The document discusses image steganography and various related concepts. It introduces image steganography as hiding secret information in a cover image. Key points covered include:
- Huffman coding is used to encode the secret image before embedding. It assigns binary codes to image intensity values.
- Discrete wavelet transform (DWT) is applied to the cover image. The secret message is embedded in the high frequency DWT coefficients while preserving the low frequency coefficients to maintain image quality.
- Inverse DWT is applied to produce a stego-image containing the hidden secret image. Haar DWT is used in the described approach.

![2
1.1 Image Steganography
Image steganography[1][2]
is the art of hiding information into a cover image. Steganography is a
branch of information hiding in which secret information is camouflaged within other
information. The word steganography in Greek means “covered writing” ( Greek words “stegos”
meaning “cover” and “grafia” meaning “writing”) .
The main objective of steganography is to communicate securely in such a way that the true
message is not visible to the observer. That is unwanted parties should not be able to distinguish
any sense between cover-image (image not containing any secret message) and stego-image
(modified cover-image that containing secret message). Thus the stego-image should not deviate
much from original cover-image. Today steganography is mostly used on computers with digital
data being the carriers and networks being the high speed delivery channels. Figure. 1 shows the
block diagram of a simple image steganographic system.
FIGURE 1.1: The block diagram of a simple steganographic system](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-2-320.jpg)

![4
1.2 Types of Digital Images[5]
The Images types are :
1) Binary
2) Gray-Scale
3) Color
4) Multispectral
1.2.1 Binary Images
Binary images are the simplest type of images and can take on two values, typically black and
white, or 0 and 1. A binary image is referred to as a 1-bit image because it takes only 1 binary
digit to represent each pixel. These types of images are frequently used in applications where the
only information required is general shape or outline, for example optical character
recognititon(OCR).
Binary images are often created from the gray scale image via a threshold operation, where every
pixel above the threshold value is turned white(‘1’), and those below it are turned black(‘0’).
1.2.2 Gray-Scale Images
Gray-scale images are referred to as monochrome(one-color) images. They contain gray-level
information, no color information. The numbers of bits used for each pixel determines the
number of different gray levels available. The typical gray scale image contains 8 bits/pixel data,
which allows us to have 256 different gray levels.
In applications like medical imaging and astronomy, 12 or 16 bits/pixel images are used. These
extra gray levels become useful when a small section of the image is made much larger to
discern details.](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-4-320.jpg)
![5
1.2.3 Color Images
Color images can be modeled as three-band monochrome image data, where each band of data
corresponds to a different color. The actual information stored in the digital image data is the
gray-level information in each spectral band.
Typical color images are represented as red, green, and blue(RGB images). Using the 8-bit
monochrome standard as a model, the corresponding color image would have 24 bits/pixel(8 bits
for each of the three color bands red, green, and blue).
1.2.4 Multispectral Images
Multispectral images typically contain information outside the normal human perceptual range.
This may include infrared, ultraviolet, X-ray, acoustic, or radar data. These are not images in the
usual sense because the information represented is not directly visible by the human system.
However, the information is often represented in visual form by mapping the different spectral
bands to RGB components.
1.3 Digital Image File Formats[5]
Types of image data divided into two primary categories : bitmap and vector.
Bitmap images (also called raster images) can be represented as a 2-dimensional function
f(x,y), where they have pixel data and the corresponding gray-level values stored in some
file format.
Vector images refer to methods of representing lines, curves, and shapes by storing only
the key points. These key points are sufficient to define the shapes. The process of
turning these into an image called rendering. After the image has been rendered, it can be
thought of as being in bitmap format, where each pixel has specific values associated
with it.](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-5-320.jpg)
![6
Most of the types of file formats fall into the category of bitmap images, for example :
PPM(Portable Pix Map) format
TIFF(Tagged Image File Format)
GIF(Graphics Image Format)
JPEG(Joint Photographic Experts Group) format
BMP(Windows Bitmap)
PNG(Portable Network Graphics)
XWD(X Window Dump)
1.4 Digital Image Representation[5]
The monochrome digital image f(x,y) resulted from sampling and quantization has finite discrete
coordinates (x,y) and intensities (gray levels). We shall use integer values for these discrete
coordinates, and gray levels. Thus, a monochrome digital image can be represented as a 2-
dimensional array (matrix) that has M rows and N columns. Each element of this matrix array is
called pixel. The spatial resolution (number of pixels) of the digital image is M*N. The gray
level resolution (number of gray levels) L is :
L=2k
Where k is the number of bits used to represent the gray levels of the digital image.
1.4.1 Spatial and Gray-level Resolution
Spatial resolution is the smallest discremble detail in an image.It is determined by the sampling
process.The spatial resolution of a digital image reflects the amount of details that one can see in
the image(i.e. the ratio of pixel “area” to the area of the image display). If an image is spatially
sampled at M*N pixels, then the larger M*N the finner the observed details.](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-6-320.jpg)


