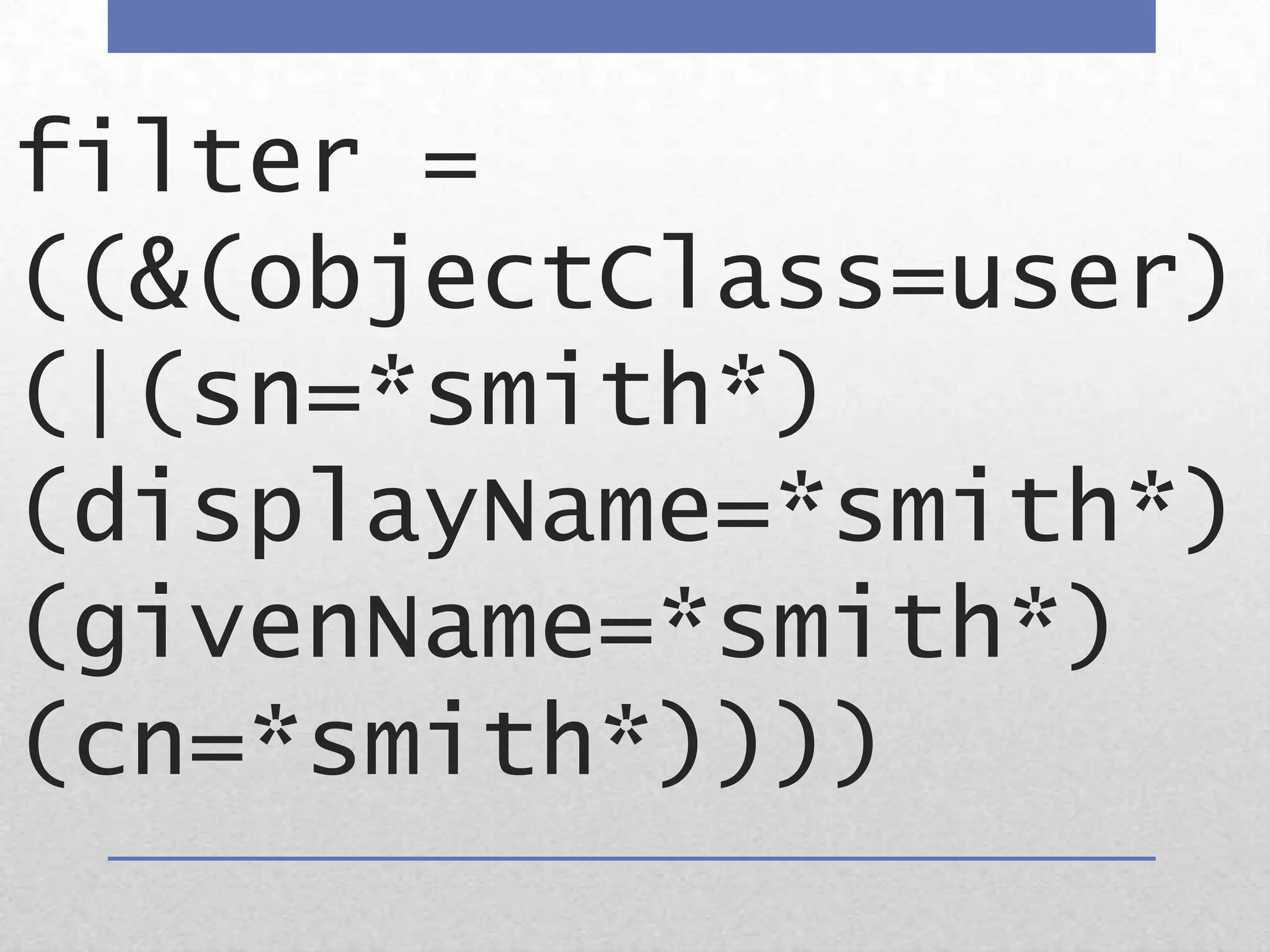
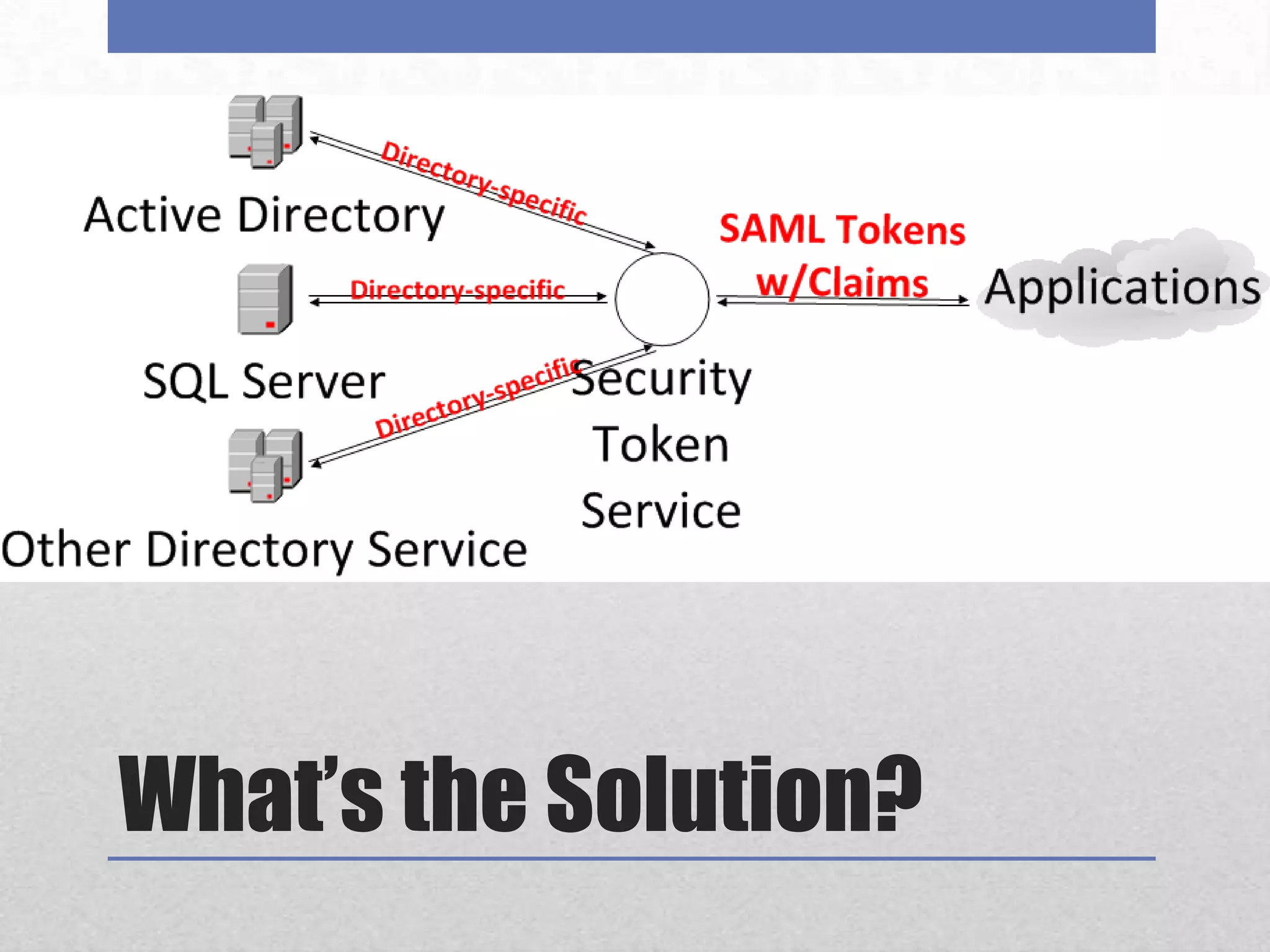
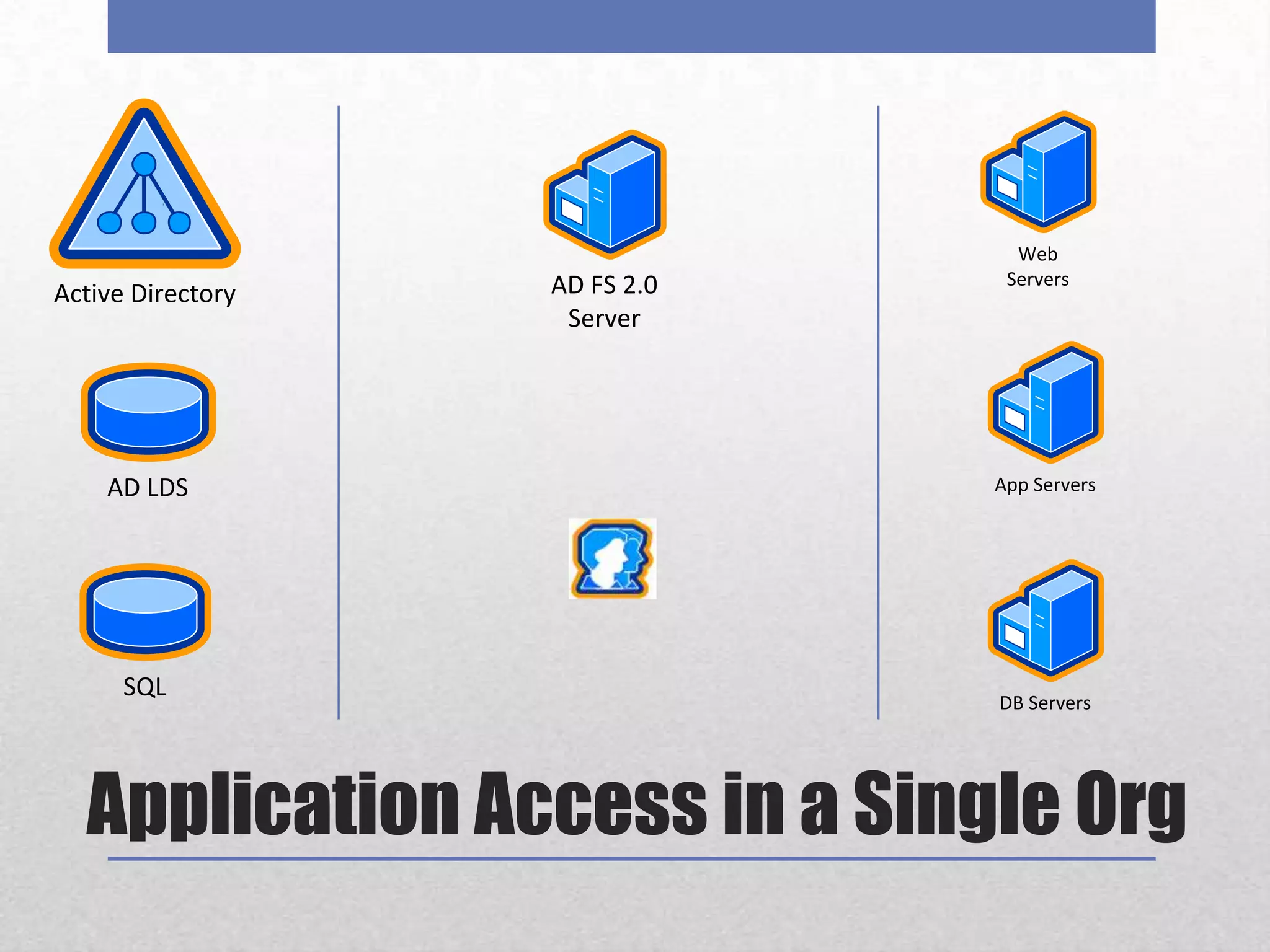
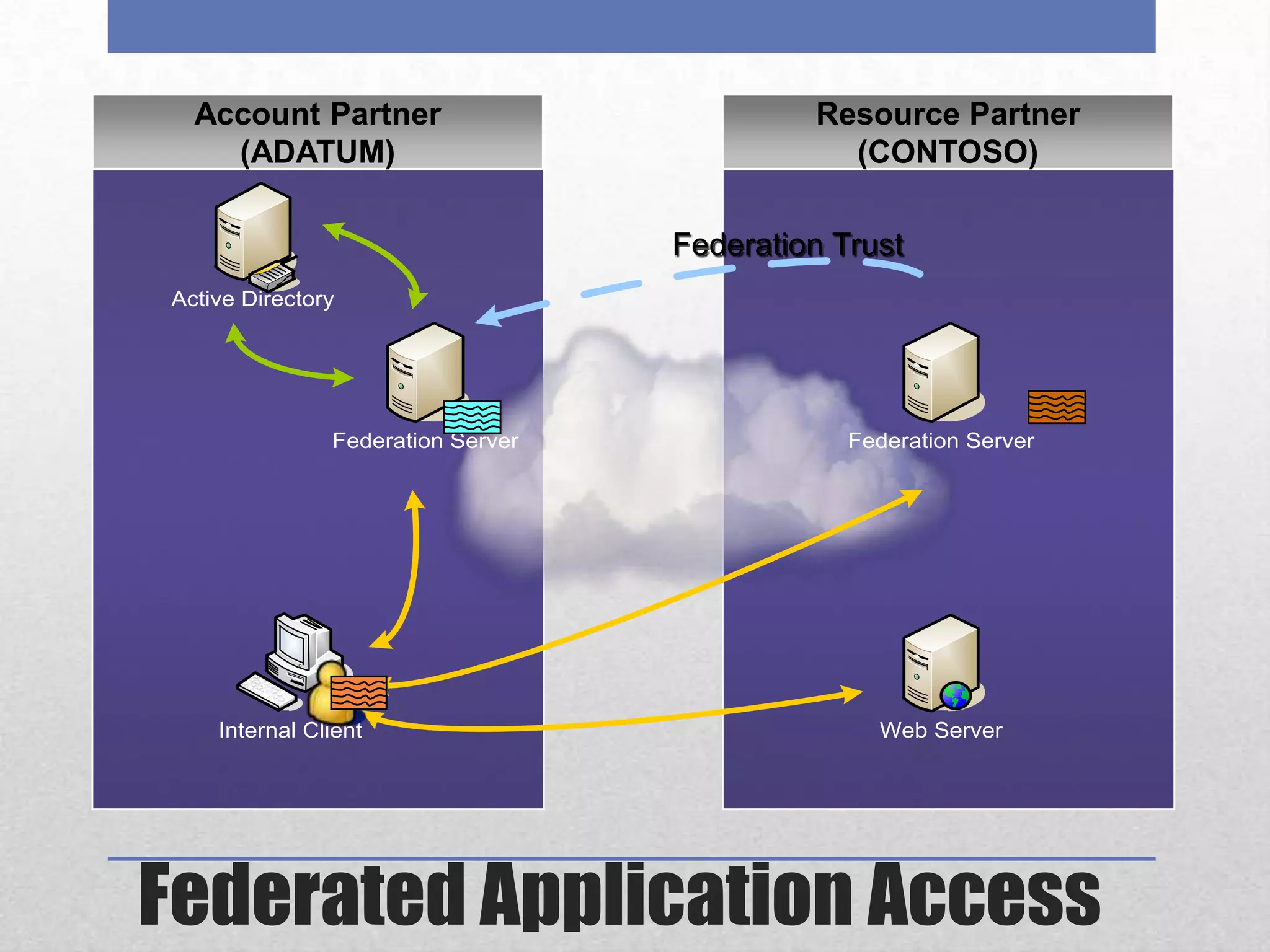
