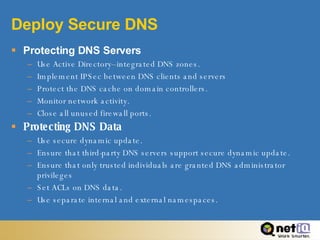
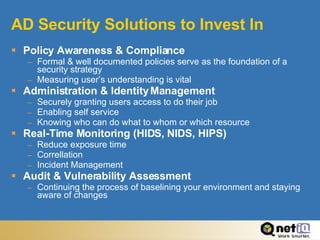
The document provides best practices for securing Active Directory, including establishing secure boundaries, deploying secure domain controllers, establishing secure policies, and maintaining secure operations. It recommends limiting physical access, disabling unnecessary services, using strong passwords, monitoring for changes, and staying current on security updates. The summary emphasizes maintaining secure domain controller operations, using tools like VPNs, firewalls, and intrusion detection to protect communications and assets.
![Best Practices for Securing Active Directory Dana J. Willis Security Engineer NetIQ Corporation [email_address]](https://image.slidesharecdn.com/200308-active-directory-security-1219445313102870-9/85/200308-Active-Directory-Security-1-320.jpg)