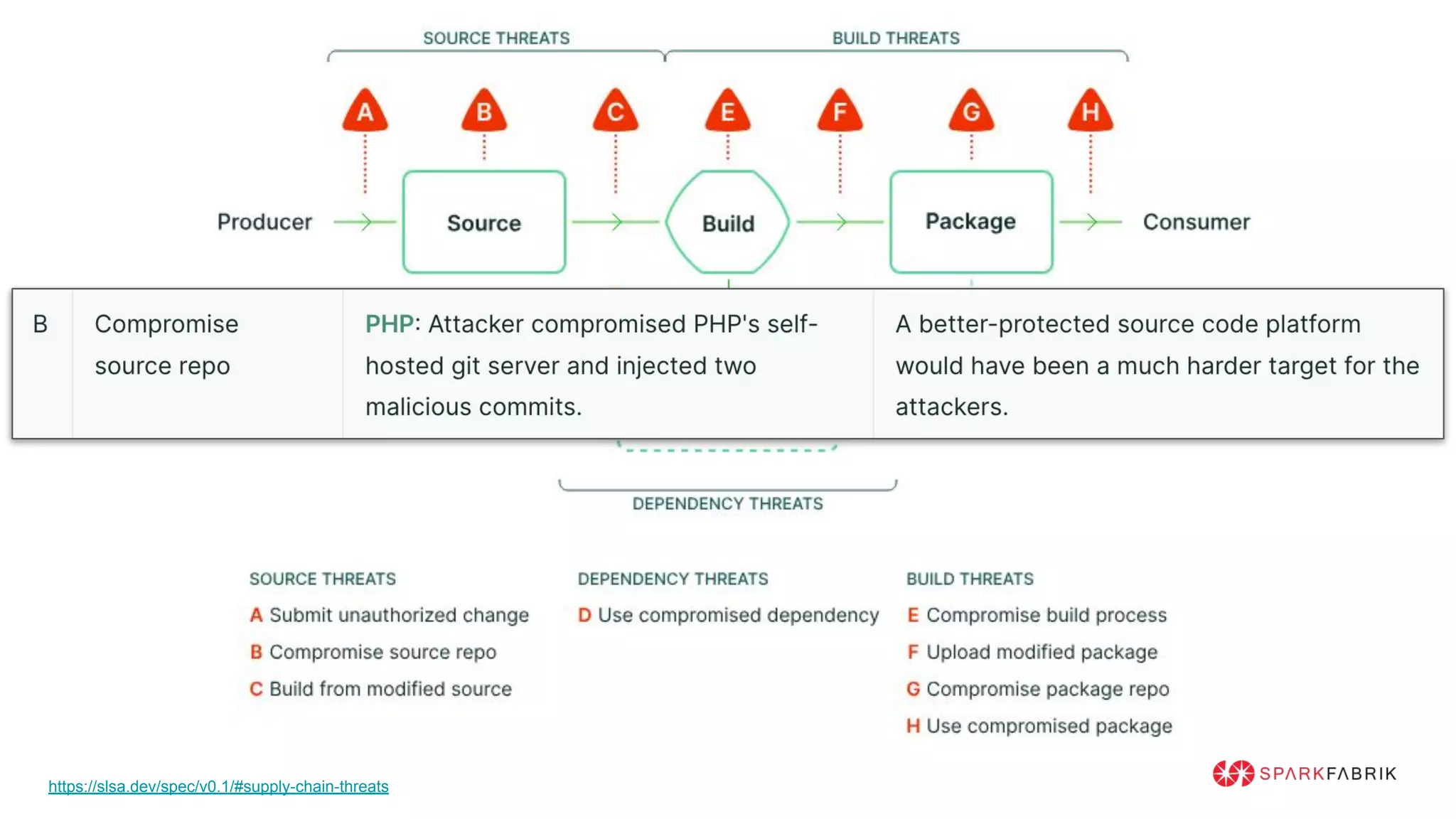
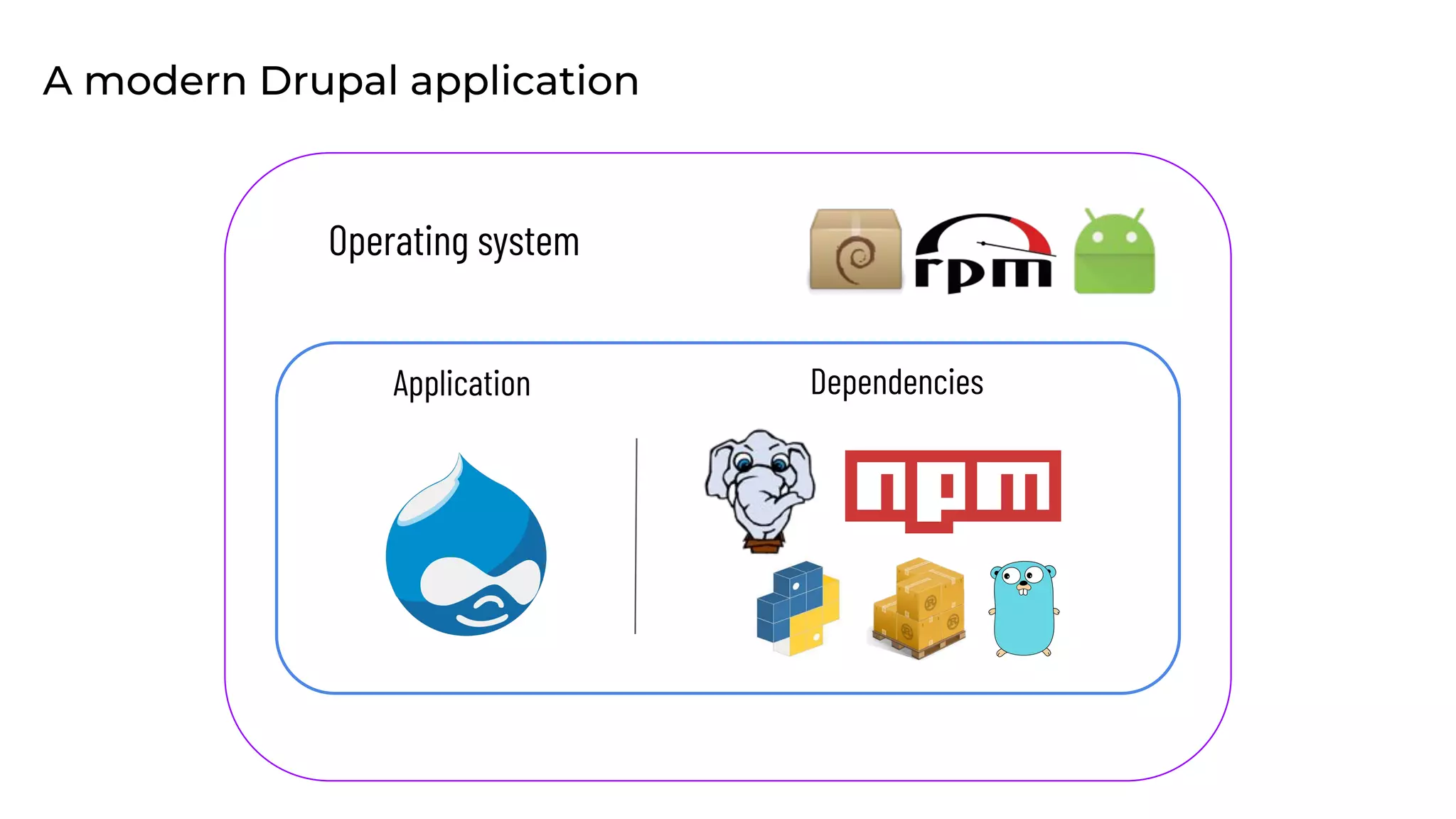
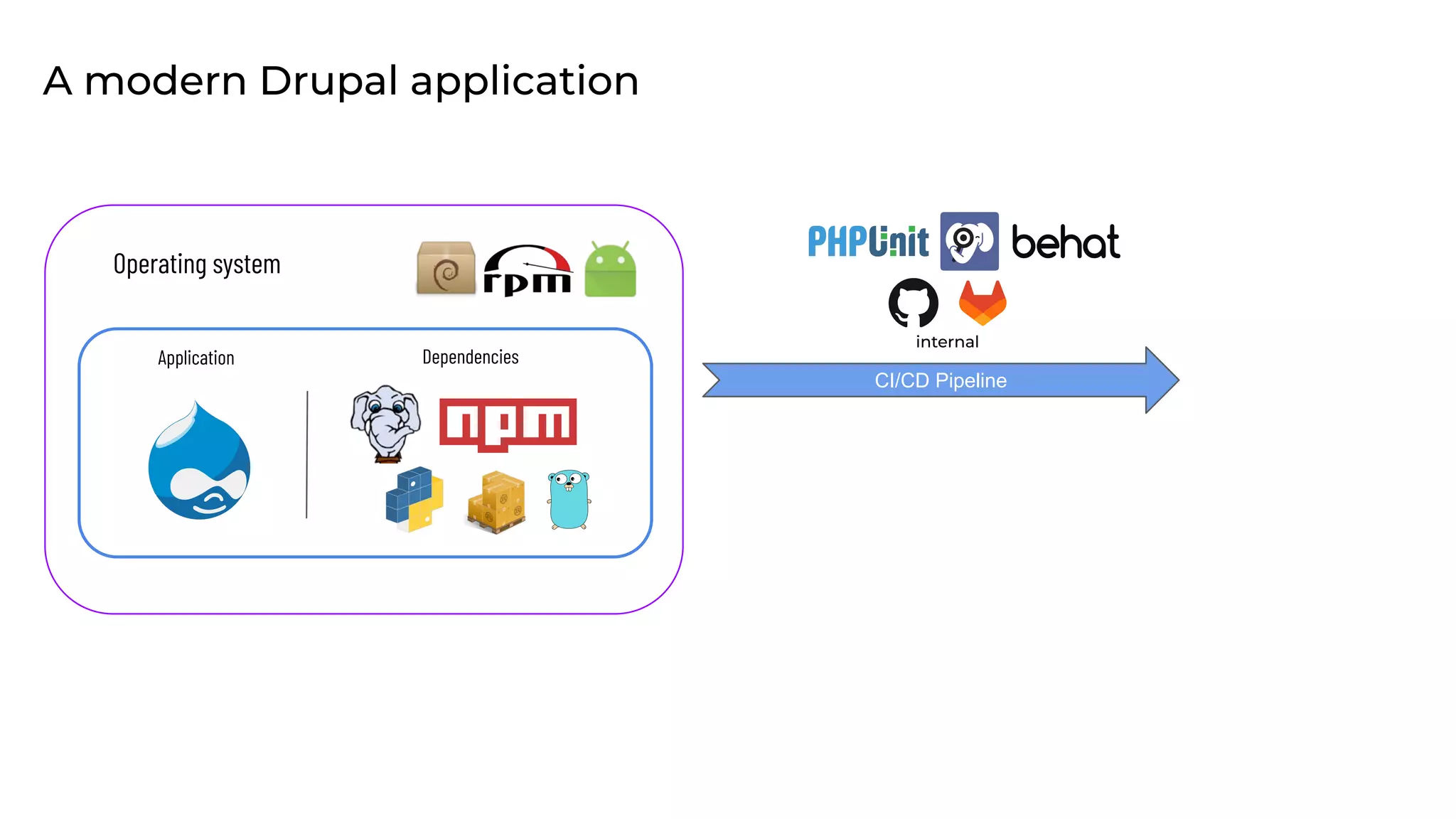
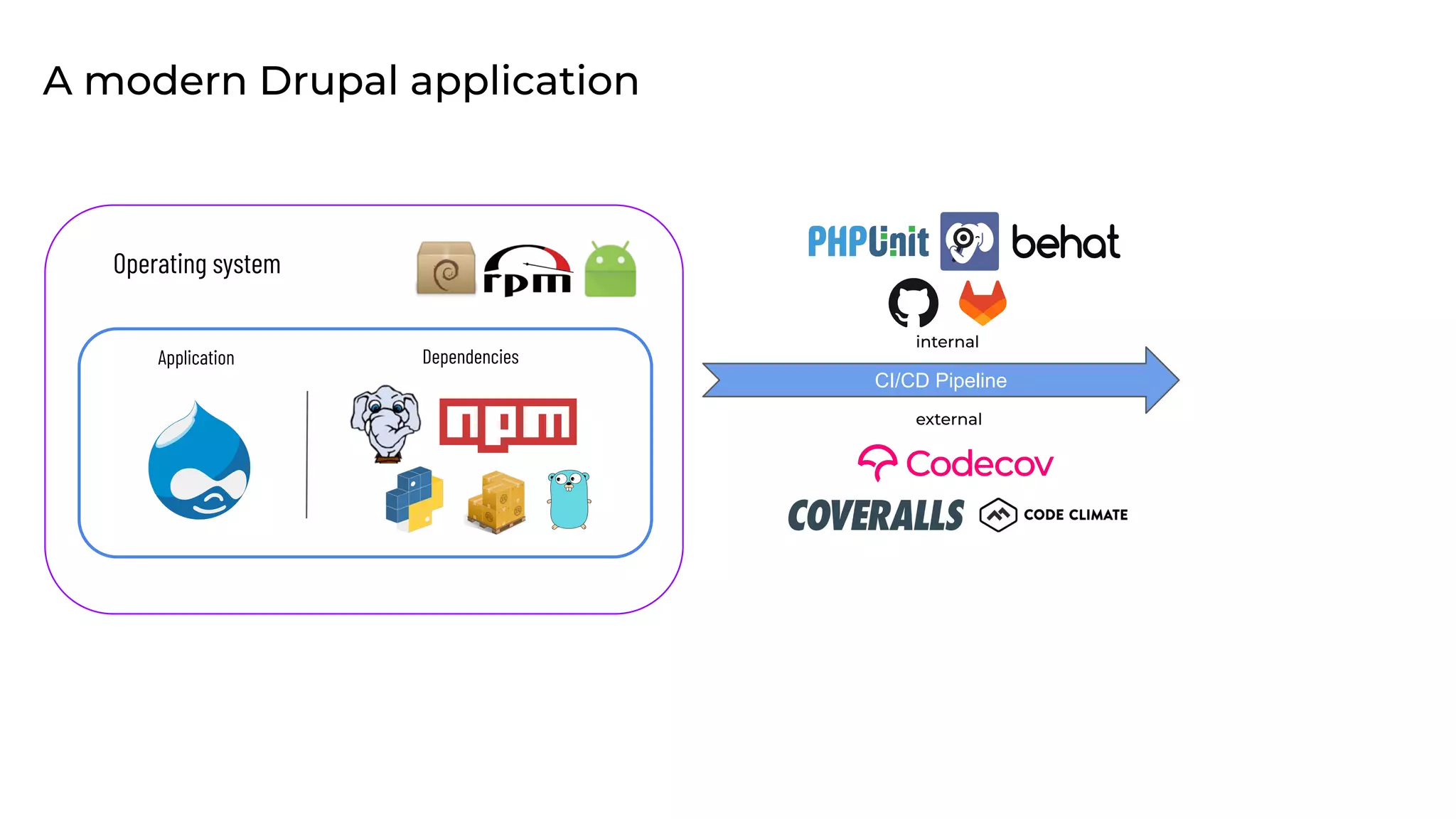
