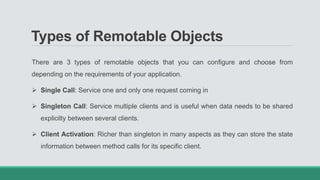
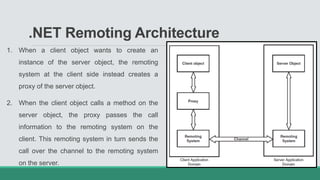
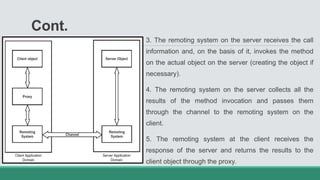
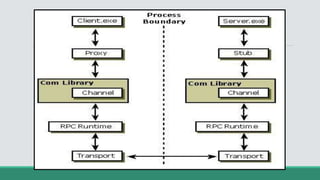
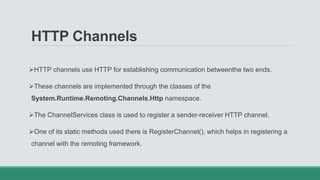
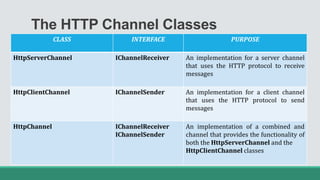
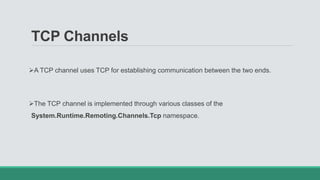
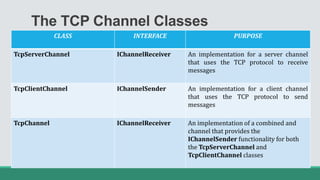
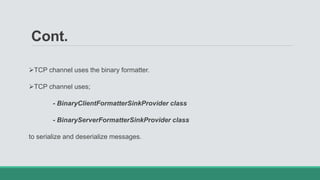
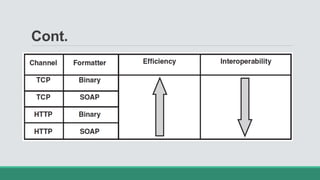
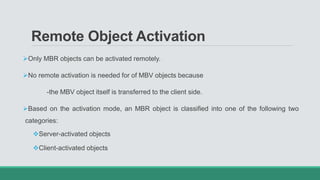
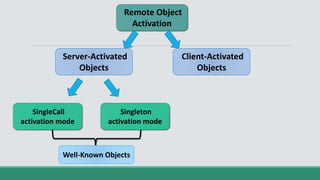
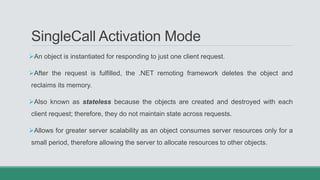
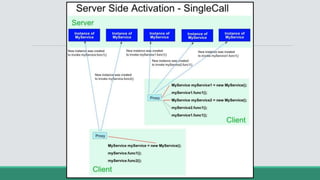
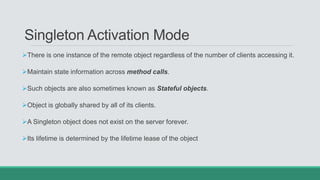
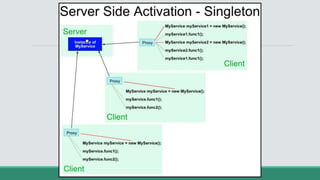
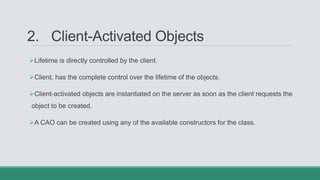
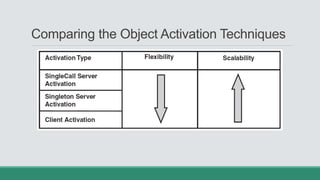
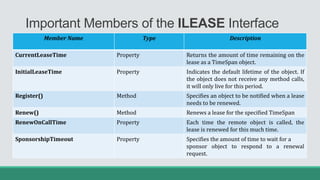
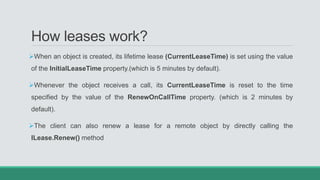
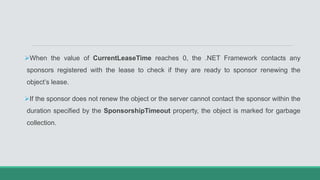
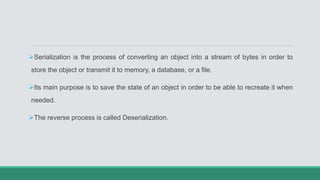
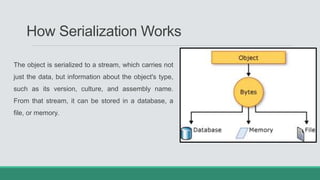
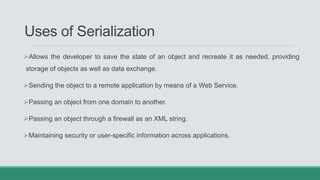
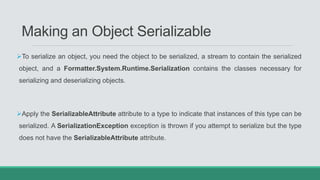
This document discusses .NET remoting and serialization. It begins by introducing application domains and distributed applications in .NET. It then covers the key concepts and components of .NET remoting including remoting namespaces, remotable objects, channels, formatters, and object lifetime management using leases. The document also compares .NET remoting to web services and discusses object marshalling and serialization.