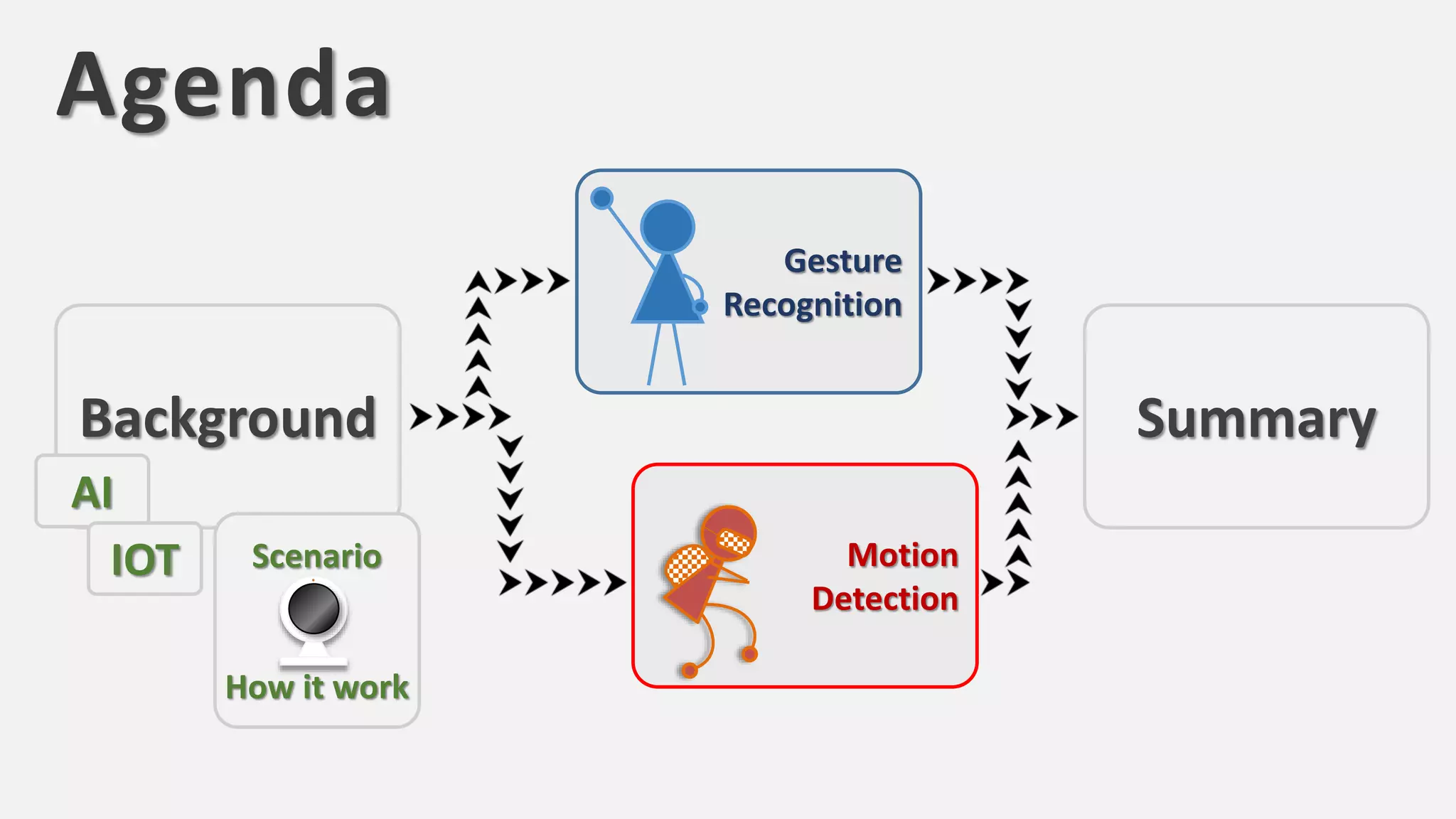
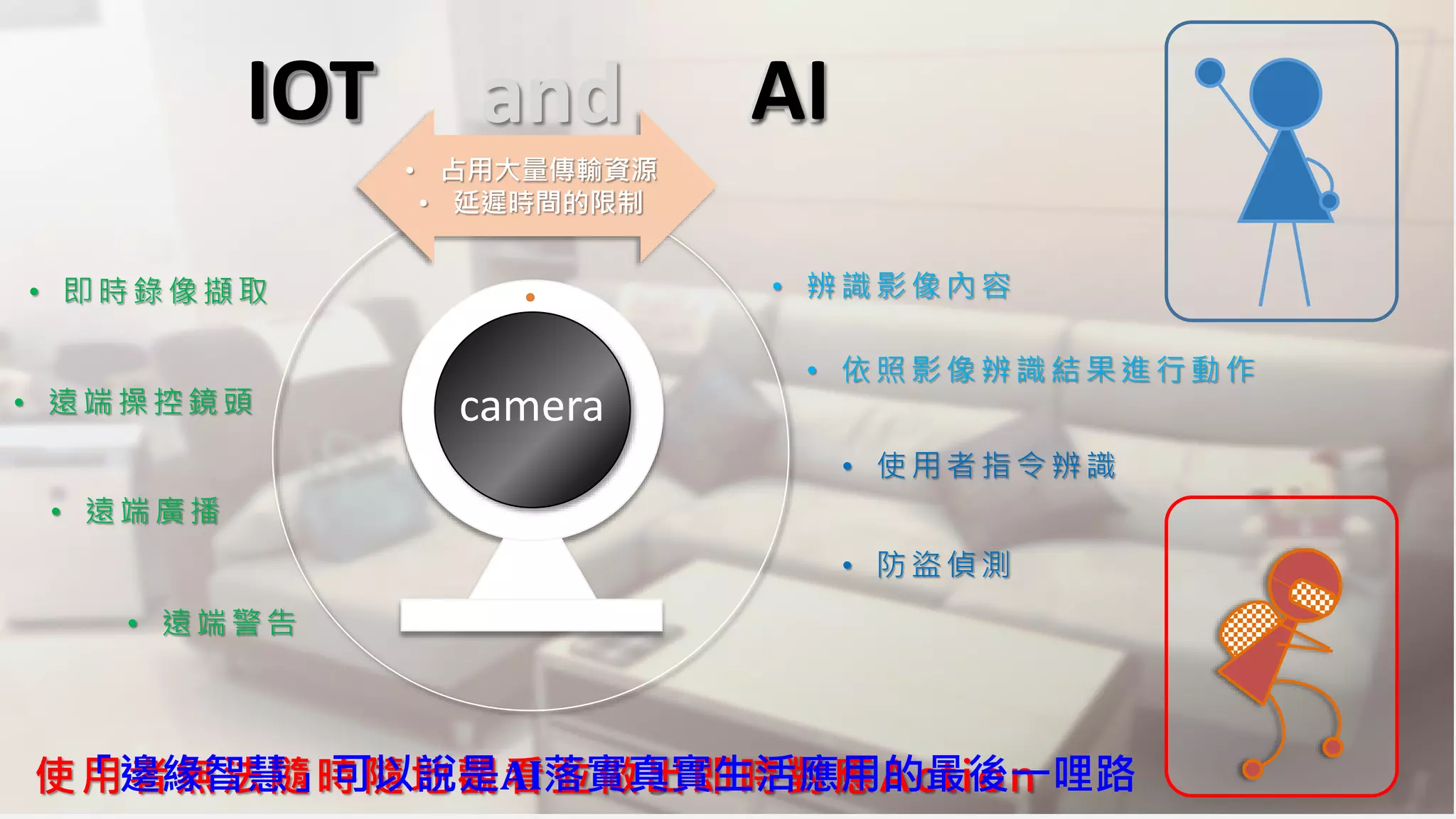
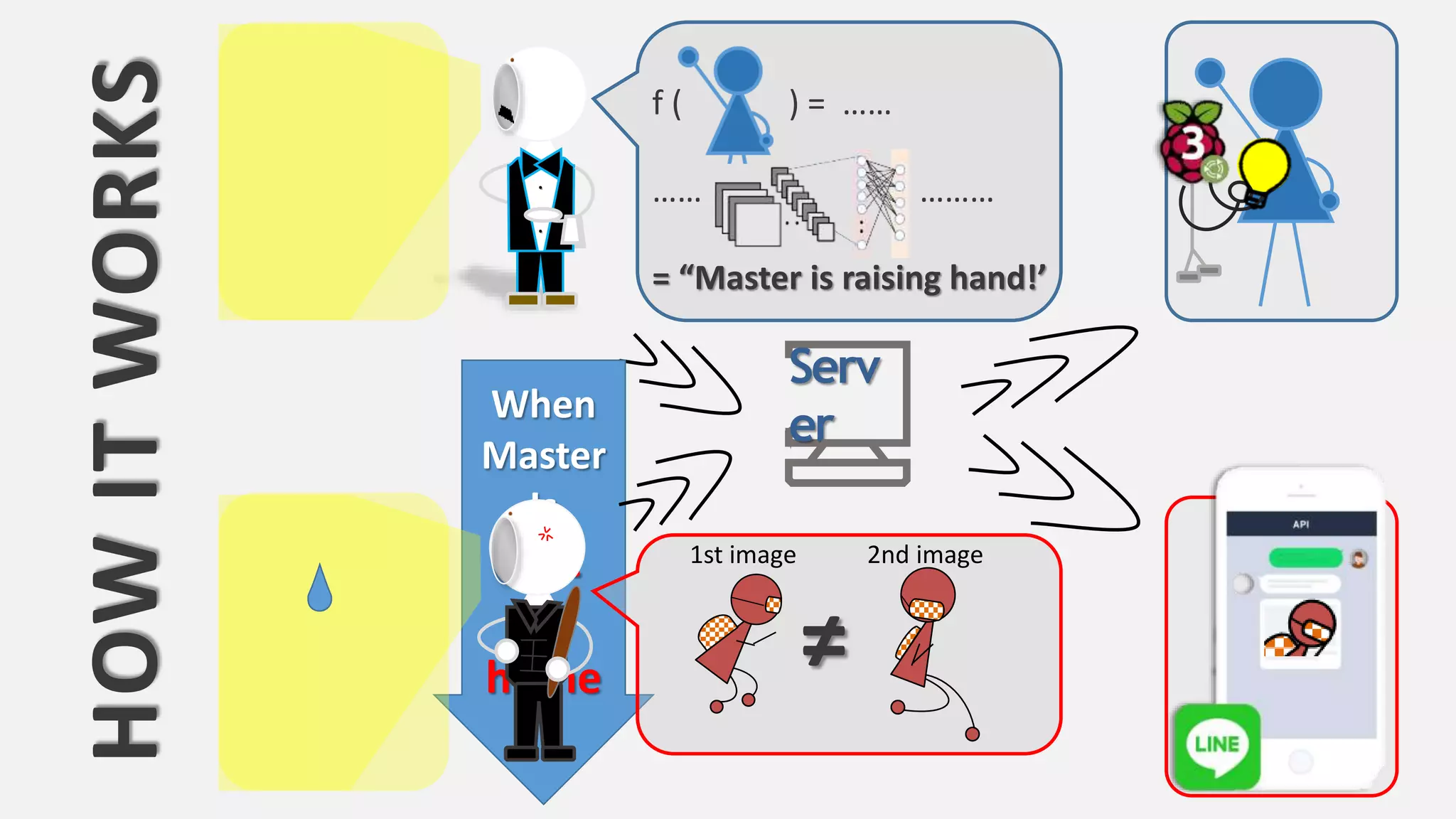
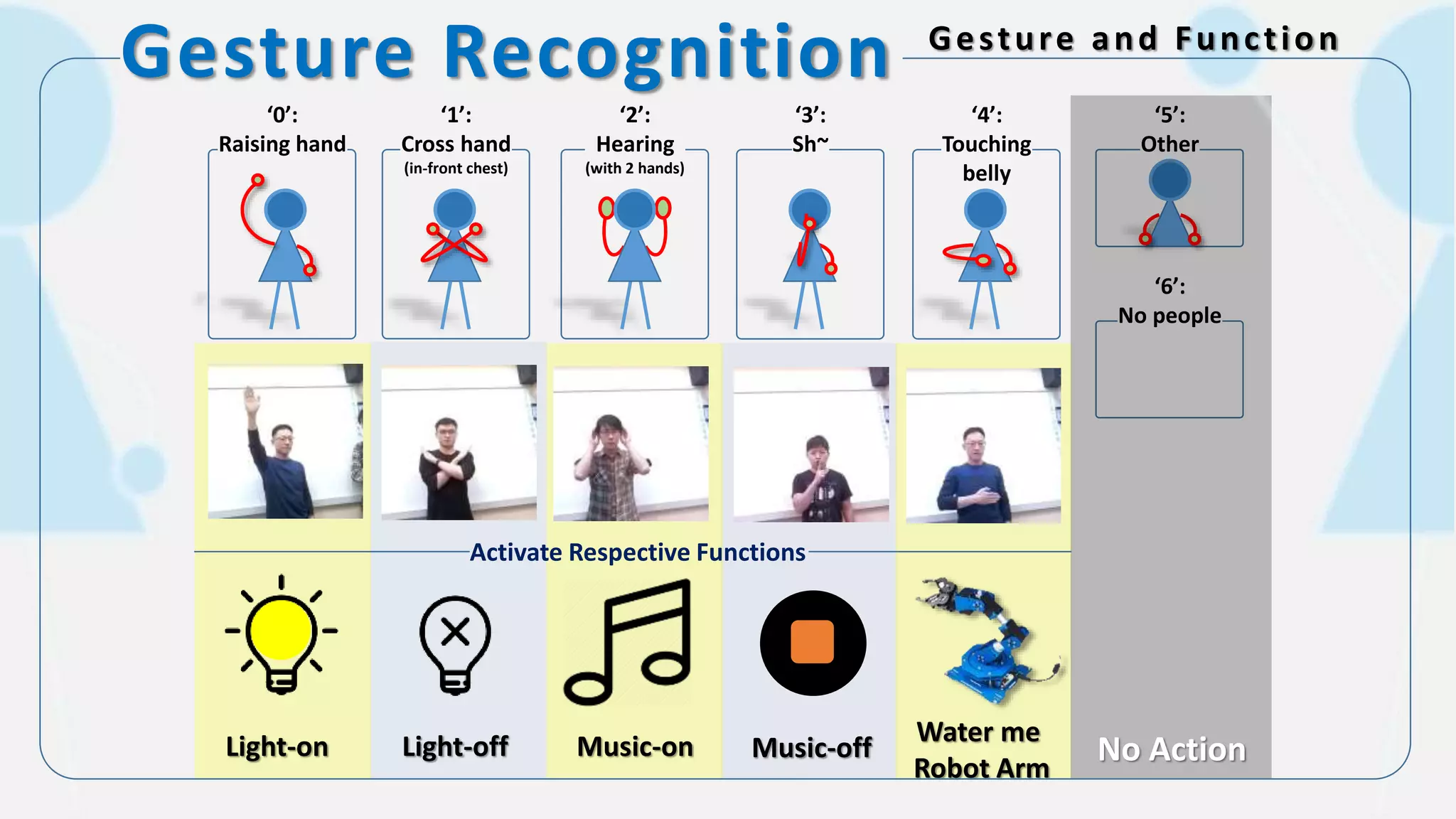