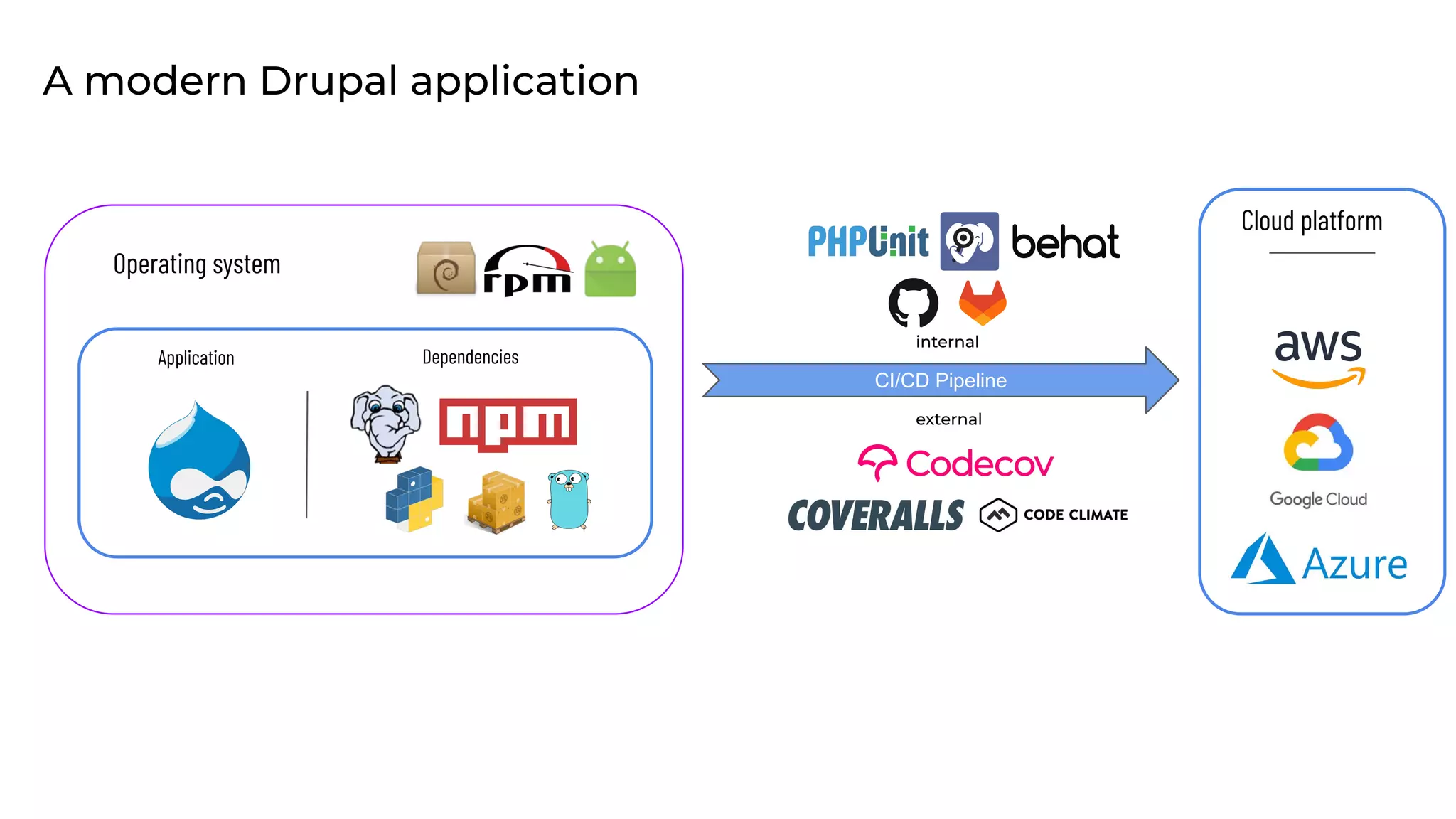
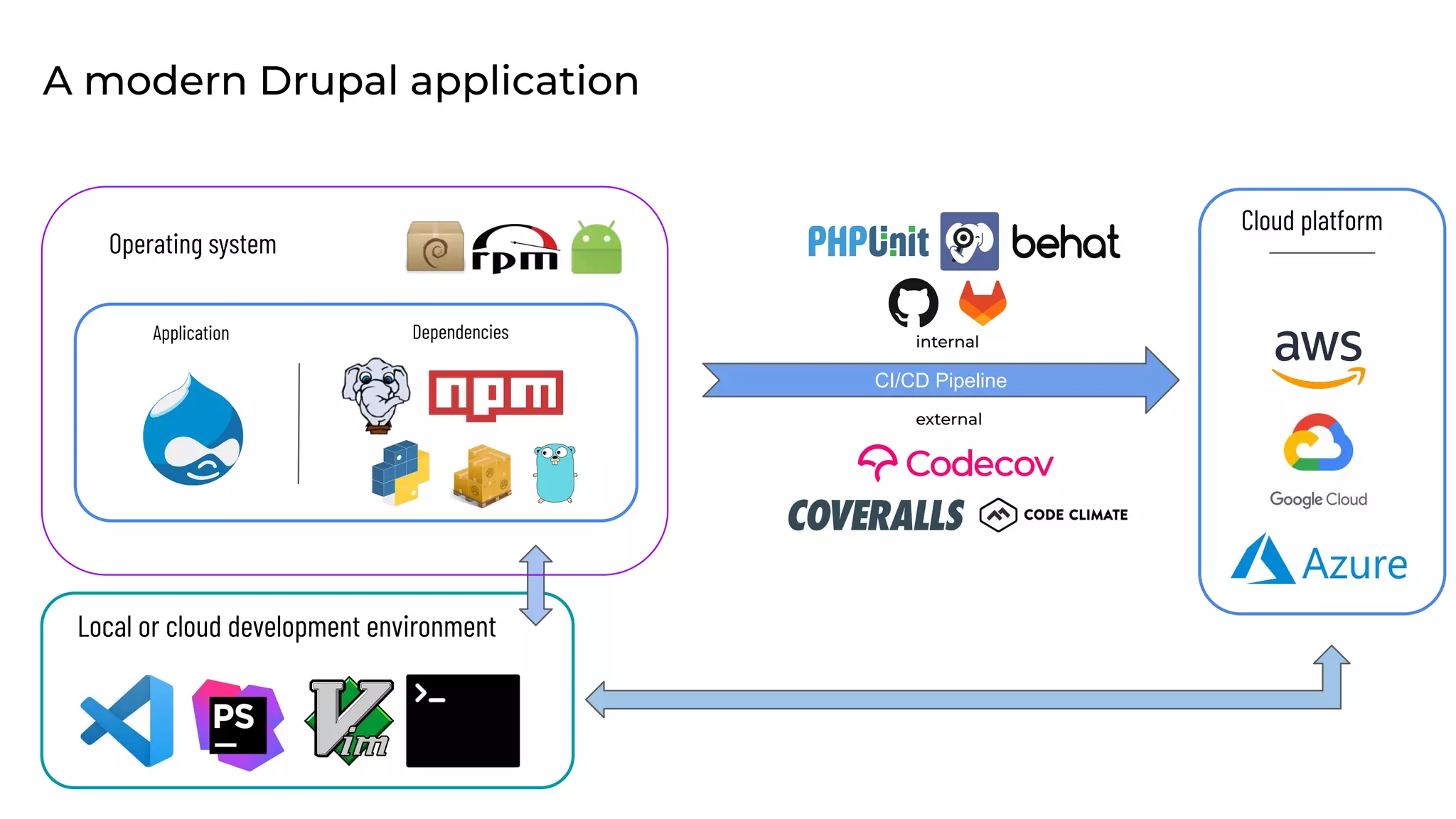
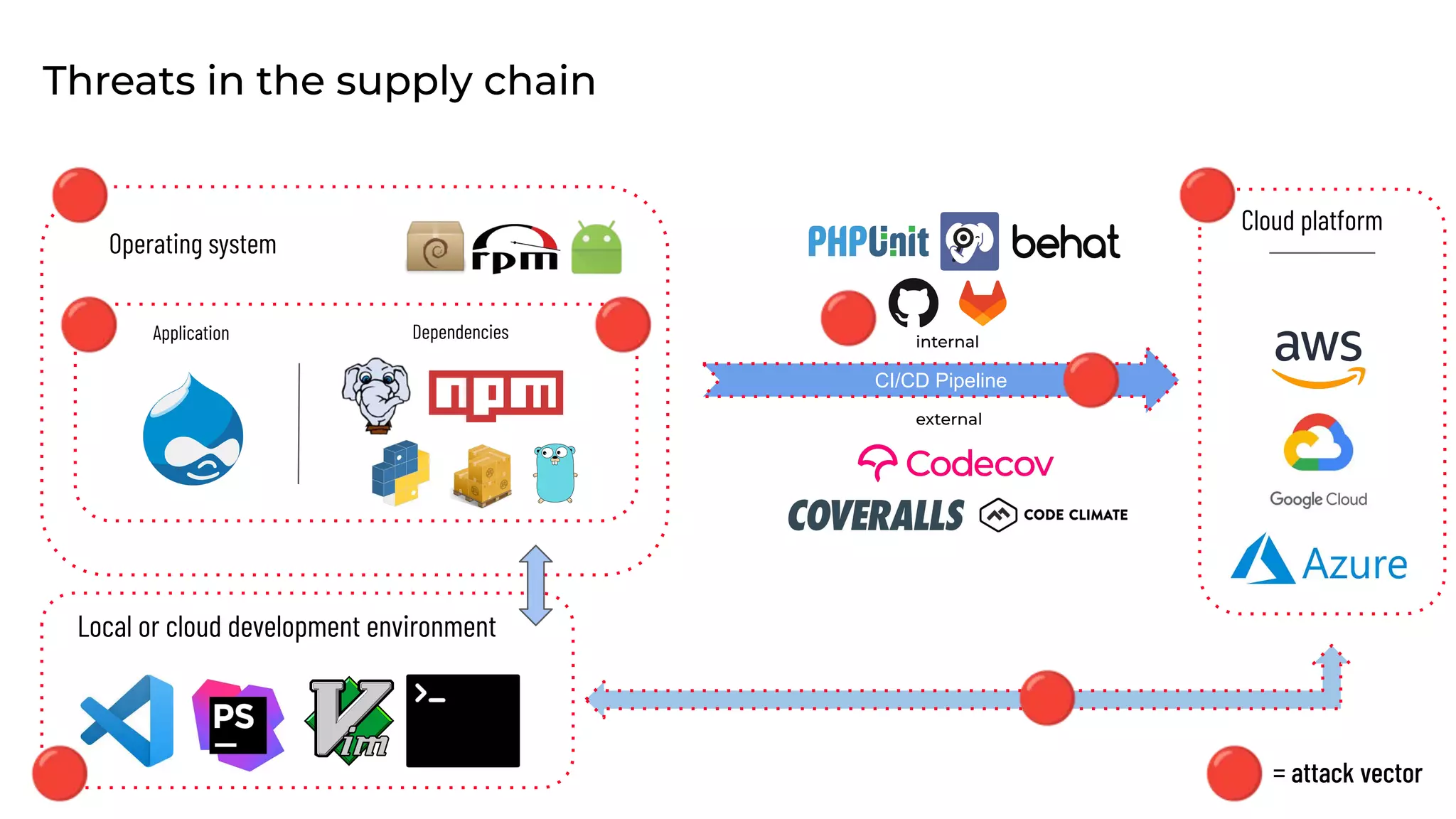
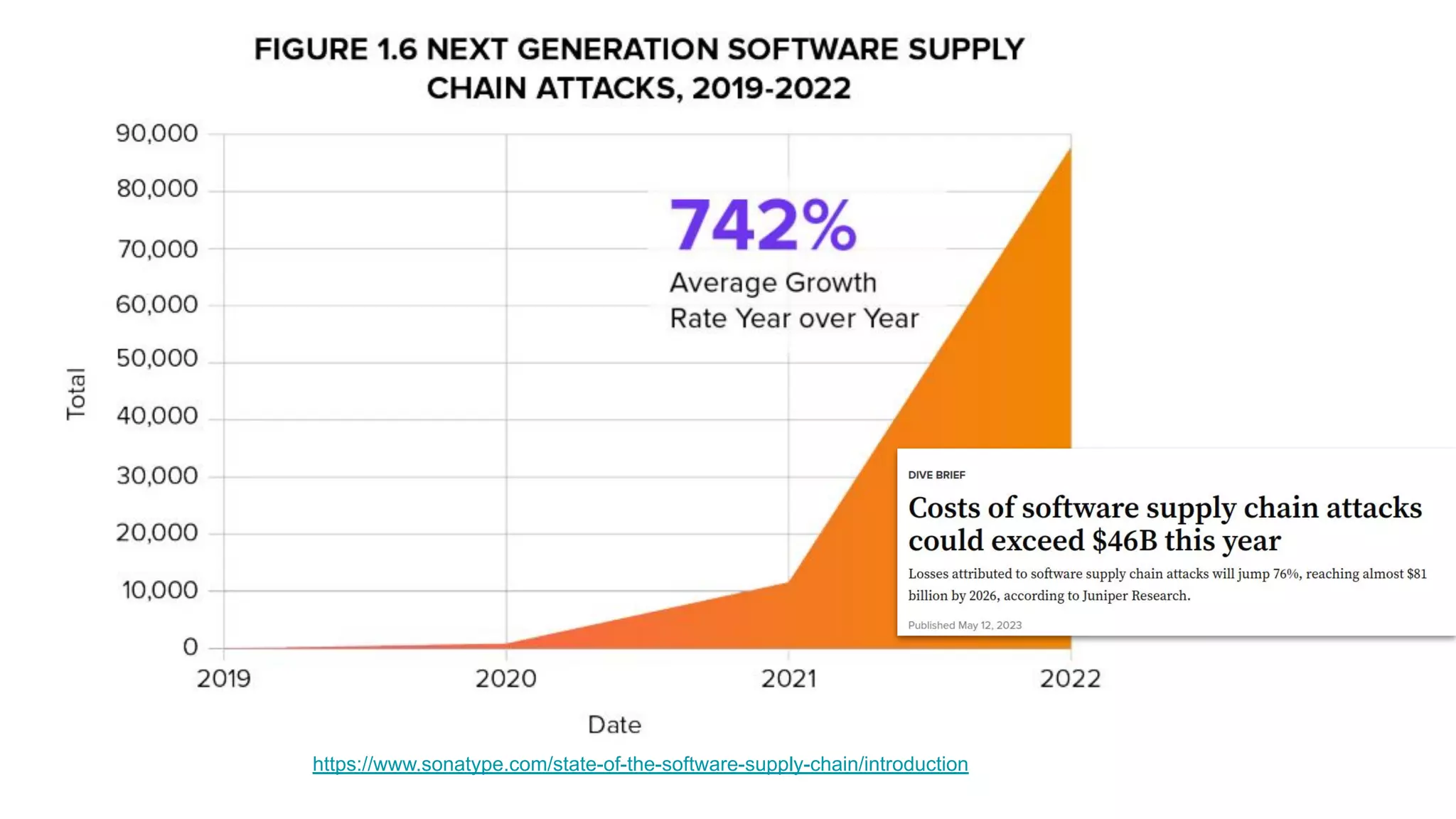
