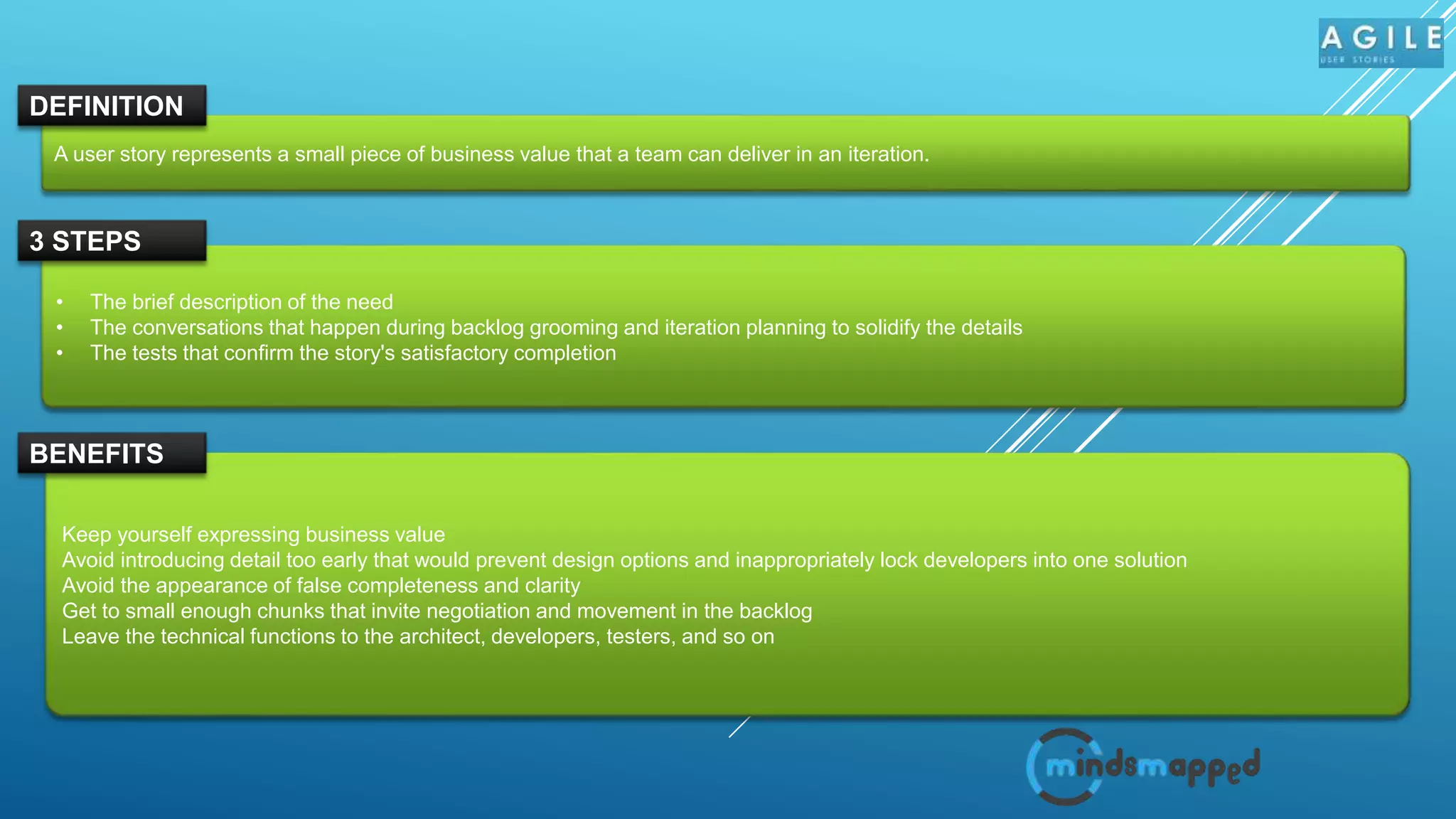
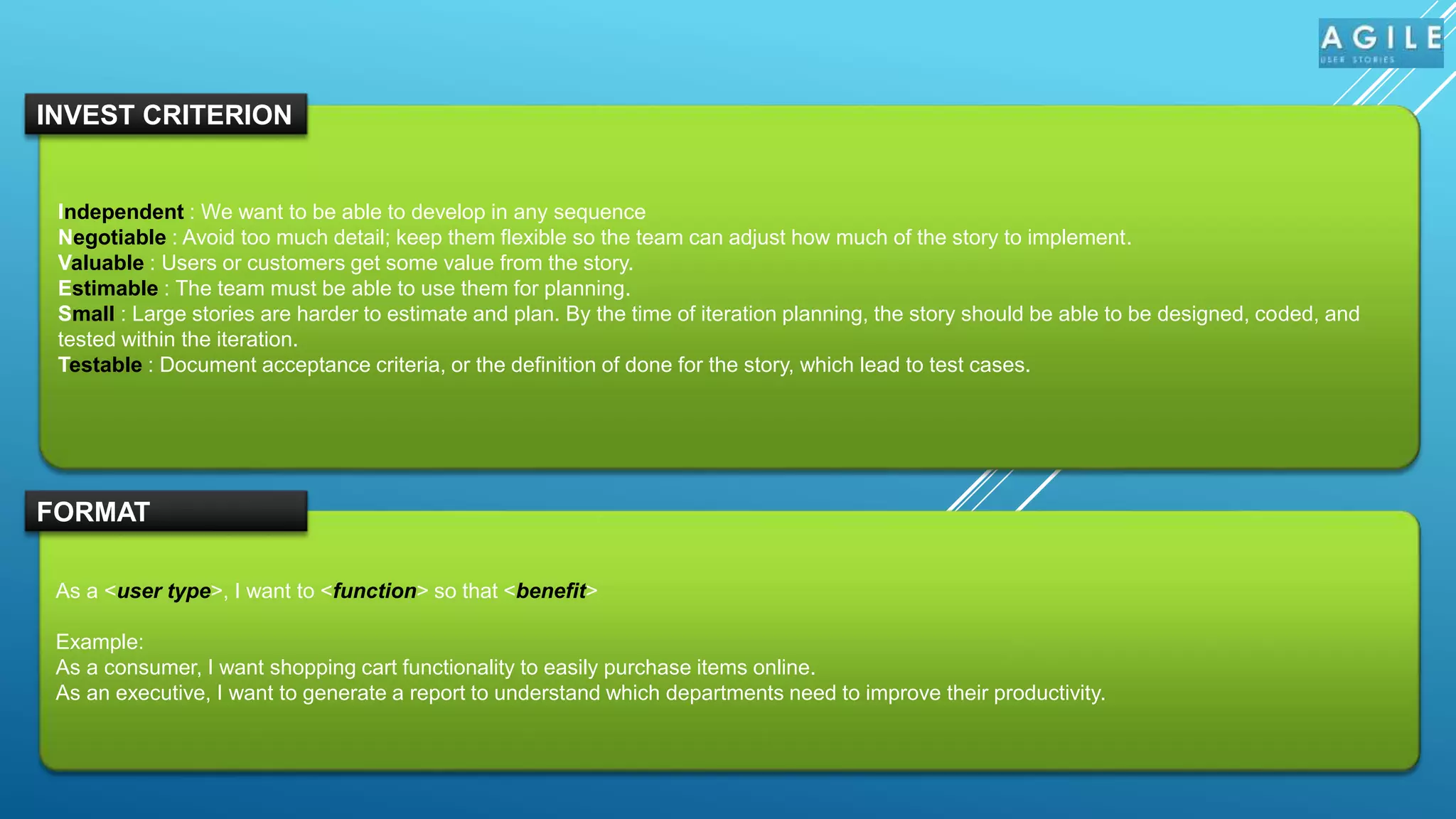
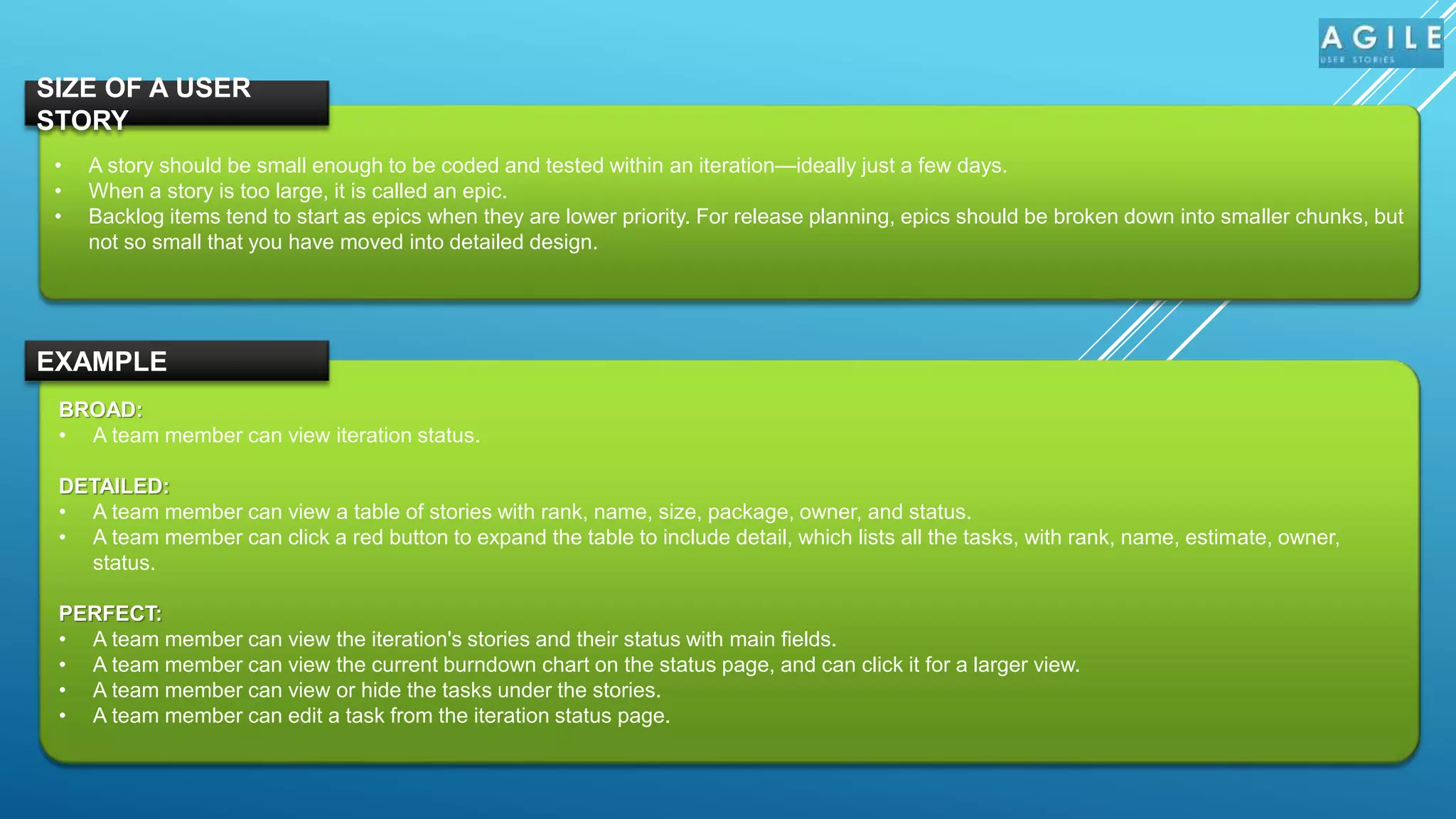
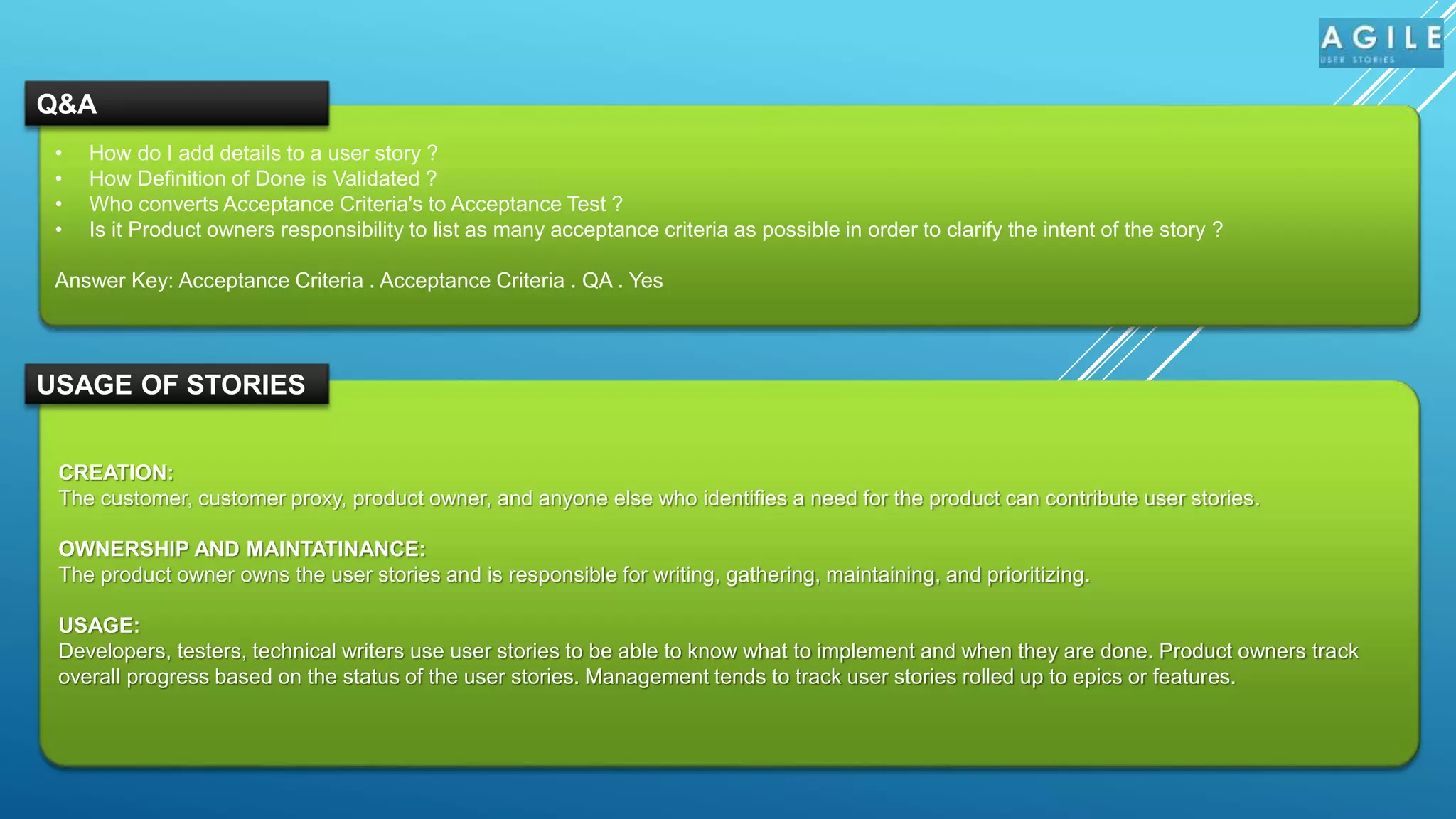
