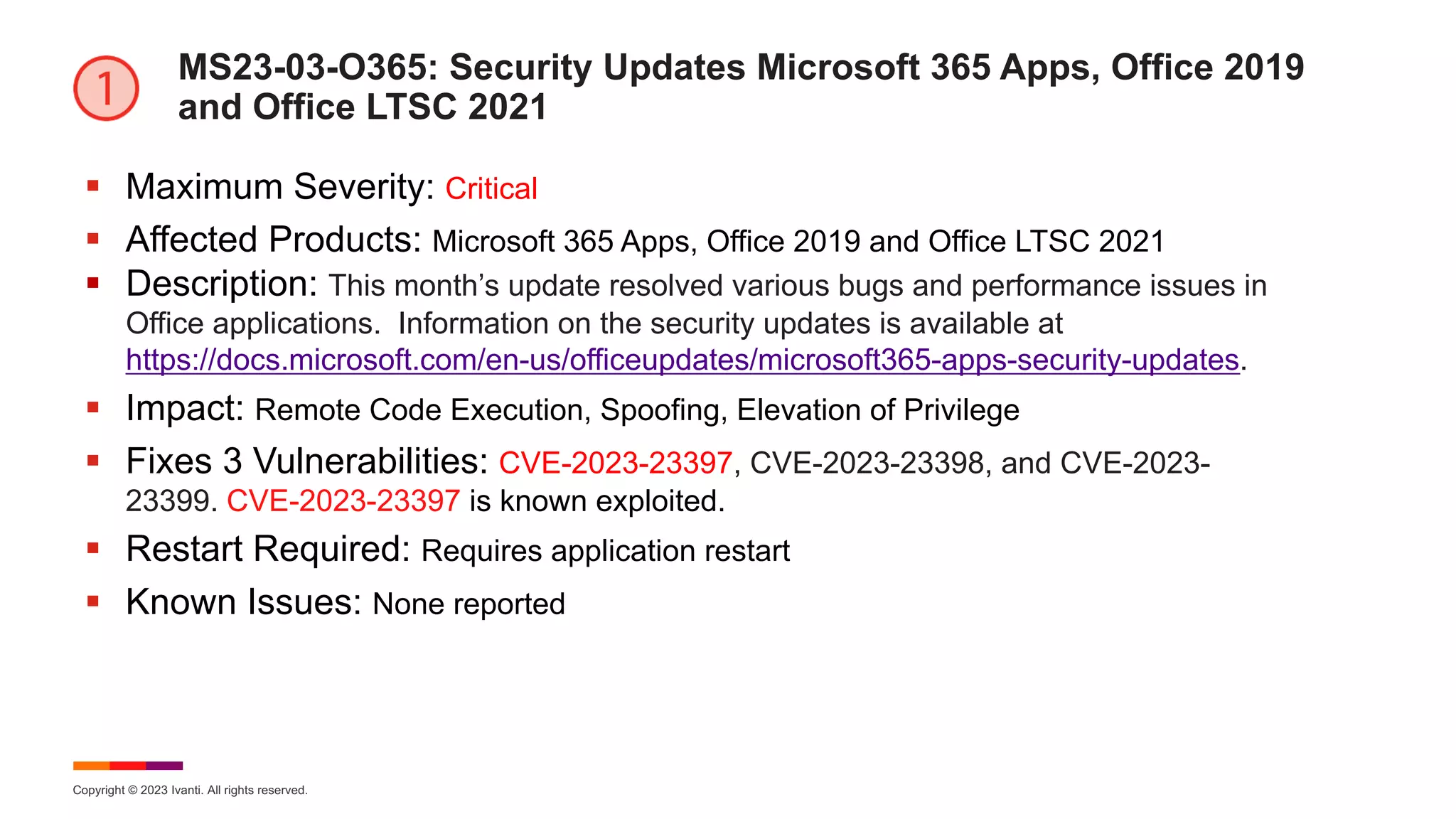
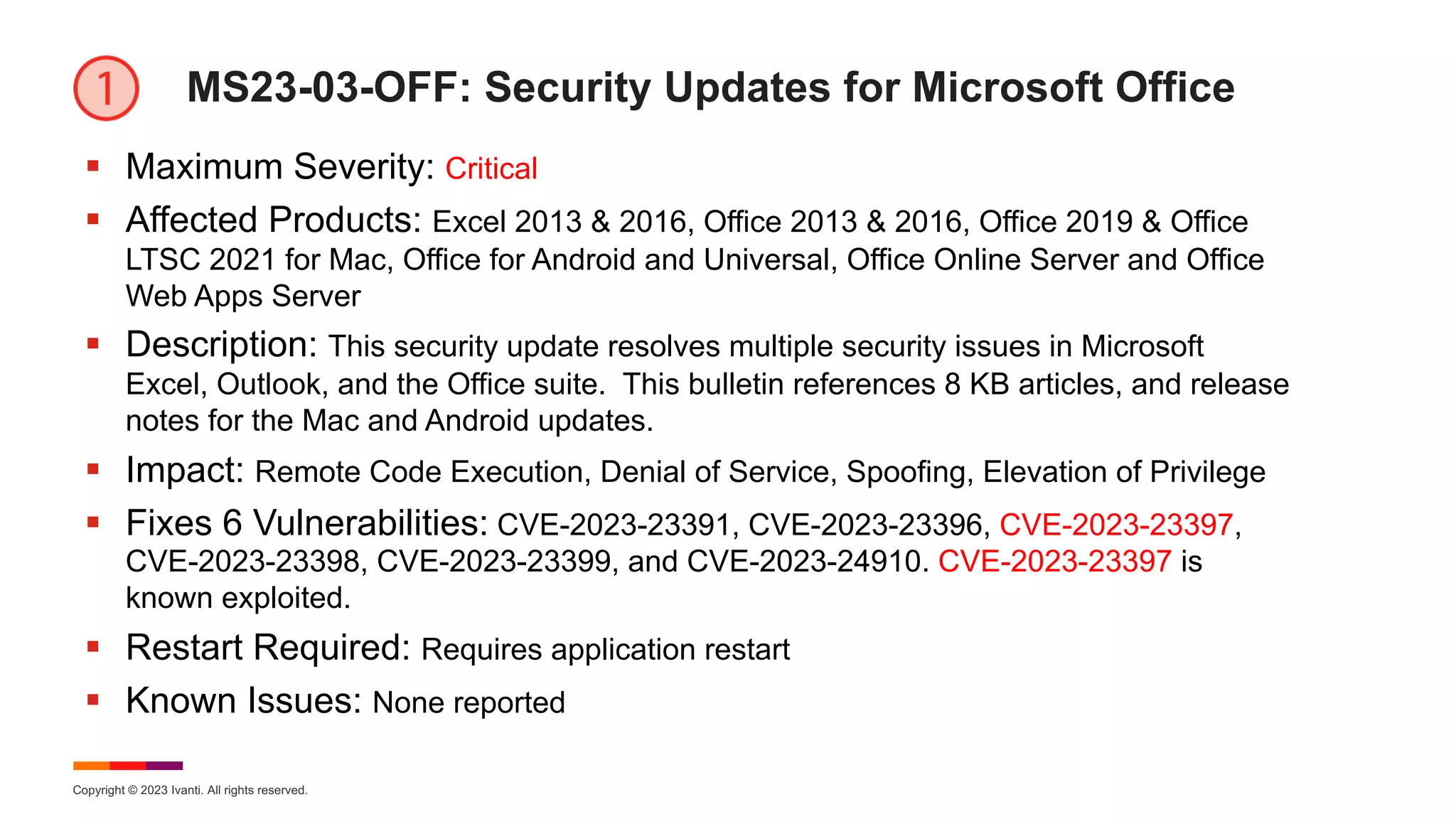
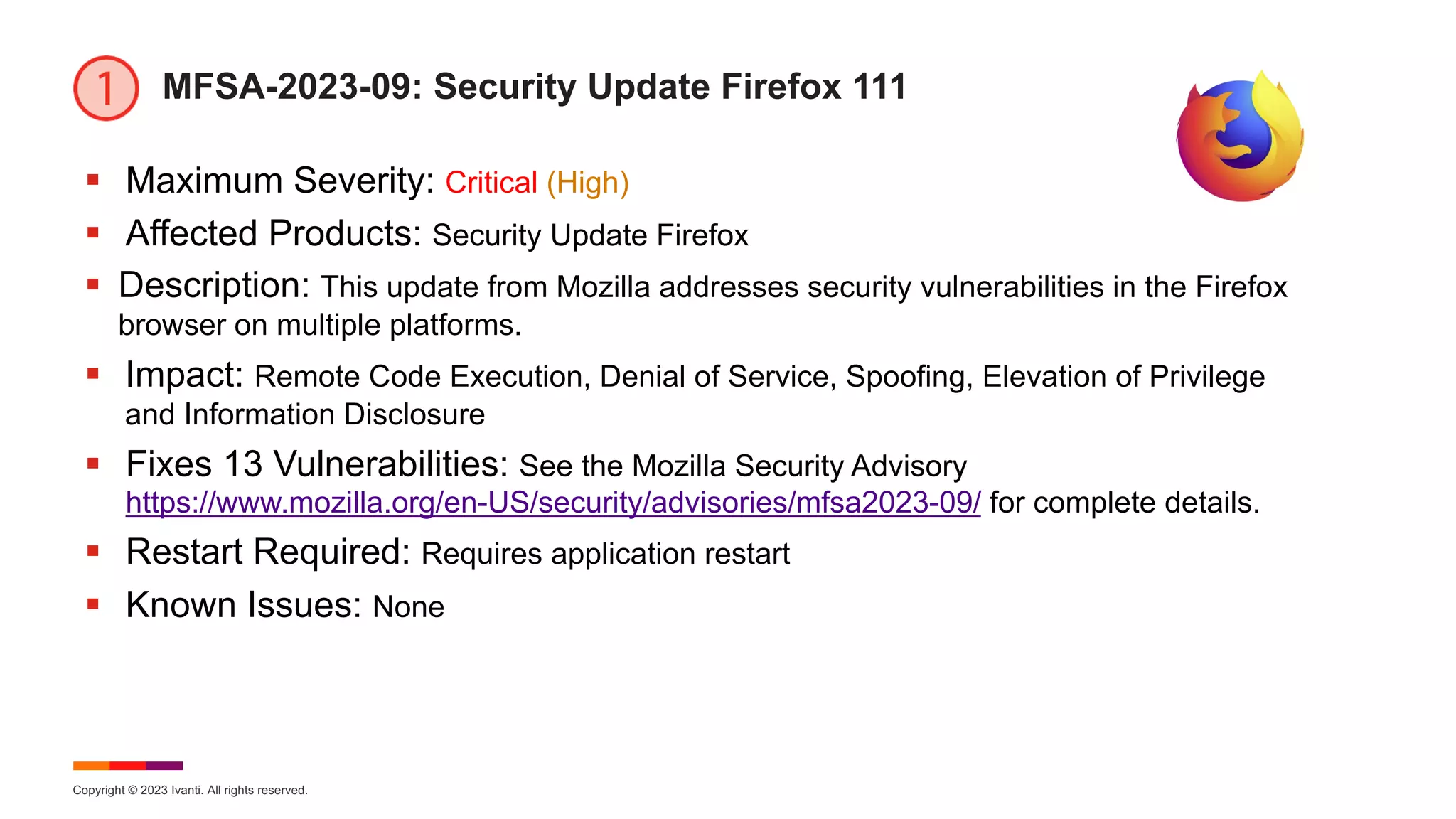
The March 2023 Patch Tuesday webinar hosted by Ivanti highlighted the resolution of 80 new CVEs by Microsoft, including two zero-day exploits affecting Microsoft Office and Windows SmartScreen, with Mozilla also releasing updates for Firefox addressing 13 vulnerabilities. Key