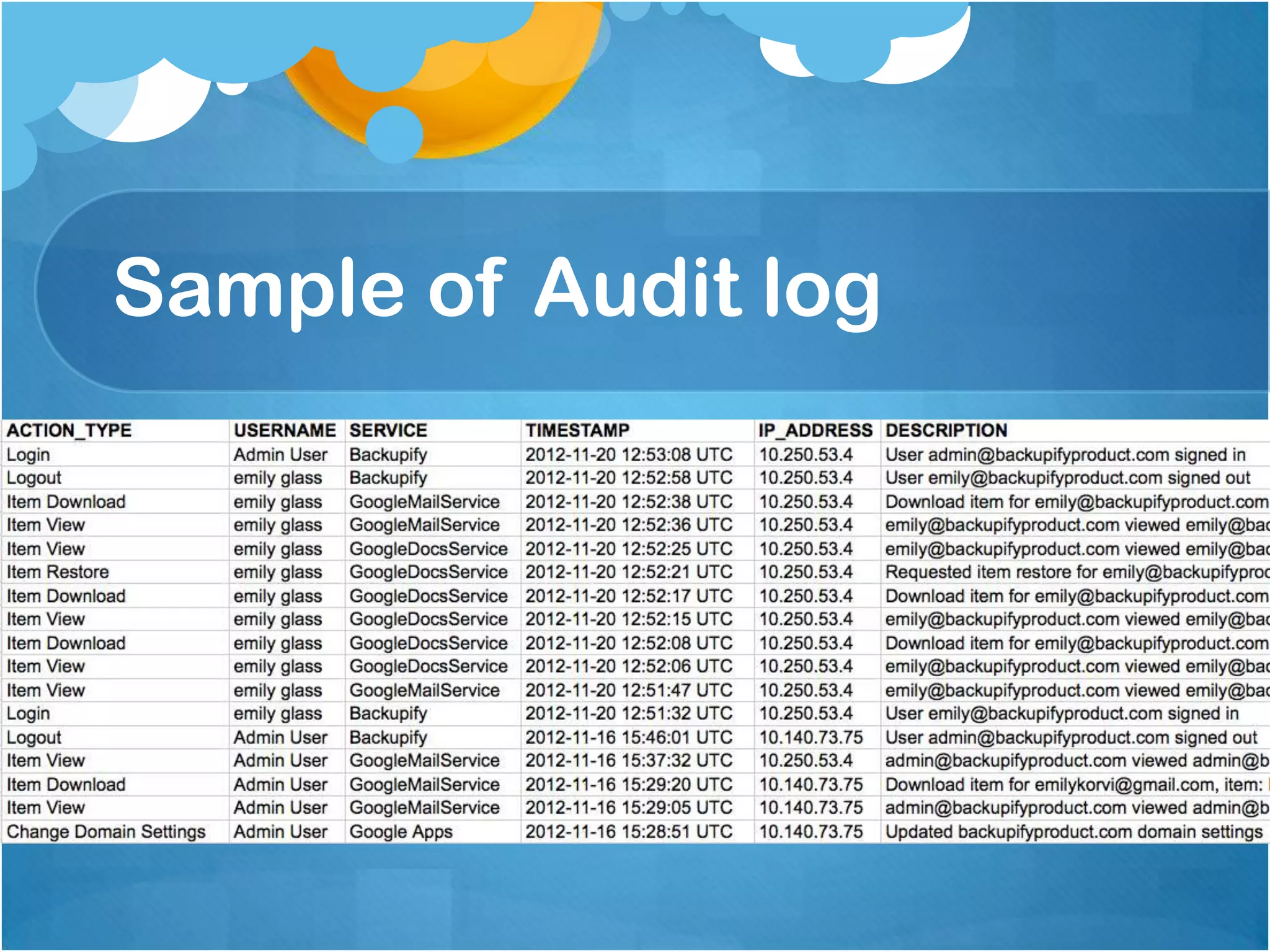
3) Maintaining audit logs of access for over a decade to monitor for inappropriate access, with study patients flagged for easier auditing.