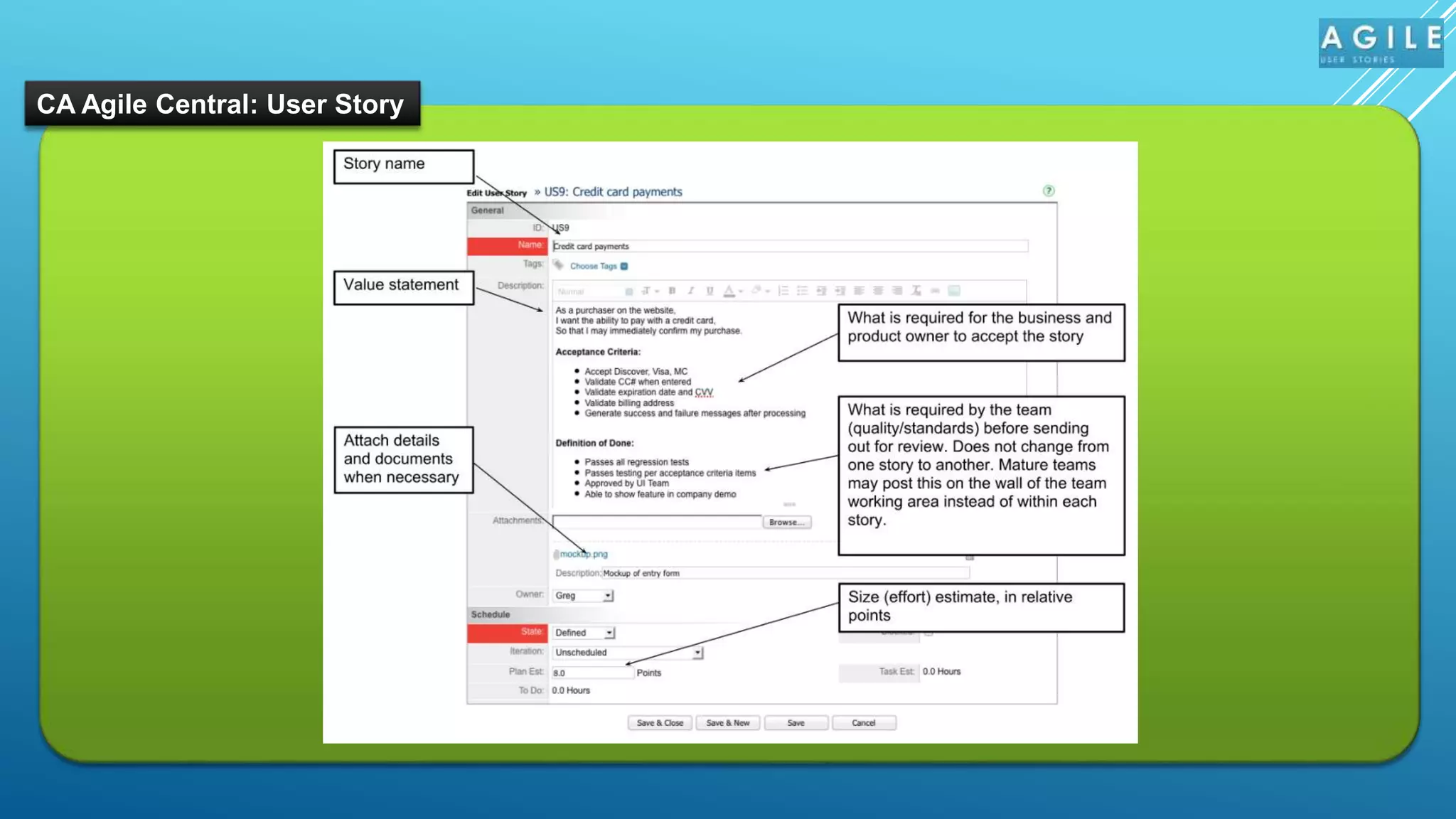
The document outlines the significance of user stories in Agile methodology, emphasizing their role as small, negotiable pieces of business value to be delivered in iterations. It details the INVEST criteria for effective user stories—Independent, Negotiable, Valuable, Estimable, Small, and Testable—and common pitfalls in writing them, such as being overly detailed or treating technical tasks as stories. Additionally, it highlights the collaborative nature of creating user stories involving various stakeholders and the responsibilities of product owners in managing them.