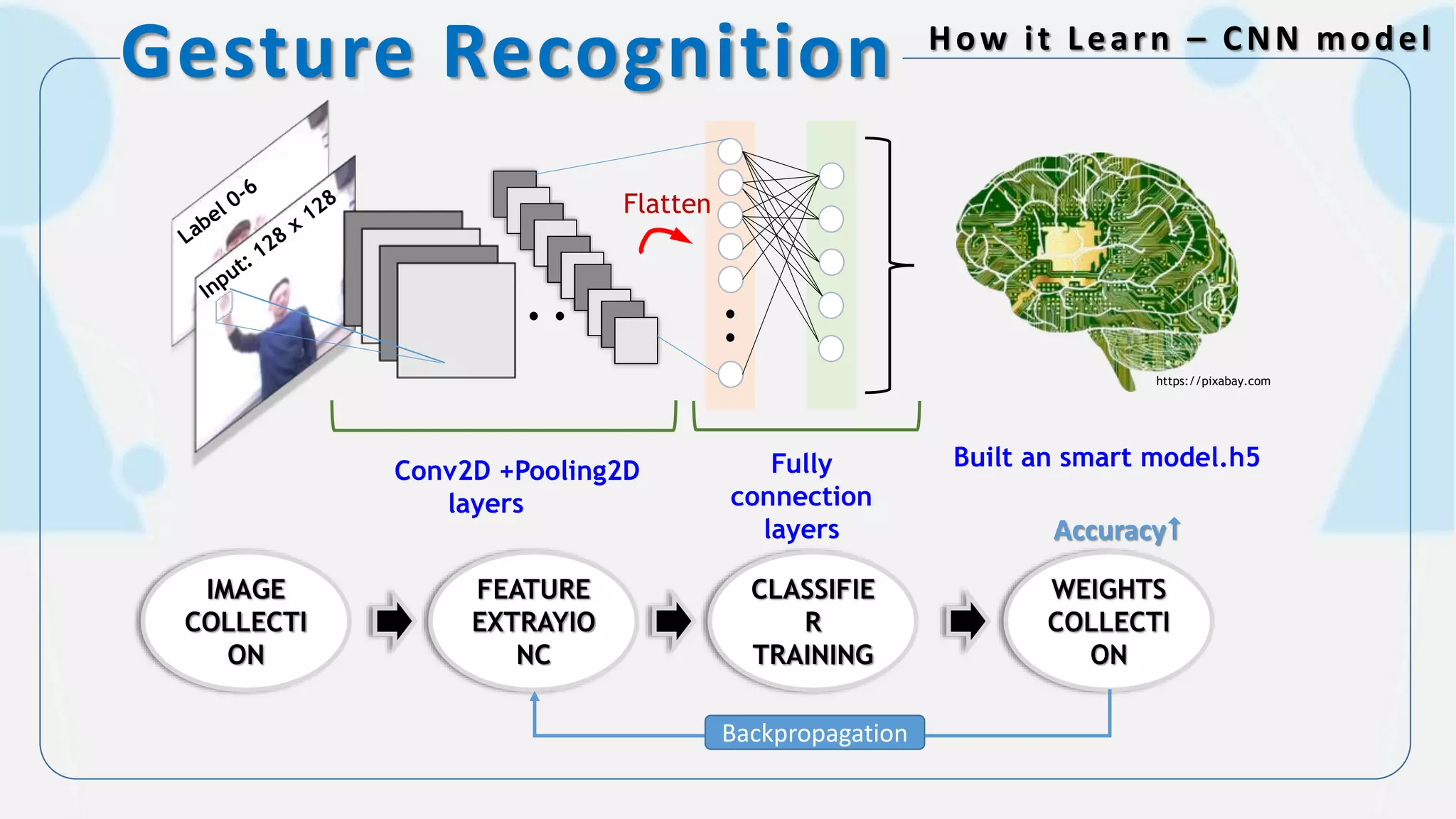
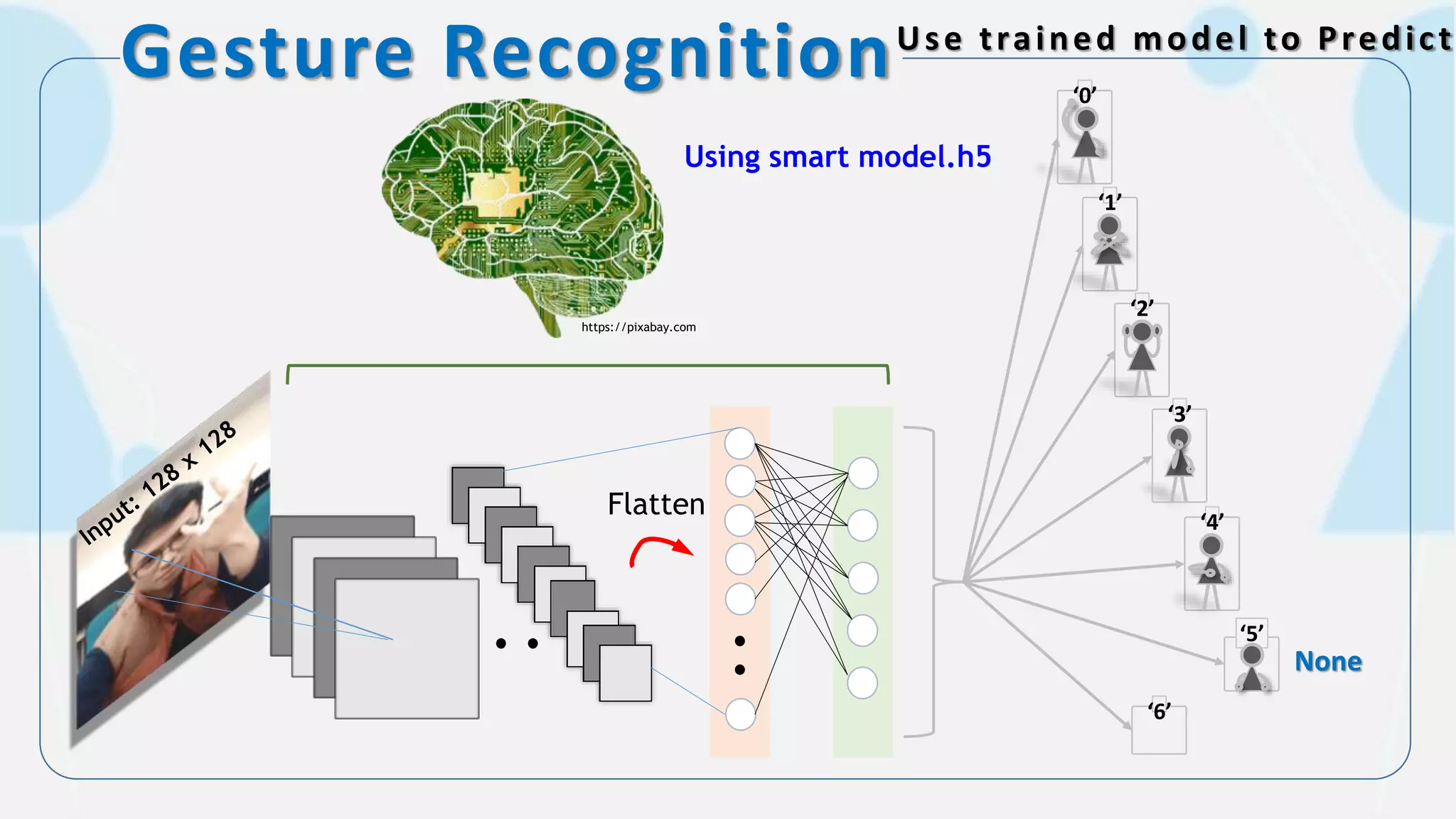
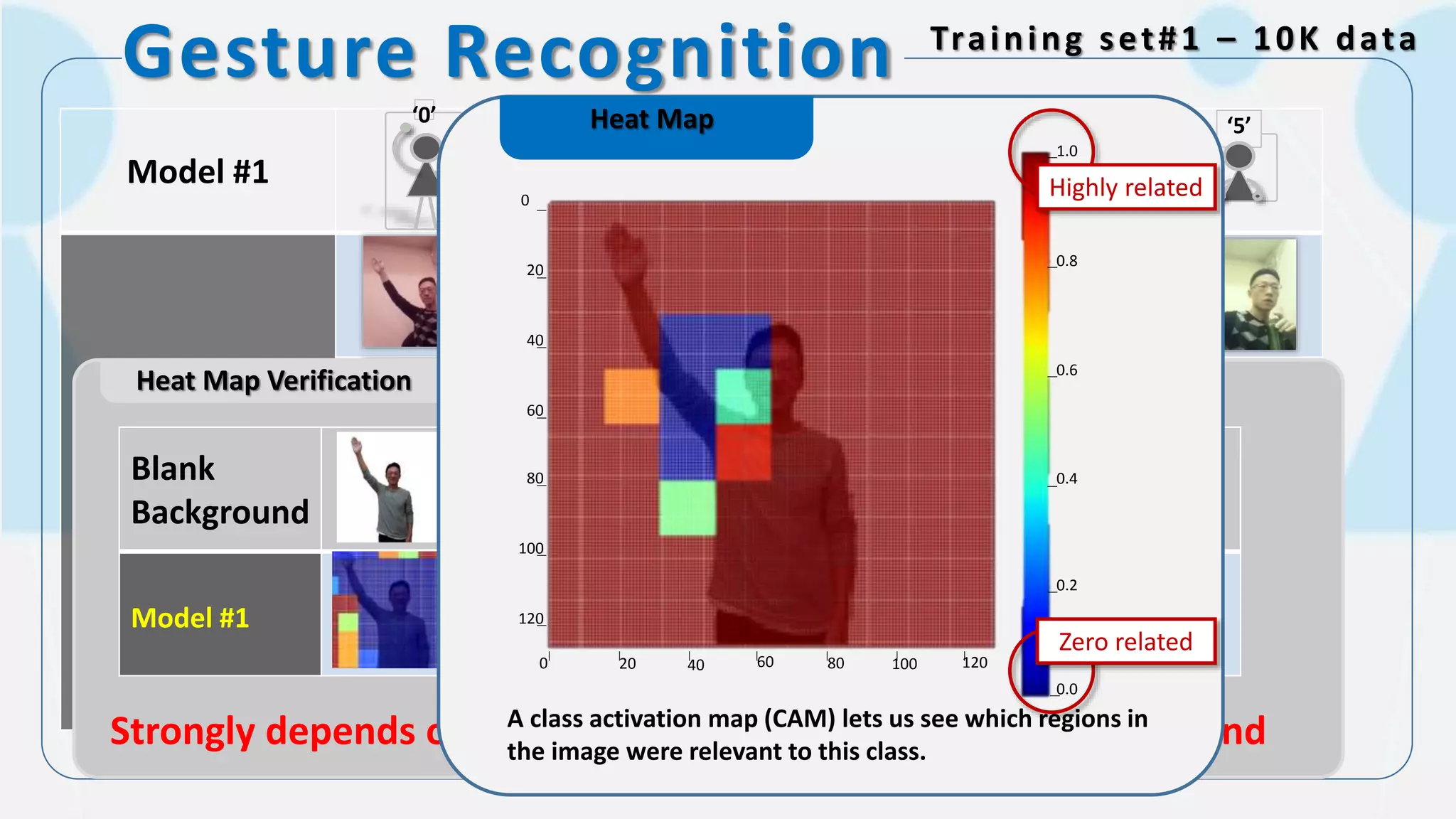
