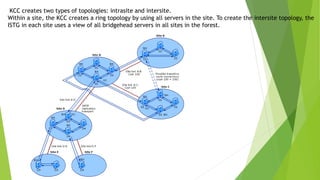
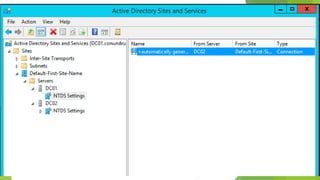
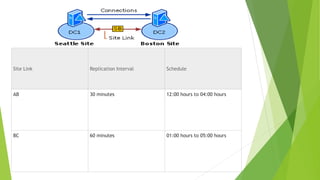
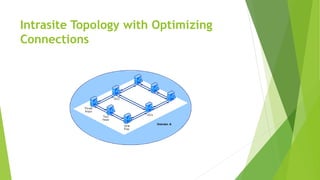
Active Directory uses sites and replication topology to optimize traffic between domain controllers. The Knowledge Consistency Checker (KCC) generates replication topologies within and between sites. The KCC runs locally on each domain controller and communicates with other KCCs through RPC calls to identify replication errors. One domain controller per site is selected as the Intersite Topology Generator (ISTG) to manage bridgehead servers for site-to-site replication. The KCC and ISTG work together to automatically configure and maintain an optimized replication topology across all domain controllers in the Active Directory forest.