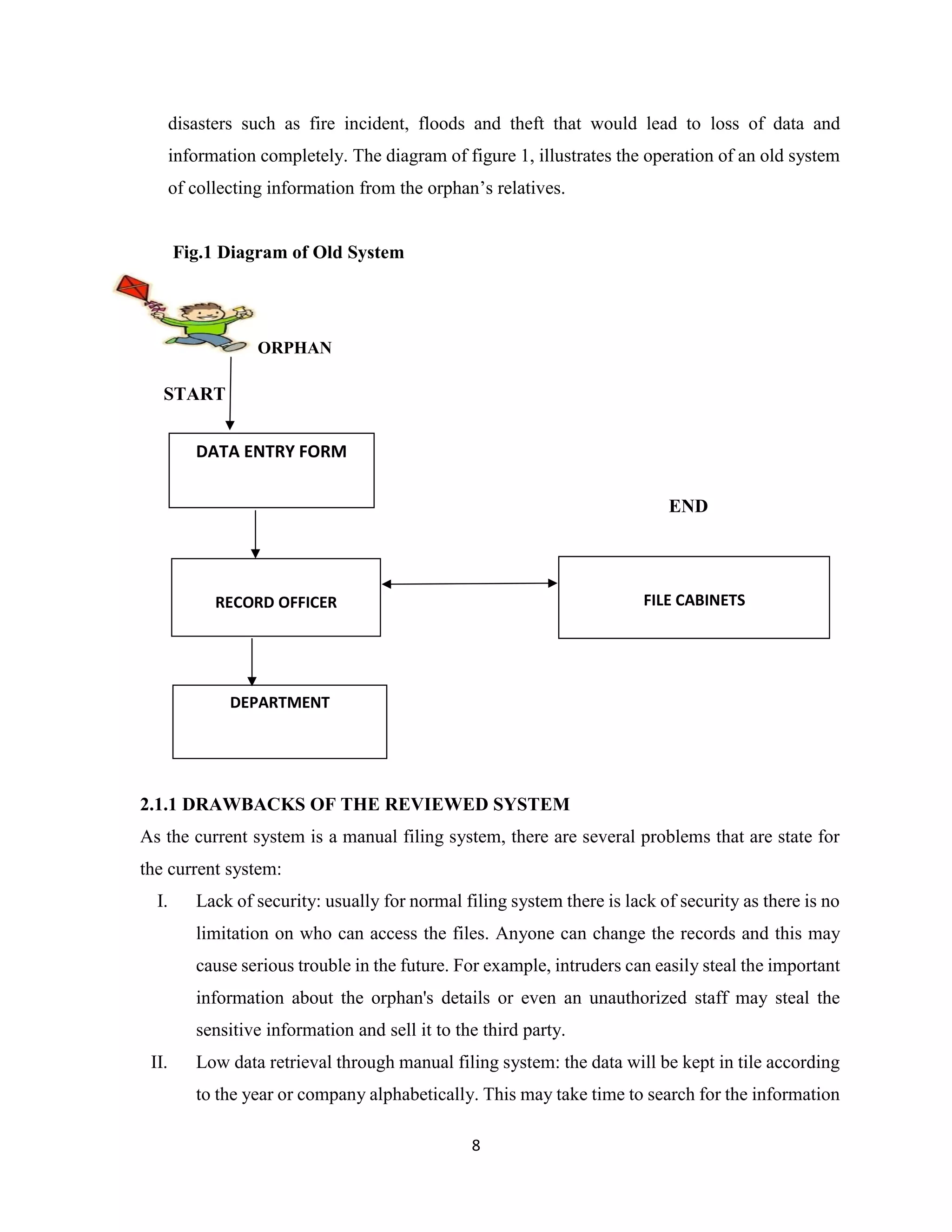
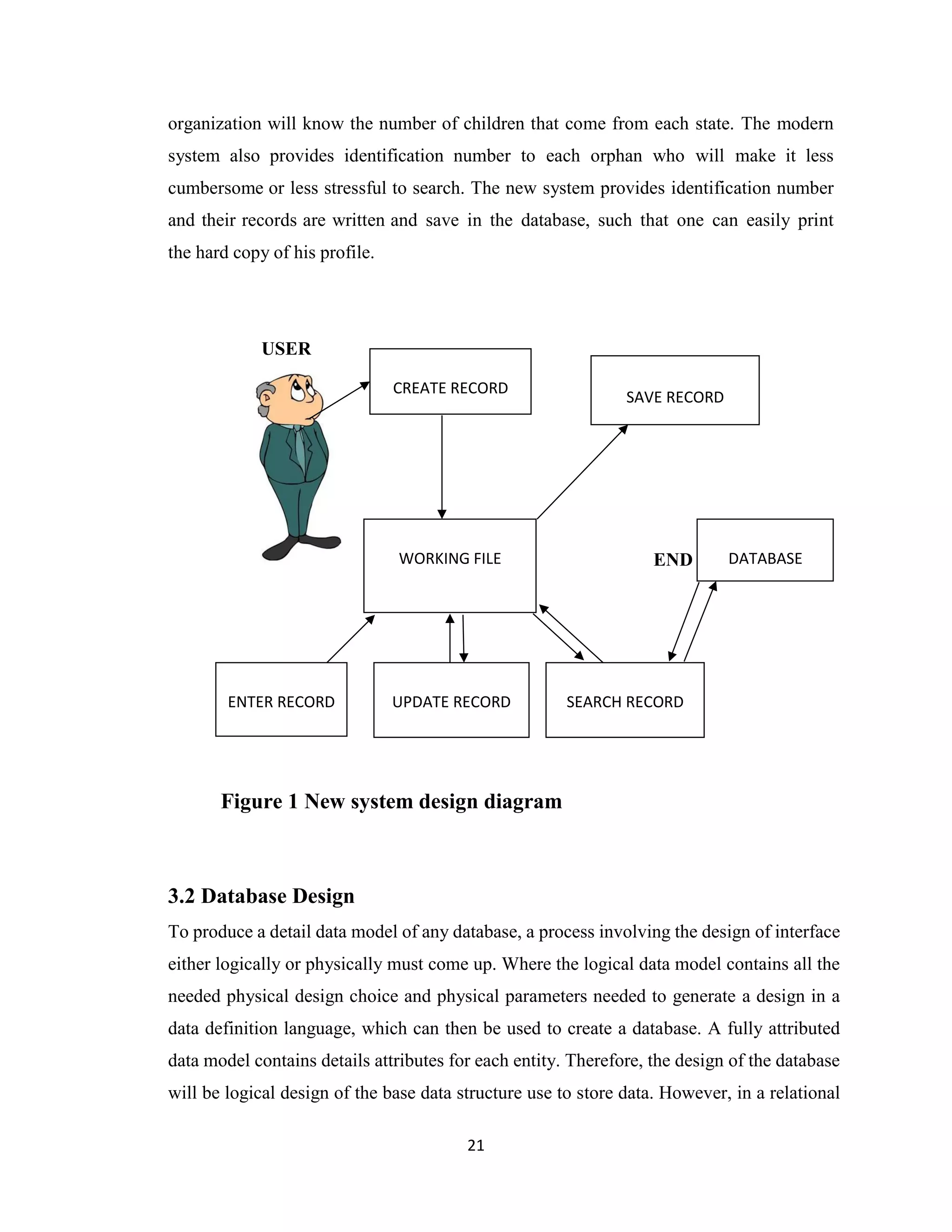
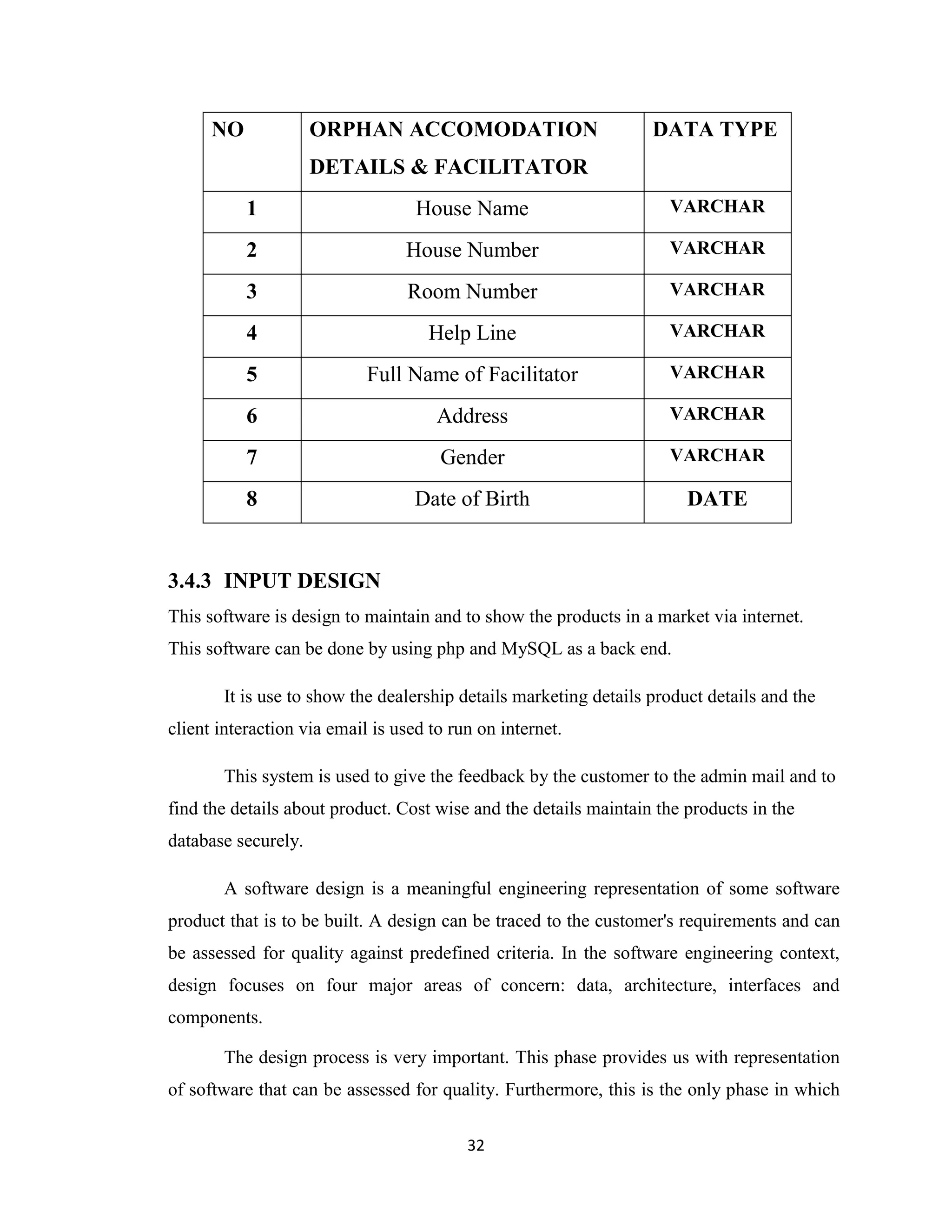
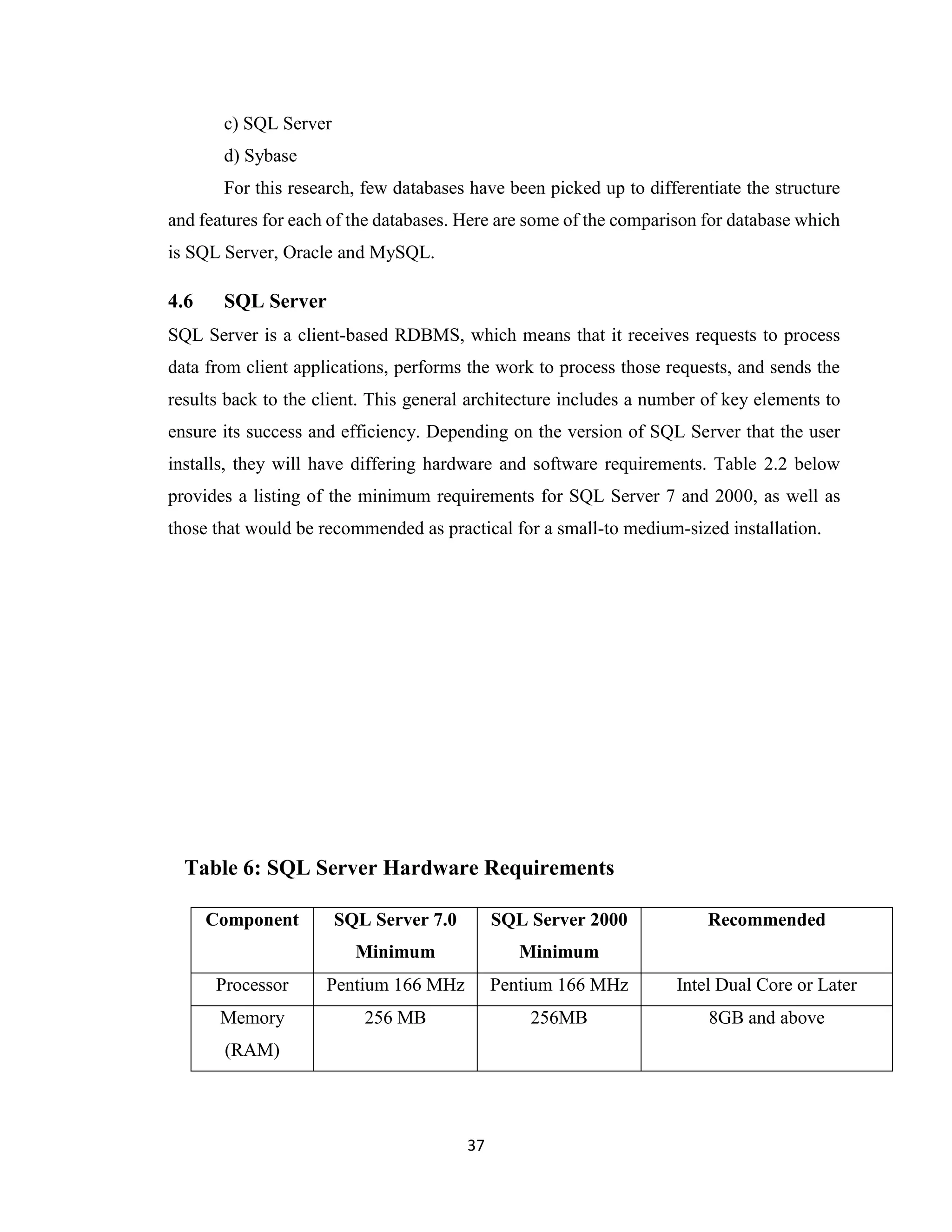
The project report discusses the development of an Orphanage Management Information System (OMIS) to transition from manual management to a computerized system, aimed at enhancing the registration and management of orphans at Flordibert Foundation in Ghana. It acknowledges various contributors to the project and outlines the difficulties faced with the existing manual system, including data redundancy and poor record management. The proposed system intends to streamline operations, improve data security, and provide a more efficient way to manage orphan records and staff information.