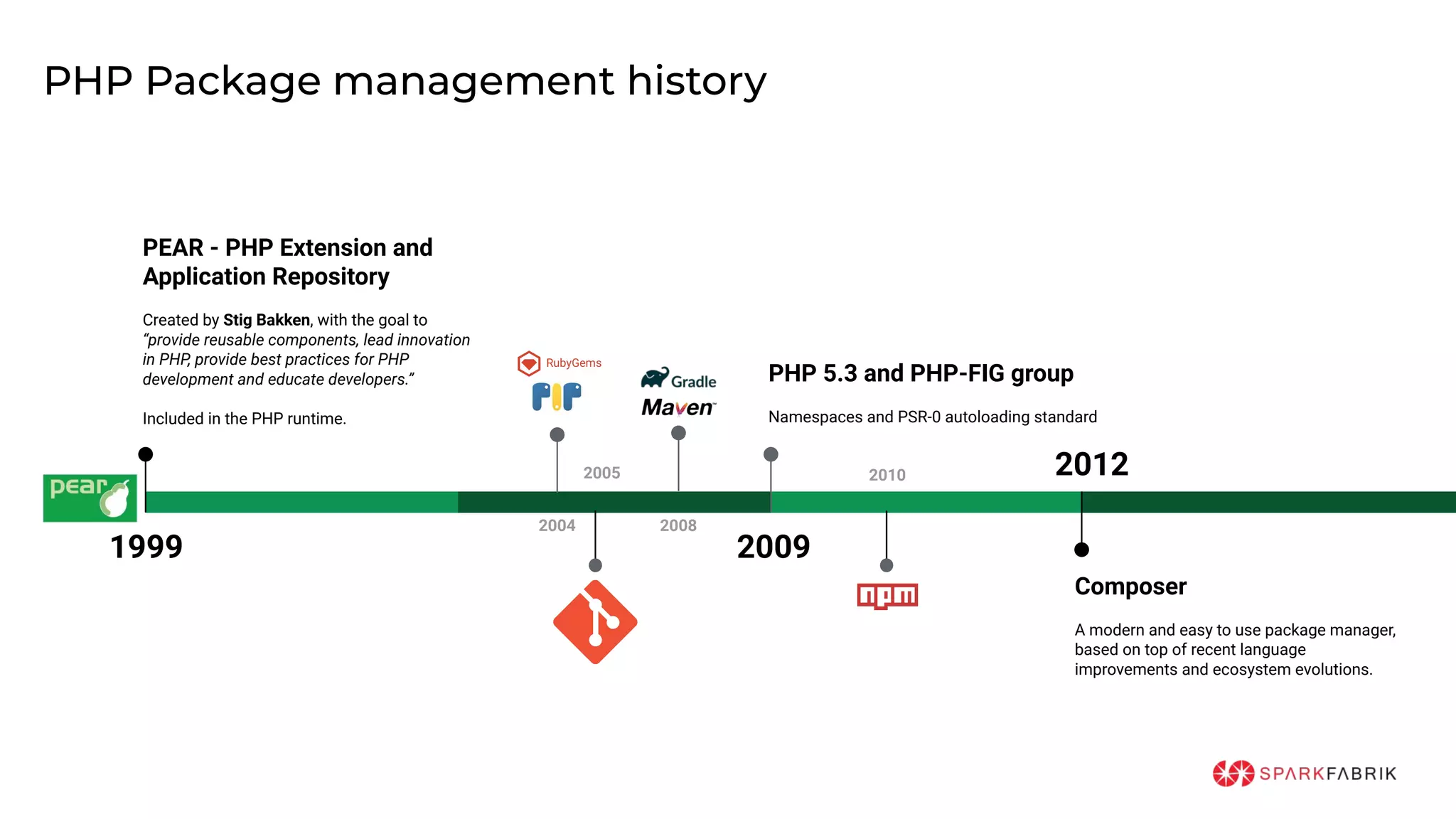
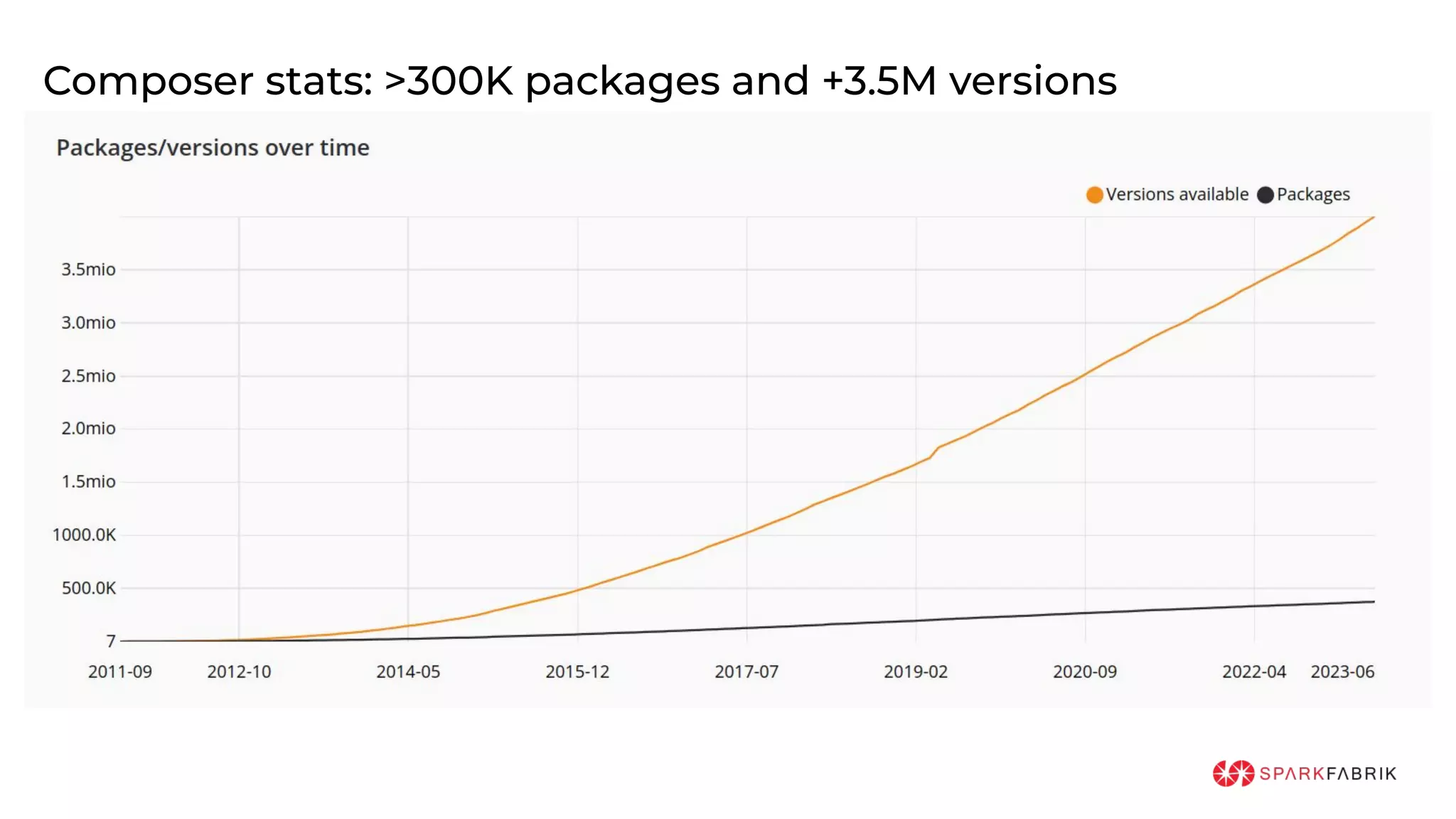
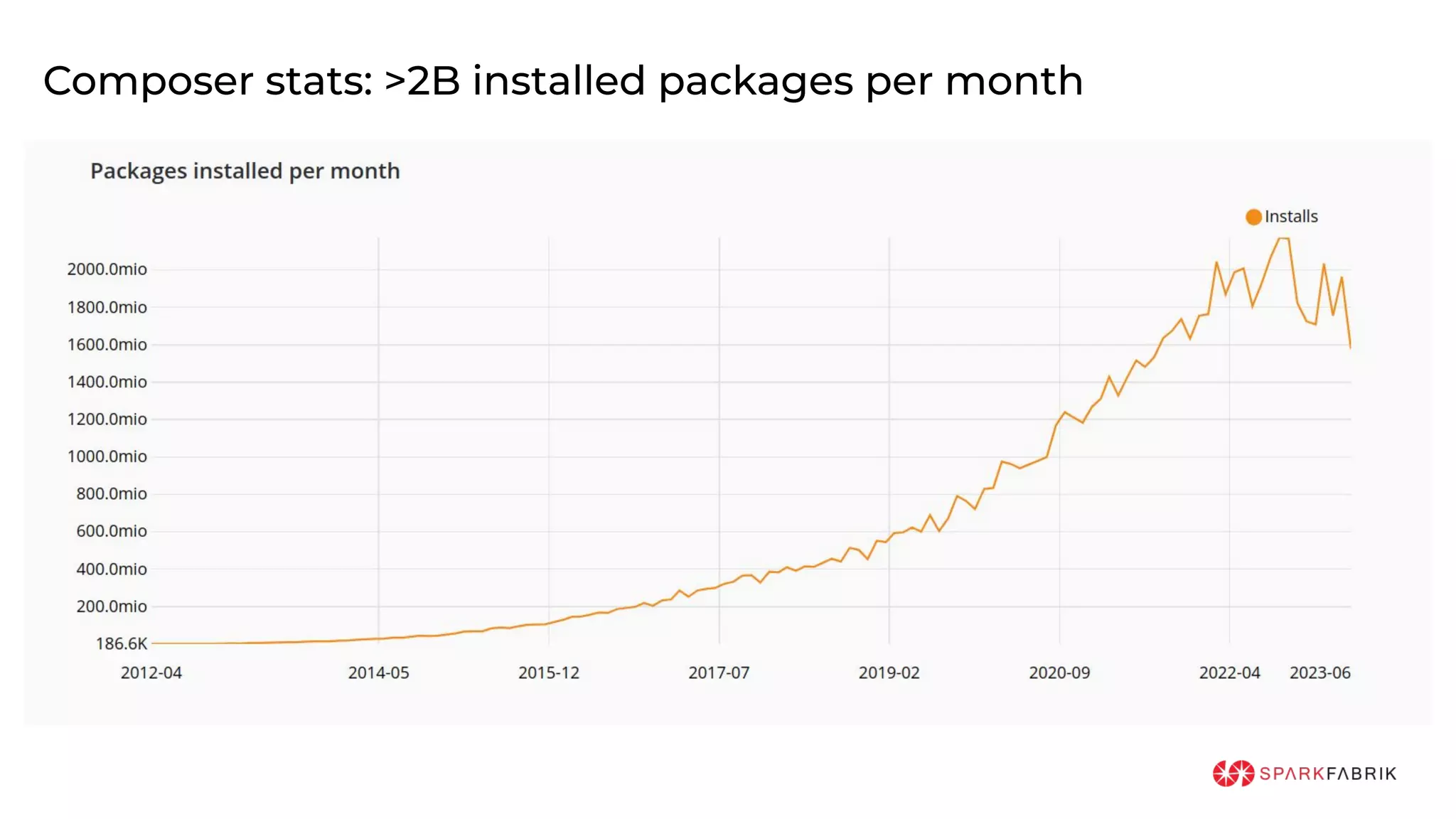
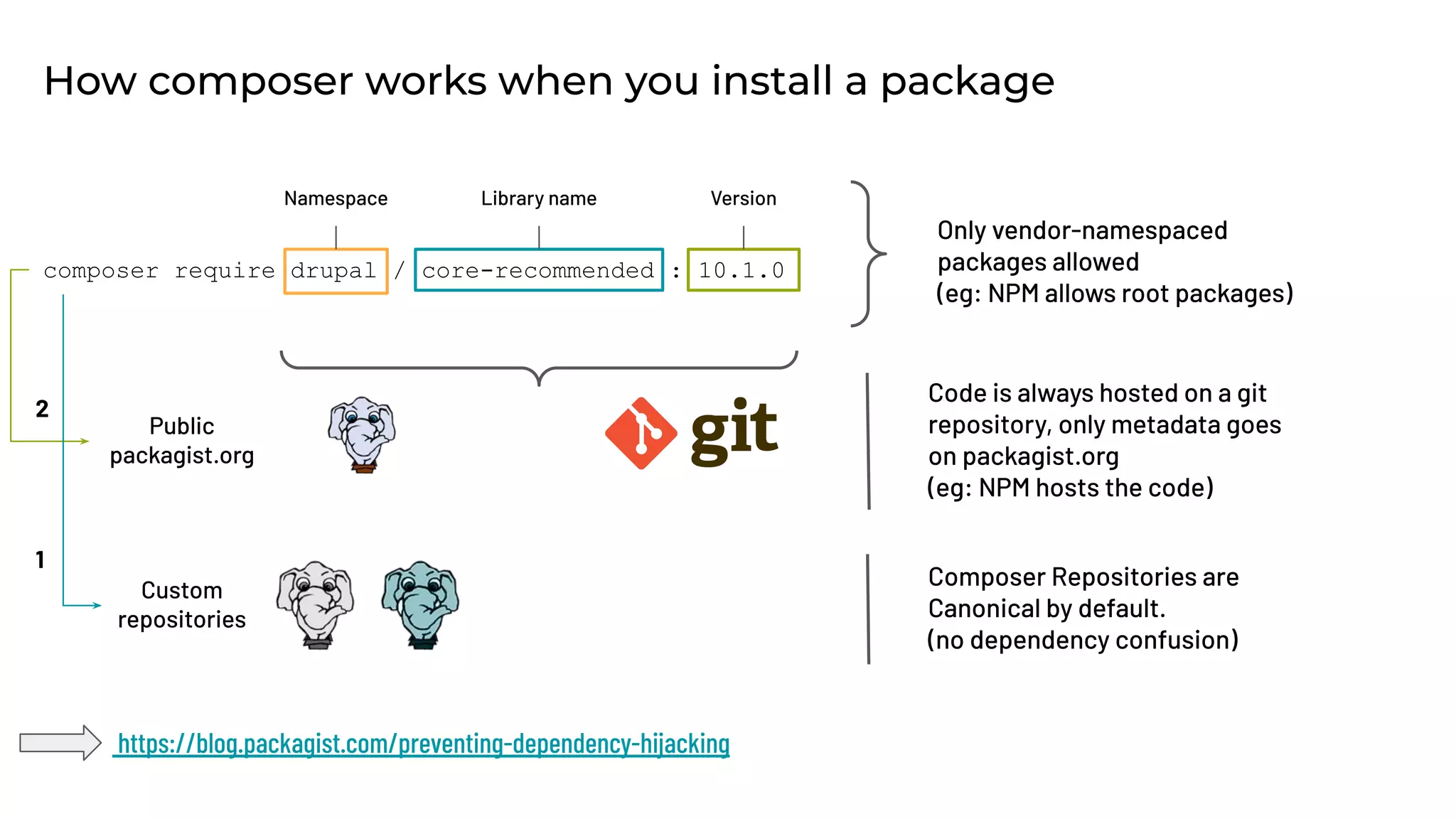
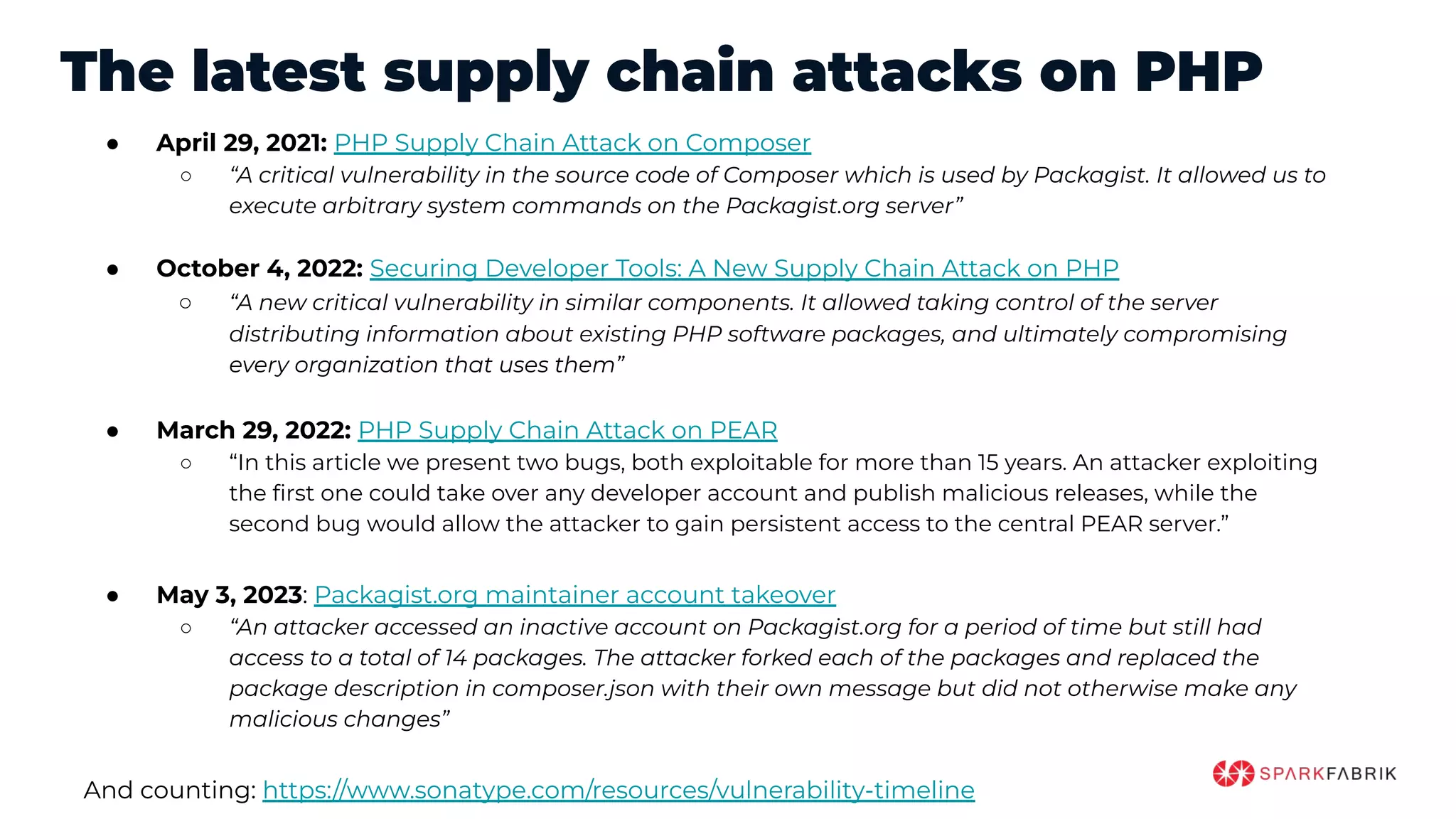
