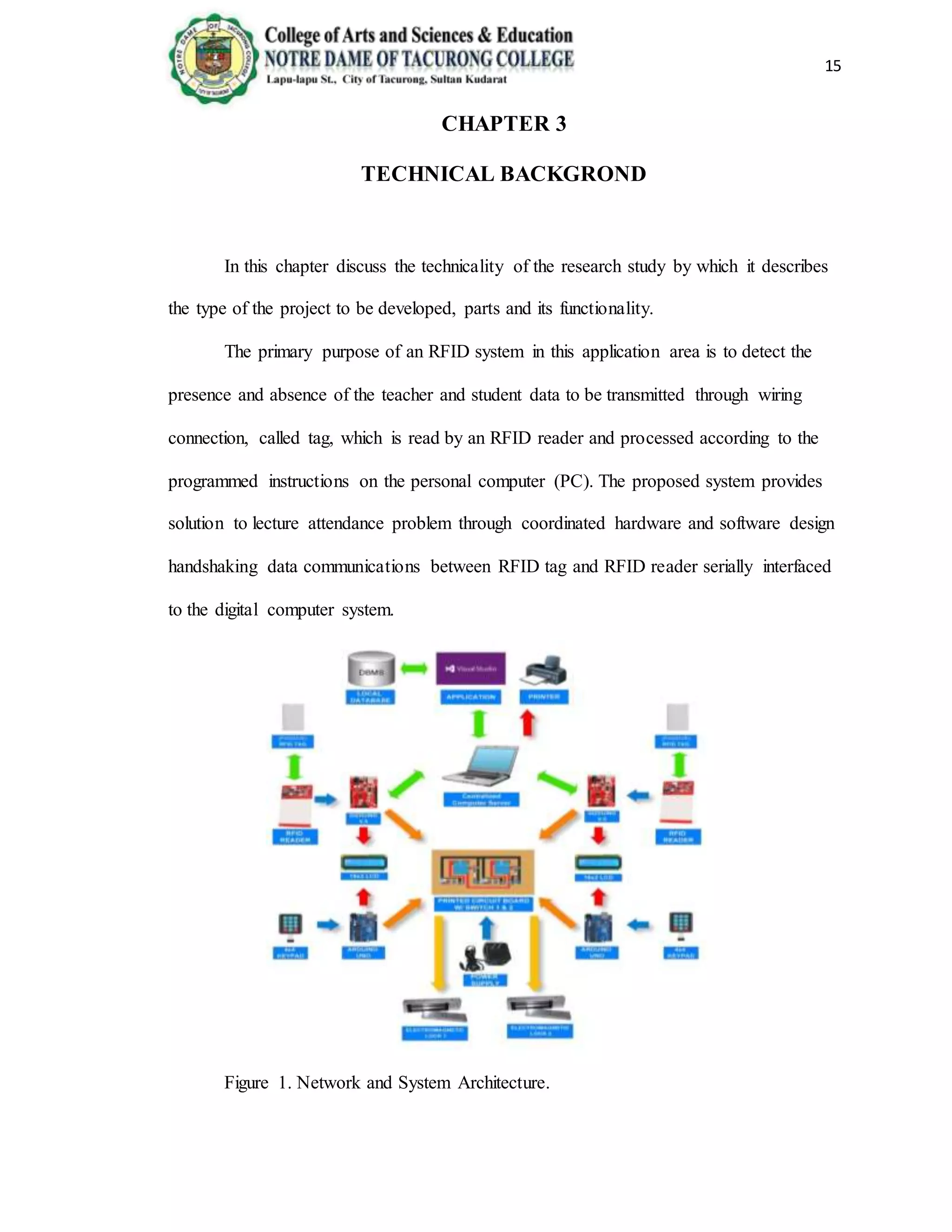
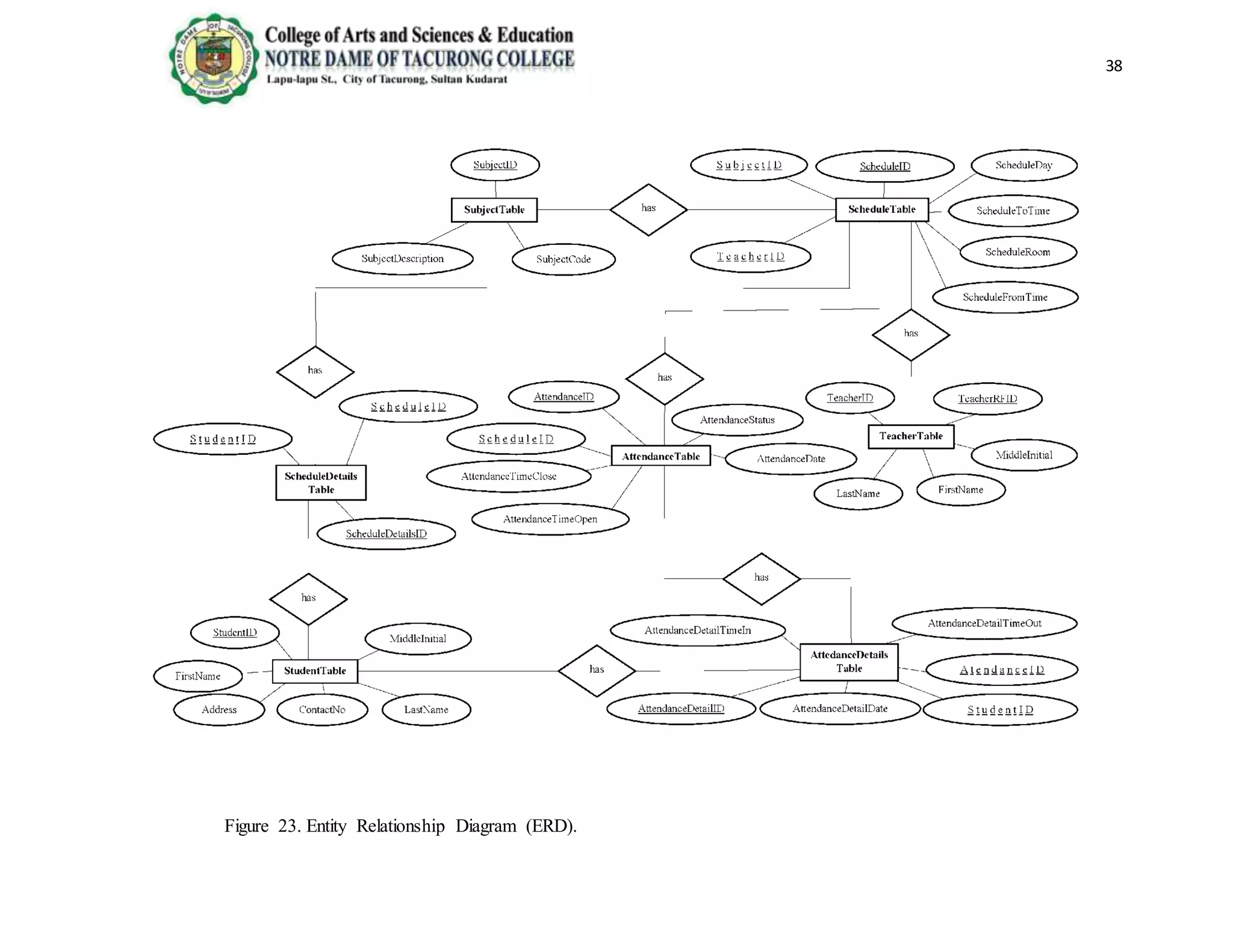
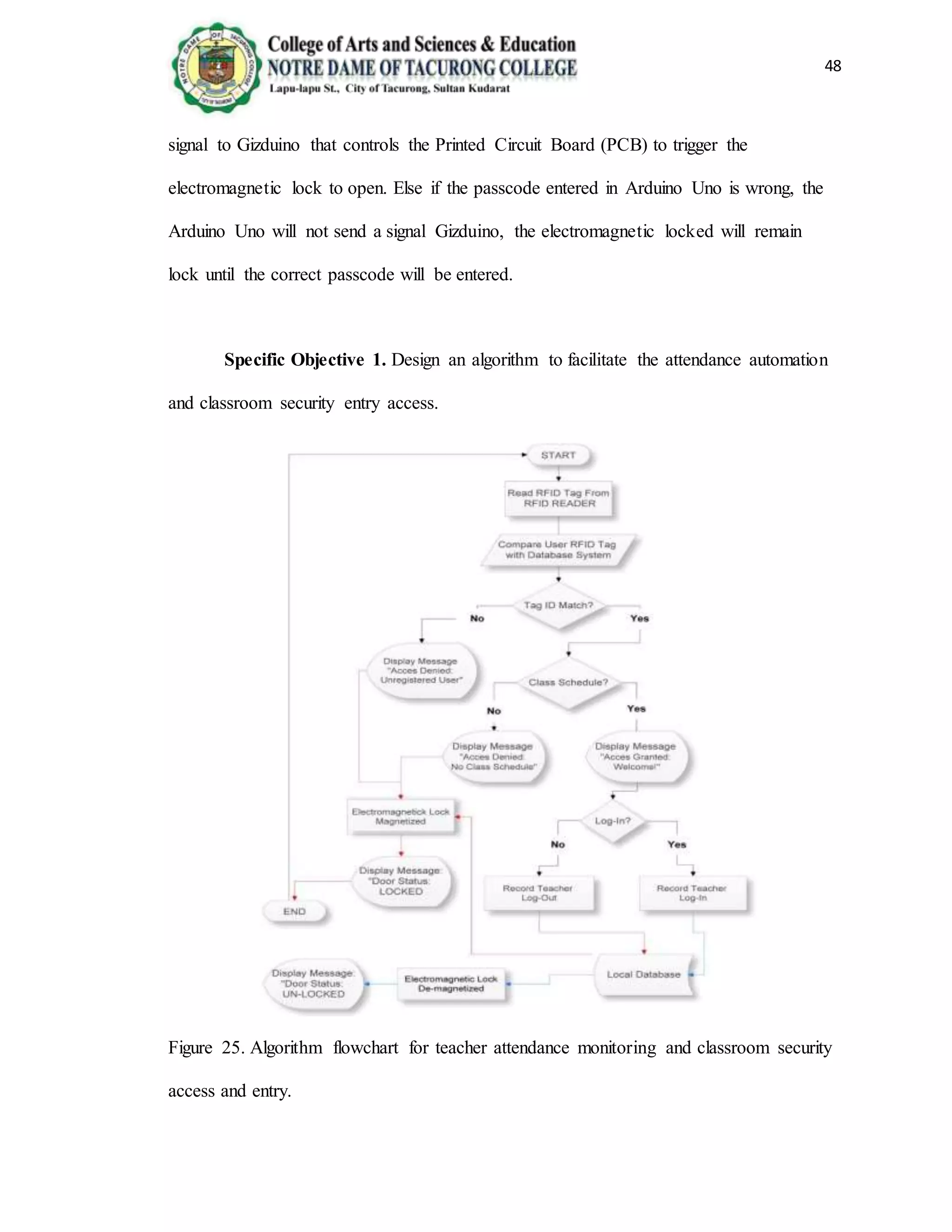
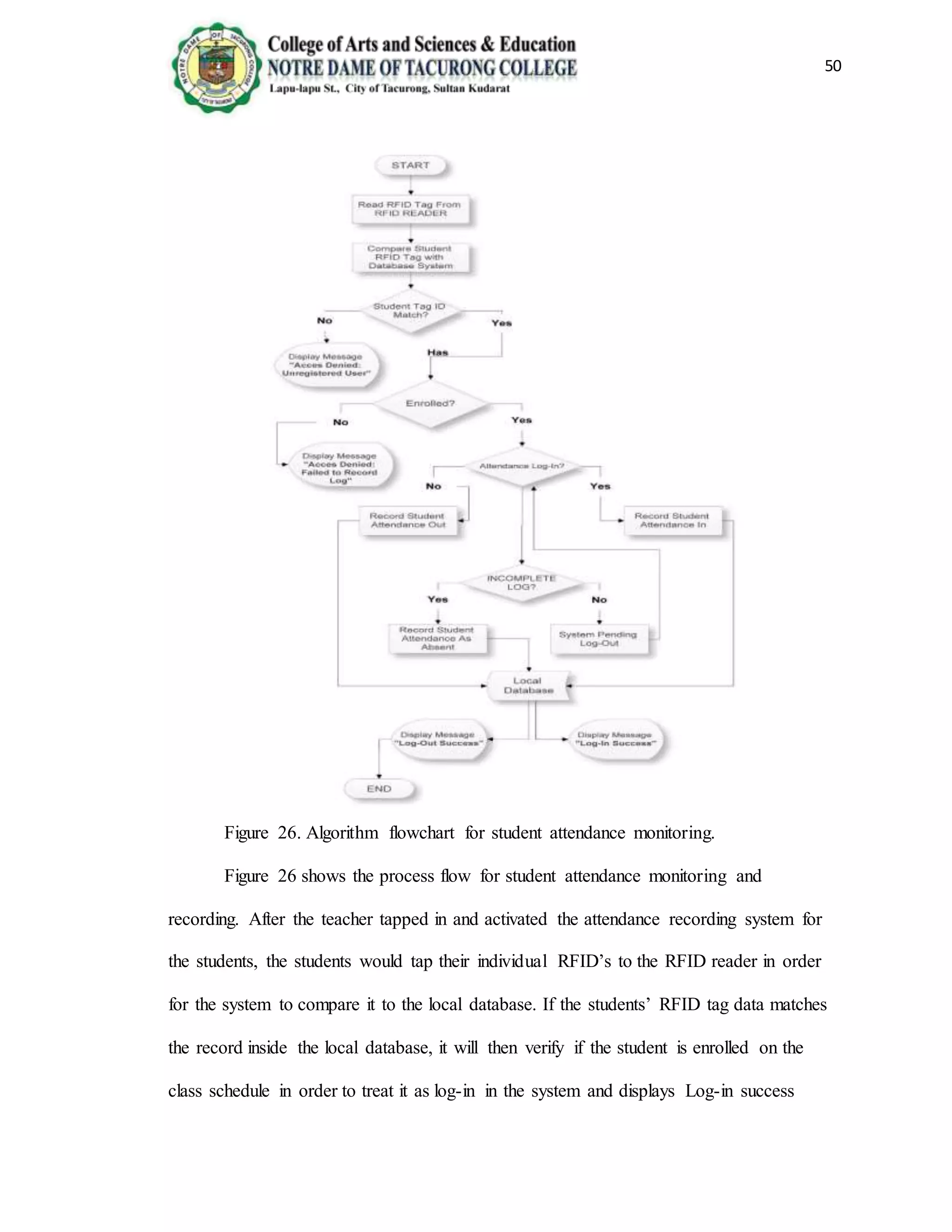
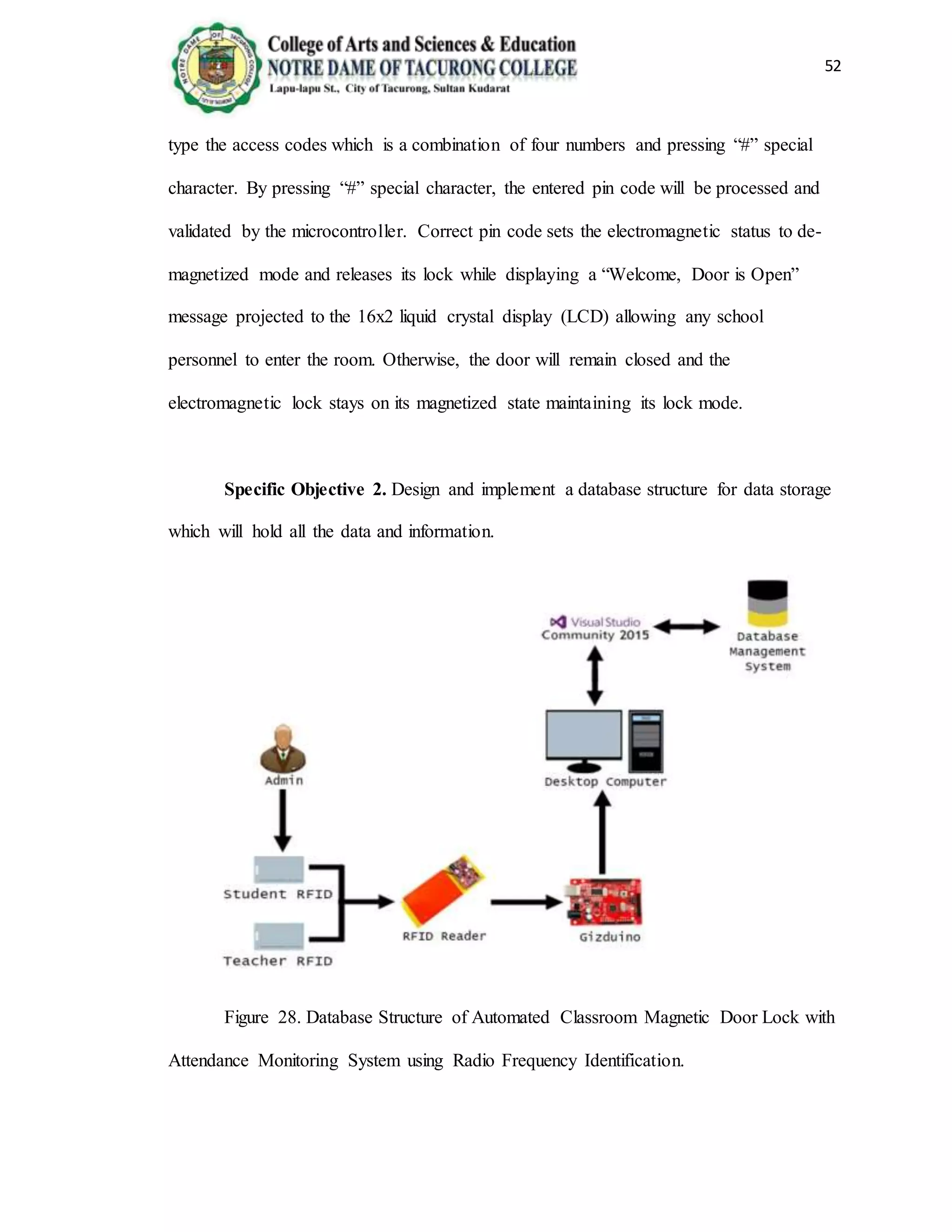
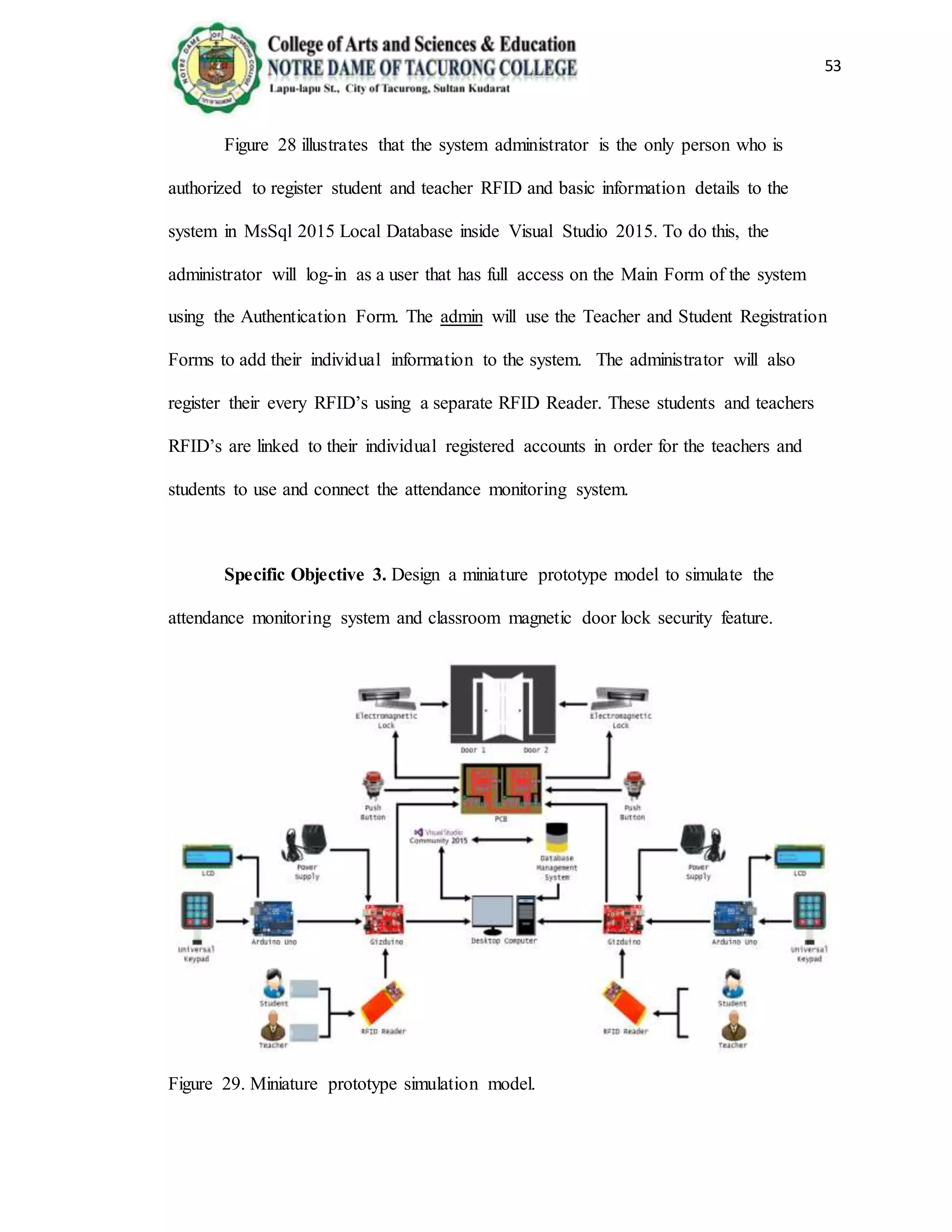
The document provides background information on the need for an automated attendance monitoring and