vulnerabilities discussed include a Windows SmartScreen bypass and a critical Microsoft Outlook elevation of privilege vulnerability. The webinar provided updates on various impacted products and known issues related to the updates, emphasizing the importance of immediate patching for security.







![Copyright © 2023 Ivanti. All rights reserved.
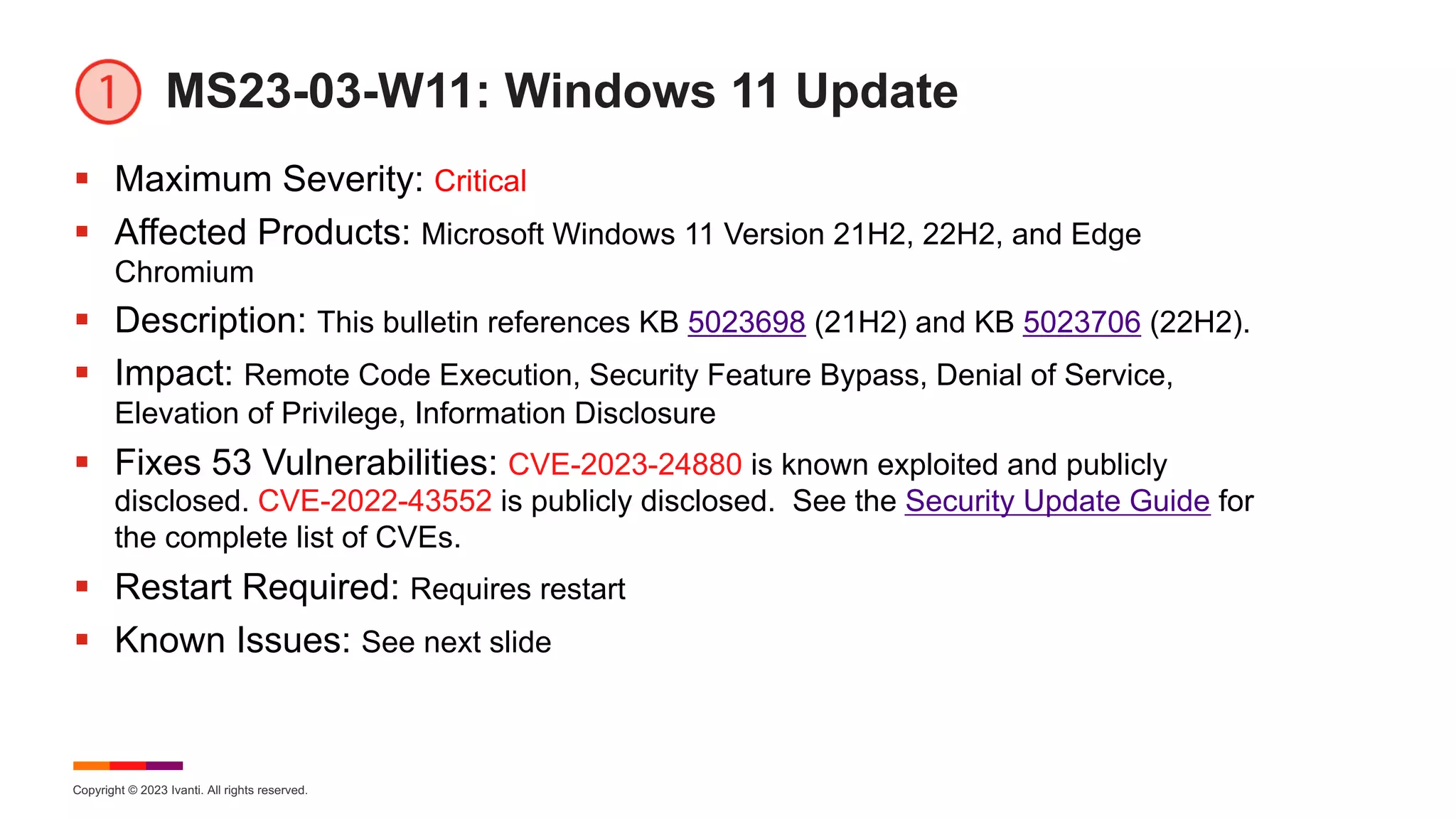
March Known Issues for Windows 11
§ KB 5023706 – Windows 11 version 22H2
§ [Provision] Using provisioning packages on Windows 11, version 22H2 (also called
Windows 11 2022 Update) might not work as expected. Windows might only be
partially configured, and the Out Of Box Experience might not finish or might restart
unexpectedly. Workaround: Provision before updating to 22H2. Microsoft is working
on a resolution.
