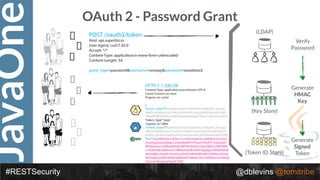
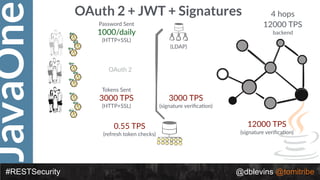
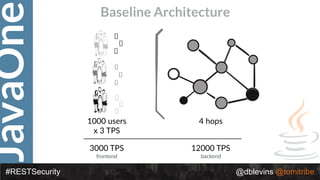
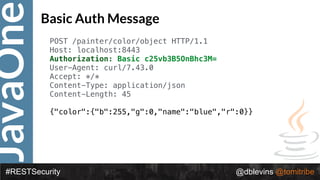
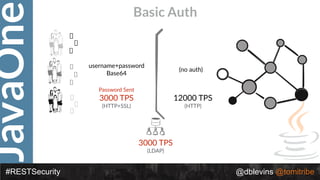
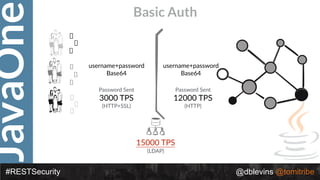
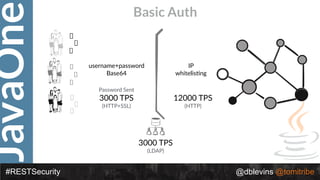
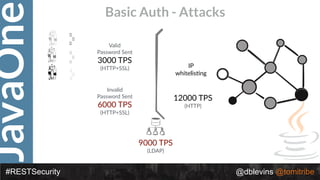
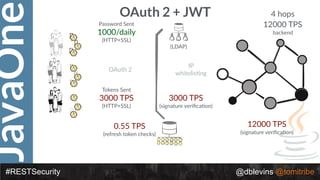
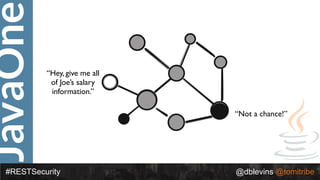
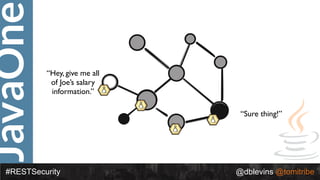
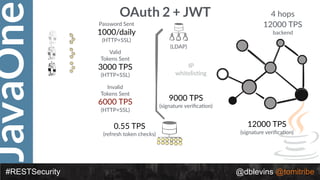
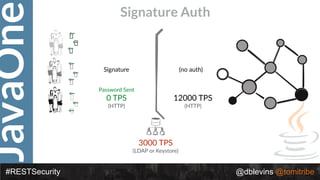
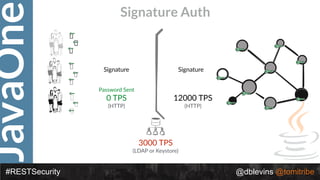
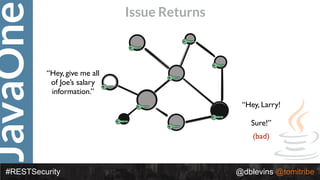
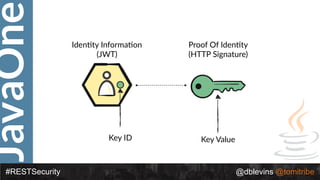
The document discusses REST security at the JavaOne conference, covering topics such as basic authentication, OAuth 2.0, and JWT. It highlights the issues related to these security methods, including their performance under various conditions and potential vulnerabilities. Finally, it illustrates practical examples of API requests demonstrating the functionality and limitations of the discussed security protocols.