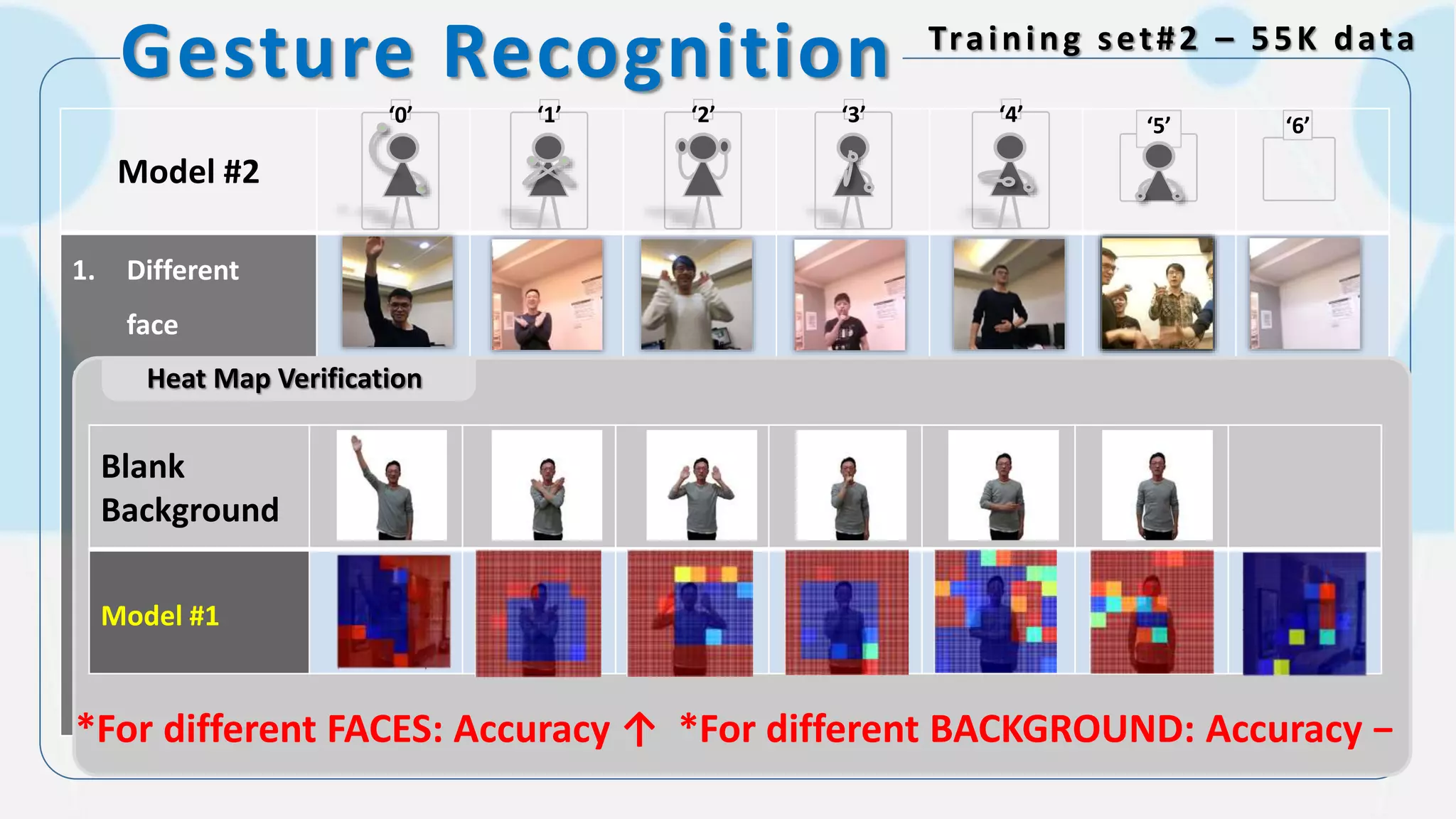
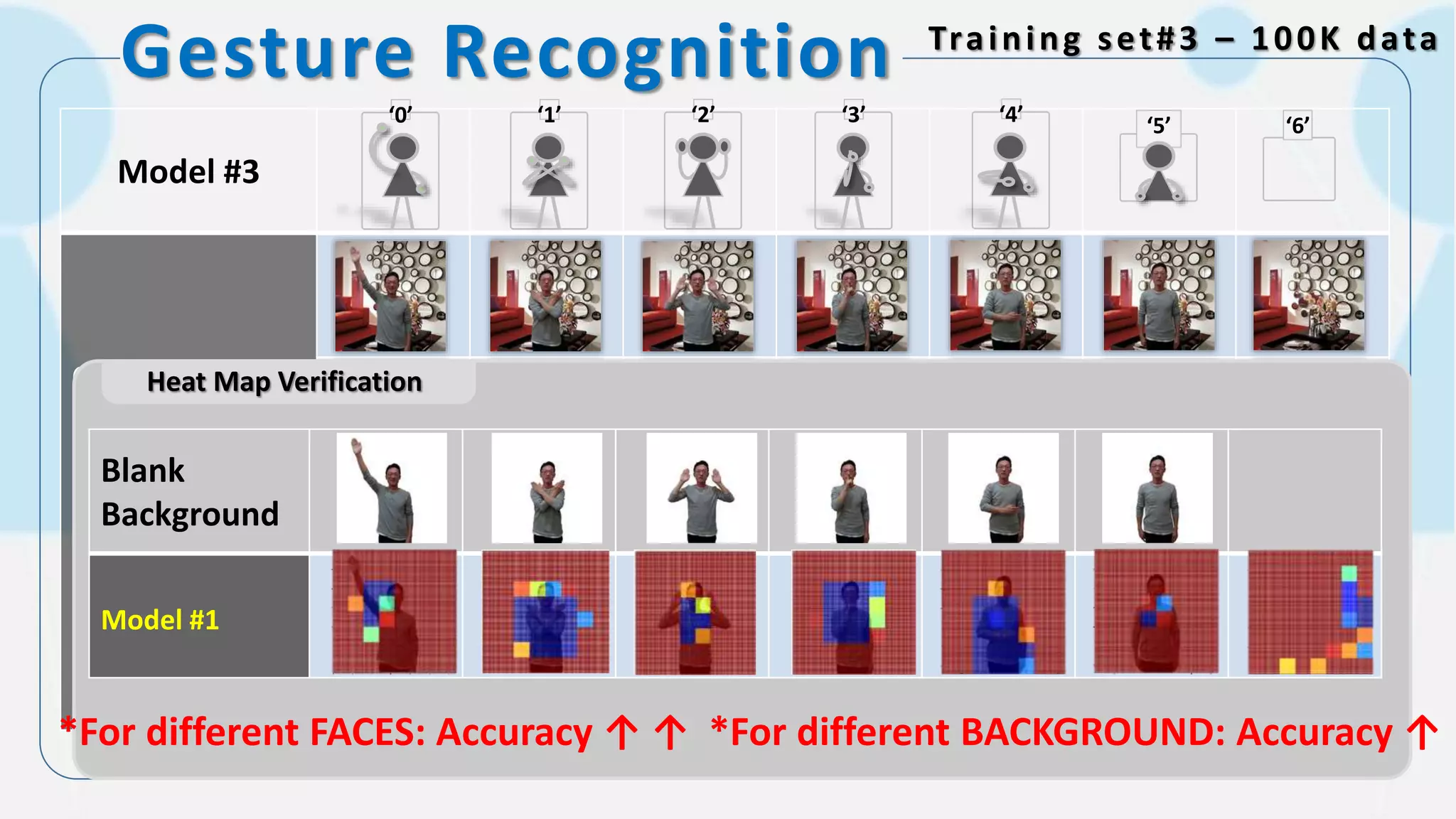
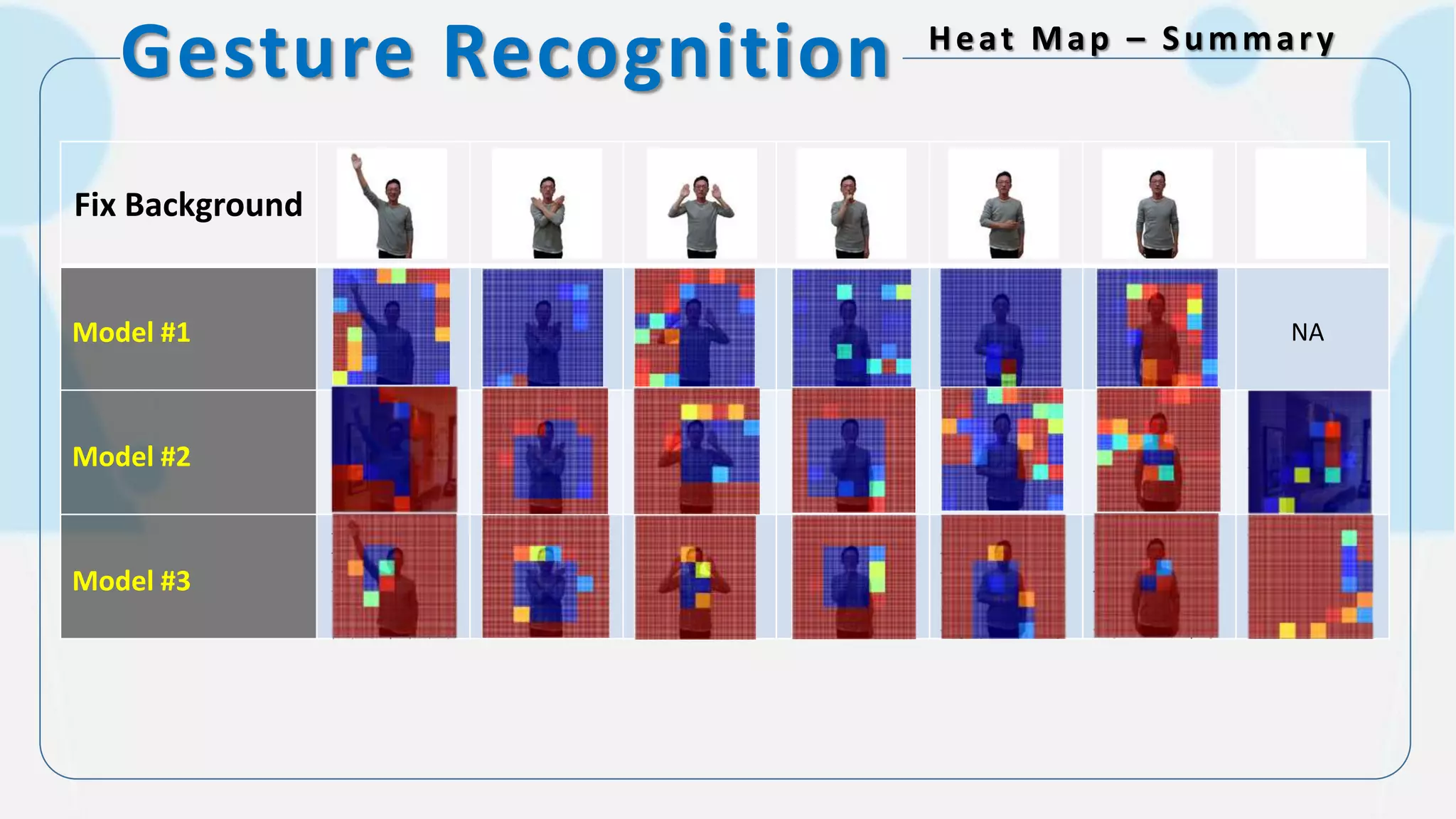
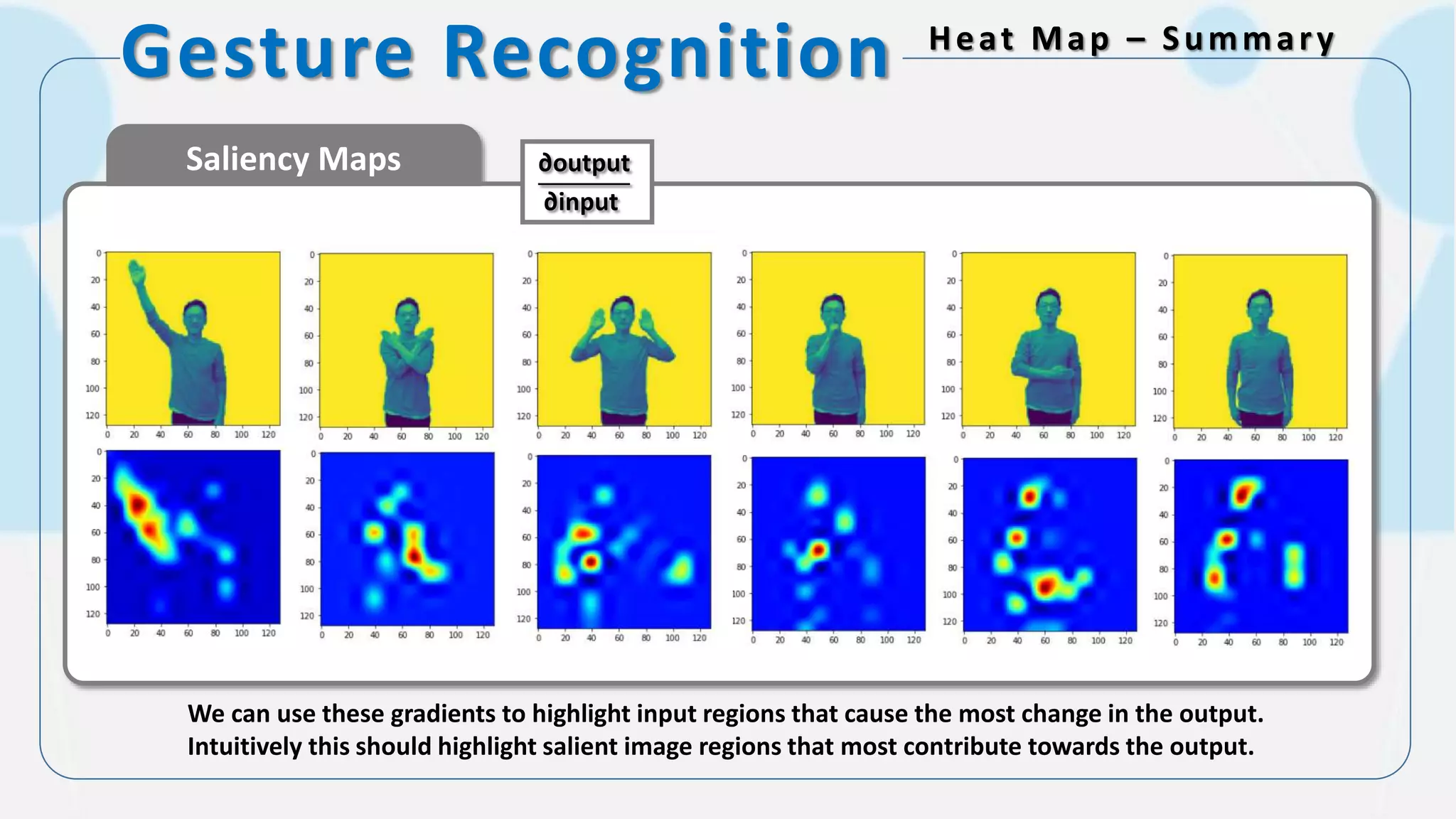
