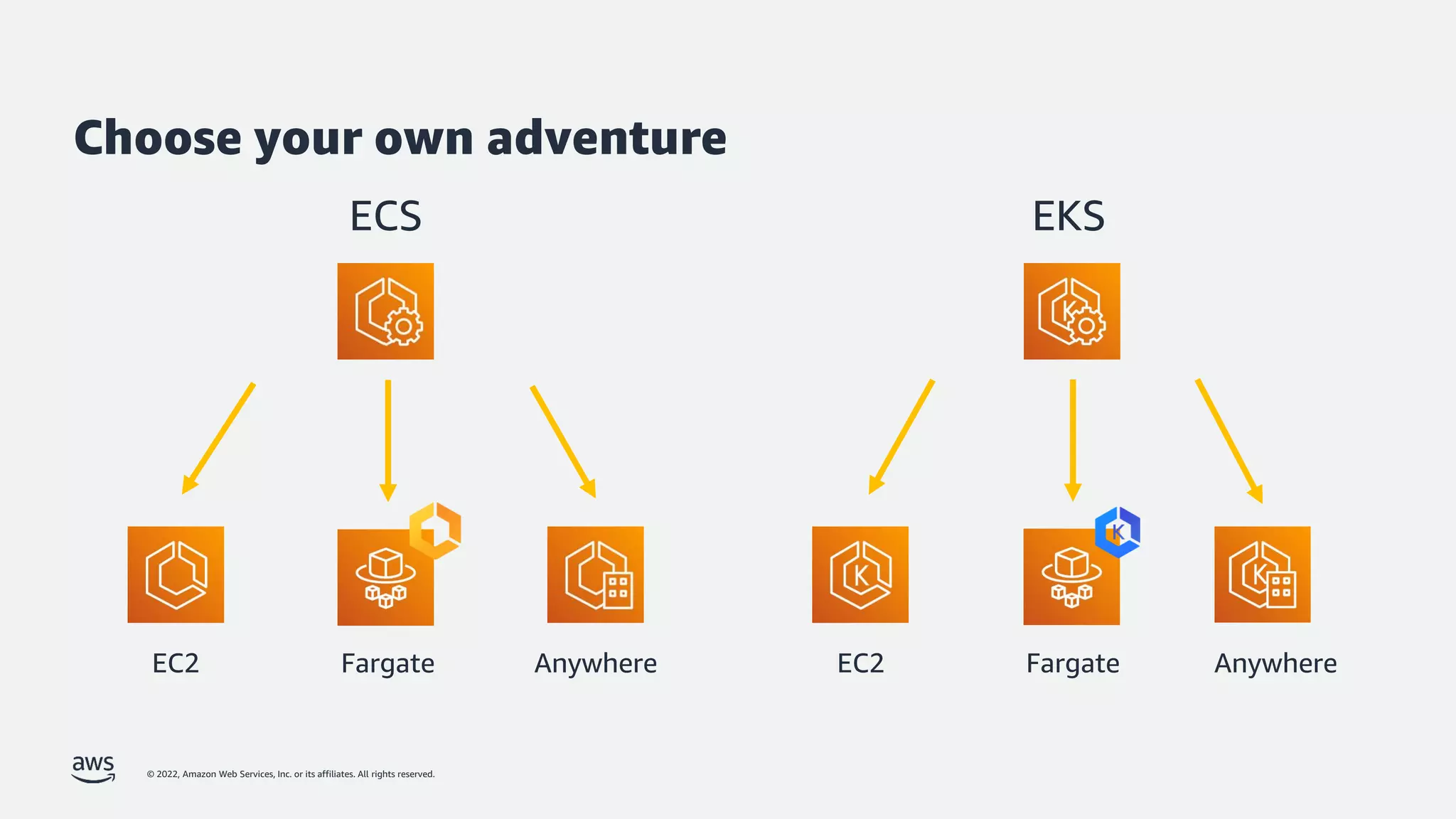
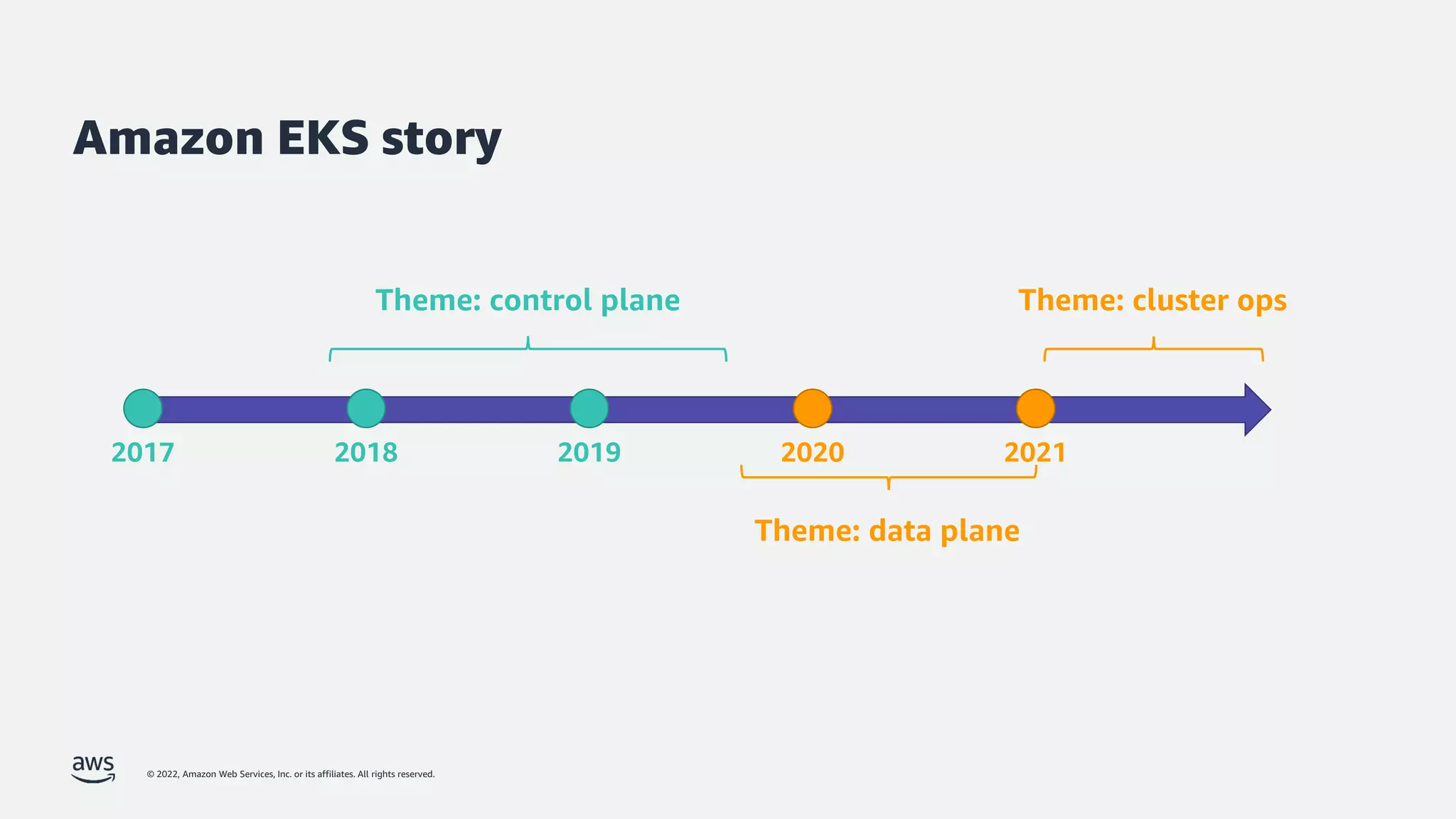
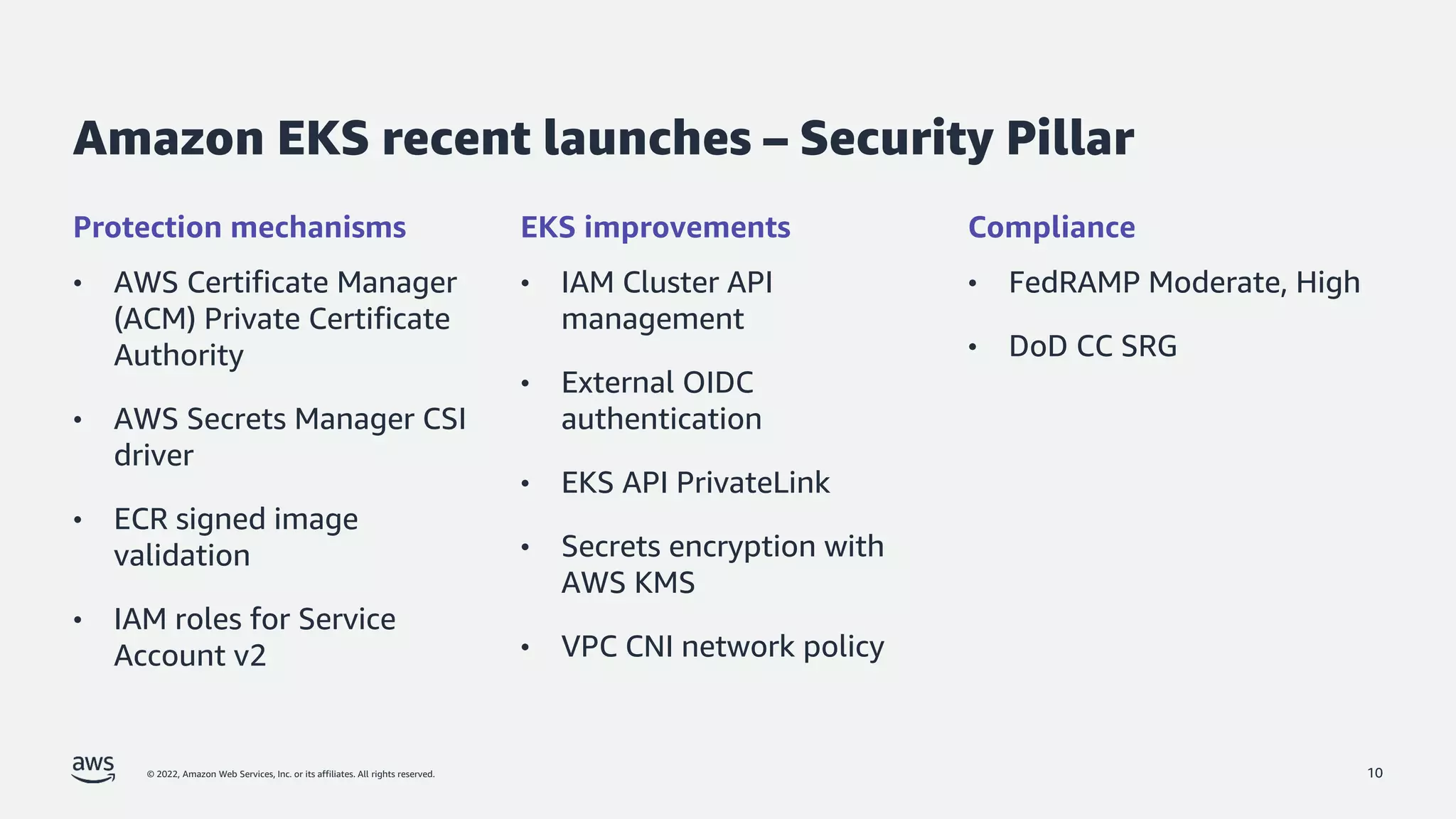
