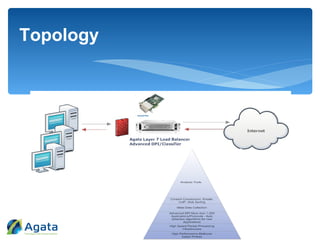
Agata Solutions, founded in 2008, specializes in high-performance network intelligence and security solutions for various sectors, including government and enterprises. Their technology focuses on real-time and historical analysis of network data, packet capture, and detecting threats like malware and data theft through a dynamic DPI engine capable of handling 20 Gbps traffic. The system supports extensive reporting and data analysis, ensuring full visibility and protection against cyber risks with capabilities like layer 7 load balancing and content filtering.