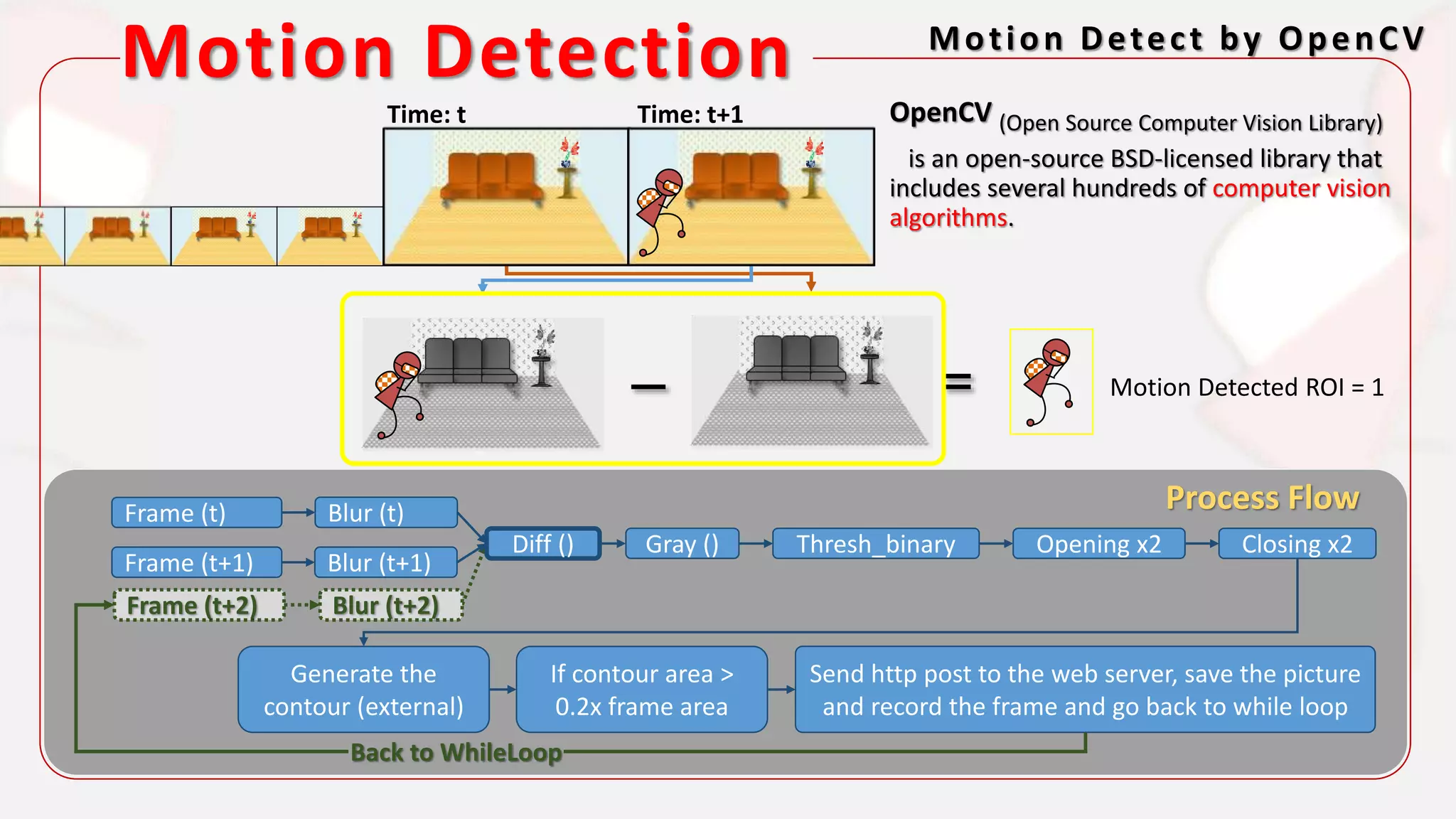
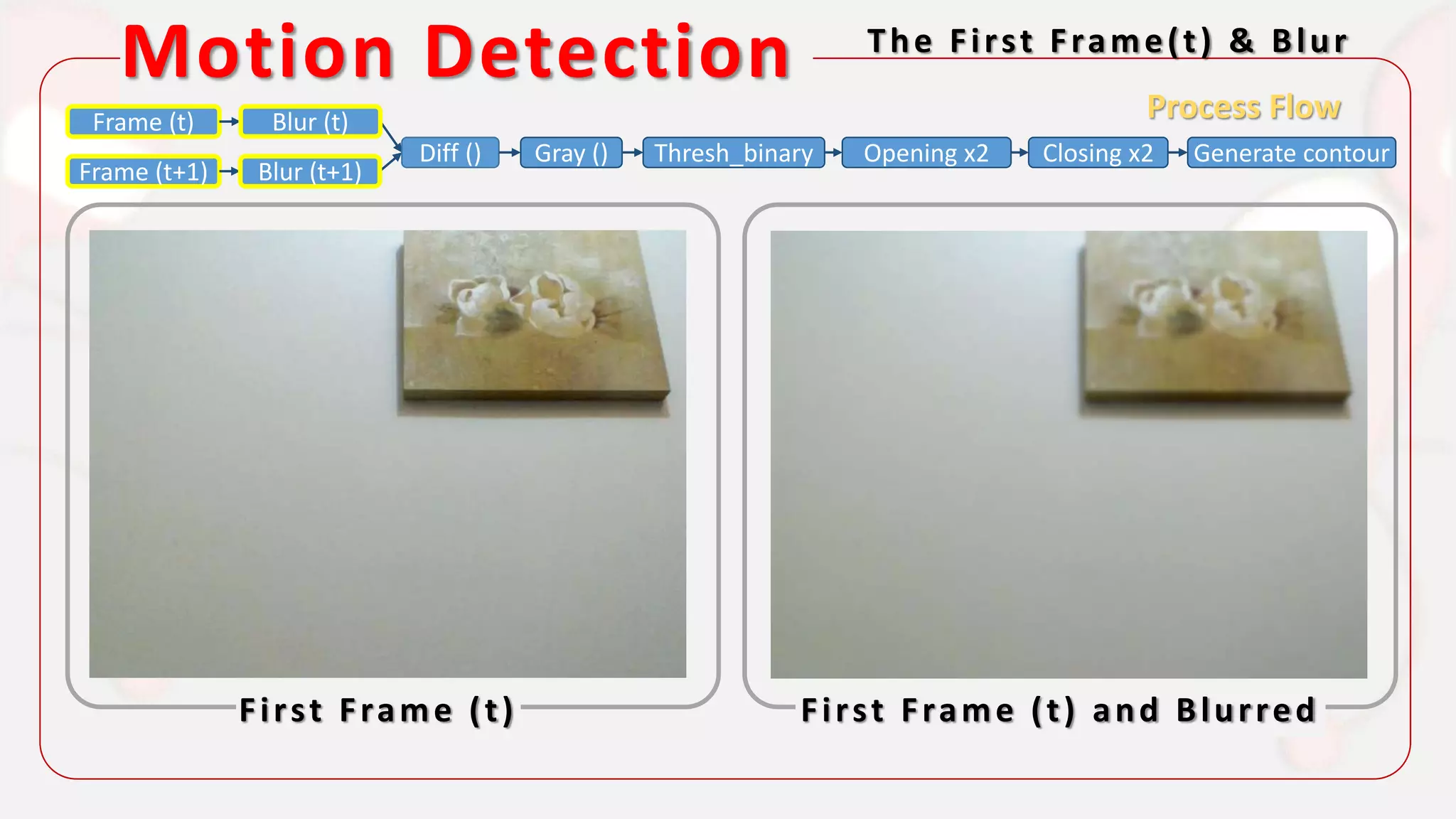
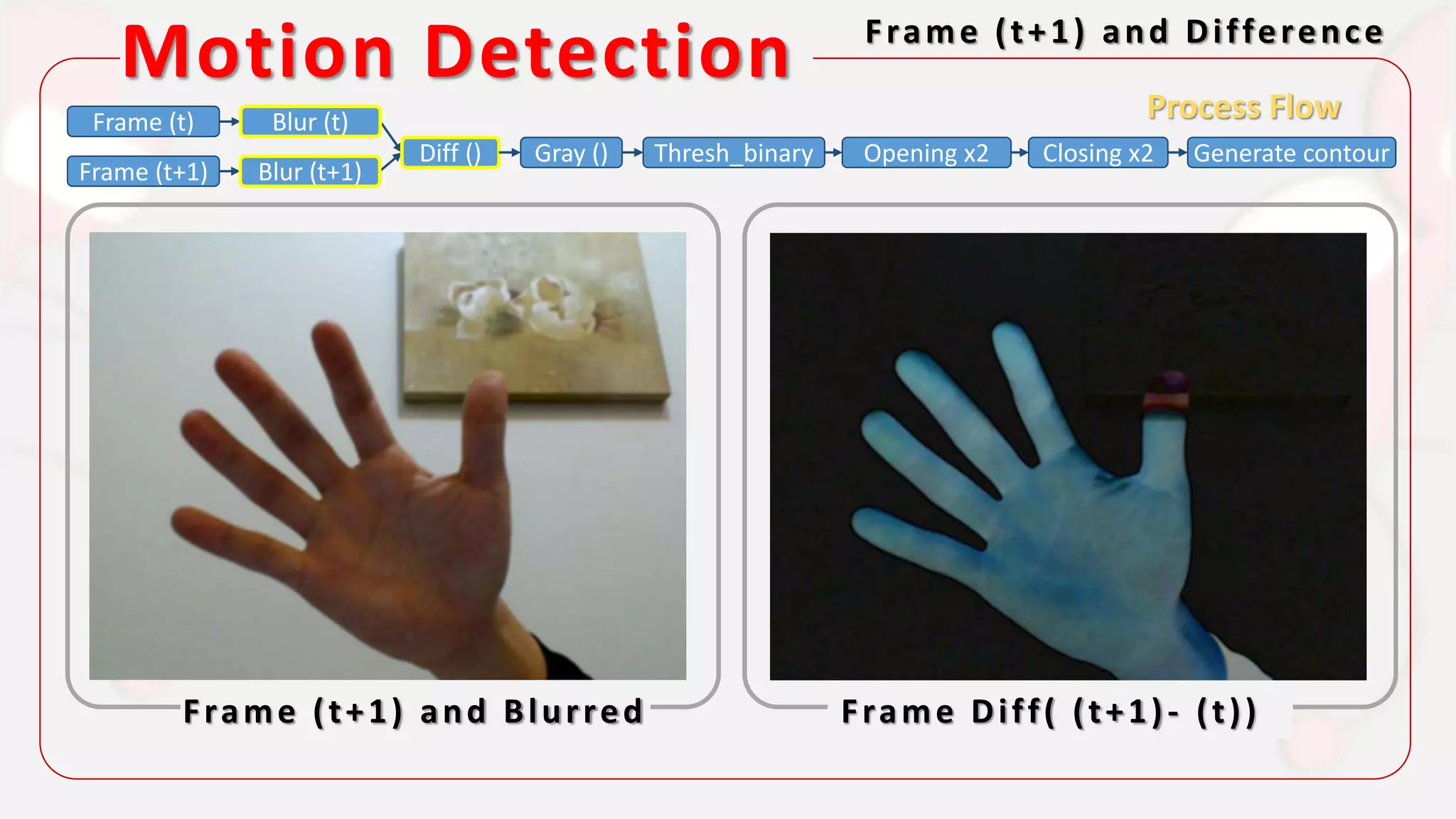
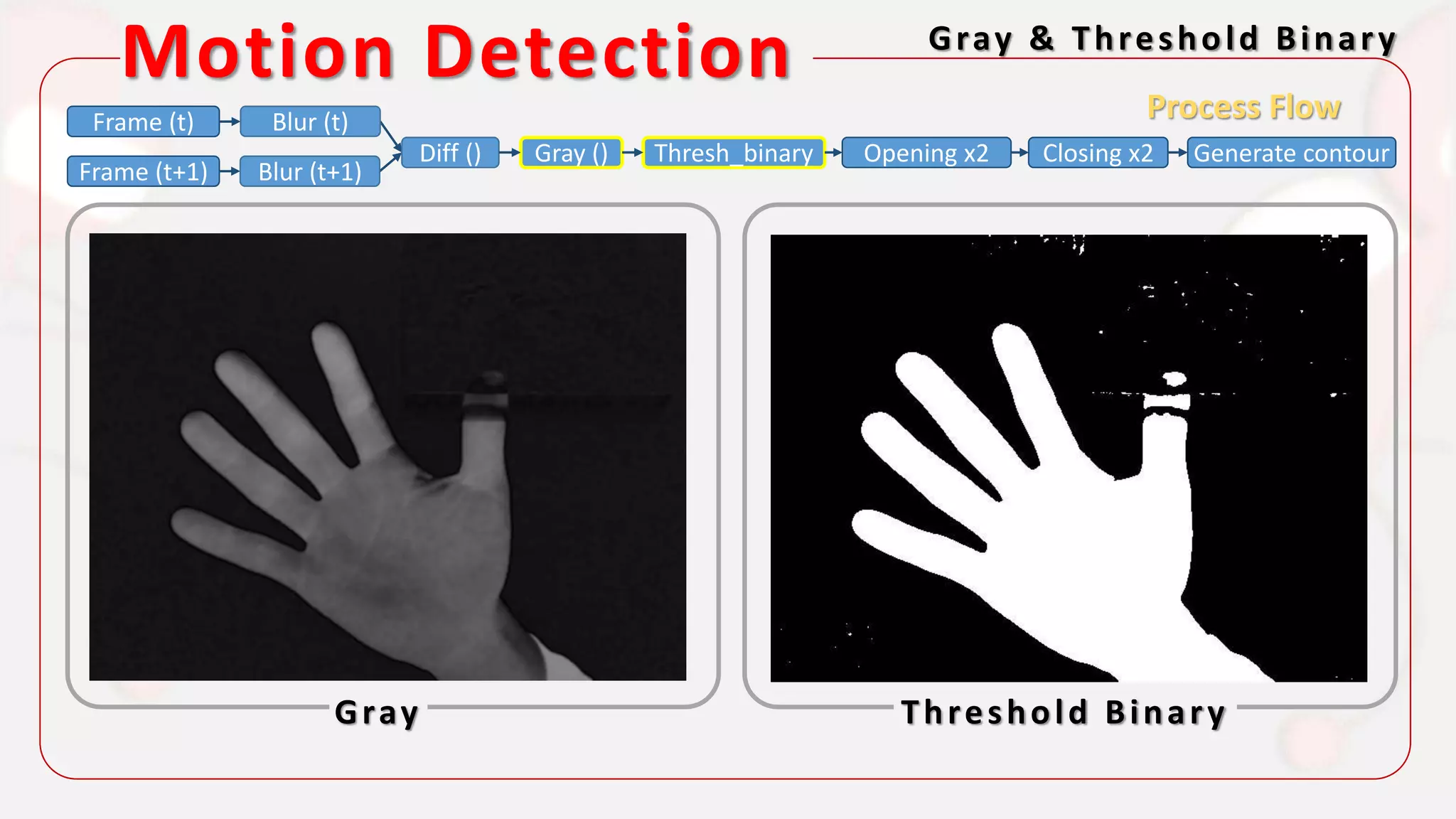