§ [Slow Copy] Copying large multiple gigabyte (GB) files might take longer than
expected to finish on Windows 11, version 22H2. Workaround: Use file copy tools
that do not use cache manager (buffered I/O). See KB for multiple mitigations.
Microsoft is working on a resolution.
§ [Missing UUP] Updates released February 14, 2023 or later might download to WSUS
but not propagate further to client devices. Affected WSUS servers are only those
running Windows Server 2022 which have been upgraded and are missing the Unified
Update Platform (UUP) MIME types Microsoft Configuration Manager is not affected
by this issue. Workaround: See KB on how to add the UUP file types to the WSUS
systems. Microsoft is working on a resolution.](https://image.slidesharecdn.com/march2023patchtuesday-230315203400-1ae5b3a5/75/2023-March-Patch-Tuesday-20-2048.jpg)
![Copyright © 2023 Ivanti. All rights reserved.
March Known Issues for Windows 11 (cont)
§ KB 5023706 – Windows 11 version 22H2 (cont)
§ [App Fail] Windows devices with some third-party UI customization apps might not
start up. These third-party apps might cause errors with explorer.exe that might repeat
multiple times in a loop. The known affected third-party UI customization apps are
ExplorerPatcher and StartAllBack. Workaround: Uninstall any third-party UI
customization app before installing this or later updates. Microsoft is investigating and
will provide more info in the future.](https://image.slidesharecdn.com/march2023patchtuesday-230315203400-1ae5b3a5/75/2023-March-Patch-Tuesday-21-2048.jpg)
![Copyright © 2023 Ivanti. All rights reserved.
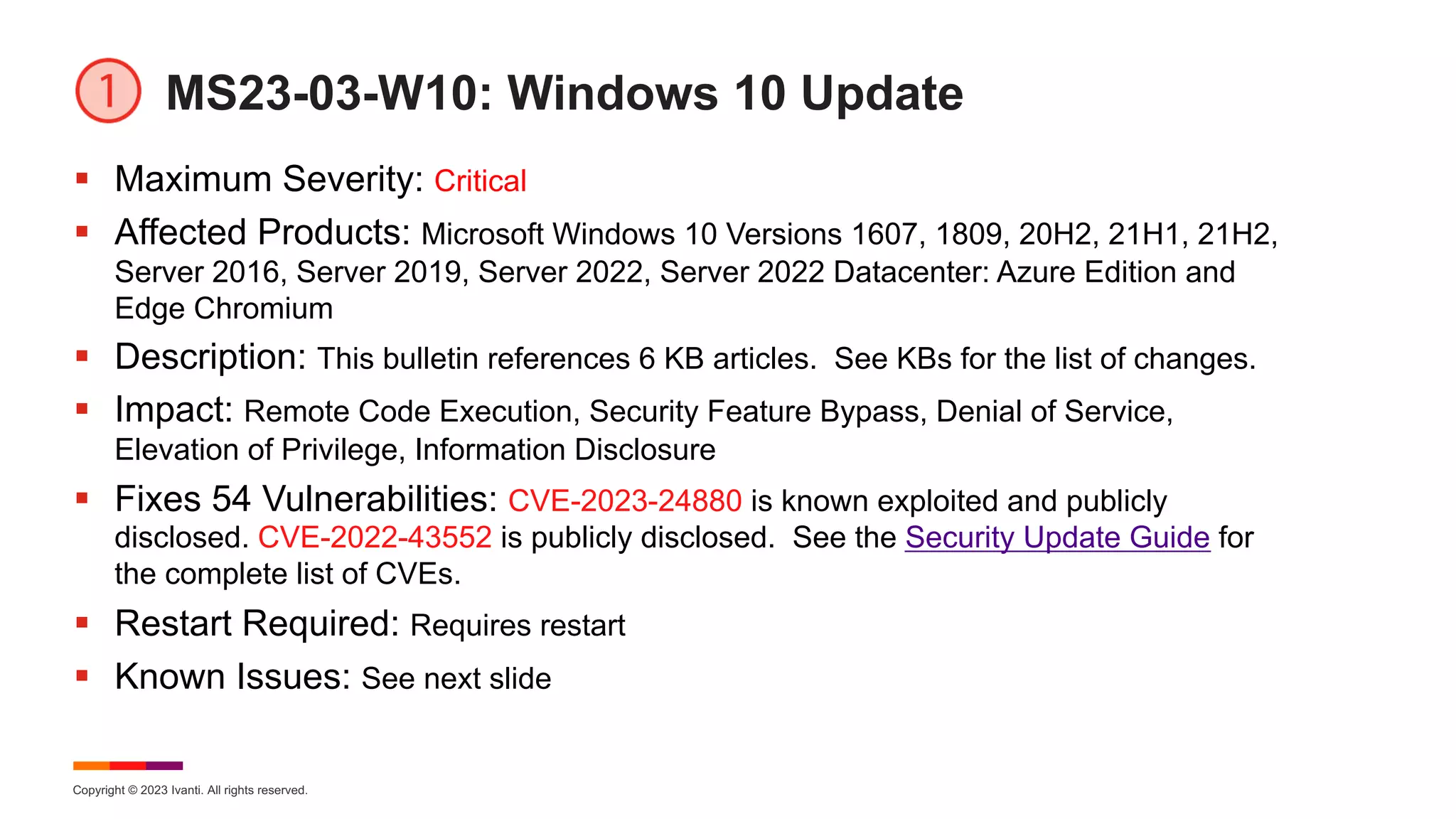
March Known Issues for Windows 10
§ KB 5023702 – Windows 10 Enterprise 2019 LTSC, Windows 10 IoT
Enterprise 2019 LTSC, Windows 10 IoT Core 2019 LTSC, Windows
Server 2019
§ [Cluster Update] After installing KB 5001342 or later, the Cluster Service might fail
to start because a Cluster Network Driver is not found. Workaround: This issue
