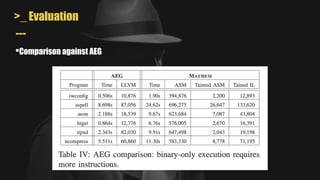
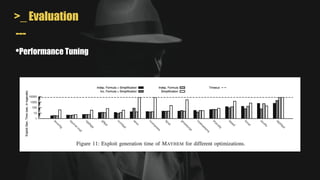
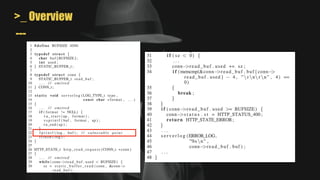
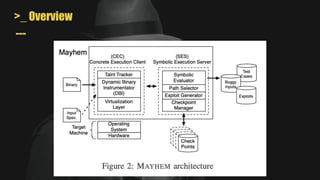
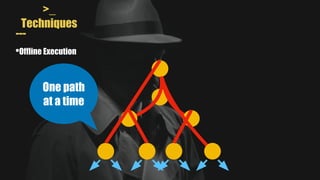
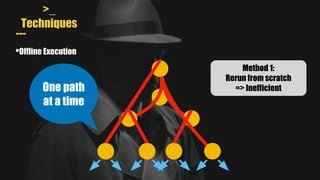
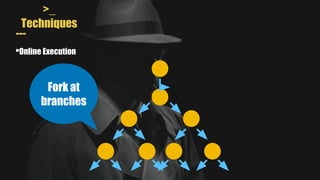
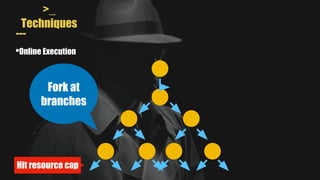
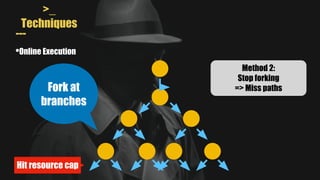
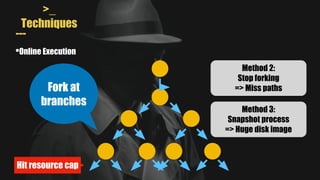
- MAYHEM is a system for automatically generating exploits by combining concrete and symbolic execution. It aims to maximize the amount of work done while minimizing wasted effort.
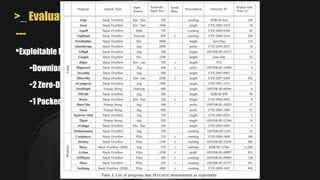
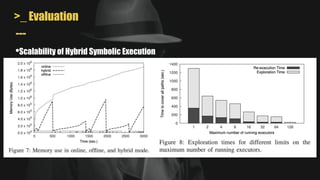
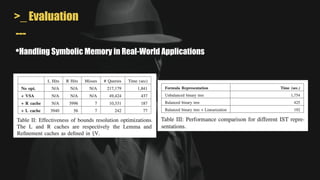
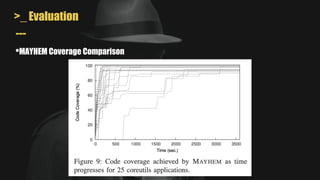
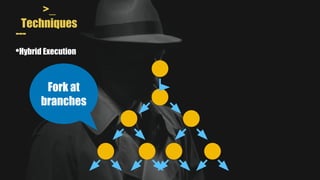
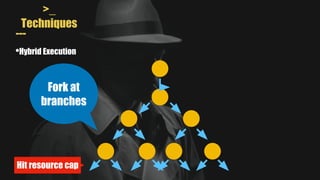
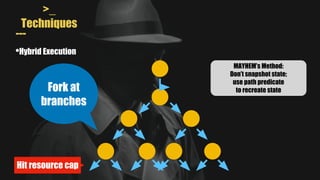
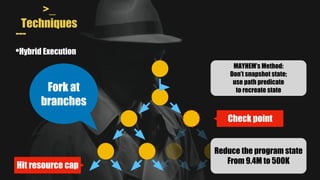
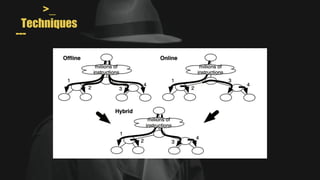
- It uses a hybrid execution approach where it concurrently runs a concrete executor client and symbolic executor server. The client explores new paths while the server performs symbolic analysis.
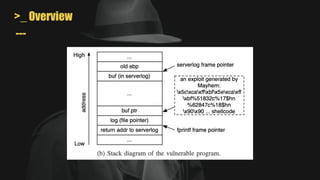
- A key challenge is handling symbolic memory addresses, which MAYHEM addresses through techniques like value set analysis to bound possible addresses and index search trees to efficiently search the memory state space.














![>_
Techniques
---
•Symbolic indices
x = user_input();
y = mem[x];
assert ( y == 42 );](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-36-320.jpg)
![>_
Techniques
---
•Symbolic indices
x = user_input();
y = mem[x];
assert ( y == 42 );
x can be everything
Which memory cell
contains 42?](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-37-320.jpg)
![>_
Techniques
---
•Symbolic indices
x = user_input();
y = mem[x];
assert ( y == 42 );
x can be everything
Which memory cell
contains 42?
2^32 cells to check
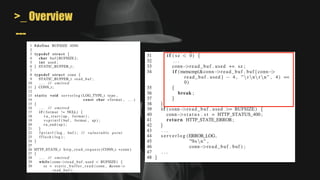
Memory
0 2^32 - 1](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-38-320.jpg)
![>_
Techniques
---
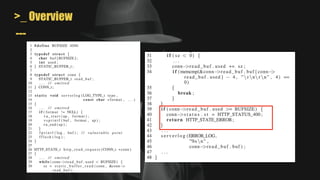
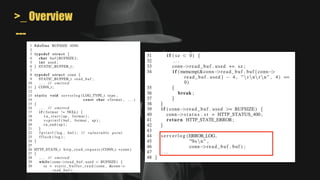
•One cause: overwritten pointers
arg
ret addr
ptr
buf
assert ( *ptr == 42 );
return;
mem[0x11223344]
ptr = 0x11223344](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-39-320.jpg)
![>_
Techniques
---
•One cause: overwritten pointers
AAAAAAA
AAAAAAA
AAAAAAA
AAAAAAA
assert ( *ptr == 42 );
return;
mem[input]
ptr = input](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-40-320.jpg)

![>_
Techniques
---
•Method 1: Concretization
mem[x] = 42;
x = 17;
mem[x] = 42;](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-42-320.jpg)
![>_
Techniques
---
•Method 2: Fully symbolic
mem[x] = 42;
mem[0] = v … mem[2^32-1] = v
0 2^32-1](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-43-320.jpg)
![>_
Techniques
---
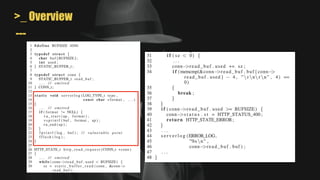
•Observation
x can be everything
x <= 42
x >= 50
y = mem[x]
F T
F T
42 < x < 50](https://image.slidesharecdn.com/unleashingmayhemonbinarycode-221012091709-948ac6e4/85/Unleashing-MAYHEM-On-Binary-Code-44-320.jpg)