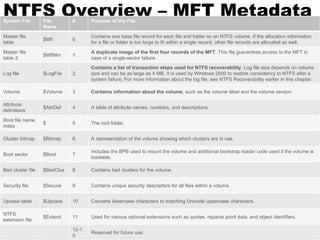
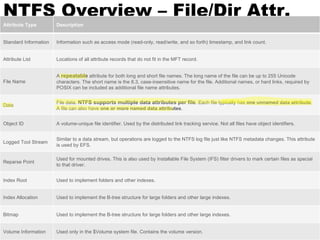
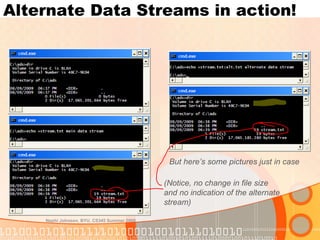
Alternate data streams allow additional data to be stored in hidden streams associated with files in the NTFS file system. Entries in the Master File Table can contain multiple data streams. Malware and hackers use alternate data streams to hide files and executables, while legitimate applications may use them to store metadata. Special tools are needed to view the hidden alternate streams associated with a file.

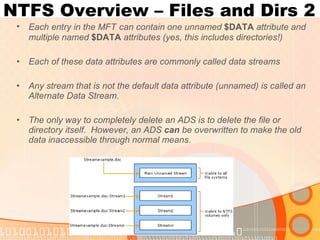
![NTFS Overview – Files and Dirs Each entry in the MFT describes a file or dir and is a collection of attributes (yes , even the file data ) [see next slide] If the total size of a file’s attributes (remember, attributes also include the file data) is smaller than the record size in the MFT (1 KB), the entire file will be stored in the MFT. If an attribute’s value(s) are small enough to fit inside the MFT entry, then that attribute is called resident . (filenames, timestamps are always resident) Otherwise, some attributes are made non-resident and a pointer to a new data run or extent is stored in the Attribute List attribute. The actual values of the non-resident attributes are stored in the extent. An extent is a contiguous “run” of clusters used to store an attribute’s data. Nephi Johnson, BYU, CS345 Summer 2009](https://image.slidesharecdn.com/alternatedatastreams-090815082802-phpapp02/85/Alternate-Data-Streams-7-320.jpg)


![Reference [1] - Discovering alternate data streams using .NET http://msdn.microsoft.com/en-us/magazine/cc163677.aspx [2] - Clusters and Extents http://msdn.microsoft.com/en-us/library/aa363841(VS.85).aspx [3] - Comparisons between FAT, HPFS, and NTFS http://support.microsoft.com/kb/100108 [4] - White paper on hiding data in NTFS (a very interesting read) http://www.forensicfocus.com/downloads/ntfs-hidden-data-analysis.pdf [5] - An excellent NTFS overview and reference http://technet.microsoft.com/en-us/library/cc781134(WS.10).aspx [6] - An old (2001) but good walkthrough of NTFS http://www.pcguide.com/ref/hdd/file/ntfs/arch.htm [7] - Explains the MFT and files with slightly more detail than [5] http://technet.microsoft.com/en-us/library/cc938949.aspx [8] - Wikipedia entry on File System Forks http://en.wikipedia.org/wiki/Alternate_data_streams [9] - Talk of ADS from a security perspective http://www.forensicfocus.com/dissecting-ntfs-hidden-streams [10] An excellent white paper on Alternate Data Streams and how to enumerate them http://www.sans.org/reading_room/whitepapers/honors/alternate_data_streams_out_of_the_shadows_and_into_the_light_1503?show=1503.php&cat=honors](https://image.slidesharecdn.com/alternatedatastreams-090815082802-phpapp02/85/Alternate-Data-Streams-13-320.jpg)