![9
2.1 Huffman Coding[2][4]
Huffman coding is an entropy encoding algorithm used for lossless data compression. The term
refers to the use of a variable-length code table for encoding a source symbol (such as a character
in a file) where the variable-length code table has been derived in a particular way based on the
estimated probability of occurrence for each possible value of the source symbol.
Huffman coding uses a specific method for choosing the representation for each symbol,
resulting in a code that expresses the most common source symbols using shorter strings of bits
than are used for less common source symbols. no other mapping of individual source symbols
to unique strings of bits will produce a smaller average output size when the actual symbol
frequencies agree with those used to create the code. The running time of Huffman's method is
fairly efficient, it takes operations to construct it.
Although Huffman's original algorithm is optimal for a symbol-by-symbol coding (i.e. a stream
of unrelated symbols) with a known input probability distribution, it is not optimal when the
symbol-by-symbol restriction is dropped, or when the probability mass functions are unknown,
not identically distributed, or not independent (e.g., "cat" is more common than "cta").
FIGURE 2.1: The block diagram of Huffman Encoding](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-9-320.jpg)



![13
can be accomplished by either transmitting the length of the decompressed data along with the
compression model or by defining a special code symbol to signify the end of input (the latter
method can adversely affect code length optimality, however).
2.1.3 Application
Arithmetic coding can be viewed as a generalization of Huffman coding, in the sense that they
produce the same output when every symbol has a probability of the form 1/2k
; in particular it
tends to offer significantly better compression for small alphabet sizes. Huffman coding
nevertheless remains in wide use because of its simplicity and high speed. Intuitively, arithmetic
coding can offer better compression than Huffman coding because its "code words" can have
effectively non-integer bit lengths, whereas code words in Huffman coding can only have an
integer number of bits. Therefore, there is an inefficiency in Huffman coding where a code word
of length k only optimally matches a symbol of probability 1/2k
and other probabilities are not
represented as optimally; whereas the code word length in arithmetic coding can be made to
exactly match the true probability of the symbol.
Huffman coding today is often used as a "back-end" to some other compression methods.
DEFLATE (PKZIP's algorithm) and multimedia codecs such as JPEG and MP3 have a front-end
model and quantization followed by Huffman coding (or variable-length prefix-free codes with a
similar structure, although perhaps not necessarily designed by using Huffman's algorithm.
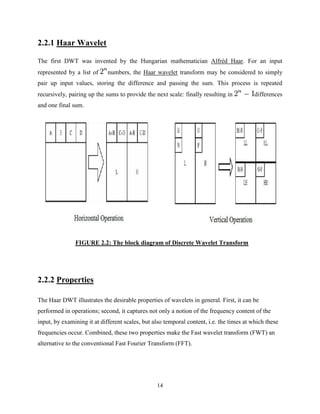
2.2 Discrete Wavelet Transform[2][4]
In numerical analysis and functional analysis, a discrete wavelet transform (DWT) is any
wavelet transform for which the wavelets are discretely sampled. As with other wavelet
transforms, a key advantage it has over Fourier transforms is temporal resolution: it captures
both frequency and location information (location in time).](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-13-320.jpg)