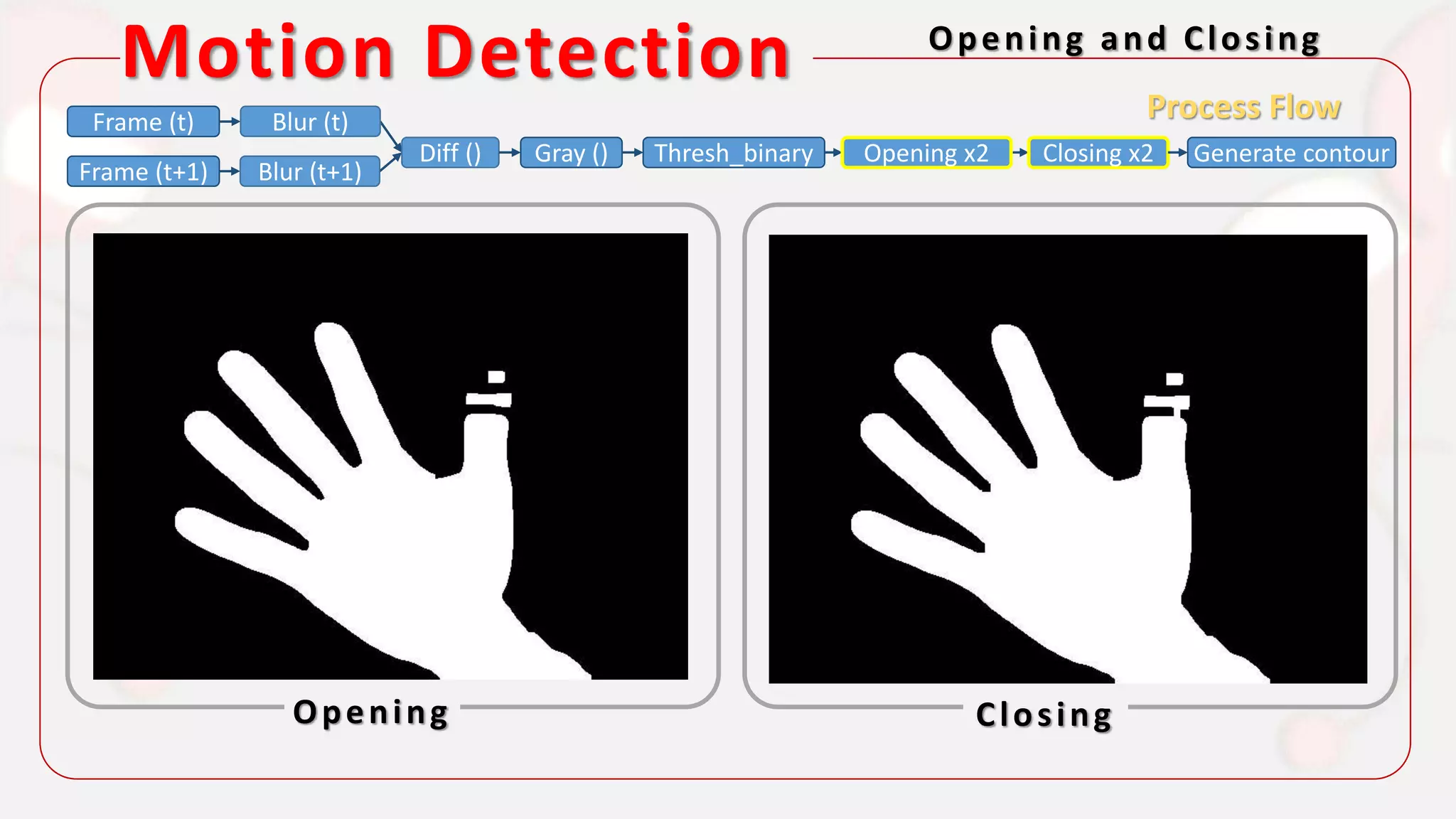
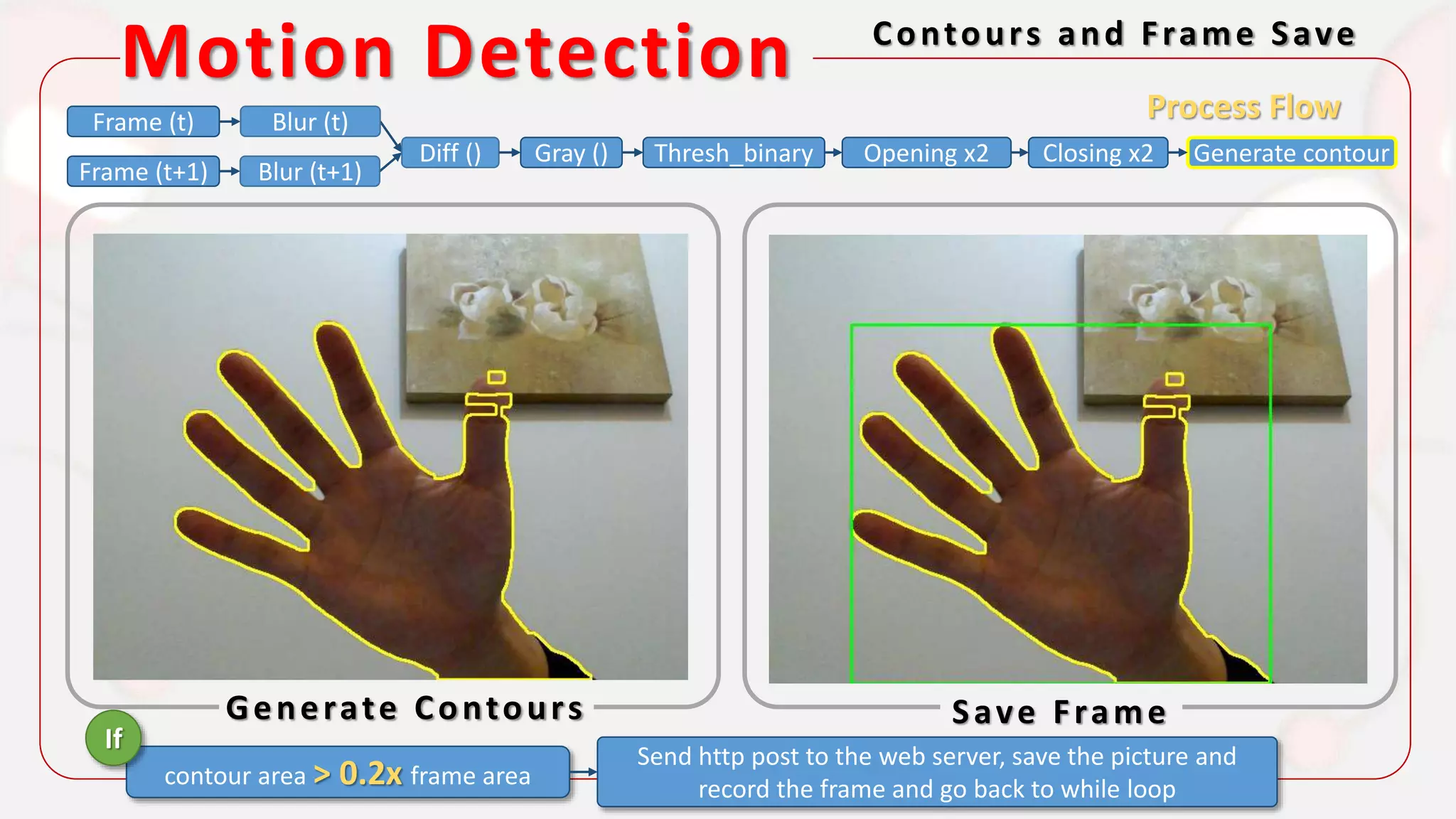
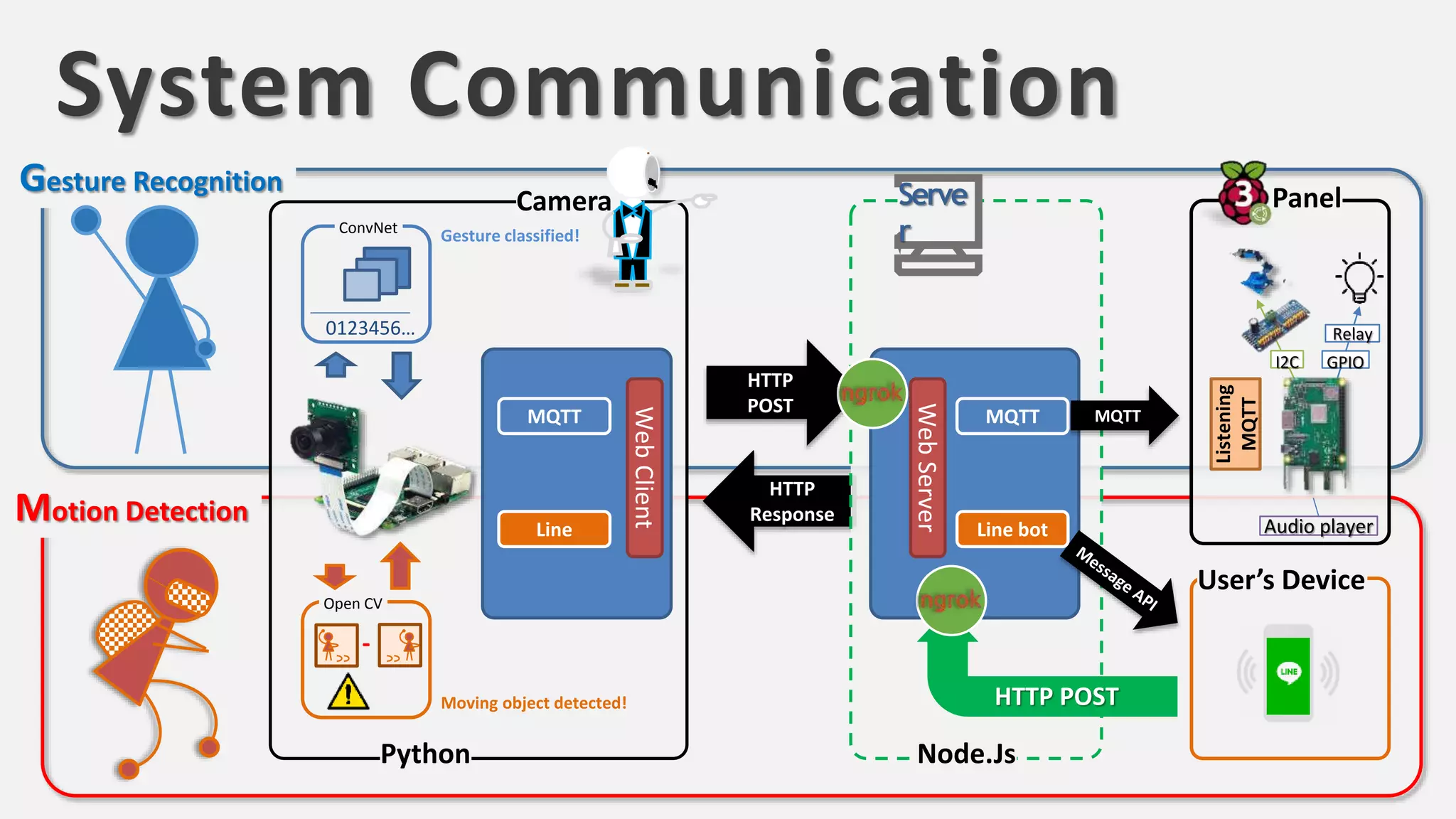
