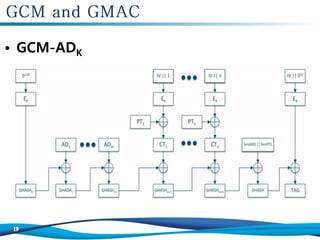
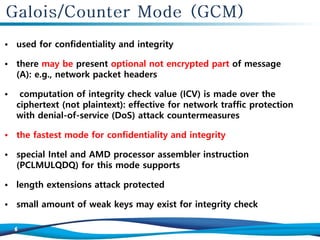
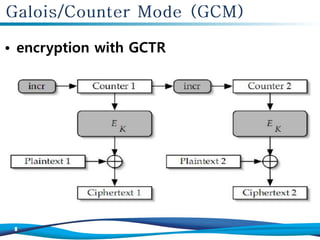
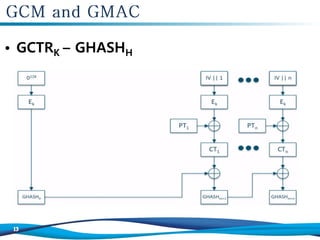
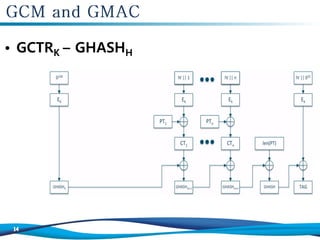
The document discusses the Galois/Counter Mode (GCM) and Message Authentication Code (MAC) used in symmetric encryption, emphasizing their roles in ensuring confidentiality, integrity, and authentication of data. It details the mechanisms and operations involved in GCM, including the use of AES for encryption and the effectiveness of GCM in protecting network traffic against attacks. Additionally, it mentions the performance benefits of GCM and the various academic references on the topic.





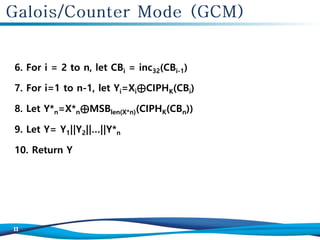
![1. If X is the empty string, then return the empty string as Y
2. Let n=[len(X)/128]
3. Let X1, X 2, ... , X n-1, X*n denote the unique sequence of
blocks such that X = X 1 || X 2 || ... || X n-1 || X*n
4. X1, X2,..., Xn-1 are complete blocks.
Consequently, Xn* is either a complete block or a nonempty
partial block, and if 1 ≤ len(X) ≤128, then X = X1*
5. Let CB1=ICB](https://image.slidesharecdn.com/algorithm-181024141235/85/Algorithm-MAC-GCM-GMAC-10-320.jpg)
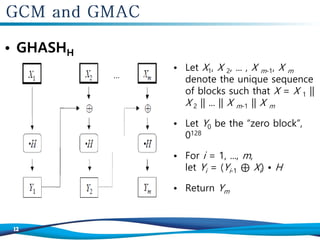
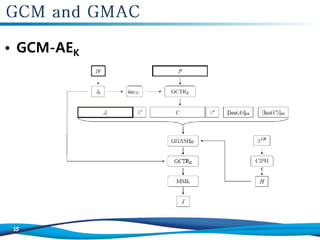
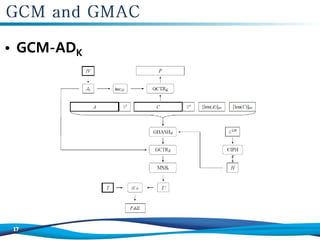
![1. Let H = CIPHK(0
128
).
2. Define a block, J0, as follows:
If len(IV)=96, then let J0 = IV || 0
31
||1.
If len(IV) ≠ 96, then let s = 128[len(IV)/128]–len(IV), and let
J0=GHASHH(IV||0
s+64
||[len(IV)]64).
3. Let C=GCTRK(inc32(J0), P)
4. Let u = 128 . [len(C)/128]–len(C) and let v = 128 . [len(A)/128]–len(A)
5. Define a block, S, as follows:
S = GHASHH (A || 0
v
|| C || 0
u
|| [len(A)]64 || [len(C)]64).
6. Let T = MSBt(GCTRK(J0,S))
7. Return (C, T)](https://image.slidesharecdn.com/algorithm-181024141235/85/Algorithm-MAC-GCM-GMAC-16-320.jpg)