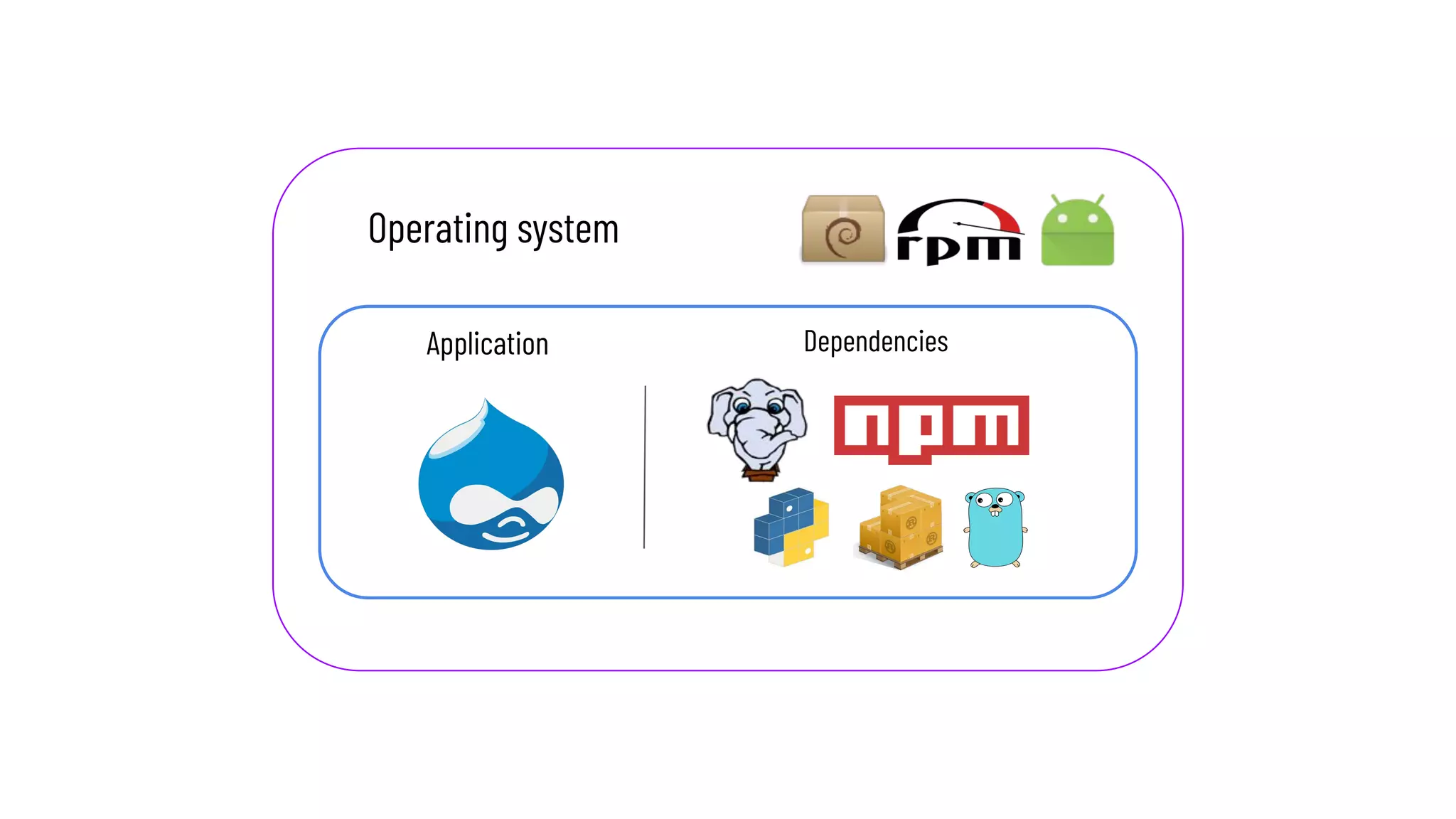
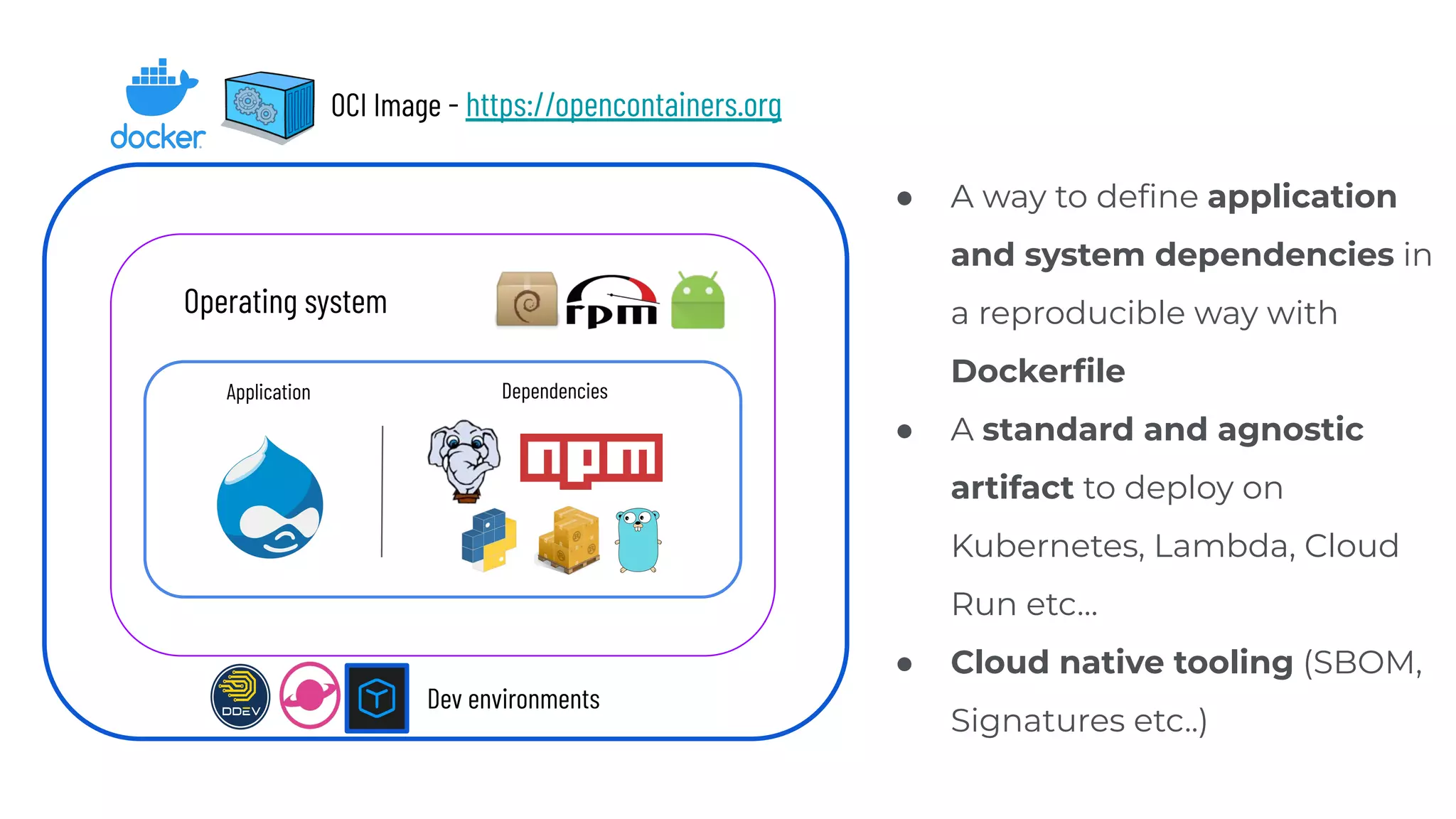
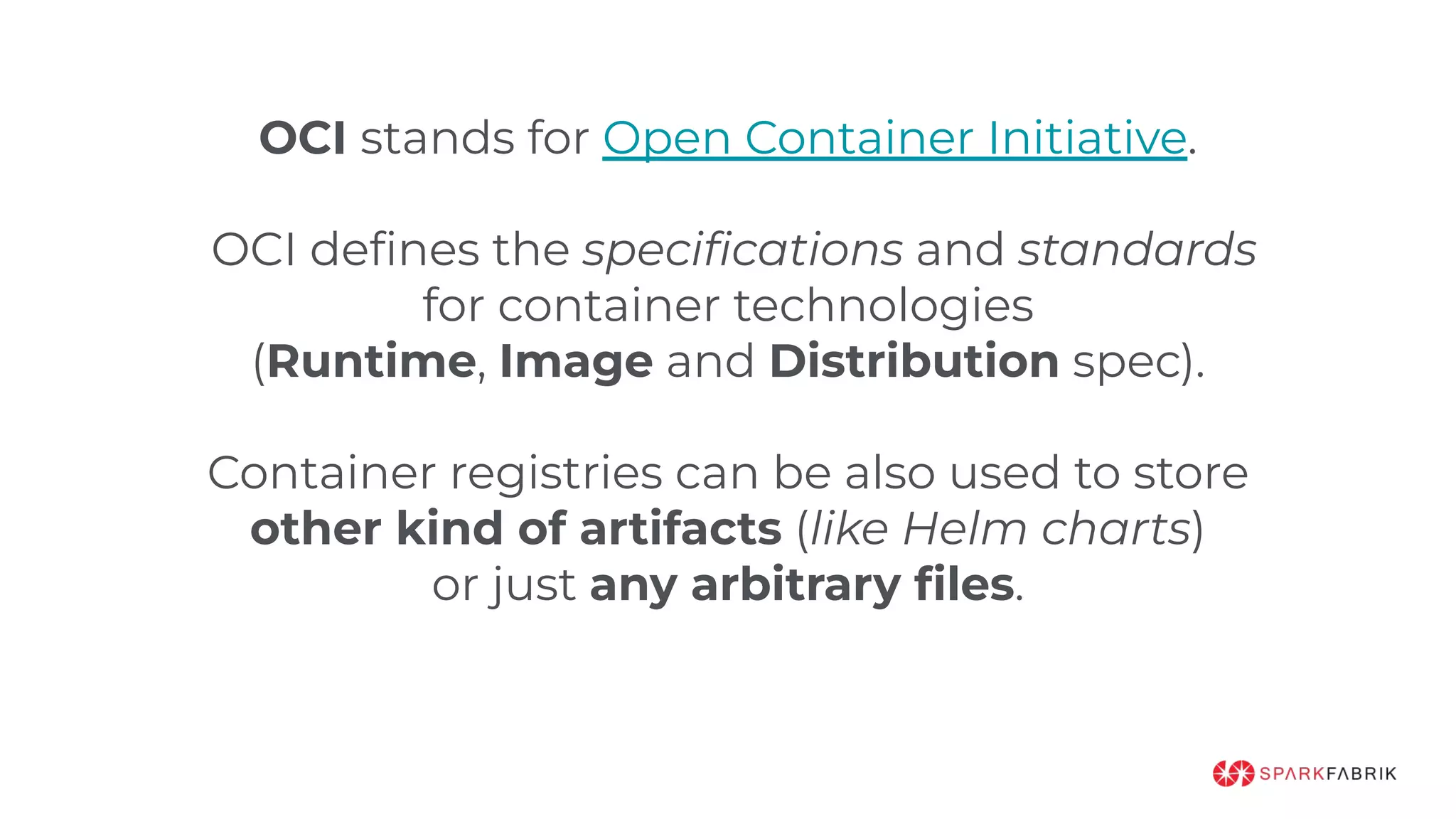
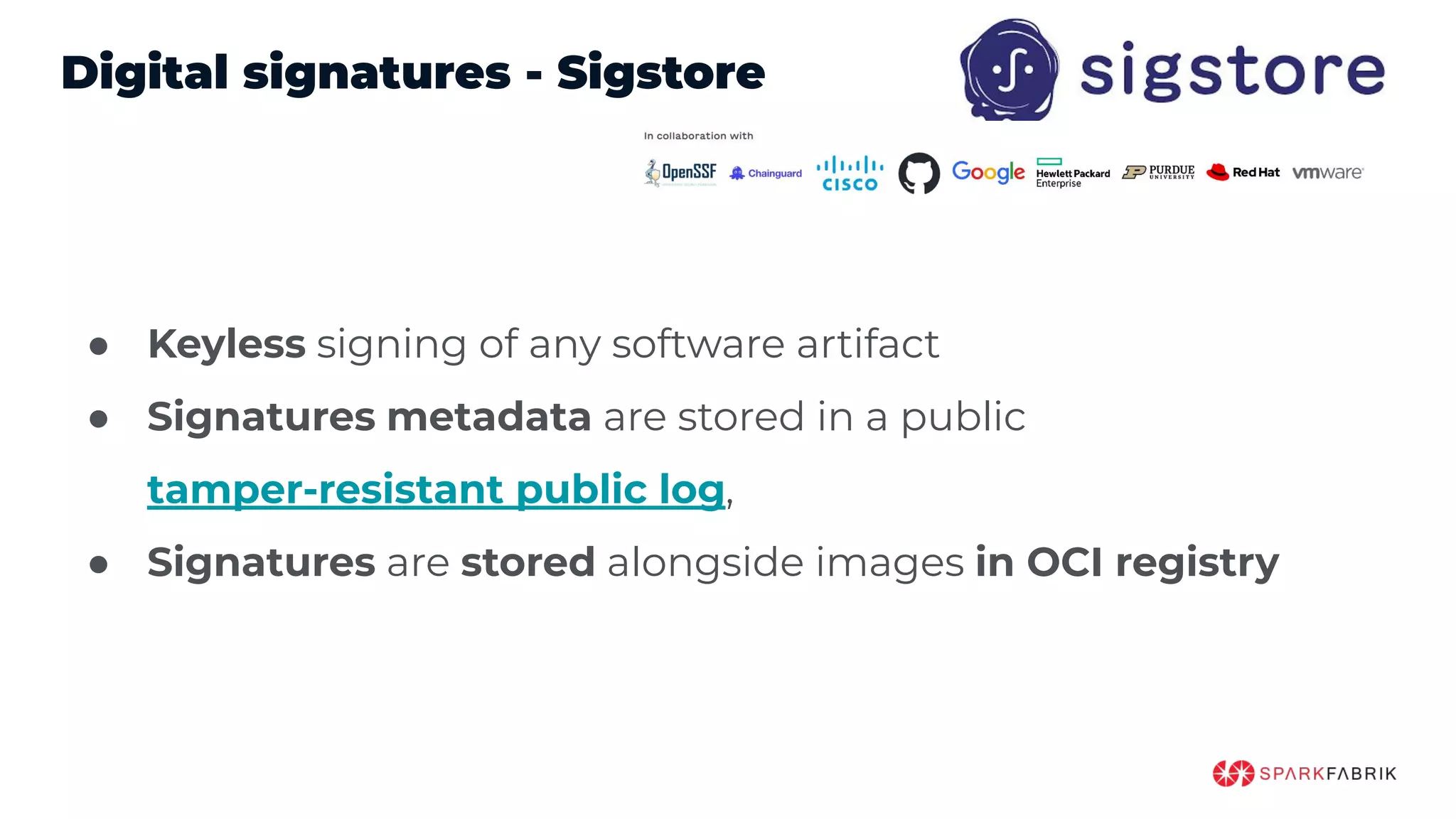