occurs because of an update to the PnP class drivers used by this service. After
about 20 minutes, you should be able to restart your device and not encounter this
issue. For more information about the specific errors, cause, and workaround for
this issue, please see KB 5003571.](https://image.slidesharecdn.com/march2023patchtuesday-230315203400-1ae5b3a5/75/2023-March-Patch-Tuesday-23-2048.jpg)
![Copyright © 2023 Ivanti. All rights reserved.
March Known Issues for Windows 10 (cont)
§ KB 5023705 – Windows Server 2022
§ [Missing UUP]
§ [ESXi Fail] After installing this update on guest virtual machines (VMs) running
Windows Server 2022 on some versions of VMware ESXi, Windows Server 2022
might not start up. Only Windows Server 2022 VMs with Secure Boot enabled are
affected by this issue. Affected versions of VMware ESXi are versions vSphere
ESXi 7.0.x and below.](https://image.slidesharecdn.com/march2023patchtuesday-230315203400-1ae5b3a5/75/2023-March-Patch-Tuesday-24-2048.jpg)
![Copyright © 2023 Ivanti. All rights reserved.
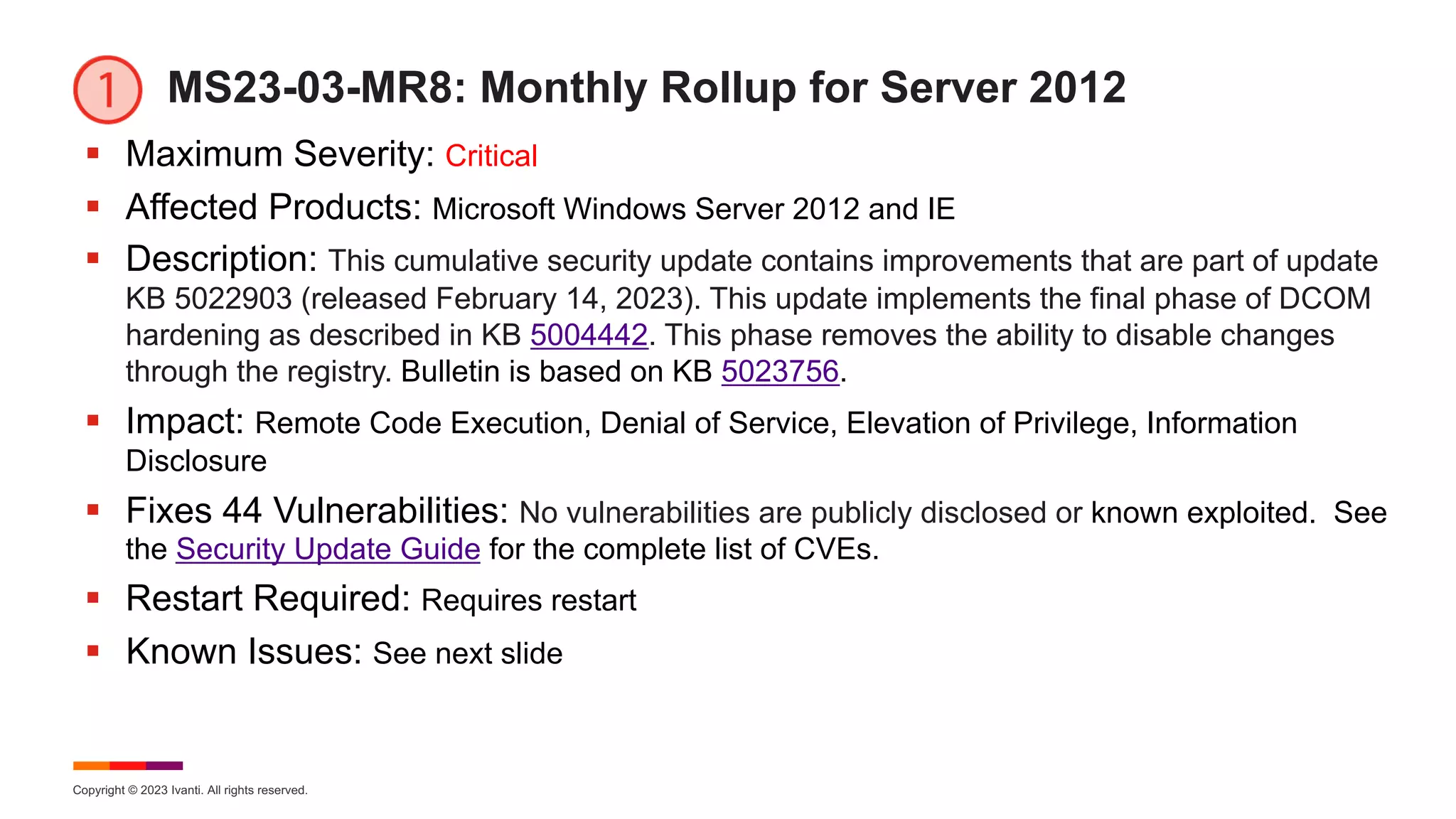
March Known Issues for Server 2012
§ KB 5023756 – Windows Server 2012 (Monthly Rollup)
§ [Domain Join] After this update or a later Windows update is installed, domain join
operations might be unsuccessful and error "0xaac (2732):
NERR_AccountReuseBlockedByPolicy" occurs. Additionally, text stating "An
account with the same name exists in Active Directory. Re-using the account was
blocked by security policy" might be displayed. Workaround: Microsoft has added
guidance to KB 5020276 and recommends upgrading to a later version of
Windows as this nears EOS.
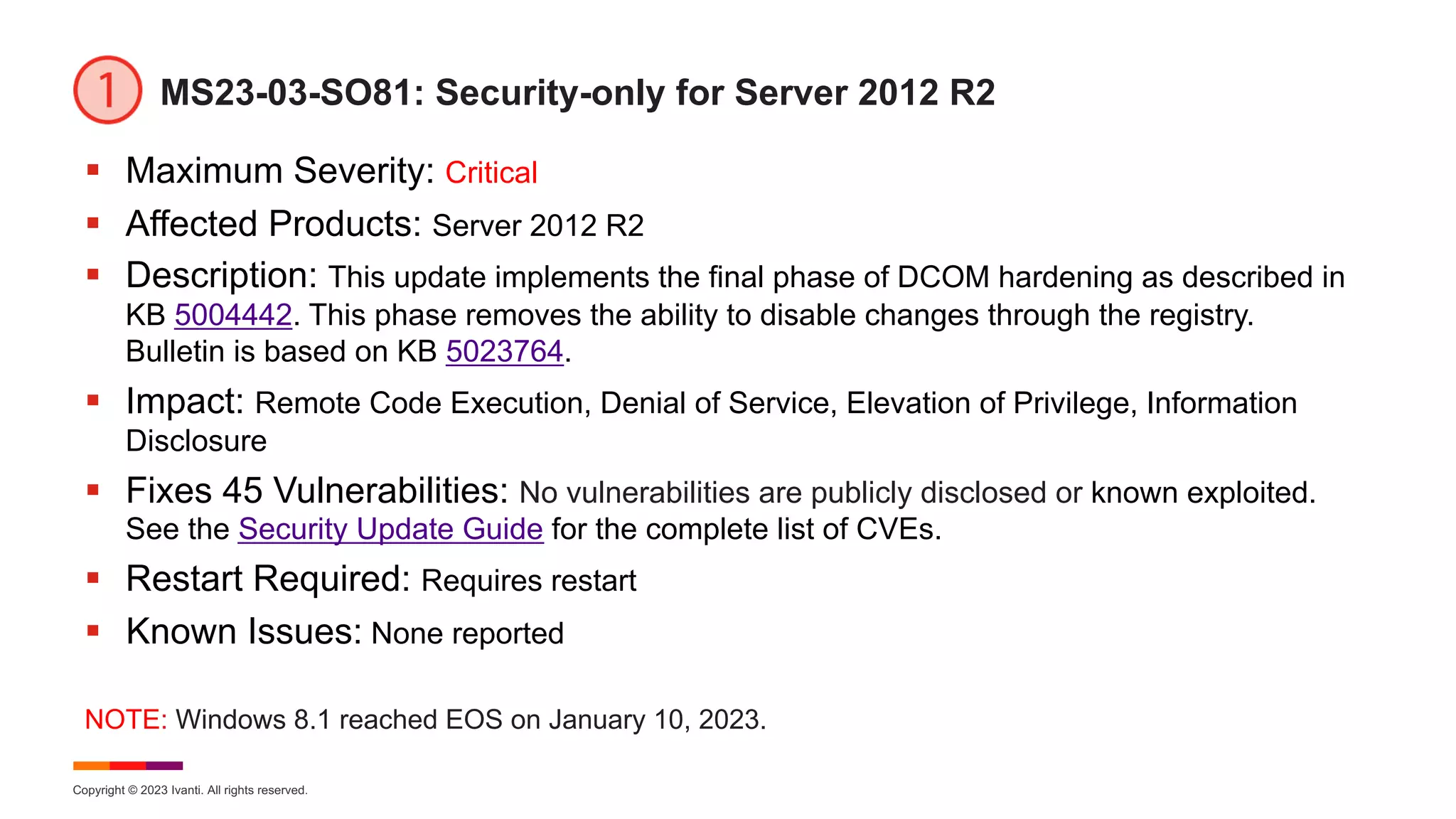
§ KB 5023752 – Windows Server 2012 (Security-only Update)
§ [Domain Join]](https://image.slidesharecdn.com/march2023patchtuesday-230315203400-1ae5b3a5/75/2023-March-Patch-Tuesday-26-2048.jpg)
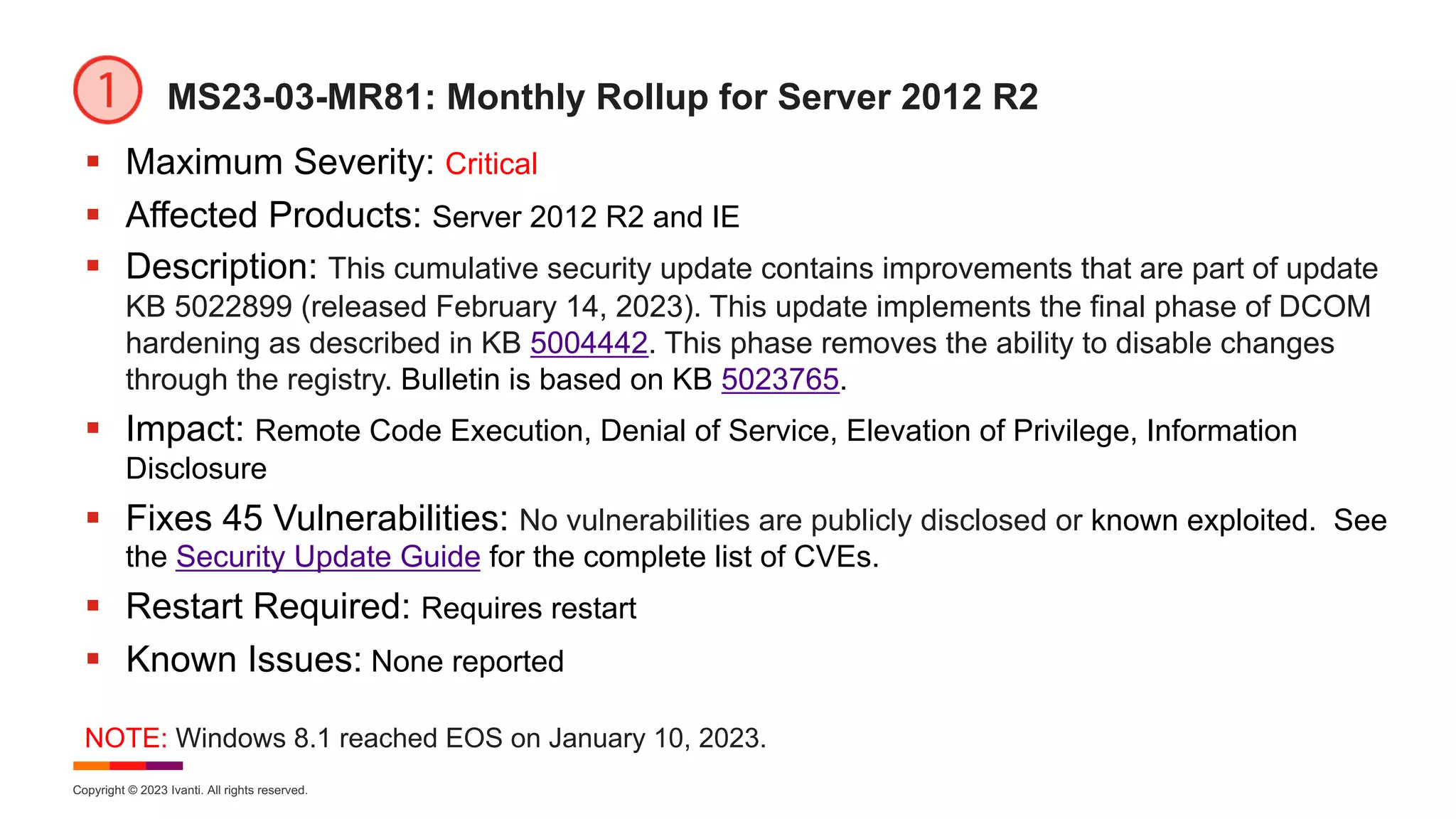
![Copyright © 2023 Ivanti. All rights reserved.
