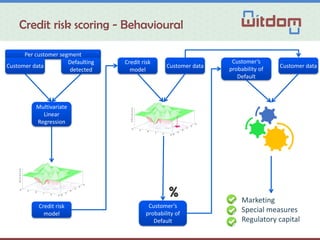
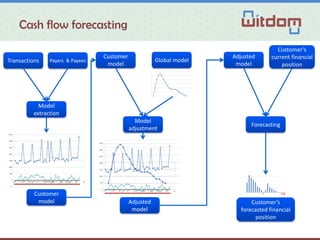
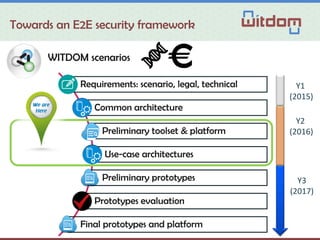
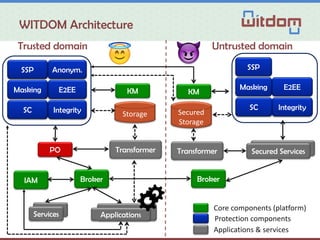
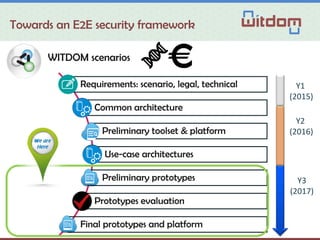
The document discusses the Witdom project, aimed at securing outsourced financial data in untrusted environments, specifically targeting the finance sector. It outlines a framework for end-to-end protection of data, detailing scenarios, legal and technical requirements, architecture, and anticipated outcomes over a three-year period starting in 2015. The project involves collaboration among seven organizations from five European countries, with a budget of 4 million euros supported by the EU's Horizon 2020 program.