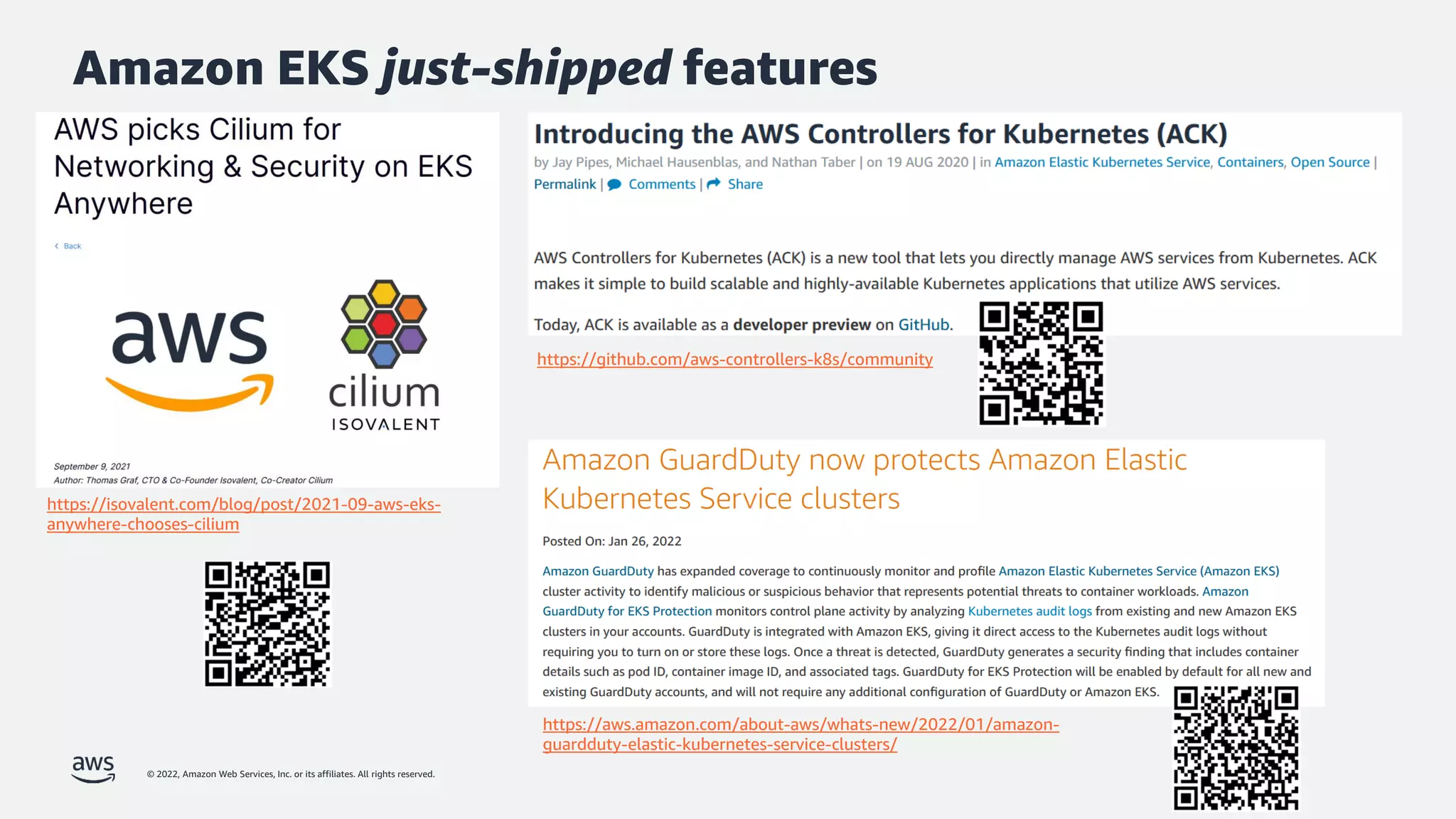
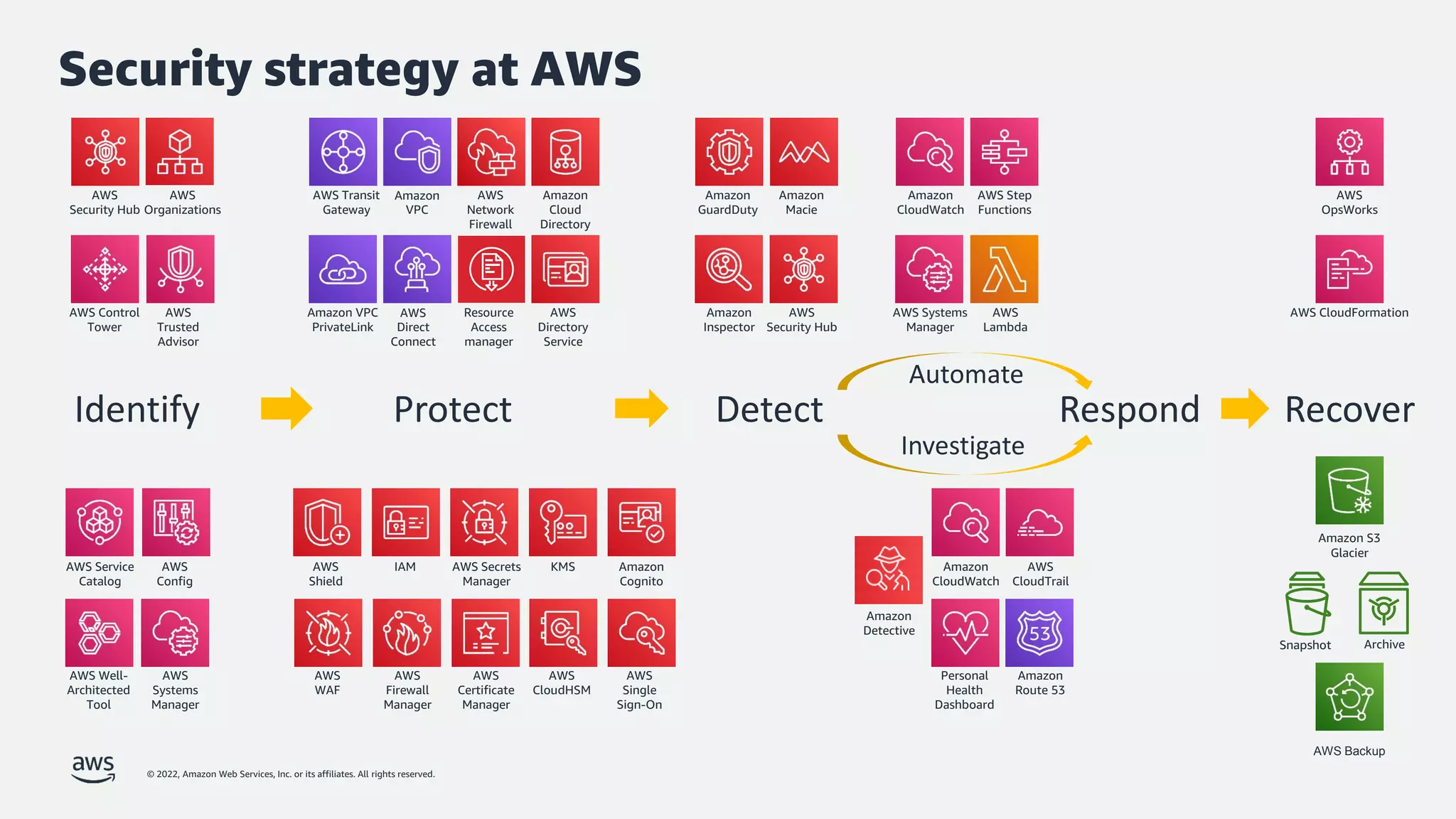
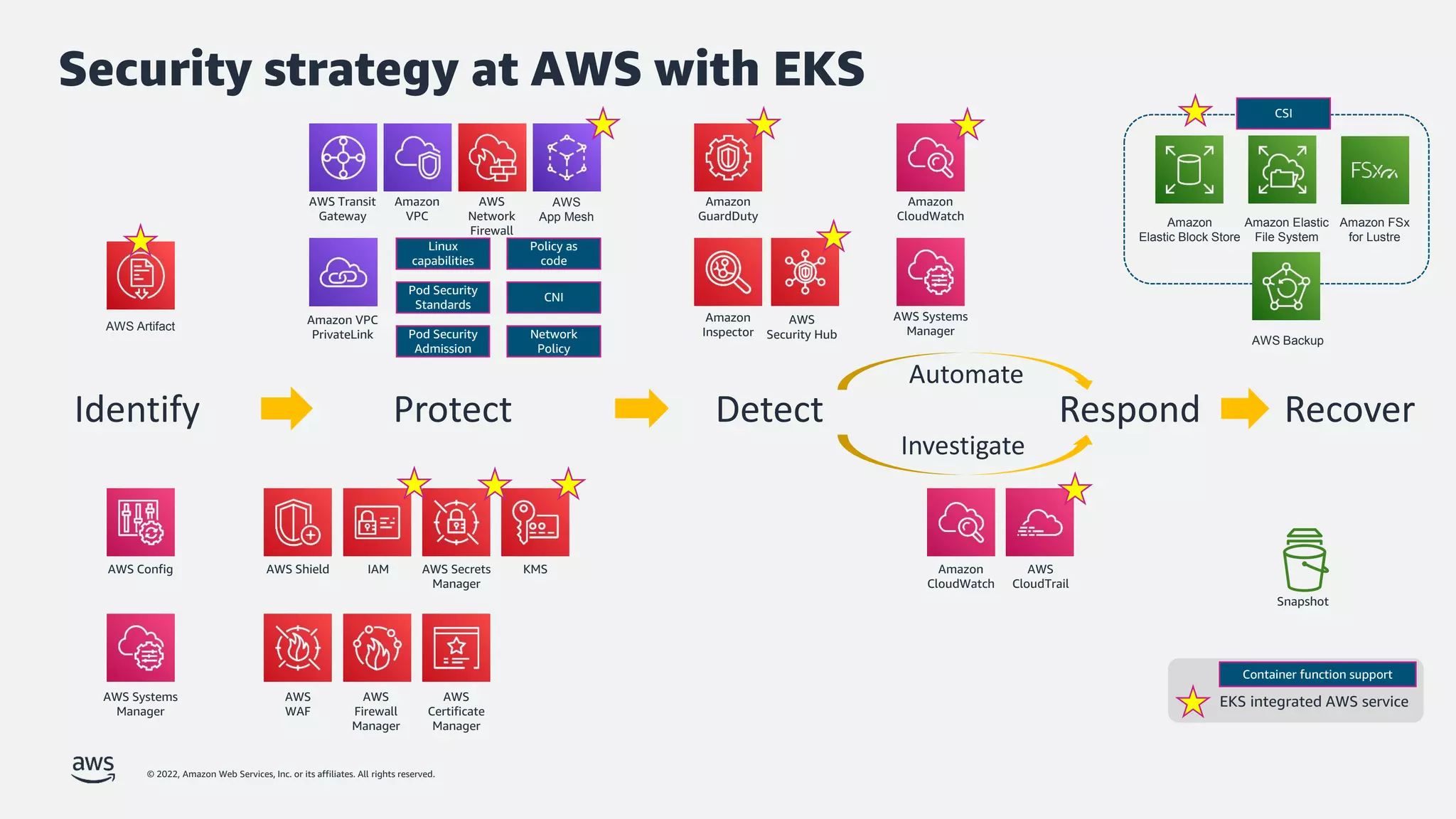