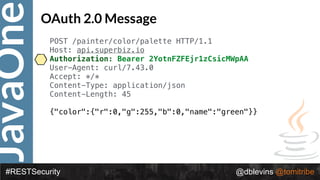

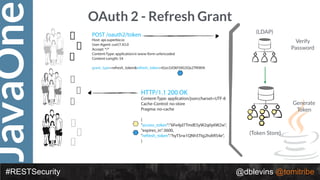


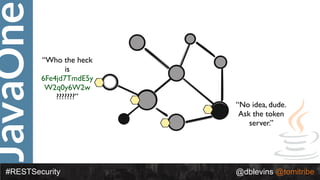
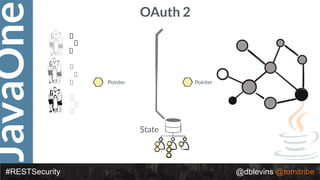








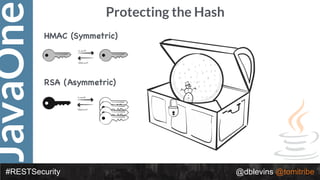




![JavaOne
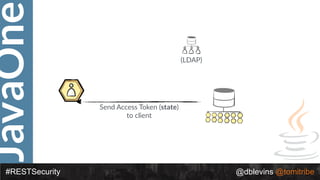
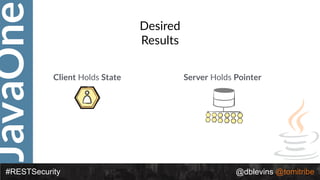
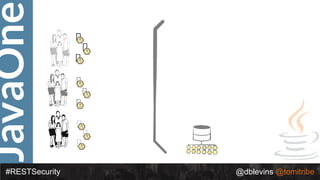
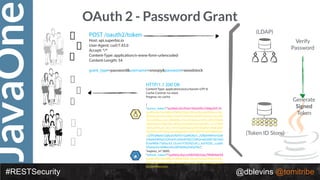
#RESTSecurity @dblevins @tomitribe
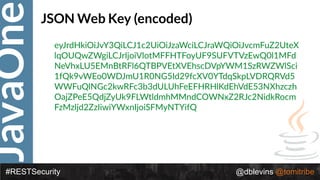
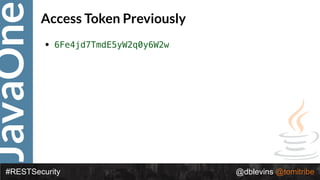
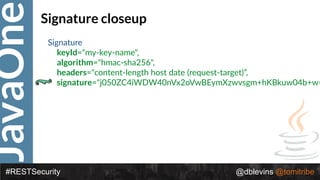
• { "alg": “RS256", "typ": “JWT" }
• {
"token-type": "access-token",
"username": "snoopy",
"animal": "beagle",
"iss": "https://demo.superbiz.com/oauth2/token",
"scopes": [
“twitter”, "mans-best-friend"
],
"exp": 1474280963,
"iat": 1474279163,
"jti": "66881b068b249ad9"
}
• DTfSdMzIIsC0j8z3icRdYO1GaMGl6j1I_2DBjiiHW9vmDz8OAw8Jh8DpO32fv
0vICc0hb4F0QCD3KQnv8GVM73kSYaOEUwlW0k1TaElxc43_Ocxm1F5IUNZvzl
LJ_ksFXGDL_cuadhVDaiqmhct098ocefuv08TdzRxqYoEqYNo](https://image.slidesharecdn.com/2017javaonedeconstructingandevolvingrestsecurity-171005022436/85/2017-JavaOne-Deconstructing-and-Evolving-REST-Security-58-320.jpg)



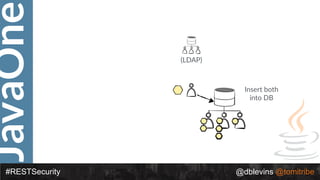
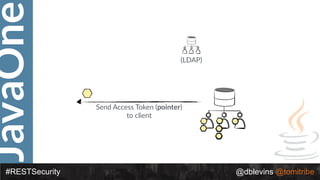

