The document discusses Win32 binary dissection, focusing on the analysis and classification of binary formats, specifically the PE/COFF format used in Windows. It covers static and dynamic analysis techniques, essential tools for dissecting binaries, and the complexity of binary compression and anti-debugging measures. Additionally, it highlights the importance of PE format for understanding malware behavior and performing binary unpacking.

![BinaryFormats
•PE/COFF [Portable Executable/Common Object File
Format]
•Ref: http://goo.gl/avLg2
Windows
•ELF [Executable and Linkable Format]
•Ref: http://goo.gl/Nd1yvG
Unix/Linux
•Mach-O File Format. Recognizes ELF formats too.
•Ref: http://goo.gl/RXKgE0
Macintosh
4Win32 Binary Dissection](https://image.slidesharecdn.com/win32binarydissection-150924113221-lva1-app6892/75/A-basic-approach-to-Understanding-Win32-Binaries-4-2048.jpg)

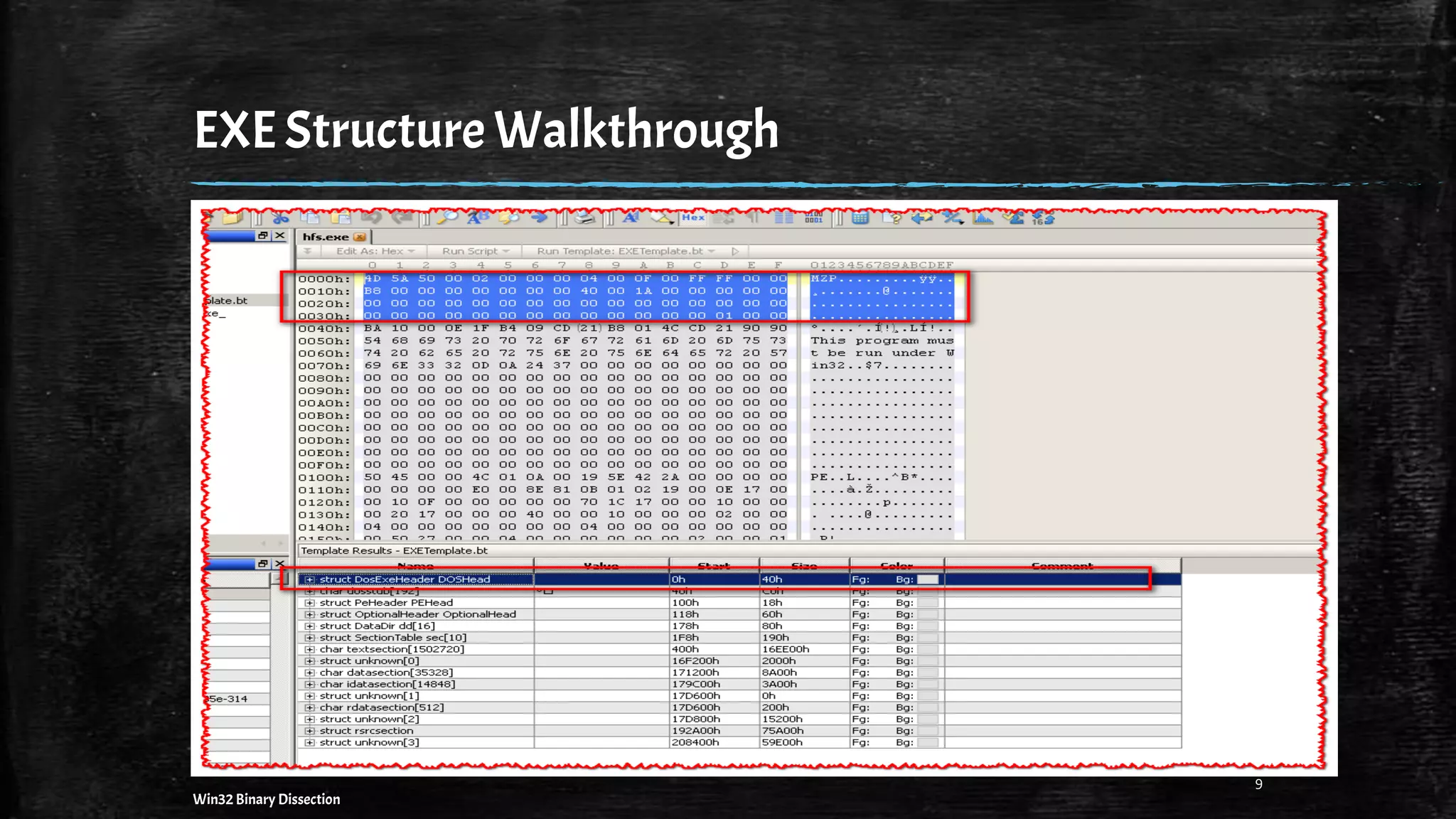
![PEFormat Walkthrough– And the boring stuff begins…
sample.exe
(windows loader kicks
in here)
Header
MZ Stub [64]
DOS Stub
[64]
PE Header [24]
Optional Header [96]
Data Directories [16]
Sections
Sections Table
[40]
CODE or .text
Imports [IAT] / Exports [EAT]
Data [Strings, Icons, Bitmaps etc.] 7Win32 Binary Dissection](https://image.slidesharecdn.com/win32binarydissection-150924113221-lva1-app6892/75/A-basic-approach-to-Understanding-Win32-Binaries-7-2048.jpg)
![Toolsof thetrade
• IDA Pro [GUI] • ImmLib [Python]
• OllyDbg//Immunity Debugger [GUI] • PEFile [Python]
• AnalyzePE [Python] • PE View / PE-Bear [GUI]
• WinDbg [GUI] • 010 Hex Editor [GUI]
• IDAPython [Python] • CFF Explorer [GUI]
Static Tools
• RegShot [GUI] • Cuckoo Framework [GUI/Web]
• FakeNet [Cmd] • Sandboxie [GUI]
• Process Explorer [GUI] • ZeroWine Sandbox [GUI]
• RegMon [GUI] • INetSim [Cmd]
• Process Hacker [GUI] • TCPView [GUI]
• IDA Pro/Olly/WinDbg [GUI] • ProcMon [GUI]
Dynamic Tools
8Win32 Binary Dissection](https://image.slidesharecdn.com/win32binarydissection-150924113221-lva1-app6892/75/A-basic-approach-to-Understanding-Win32-Binaries-8-2048.jpg)
![Letsunderstandbinariesthroughdemos!!
10Win32 Binary Dissection
▪ 010 Hex Editor [For structure parsing]
▪ UPX Compression Tool [For packing]
▪ Immunity//OllyDbg Demo [For unpacking]
▪ ImpREC [Fix IATs]](https://image.slidesharecdn.com/win32binarydissection-150924113221-lva1-app6892/75/A-basic-approach-to-Understanding-Win32-Binaries-10-2048.jpg)