classroom security system using RFID technology at Notre Dame of Tacurong College. It discusses how previous studies have implemented similar RFID-based systems to automate attendance tracking and improve security. The objectives of the proposed system are to design an algorithm and database to facilitate attendance automation and access control, and to develop a prototype model to demonstrate the system's features. The system aims to address issues like inaccurate manual attendance tracking and lack of classroom security controls.
















































![87
Imports System.IO.Ports
Public Class FormDTR
Delegate Sub settextcallback(ByVal [text] As String)
Property Status As Boolean
Property AttendanceId As Integer
Property ScheduleId As Integer
Property port As String
Sub RefreshData(ByVal attid As Integer)
Using jb As New JBContext
Dim getstuds = (From ad In jb.AttendanceDetail Join s In jb.Students
On
ad.ADtlStd.StdId Equals s.StdId
Where ad.ADtlAtt.AttId = attid
Select ad.ADtlId, s.StdFName, s.StdLName, ad.ADtlDate,
ad.ADtlTimeIn, ad.ADtlTimeOut).ToList
With dgv
.DataSource = Nothing
.DataSource = getstuds
End With
End Using
End Sub
Private Sub tbrfid_TextChanged(sender As Object, e As EventArgs) Handles
tbrfid.TextChanged
If tbrfid.Text.Length = 104 Then
If isTeacher(tbrfid.Text) Then
'GetSchedule(tbrfid.Text, Now)
If sprfid1.PortName = "COM5" Then
GetSchedule(tbrfid.Text, Now)
sprfid1.Write("O")
End If
Else
Using jb As New JBContext
Dim gatt = (From a In jb.Attendance
Where a.AttSchedule.ScdId = ScheduleId And
a.AttStat = True Select a
)
If gatt.Count > 0 Then
LogAttendance(tbrfid.Text, gatt.First.AttId)
tbrfid.Clear()
tbrfid.Focus()
Else
MsgBox("No onging class.")
