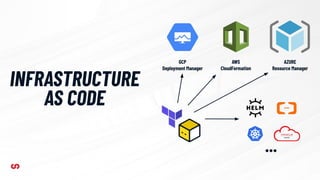
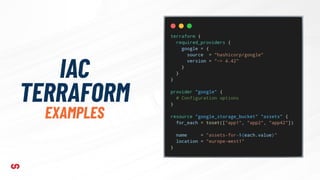
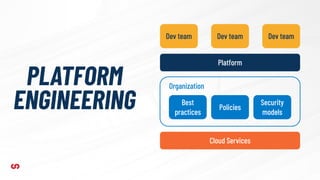
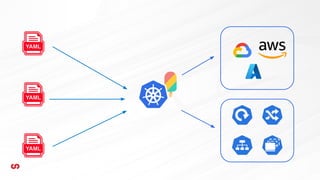
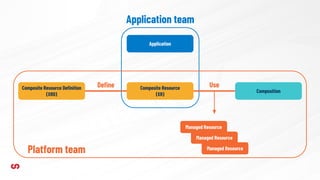
This document discusses application-driven infrastructure using Crossplane. It introduces Crossplane as a Kubernetes-native framework that allows platform teams to assemble infrastructure from multiple vendors and expose higher-level APIs. This enables development teams to consume infrastructure services without having to write custom code. Crossplane uses the concepts of providers, managed resources, and composite resources to map external services to Kubernetes and provide opinionated APIs through self-service resources. It aims to simplify infrastructure provisioning and management for both platform and application teams.