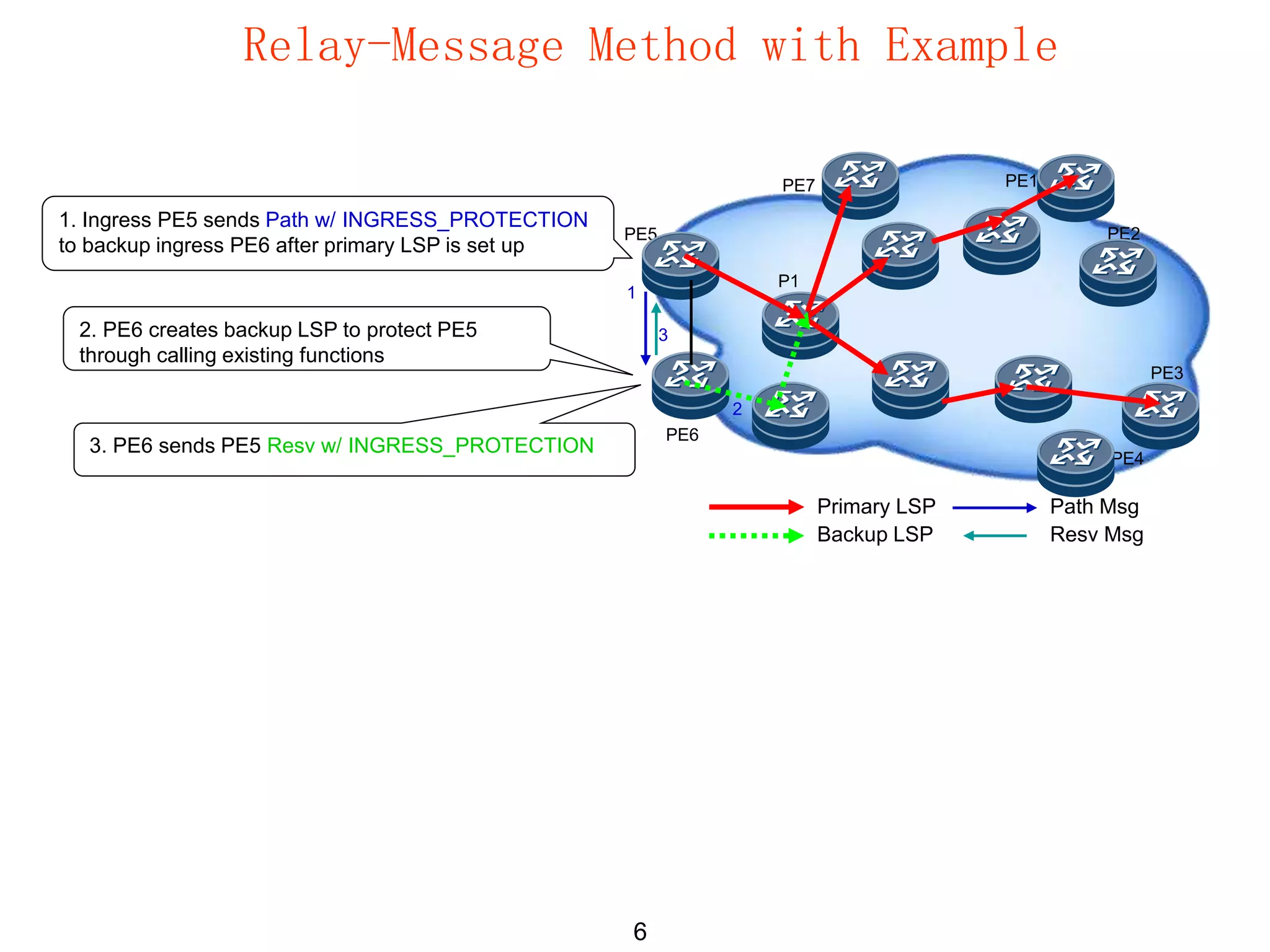
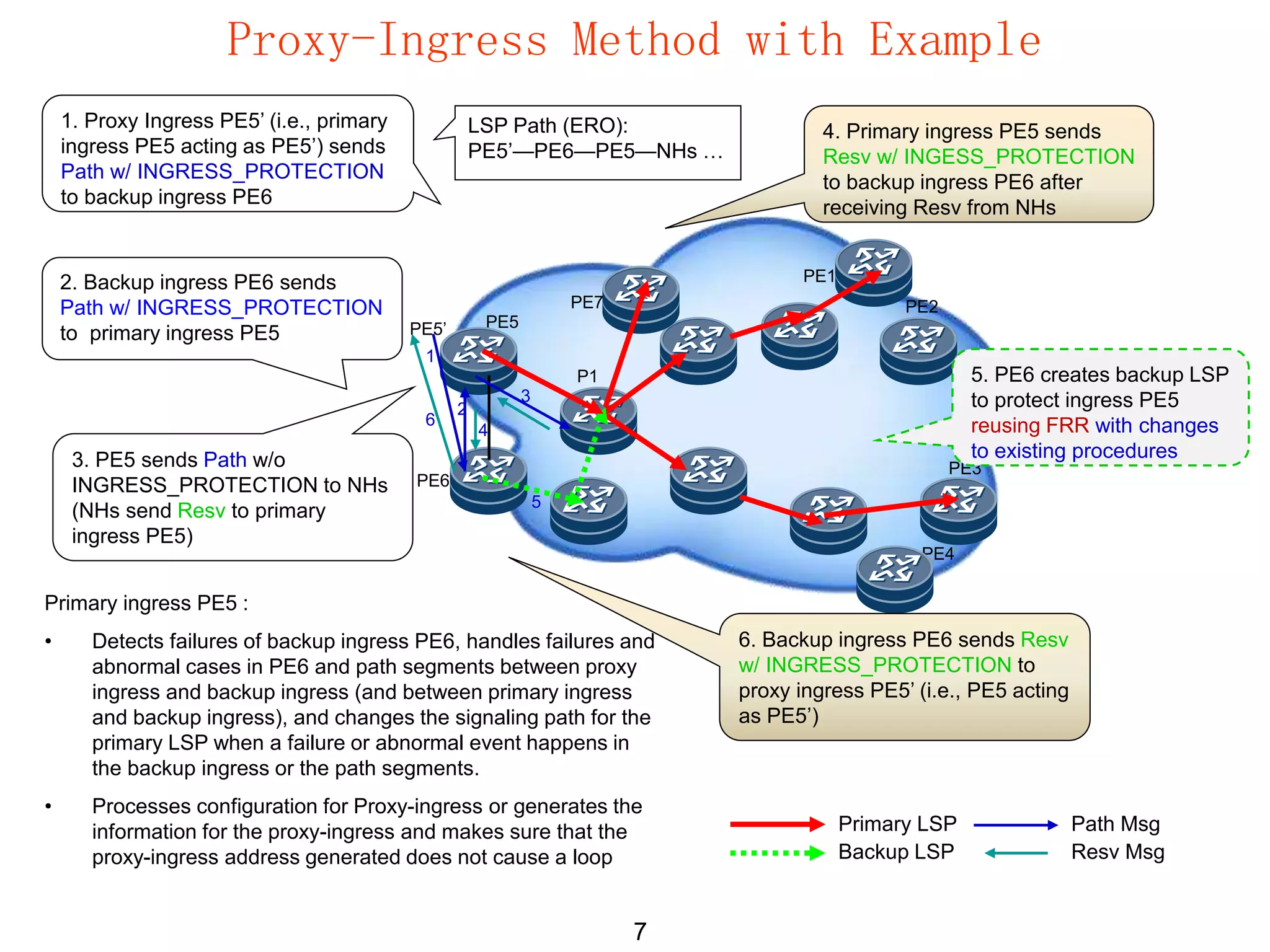
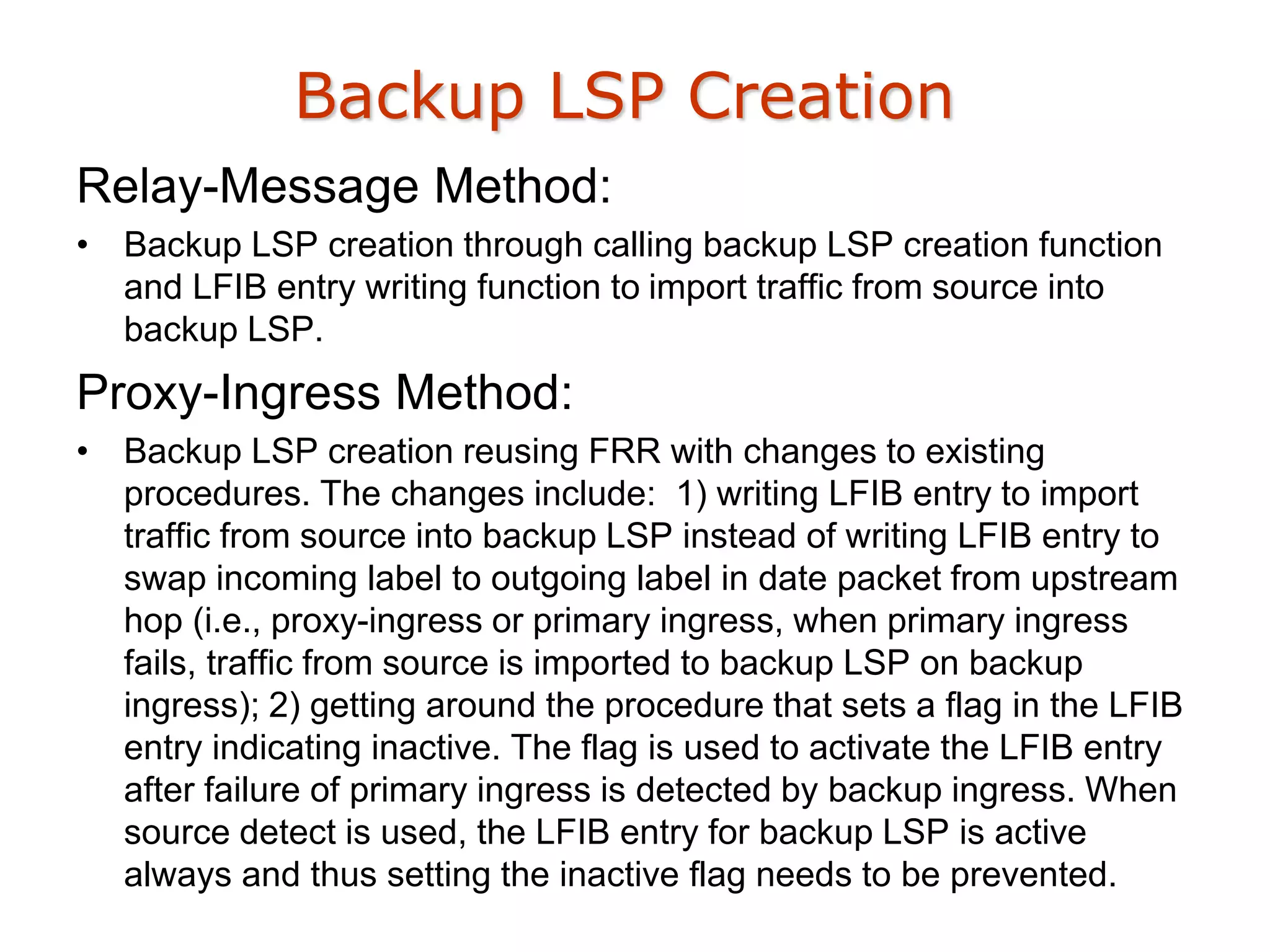
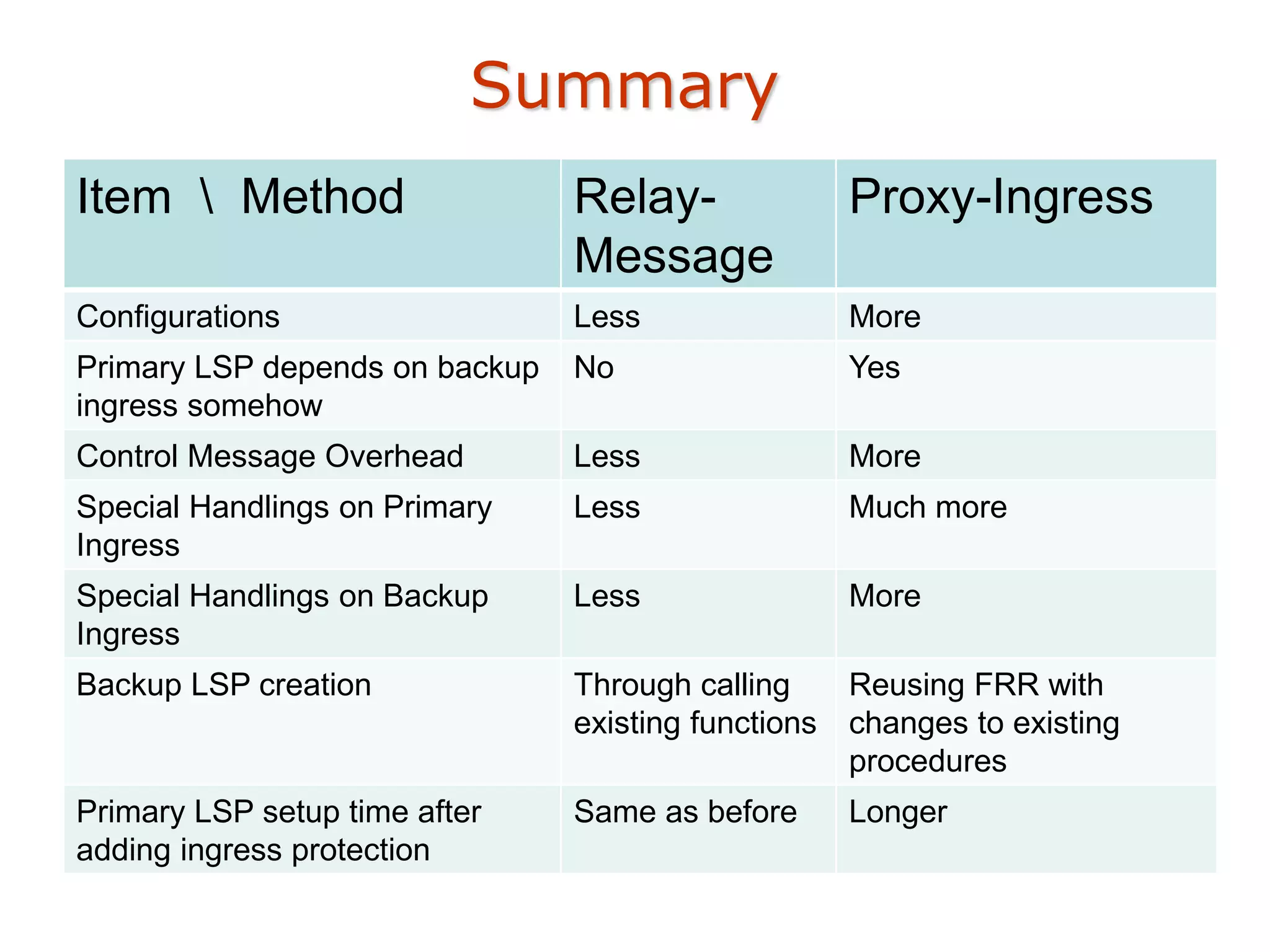
The document analyzes two methods, relay-message and proxy-ingress, for transferring ingress protection from primary to backup ingress, detailing their processes, changes, and implications. Relay-message allows the primary ingress to send paths with protection to the backup and vice versa, while proxy-ingress involves the primary ingress acting as a proxy to handle failures and establish paths. Key differences include the dependency of the primary LSP on the backup ingress in the proxy-ingress method and the associated message overhead and handling mechanisms for each method.