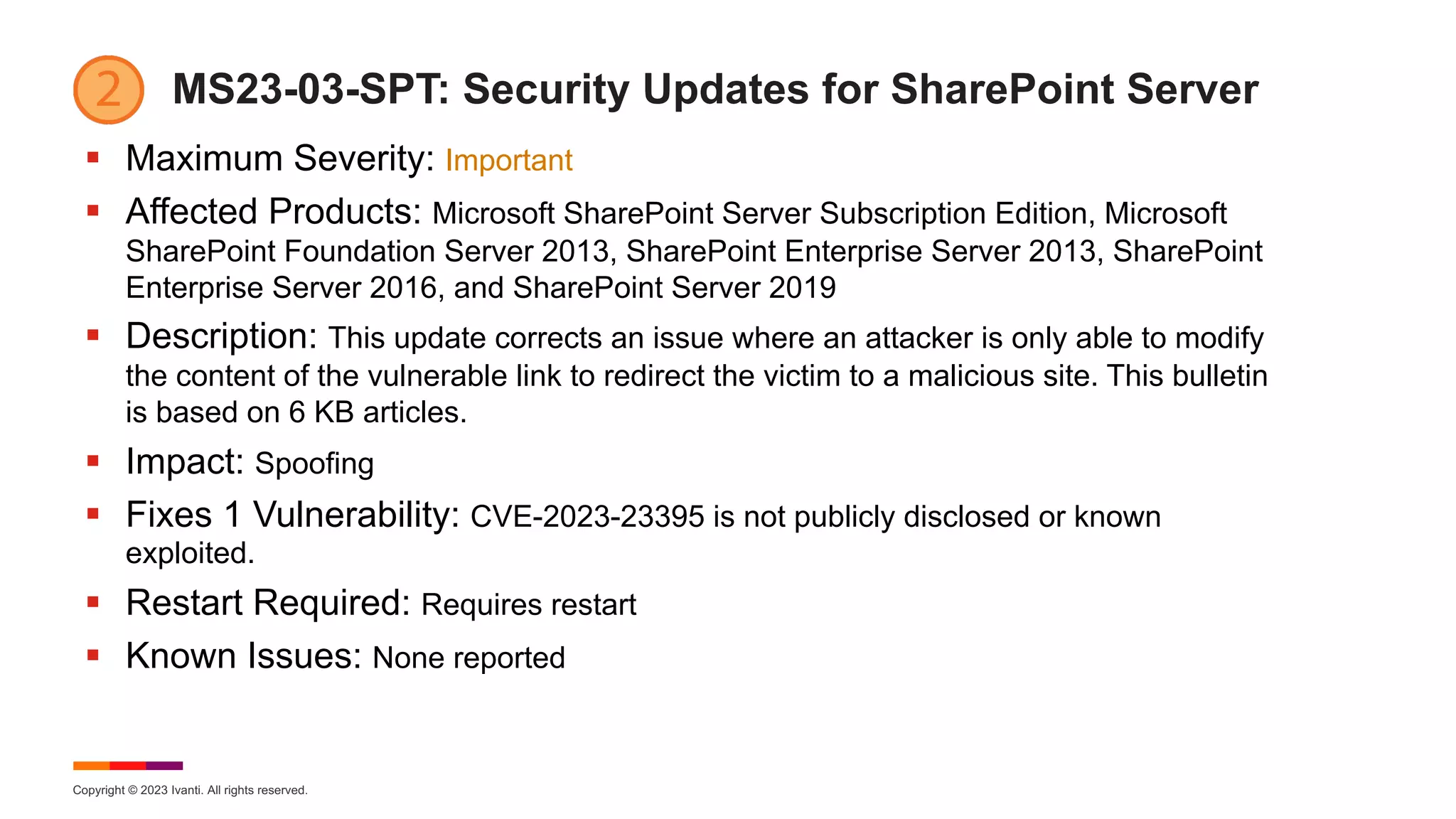
MS23-03-SO8: Security-only Update for Windows Server 2012
§ Maximum Severity: Critical
§ Affected Products: Microsoft Windows Server 2012
§ Description: This update implements the final phase of DCOM hardening as
described in KB 5004442. This phase removes the ability to disable changes through
the registry. Bulletin is based on KB 5023752.
§ Impact: Remote Code Execution, Denial of Service, Elevation of Privilege,
Information Disclosure
§ Fixes 44 Vulnerabilities: No vulnerabilities are publicly disclosed or known
exploited. See the Security Update Guide for the complete list of CVEs.
§ Restart Required: Requires restart
§ Known Issues: [Domain Join]](https://image.slidesharecdn.com/march2023patchtuesday-230315203400-1ae5b3a5/75/2023-March-Patch-Tuesday-27-2048.jpg)