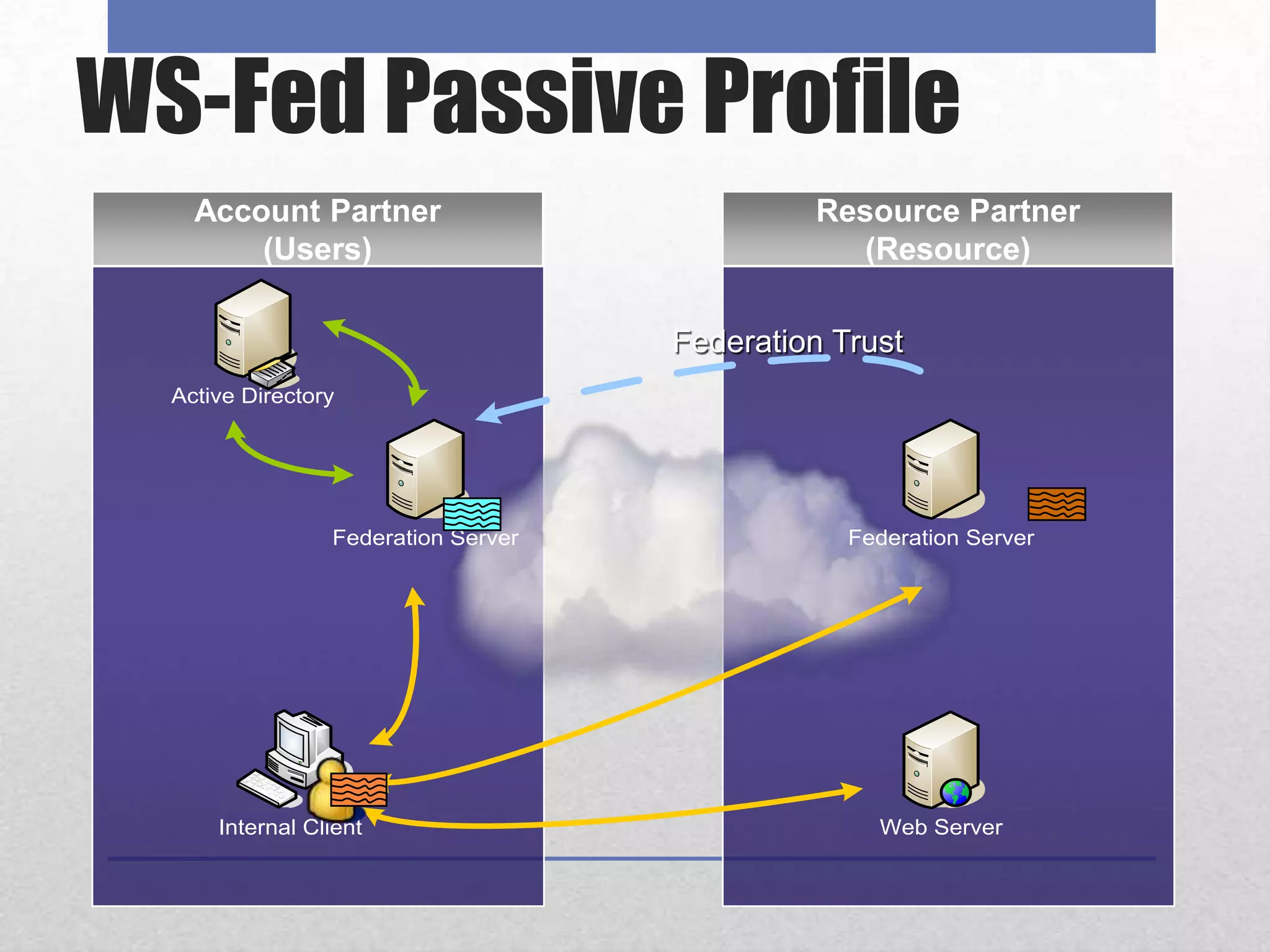
AD FS 2 & Claims-Based Identity provides a consistent identity layer across applications by extracting identity information from Active Directory and other sources and expressing it as standardized claims. This allows applications to authenticate users once via AD FS and receive attributes about the user, without the applications needing direct access to identity stores. Claims can include group memberships, email address, or any other identity attributes that can be used for authorization and personalization. AD FS supports web single sign-on, web services, and "claims-aware" applications via standards like WS-Federation, SAML 2.0, and can federate identity across organizations.