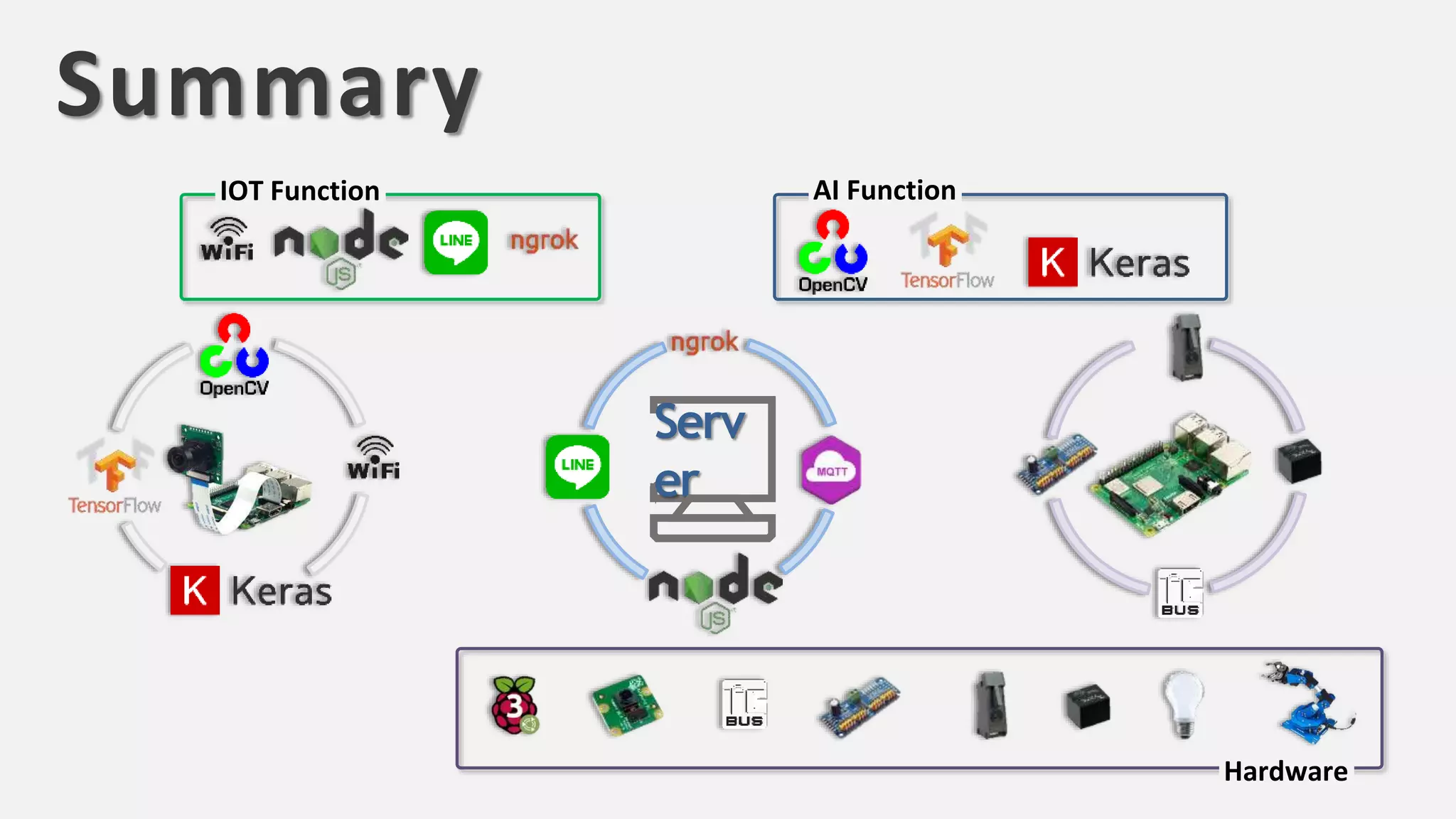
The document discusses the integration of AI in smart home cameras, focusing on gesture recognition and motion detection functionalities. It describes the process of training models for recognizing various gestures and outlines the technical flow of motion detection utilizing OpenCV. Additionally, it details the communication between devices using protocols like HTTP and MQTT for real-time responses and interactions.