The document discusses security options for stateless microservices, focusing on JWT and OAuth 2.0 as alternatives to basic authentication. It highlights the challenges of basic auth and introduces the structure and functionality of OAuth 2.0, including password grants and token management. Additionally, it explains how JSON Web Tokens (JWT) improve security through encoding and signing mechanisms.













































![#RESTSecurity @otaviojava @tomitribe
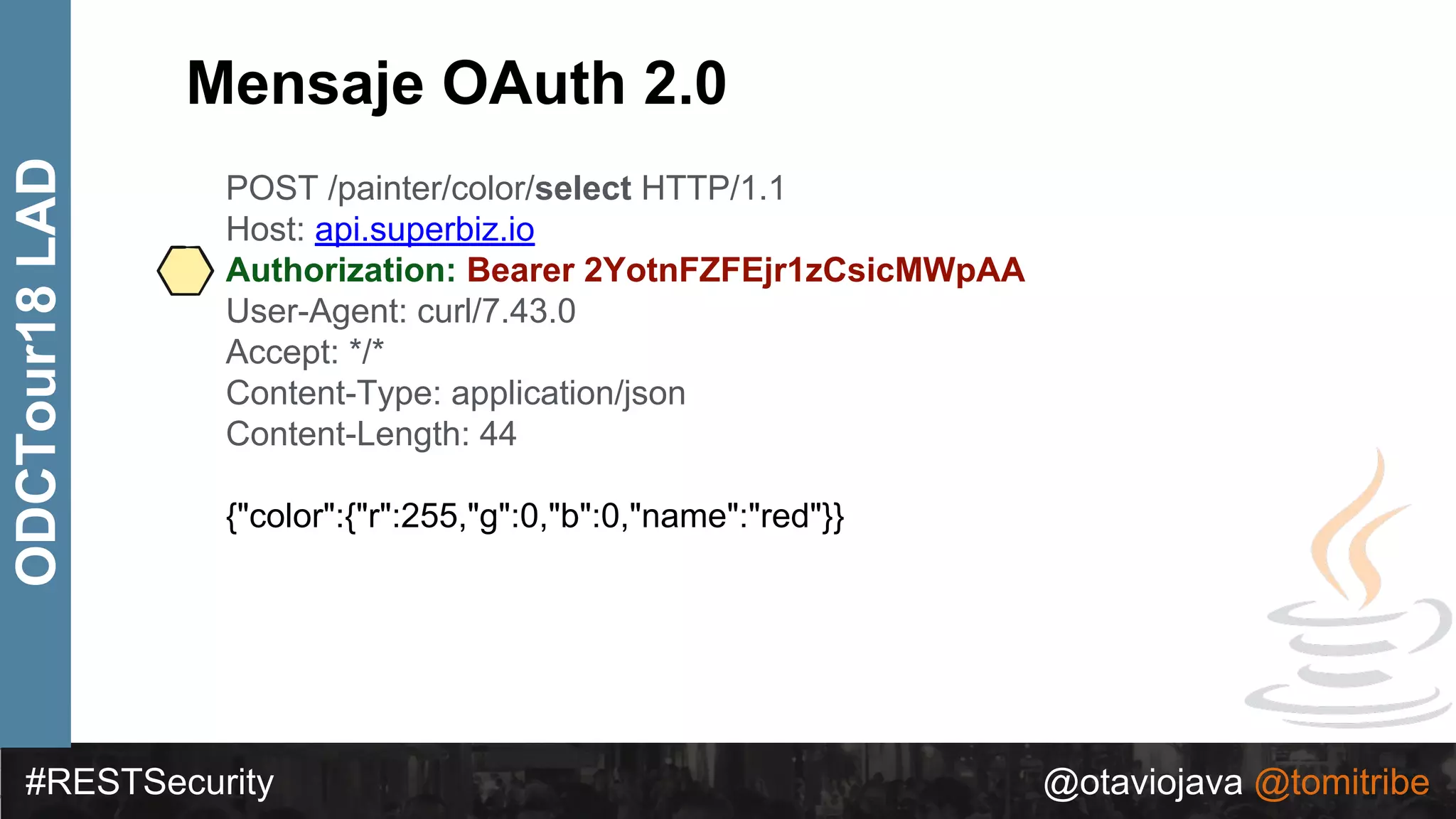
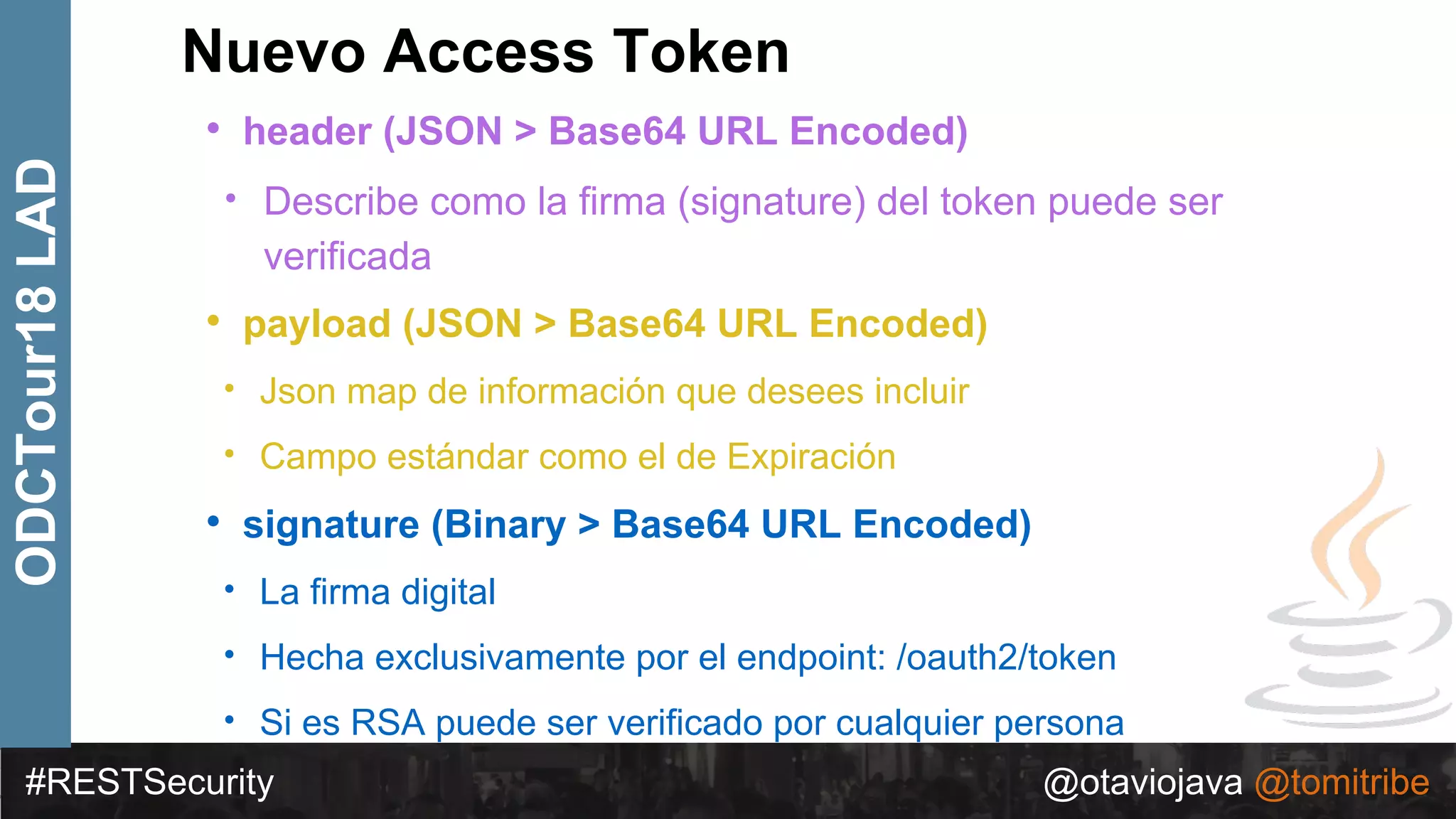
ODCTour18LAD ∙ { "alg": “RS256", "typ": “JWT" }
∙ {
"token-type": "access-token",
"username": "snoopy",
"animal": "beagle",
"iss": "https://demo.superbiz.com/oauth2/token",
"scopes": [
“twitter”, "mans-best-friend"
],
"exp": 1474280963,
"iat": 1474279163,
"jti": "66881b068b249ad9"
}
∙ DTfSdMzIIsC0j8z3icRdYO1GaMGl6j1I_2DBjiiHW9vmDz8OAw8Jh8DpO32fv0vI
Cc0hb4F0QCD3KQnv8GVM73kSYaOEUwlW0k1TaElxc43_Ocxm1F5IUNZvzlLJ
_ksFXGDL_cuadhVDaiqmhct098ocefuv08TdzRxqYoEqYNo](https://image.slidesharecdn.com/statelessmicroservicesecurityviajwtandmicroprofile-es2-180824151941/75/Stateless-Microservice-Security-via-JWT-and-MicroProfile-Mexico-49-2048.jpg)






























