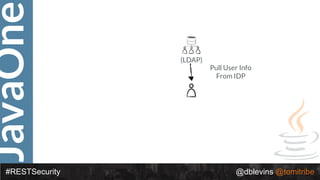
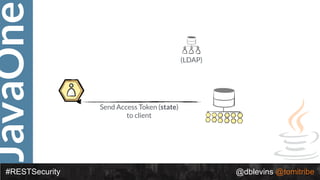
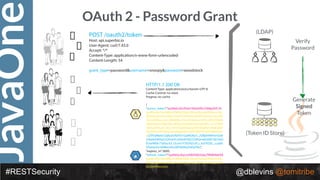
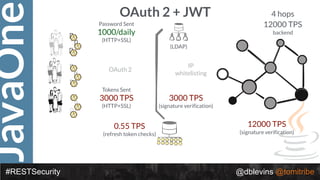
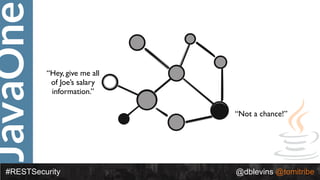
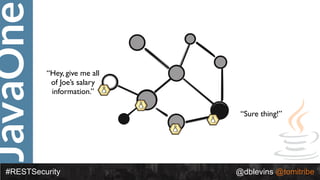
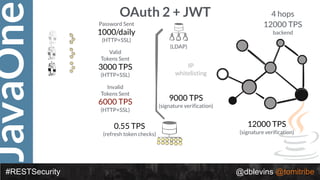
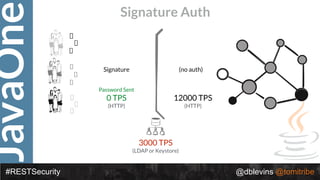
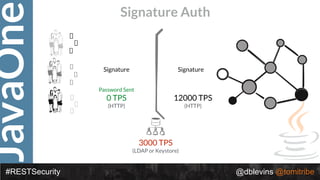
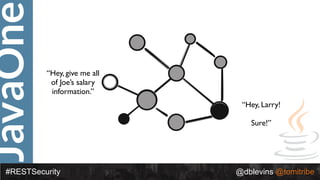
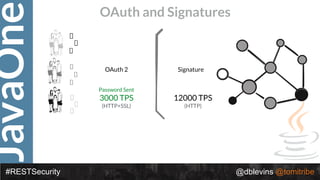
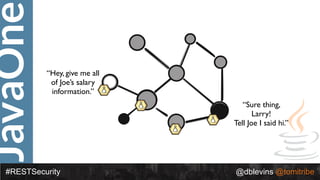
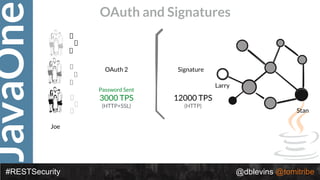
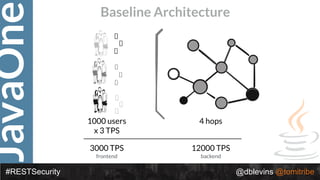
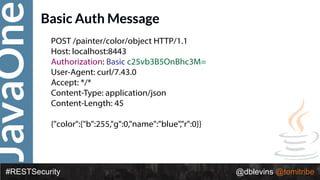
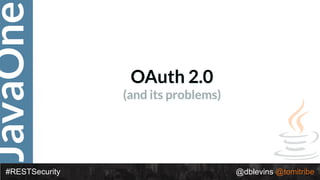
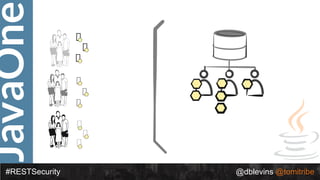
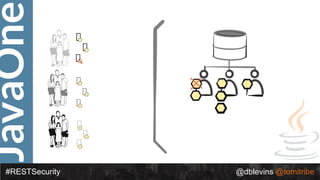
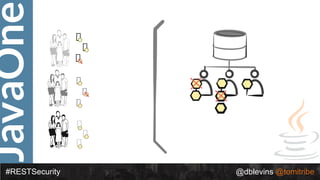
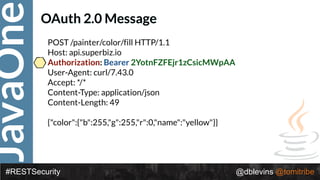
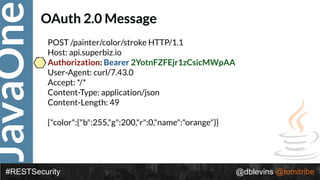
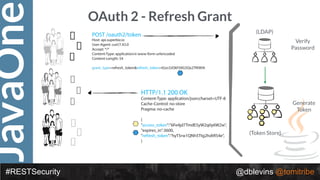
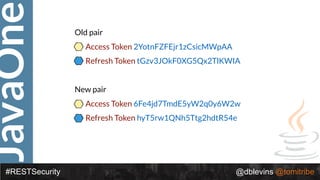
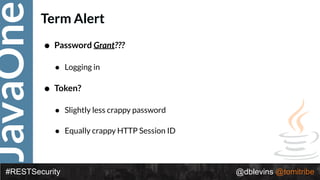
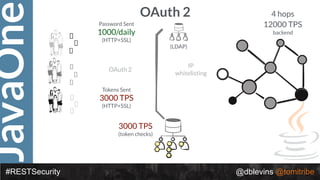
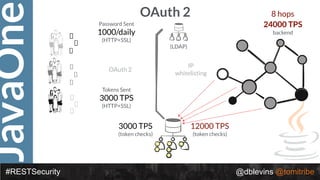
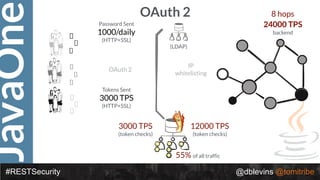
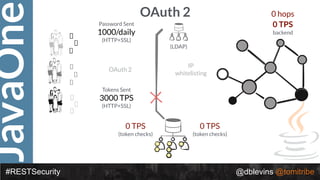
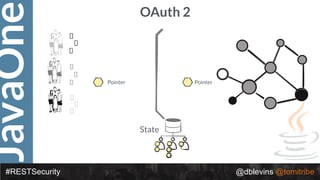