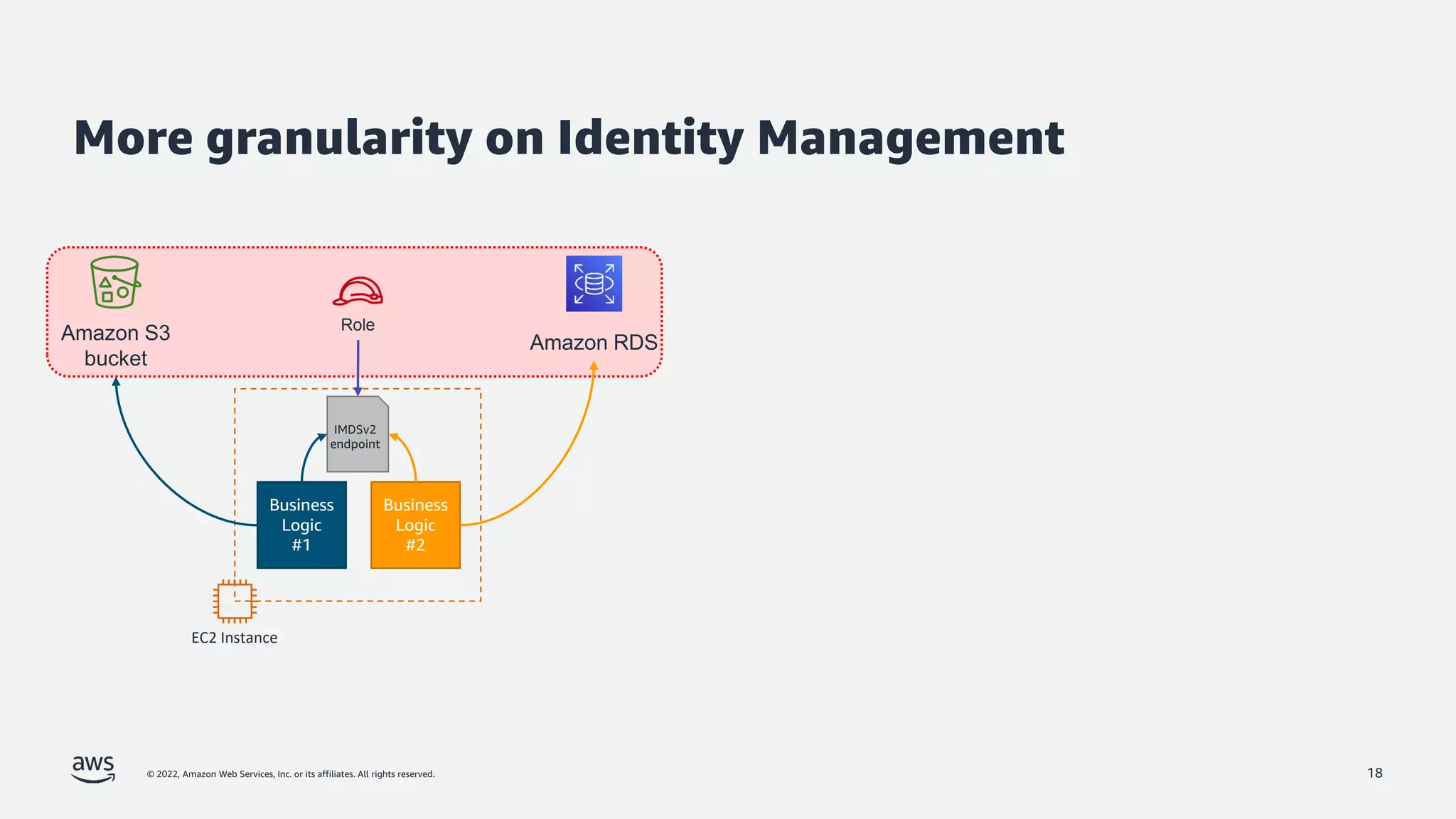
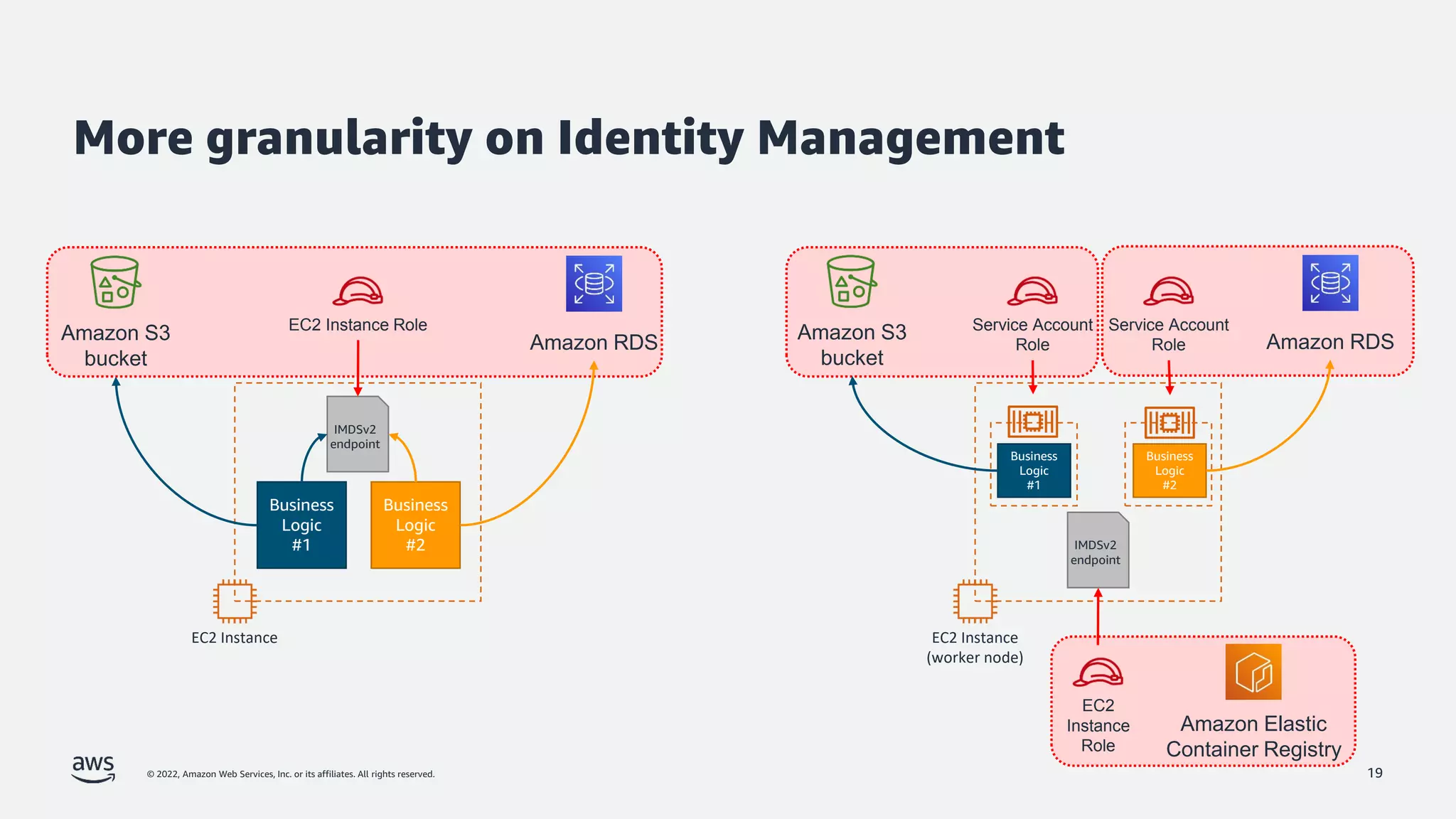
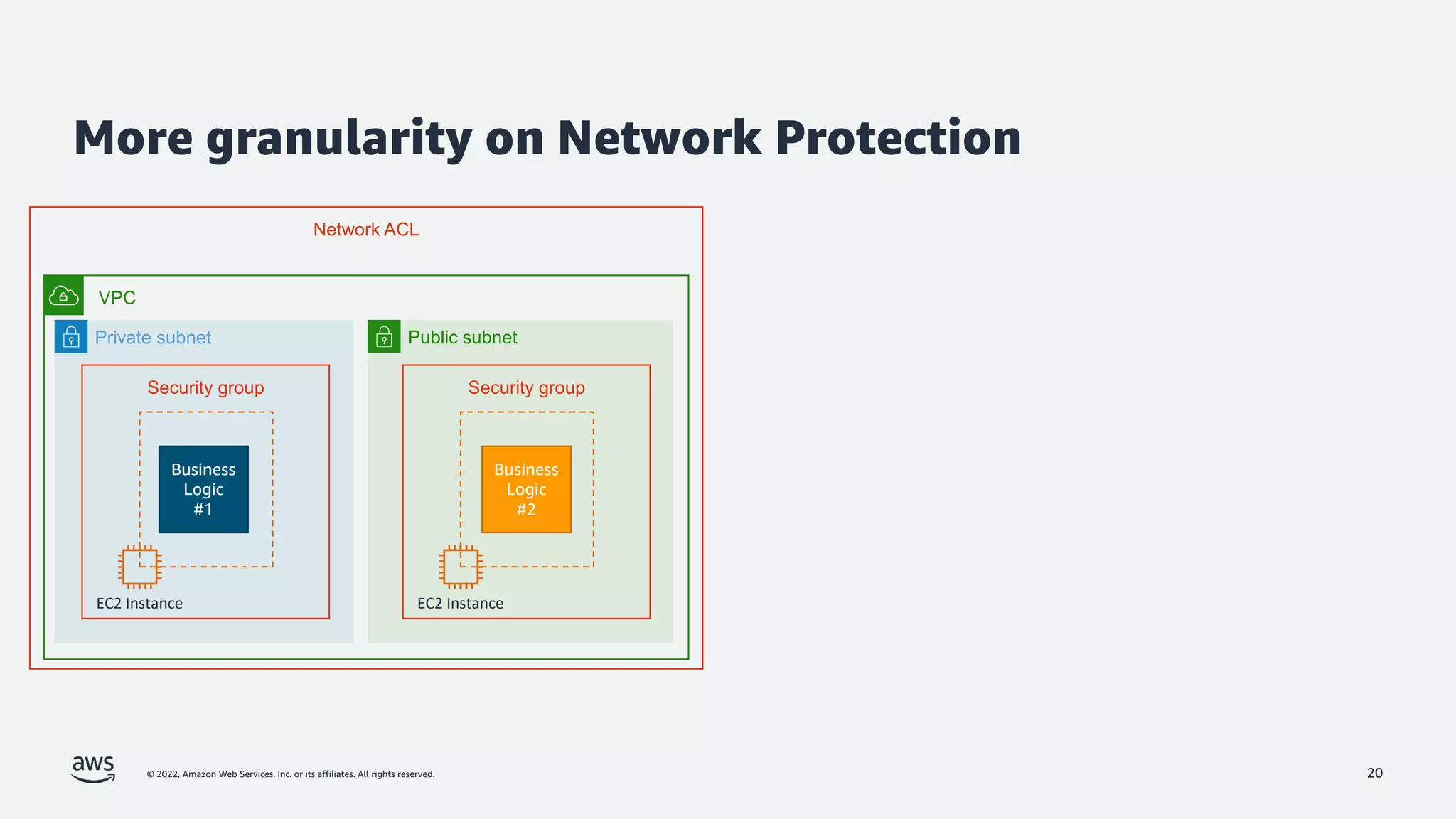
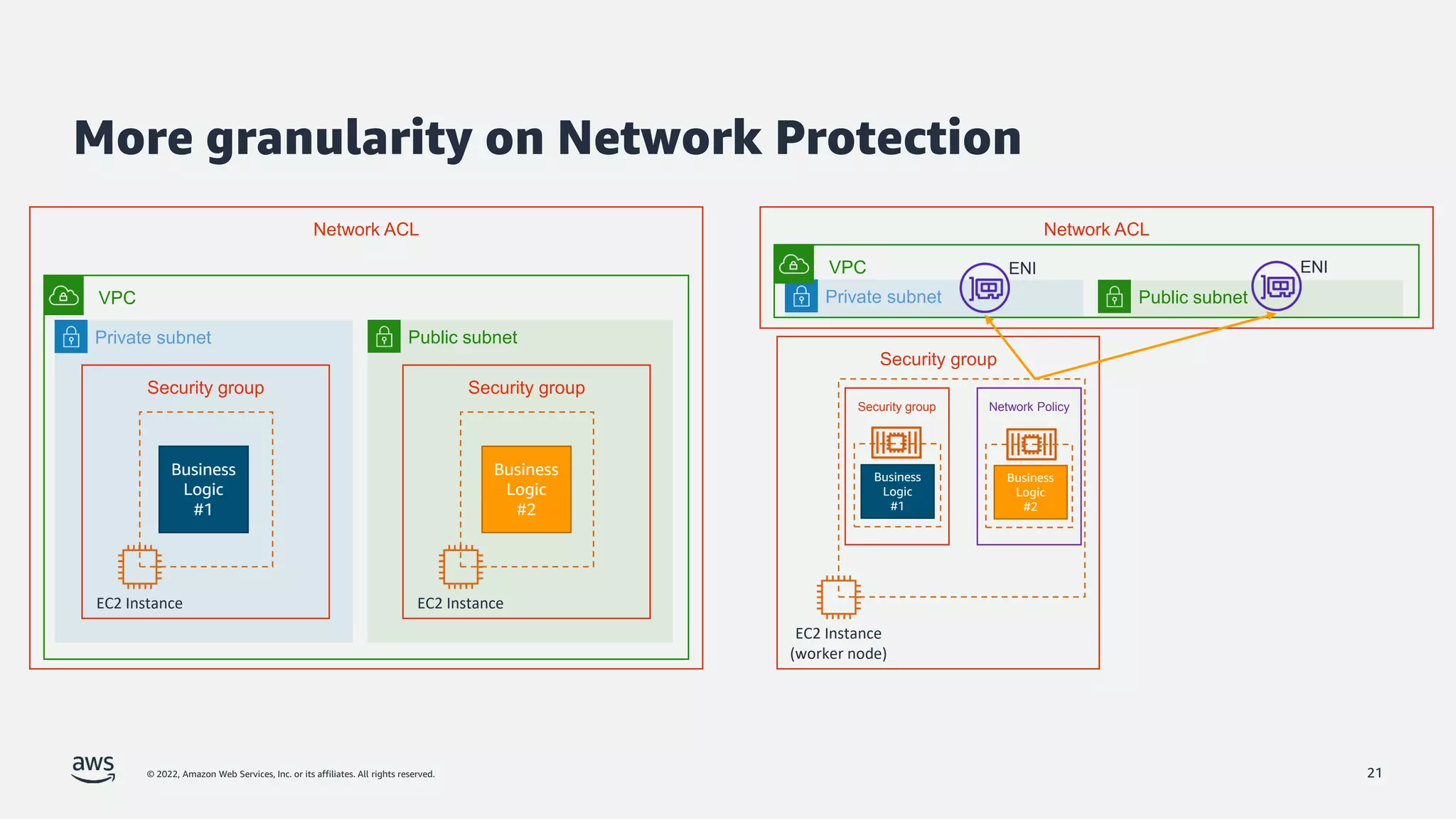