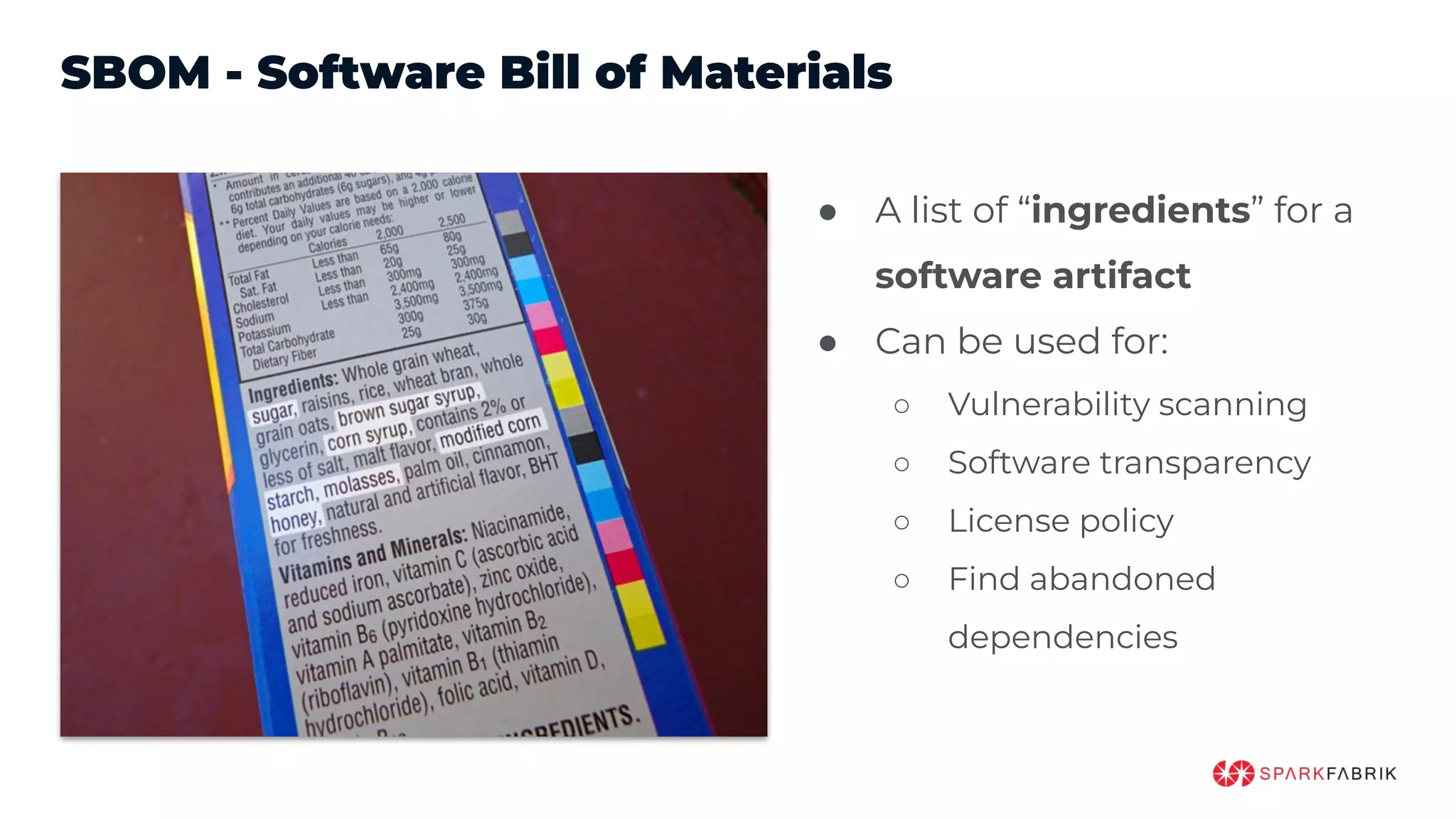
This document discusses the secure software supply chain and current state of the PHP ecosystem. It begins with introductions and defines a software supply chain as a network involved in creating and delivering a product to consumers. It then discusses threats in modern software supply chains like dependencies and demonstrates building a software bill of materials (SBOM) to analyze dependencies. It also covers recent supply chain attacks on PHP infrastructure and tools like Composer and PEAR. Finally, it recommends mitigations like using signed container images to verify integrity and provenance and generating SBOMs to detect vulnerabilities.