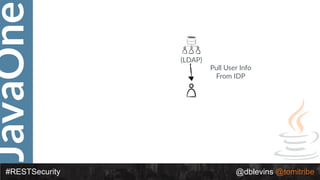









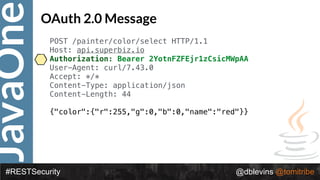
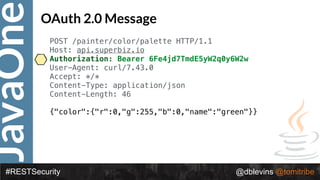
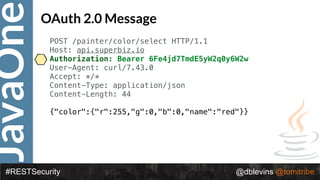
![JavaOne
#RESTSecurity @dblevins @tomitribe
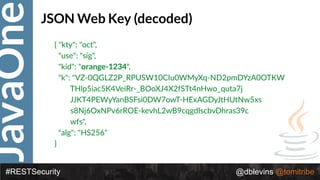
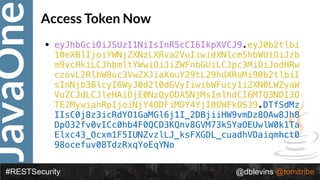
{ "alg": “RS256", "typ": “JWT" }
{ "token-type": "access-token",
"username": "snoopy",
"iss": "hmps://demo.superbiz.com/oauth2/token",
"scopes": ["twimer”, "mans-best-friend"],
"exp": 1474280963,
"iat": 1474279163,
"j?": "66881b068b249ad9"
}
DTfSdMzIIsC0j8z3icRdYO1GaMGl6j1I_2DBjiiHW9vmDz8OAw8Jh8DpO32fv0vICc
0hb4F0QCD3KQnv8GVM73kSYaOEUwlW0k1TaElxc43_Ocxm1F5IUNZvzlLJ_ksFX
GDL_cuadhVDaiqmhct098ocefuv08TdzRxqYoEqYNo
Access Token](https://image.slidesharecdn.com/2017javaonedeconstructingandevolvingrestsecurity-171005022436/85/2017-JavaOne-Deconstructing-and-Evolving-REST-Security-90-320.jpg)
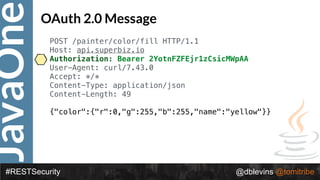
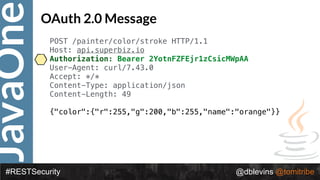
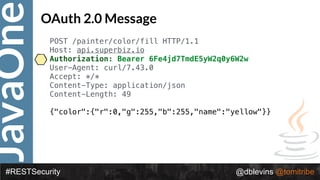
![JavaOne
#RESTSecurity @dblevins @tomitribe
{ "alg": “RS256", "typ": “JWT" }
{ "token-type": "pop",
"cnf":{ "kid": "green-1234" }
"username": "snoopy",
"iss": "hmps://demo.superbiz.com/oauth2/token",
"scopes": ["twimer”, "mans-best-friend"],
"exp": 1474280963,
"iat": 1474279163,
"j?": "66881b068b249ad9"
}
DTfSdMzIIsC0j8z3icRdYO1GaMGl6j1I_2DBjiiHW9vmDz8OAw8Jh8DpO32fv0vICc
0hb4F0QCD3KQnv8GVM73kSYaOEUwlW0k1TaElxc43_Ocxm1F5IUNZvzlLJ_ksFX
GDL_cuadhVDaiqmhct098ocefuv08TdzRxqYoEqYNo
Access Token](https://image.slidesharecdn.com/2017javaonedeconstructingandevolvingrestsecurity-171005022436/85/2017-JavaOne-Deconstructing-and-Evolving-REST-Security-91-320.jpg)