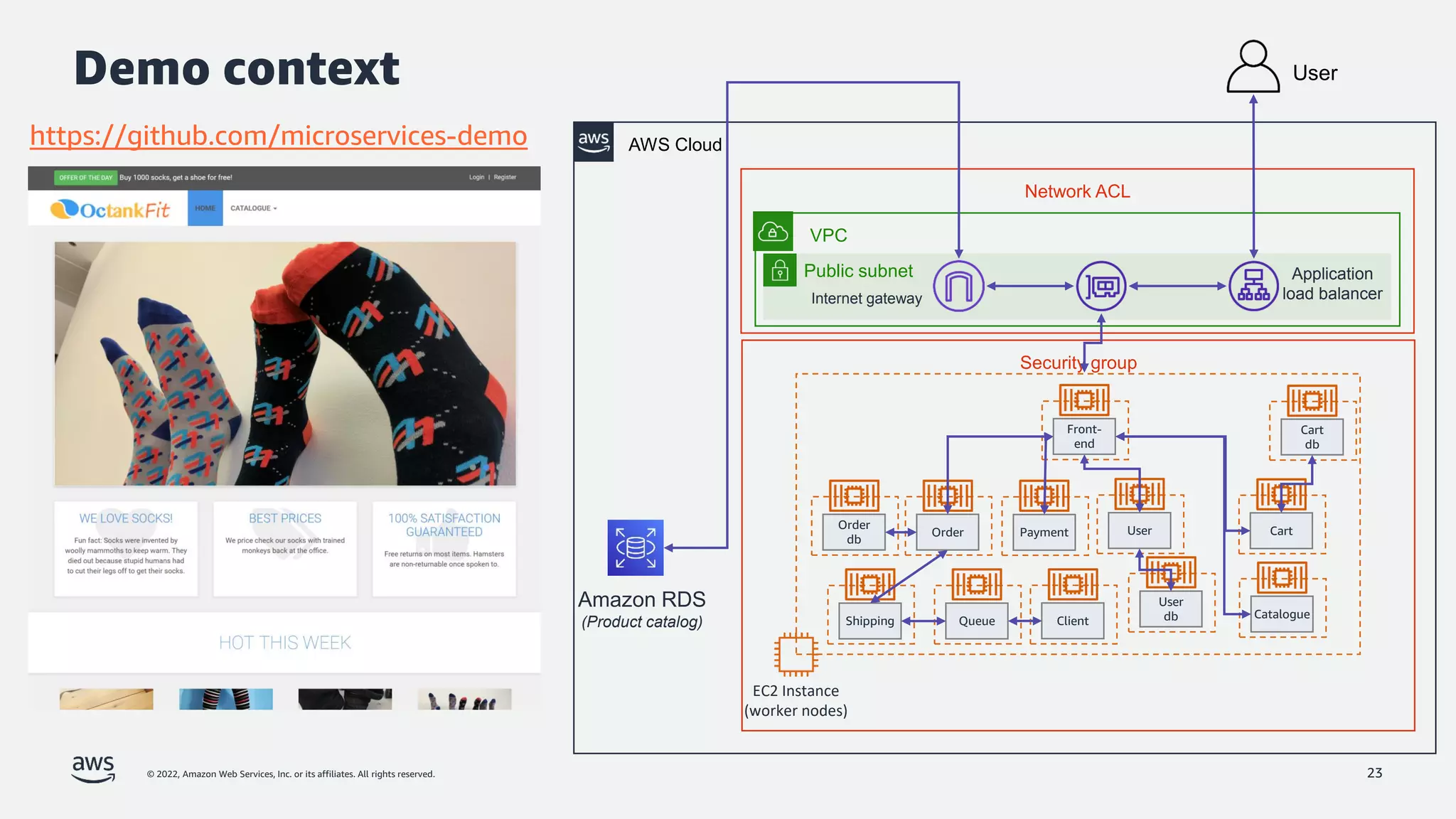
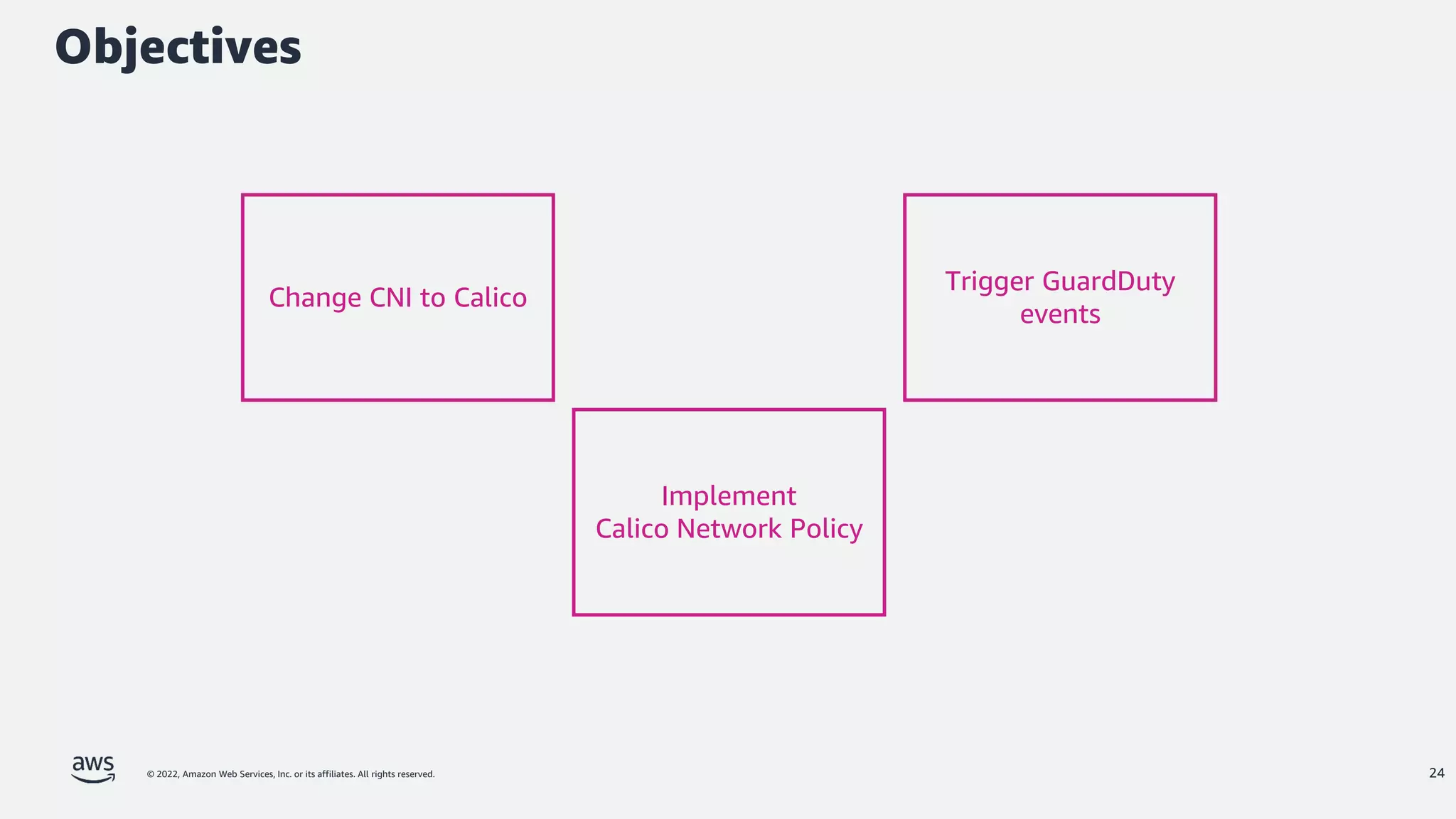
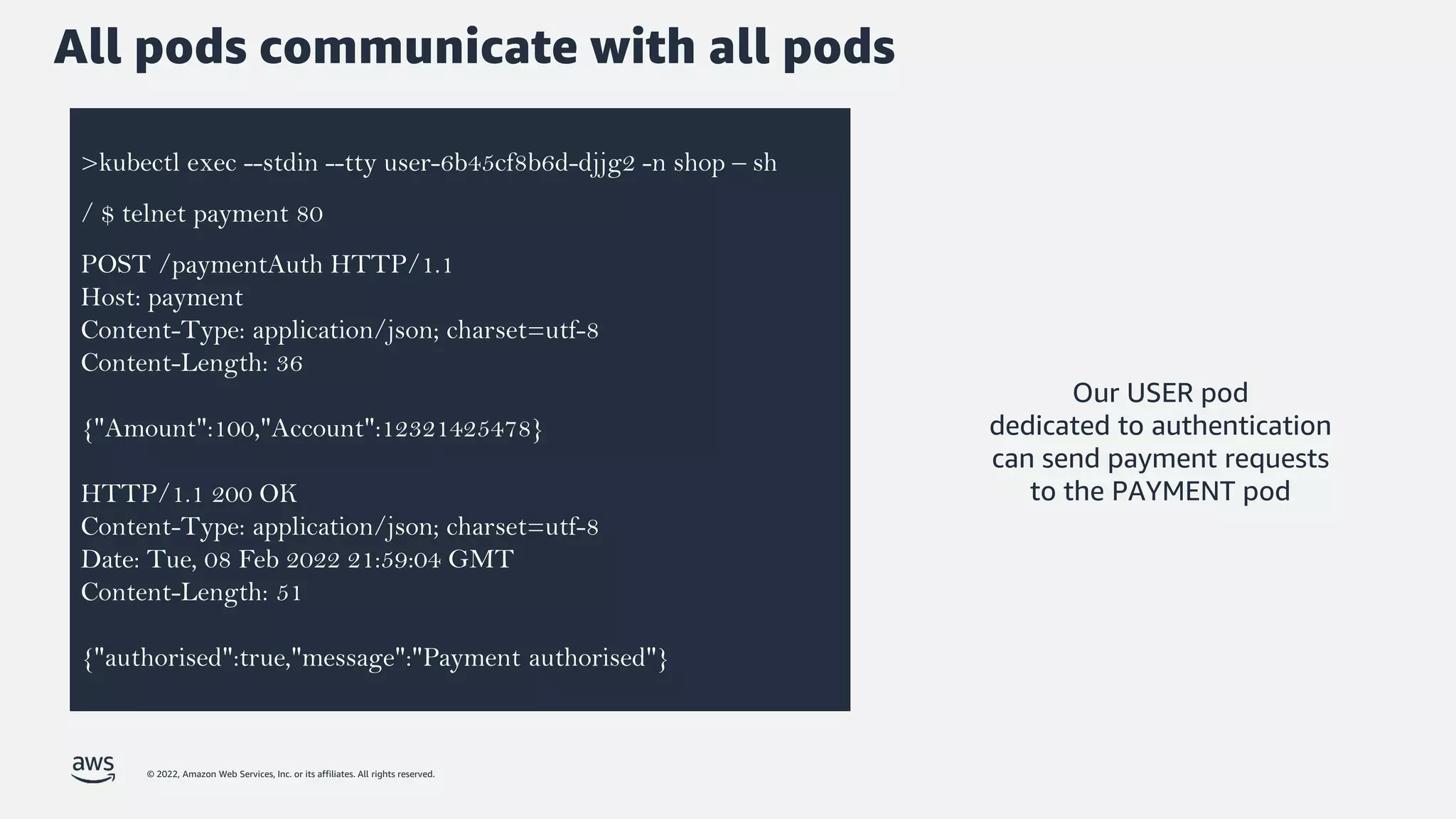