tbrfid.Clear()
tbrfid.Focus()
End If](https://image.slidesharecdn.com/3final-161030235241/75/3-Content-Body-87-2048.jpg)

![89
.ADtlStd = stud}
With jb
.AttendanceDetail.Add(dtl)
.SaveChanges()
End With
End If
RefreshData(attid)
End Using
Else
MsgBox("Not enrolled in this subject")
End If
End Sub
Private Sub ReceivedText(ByVal [text] As String)
If tbrfid.InvokeRequired Then
Dim x As New settextcallback(AddressOf ReceivedText)
Me.BeginInvoke(x, New Object() {(text)})
Else
tbrfid.Text &= [text]
End If
End Sub
Private Sub sprfid_DataReceived(sender As Object, e As
SerialDataReceivedEventArgs) Handles sprfid1.DataReceived
ReceivedText(sprfid1.ReadExisting())
port = "COM5"
End Sub
Private Sub sprfid_DataReceived2(sender As Object, e As
SerialDataReceivedEventArgs) Handles sprfid2.DataReceived
ReceivedText(sprfid2.ReadExisting())
port = "COM6"
End Sub
Sub CreateAttendance(ByVal stat As Boolean, ByVal d As Date, ByVal id As
Integer)
Using jb As New JBContext
Dim sched = (From s In jb.Schedule
Where s.ScdId = id
Select s).First
dgv.DataSource = Nothing
Dim att As New Attendance With {
.AttDate = Today,
.AttStat = stat,
.AttSchedule = sched,
.AttTimeOpen = Now.TimeOfDay}
With jb
.Attendance.Add(att)
.SaveChanges()
tbstat.Text = "Ongoing"
Status = True
tbrfid.Clear()](https://image.slidesharecdn.com/3final-161030235241/75/3-Content-Body-89-2048.jpg)








![98
tbmname.Text = .StdMName
tbaddress.Text = .Address
tbcontact.Text = .StdContact
End With
Return True
Else
Clear()
tbrfid.Text = RFID
Return False
End If
End Using
End Function
End Class
FormStudentRegistration
Imports System.IO.Ports
Public Class FormStudentRegistration
Delegate Sub settextcallback(ByVal [text] As String)
Private Sub StudentIn_OutSerialPort_DataReceived(ByVal sender As
System.Object, ByVal e As System.IO.Ports.SerialDataReceivedEventArgs) Handles
sprfid.DataReceived
ReceivedText(sprfid.ReadExisting())
End Sub
Private Sub ReceivedText(ByVal [text] As String)
If tbrfid.InvokeRequired Then
Dim x As New settextcallback(AddressOf ReceivedText)
Me.BeginInvoke(x, New Object() {(text)})
Else
tbrfid.Text &= [text]
End If
End Sub
Private Sub tbrfid_TextChanged(sender As Object, e As EventArgs) Handles
tbrfid.TextChanged
If tbrfid.Text.Length = 104 Then
With FormStudentDetail
.RFID = tbrfid.Text.Trim
.ShowDialog()
RefreshData()
tbrfid.Clear()
End With
End If
End Sub
Private Sub FormStudentRegistration_Load(sender As Object, e As EventArgs)
Handles MyBase.Load
Try
RefreshData()
With sprfid](https://image.slidesharecdn.com/3final-161030235241/75/3-Content-Body-98-2048.jpg)








![109
End If
End Sub
Private Sub btnrefresh_Click(sender As Object, e As EventArgs) Handles
btnrefresh.Click
RefreshData()
End Sub
Private Sub ManageStudentsToolStripMenuItem_Click(sender As Object, e As
EventArgs) Handles ManageStudentsToolStripMenuItem.Click
If dgv.SelectedRows.Count > 0 Then
With FormSchedStudents
.SchedId = dgv.SelectedRows(0).Cells(0).Value
.ShowDialog()
End With
End If
End Sub
End Class
TeacherRegistration
Imports System.IO.Ports
Public Class FormTeacherRegistration
Delegate Sub settextcallback(ByVal [text] As String)
Private Sub StudentIn_OutSerialPort_DataReceived(ByVal sender As
System.Object, ByVal e As System.IO.Ports.SerialDataReceivedEventArgs) Handles
sprfid.DataReceived
ReceivedText(sprfid.ReadExisting())
End Sub
Private Sub ReceivedText(ByVal [text] As String)
If tbrfid.InvokeRequired Then
Dim x As New settextcallback(AddressOf ReceivedText)
Me.Invoke(x, New Object() {(text)})
Else
tbrfid.Text &= [text]
End If
End Sub
Private Sub tbrfid_TextChanged(sender As Object, e As EventArgs) Handles
tbrfid.TextChanged
If tbrfid.Text.Length = 104 Then
With FormTeacherDetail
.RFID = tbrfid.Text.Trim
.ShowDialog()
RefreshData()
tbrfid.Clear()
End With
End If
End Sub](https://image.slidesharecdn.com/3final-161030235241/75/3-Content-Body-109-2048.jpg)