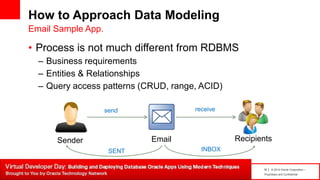
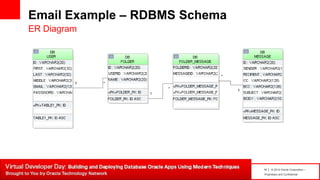
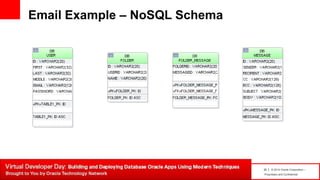
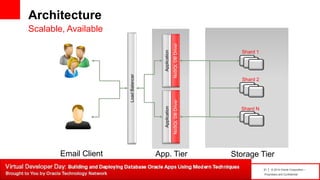
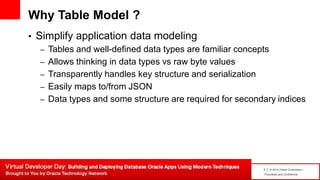
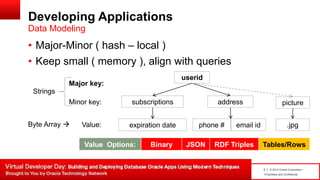
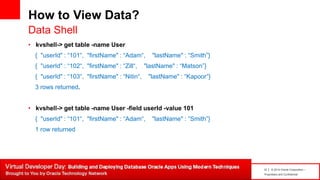
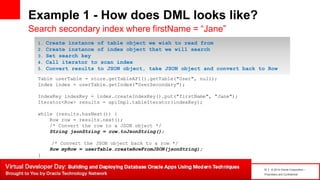
The document introduces table-based data modeling features for Oracle NoSQL Database. It discusses using tables to simplify application data modeling with familiar concepts like tables and data types. Examples show how to model user and email data using tables, including defining the schema using DDL, querying the data using DML, and indexing the tables. The document also provides an example of modeling user and email data from an email client application to illustrate how to approach data modeling.




![8 | © 2014 Oracle Corporation –
Proprietary and Confidential
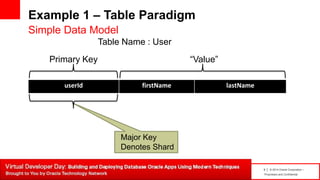
Example 1 – Key/Value Paradigm
Simple Data Model
Key Space : /user/userId
Value : {
“name" : “User",
"namespace" : "com.company. avro",
"type" : "record",
"fields": [
{"name": “userId", "type": “Integer", "default": 0},
{"name": “firstName", "type": “String", "default": ""},
{"name": “lastName", "type": “String", "default": ""}
]
}](https://image.slidesharecdn.com/applicationdevelopmentwithoraclenosqldatabase3-140416180331-phpapp02/85/Application-development-with-Oracle-NoSQL-Database-3-0-7-320.jpg)
![11 | © 2014 Oracle Corporation –
Proprietary and Confidential
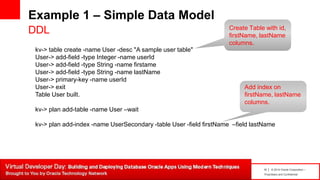
How to Describe It ?
DDL
kv-> show tables -name User
{ "type" : "table",
“name" : "User", "id" : "r",
"description" : “A sample user table”,
"shardKey" : [ "userId" ],
"primaryKey" : [ "userId" ],
"fields" : [
{ "name" : “userId", "type" : "Integer" },
{ "name" : "firstName", "type" : "String" },
{ "name" : "lastName", "type" : "String" }
] }](https://image.slidesharecdn.com/applicationdevelopmentwithoraclenosqldatabase3-140416180331-phpapp02/85/Application-development-with-Oracle-NoSQL-Database-3-0-10-320.jpg)
![14 | © 2014 Oracle Corporation –
Proprietary and Confidential
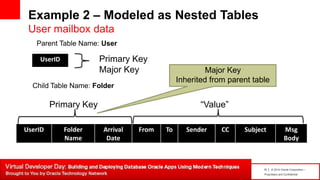
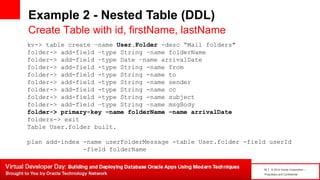
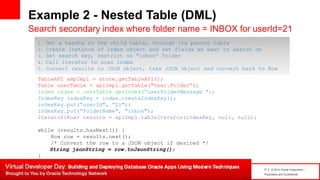
Example 2 – Major/Minor KV Paradigm
User mailbox data
Key Space : /user/id/-/folder/inbox/arrival date
/user/id/-/folder/deleted/arrival date
Value : {
“name" : "Email",
"namespace" : "com.companyX.email.avro",
"type" : "record",
"fields": [
{"name": "from", "type": "string", "default": ""},
{"name": "to", "type": "string", "default": ""},
{"name": "sender", "type": "string", "default": ""},
{"name": "cc", "type": "string", "default": ""},
{"name": "subject", "type": "string", "default": ""},
{“name”: “msgBody”, “type”: “string”, “default”: “”} ] }](https://image.slidesharecdn.com/applicationdevelopmentwithoraclenosqldatabase3-140416180331-phpapp02/85/Application-development-with-Oracle-NoSQL-Database-3-0-13-320.jpg)