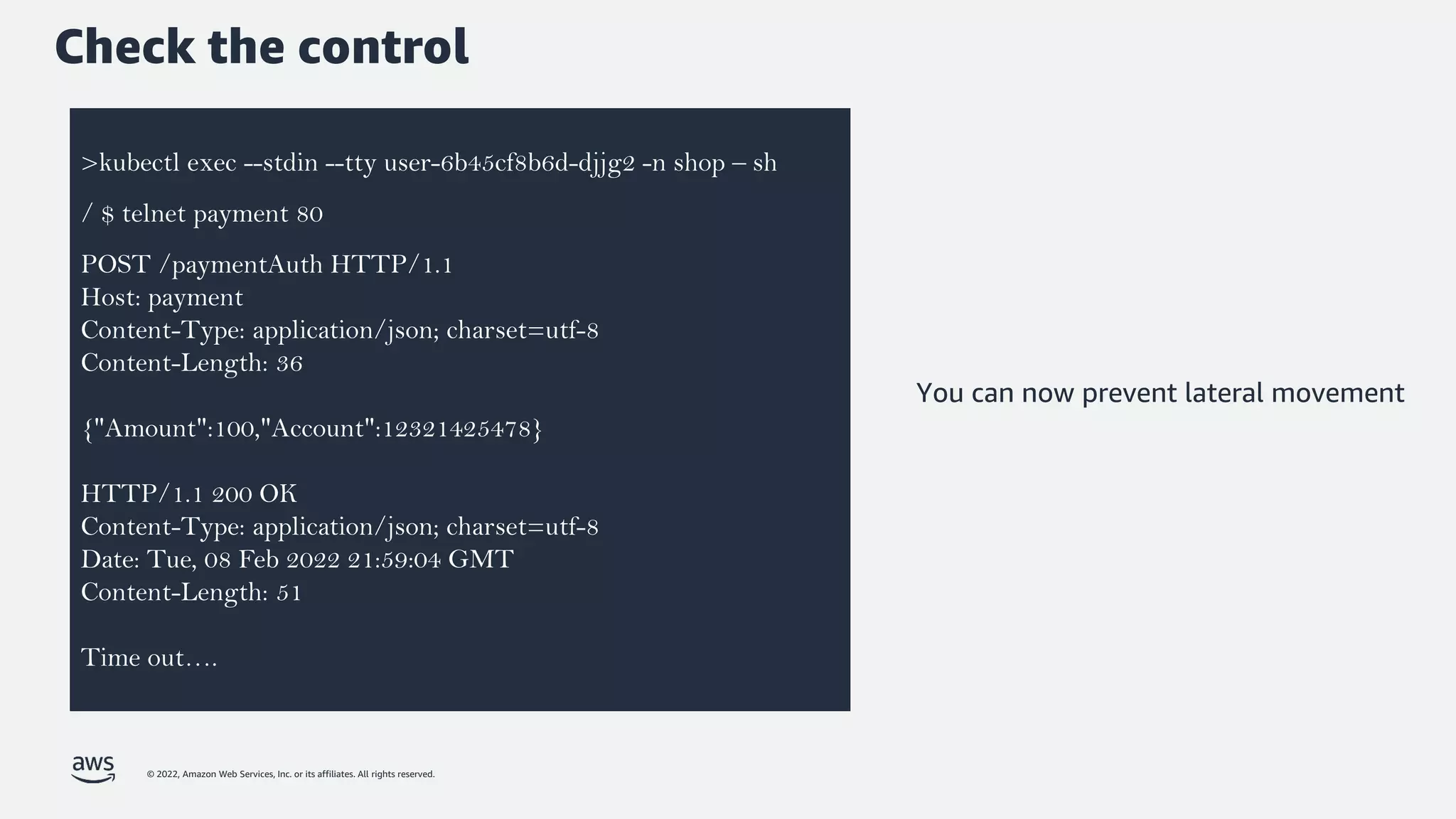
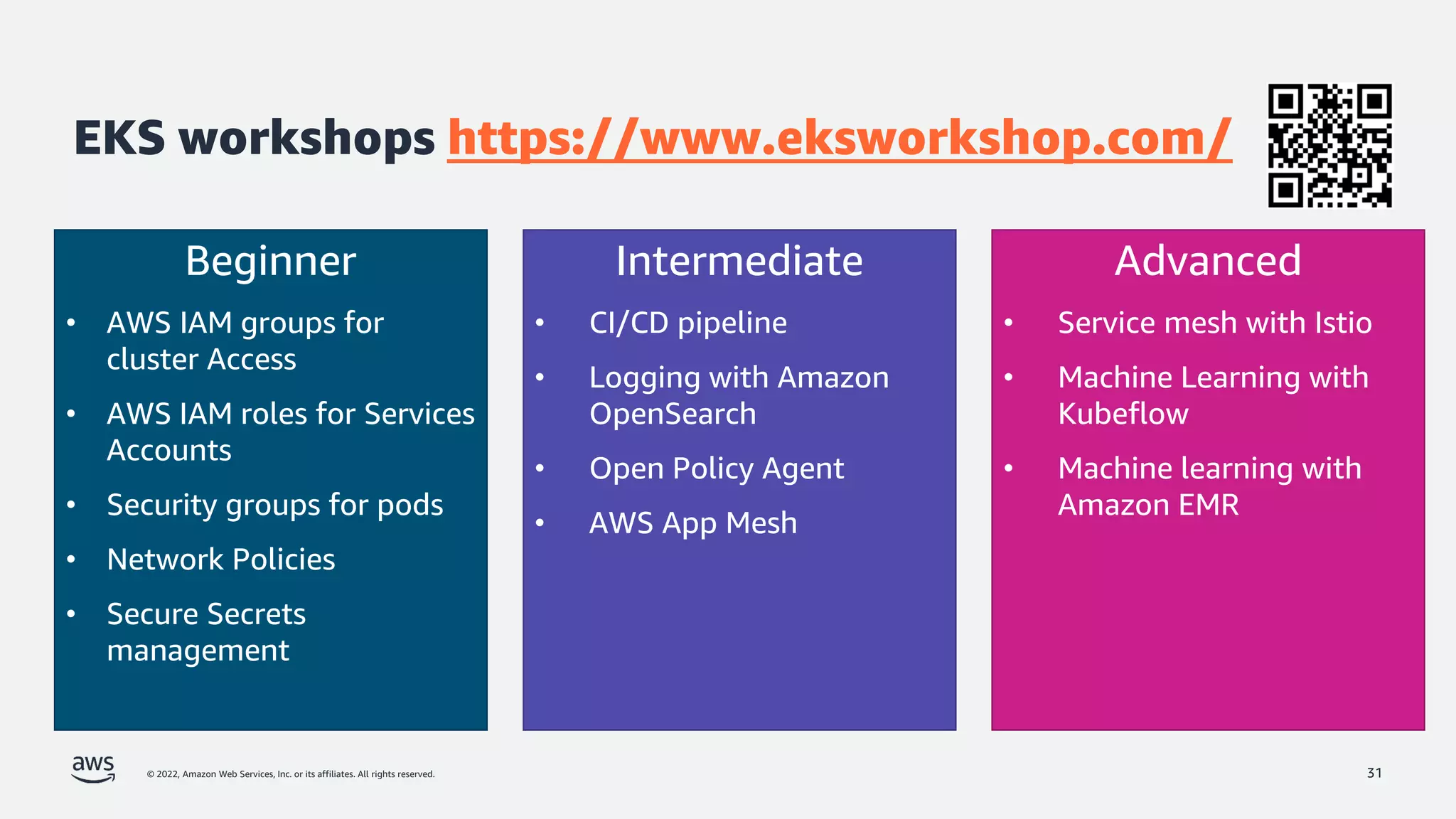
The document discusses security best practices for Amazon EKS, focusing on various protective measures and recent feature launches aimed at enhancing security within the platform. It highlights the shared responsibility model, improvements in IAM and compliance features, and practical steps for securing Kubernetes environments. Additionally, it includes resources for further learning and upcoming features related to EKS security.