![18
3.1 About Matlab
MATLAB[3]
(matrix laboratory) is a numerical computing environment and fourth-generation
programming language. Developed by Math Works, MATLAB allows matrix manipulations,
plotting of functions and data, implementation of algorithms, creation of user interfaces, and
interfacing with programs written in other languages, including C, C++, Java, and Fortran.
Although MATLAB is intended primarily for numerical computing, an optional toolbox uses
the MuPAD symbolic engine, allowing access to symbolic computing capabilities. An additional
package, Simulink, adds graphical multi-domain simulation and Model-Based
Design for dynamic and embedded systems.
In 2004, MATLAB had around one million users across industry and academia. MATLAB users
come from various backgrounds of engineering, science, and economics.
Syntax-The MATLAB application is built around the MATLAB language, and most use of
MATLAB involves typing MATLAB code into the Command Window (as an interactive
mathematical shell), or executing text files containing MATLAB codes, including scripts
and/or functions.
Variables-Variables are defined using the assignment operator, =. MATLAB is a weakly
typed programming language because types are implicitly converted. It is a dynamically typed
language because variables can be assigned without declaring their type, except if they are to be
treated as symbolic objects,[8]
and that their type can change. Values can come from constants,
from computation involving values of other variables, or from the output of a function.
Structures-MATLAB has structure data types.[10]
Since all variables in MATLAB are arrays, a
more adequate name is "structure array", where each element of the array has the same field
names. In addition, MATLAB supports dynamic field names[11]
(field look-ups by name, field
manipulations, etc.). Unfortunately, MATLAB JIT does not support MATLAB structures,
therefore just a simple bundling of various variables into a structure will come at a cost.](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-18-320.jpg)
![19
3.2 MATLAB Codes
1. Code for converting image to Huffman code
clc;
clear all;
img=imread('Desert.jpg');
%converting RGB to grayscale image
%monochoromatic luminance method
img1=.2989*img(:,:,1)+.5870*img(:,:,2)+.1140*img(:,:,3);
%imshow(img1);
%creating histogram og image
hist=imhist(img1);
%imhist(img1);
symbol=0:255;
sum=0;
%finding probabilities of each symbols
for i=1:256
sum=sum+hist(i);
end
for i=1:256
prob(i)=double(hist(i))/sum;
end
%prob;
f=0;
for i=1:256
f=f+prob(i);
end
%f;
[dict,avglen] = huffmandict(symbol,prob);
[rows columns size]=size(img1);
pixels=rows*columns
img2=reshape(img1,1,pixels);
encode = huffmanenco(img2,dict);
%pilot image
pilot=imread('Koala.jpg');
pilot1=.2989*pilot(:,:,1)+.5870*pilot(:,:,2)+.1140*pilot(:,:,3);
f=1;
[cA,cH,cV,cD] = dwt2(pilot1,'haar');
h=1;
w=1;
for i=1:2:442651
b(w)=encode(i)*2+encode(i+1);
w=w+1;
end
for i=1:267
for k=1:400
cH1(i,k)=cH(i,k)-mod(cH(i,k),4)+b(h);](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-19-320.jpg)
![21
2. Histogram
%histogram of image
clc;
clear all;
img=imread('Koala.jpg');
%converting RGB to grayscale image
%monochoromatic luminance method
img1=.2989*img(:,:,1)+.5870*img(:,:,2)+.1140*img(:,:,3);
%imshow(img1);
%creating histogram og image
hist=imhist(img1);
imhist(img1);
3. Pilot Image
%pilot image
%pilot=imread('Koala.jpg');
%pilot1=.2989*pilot(:,:,1)+.5870*pilot(:,:,2)+.1140*pilot(:,:,3);
%[cA,cH,cV,cD] = dwt2(pilot1,'haar');
for i=1:2:442652
b(f)=encode(i)*2+encode(i+1);
j=j+1;
end
4. Retrieval Image
p=1;
for i=1:267
for o=1:400
ret(p)=mod(cH1(i,o),4);
p=p+1;
end
end
for i=1:267
for o=1:400
ret(p)=mod(cV1(i,o),4);
p=p+1;
end](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-21-320.jpg)
![22
end
for i=1:267
for o=1:400
if(p<=442652)
ret(p)=mod(cD1(i,o),4);
p=p+1;
else
break;
end
end
end
p=1;
for i=1:267
for o=1:400
ret(p)=mod(cH1(i,o),4);
p=p+1;
end
end
for i=1:267
for o=1:400
ret(p)=mod(cV1(i,o),4);
p=p+1;
end
end
for i=1:267
for o=1:400
if(p<=442652)
ret(p)=mod(cD1(i,o),4);
p=p+1;
else
break;
end
end
end
5. Huffmandict
clc;
clear all;
img=imread('Koala.jpg');
%converting RGB to grayscale image
%monochoromatic luminance method
img1=.2989*img(:,:,1)+.5870*img(:,:,2)+.1140*img(:,:,3);
%imshow(img1);
%creating histogram og image
hist=imhist(img1);
%imhist(img1);
symbol=[1:256];
sum=0;
%finding probabilities of each symbols](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-22-320.jpg)
![23
for i=1:256
sum=sum+hist(i);
end
for i=1:256
prob(i)=double(hist(i))/sum;
end
%prob;
f=0;
for i=1:256
f=f+prob(i);
end
%f;
[dict,avglen] = huffmandict(symbol,prob);
6. Display
%reconstruction from modified subband
f=idwt2(cA,cH,cV,cD,'haar');
f1=idwt2(cA,cH1,cV1,cD1,'haar');
subplot(4,3,1);imshow(f,[]);title('Origanal Pilot Image')
subplot(4,3,4);imshow(cH);title('Origanal Vector Horizontal')
subplot(4,3,7);imshow(cV);title('Origanal Vector Vertical')
subplot(4,3,10);imshow(cD);title('Origanal Vector Diagonal')
subplot(4,3,3);imshow(f1,[]);title('Stegno Image')
subplot(4,3,6);imshow(cH1);title('Modified Vector Horizontal')
subplot(4,3,9);imshow(cV1);title('Modified Vector Vertical')
subplot(4,3,12);imshow(cD1);title('Modified Vector Diagonal')
subplot(4,3,5);imshow(img);title('Secret Image')](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-23-320.jpg)



![27
REFERENCES
1. Chen, P.Y. and Wu, W.E. “ A DWT Based Approach for Image Steganography ”,
International Journal of Applied Science and Engineering[1]
2. A Novel Technique for Image Steganography Based on DWT and Huffman Encoding by
Amitava Nag, Sushanta Biswas, Debasree Sarkar & Partha Pratim Sarkar[2]
3. Wikipedia - The Free Encyclopedia. Steganography.
http://en.wikipedia.org/wiki/Steganography[3]
4. Digital Image Processing Using MATLAB by Rafael C. Gonzalez and Steven L.
Eddins[4]
5. http://uotechnology.edu.iq/DIP_Lecture2.pdf[5]](https://image.slidesharecdn.com/8f9092fe-1fd9-41c1-999e-1fce59cd16c7-161101135504/85/akashreport-27-320.jpg)