The document discusses REST security, focusing on various authentication and authorization mechanisms including basic auth, OAuth 2.0, and JSON Web Tokens (JWT). It highlights the performance metrics, potential security issues, and architectural changes when implementing these security models. Additionally, the document emphasizes the advantages of using JWT over traditional methods for improved security and efficiency in user authentication.














![JavaOne
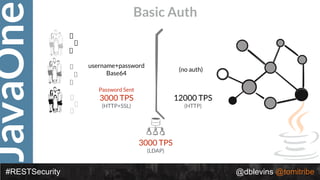
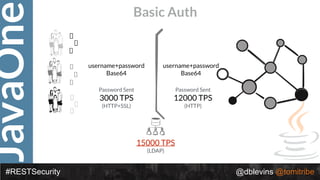
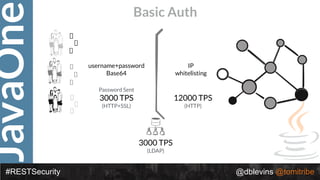
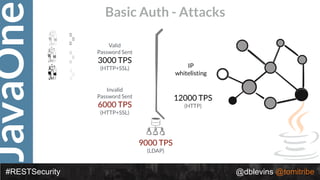
#RESTSecurity @dblevins @tomitribe
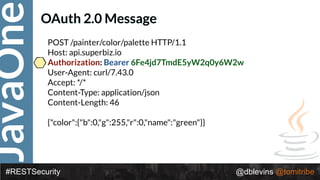
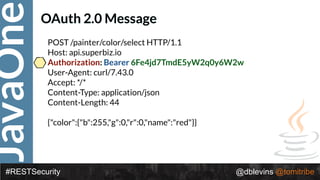
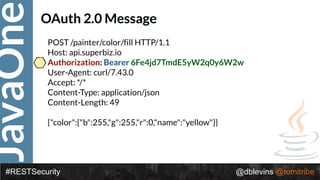
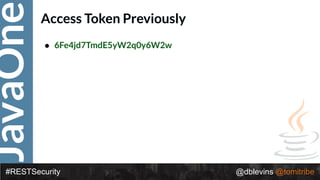
• { "alg": “RS256", "typ": “JWT" }
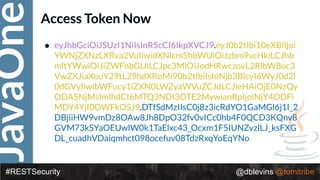
• {
"token-type": "access-token",
"username": "snoopy",
"animal": "beagle",
"iss": "https://demo.superbiz.com/oauth2/token",
"scopes": [
“twitter”, "mans-best-friend"
],
"exp": 1474280963,
"iat": 1474279163,
"jti": "66881b068b249ad9"
}
• DTfSdMzIIsC0j8z3icRdYO1GaMGl6j1I_2DBjiiHW9vmDz8OAw8Jh8DpO32fv0vIC
c0hb4F0QCD3KQnv8GVM73kSYaOEUwlW0k1TaElxc43_Ocxm1F5IUNZvzlLJ_ks
FXGDL_cuadhVDaiqmhct098ocefuv08TdzRxqYoEqYNo](https://image.slidesharecdn.com/2016javaonedeconstructingrestsecurity-161012192137/85/2016-JavaOne-Deconstructing-REST-Security-47-320.jpg)