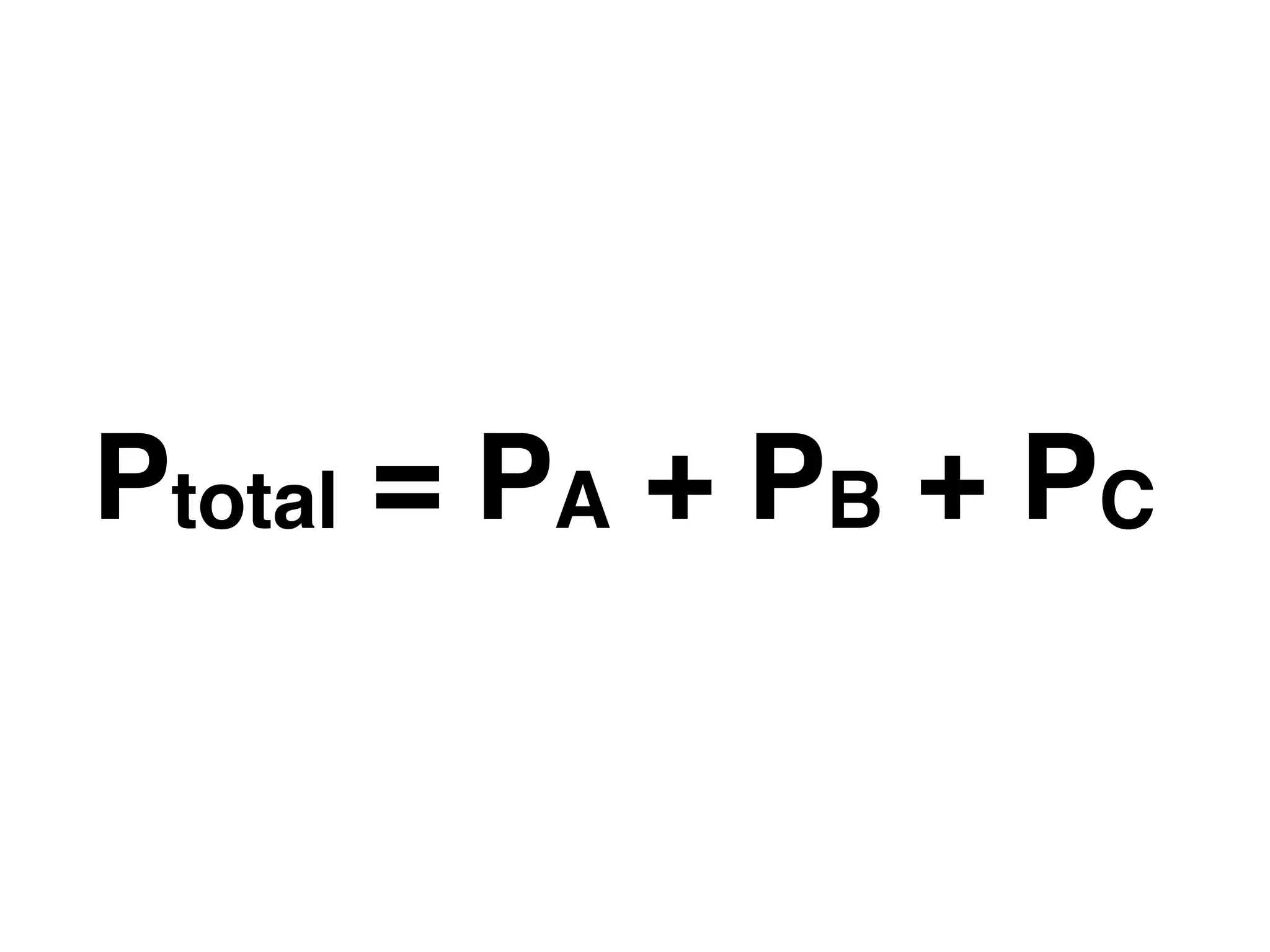Embed presentation
Download as PDF, PPTX

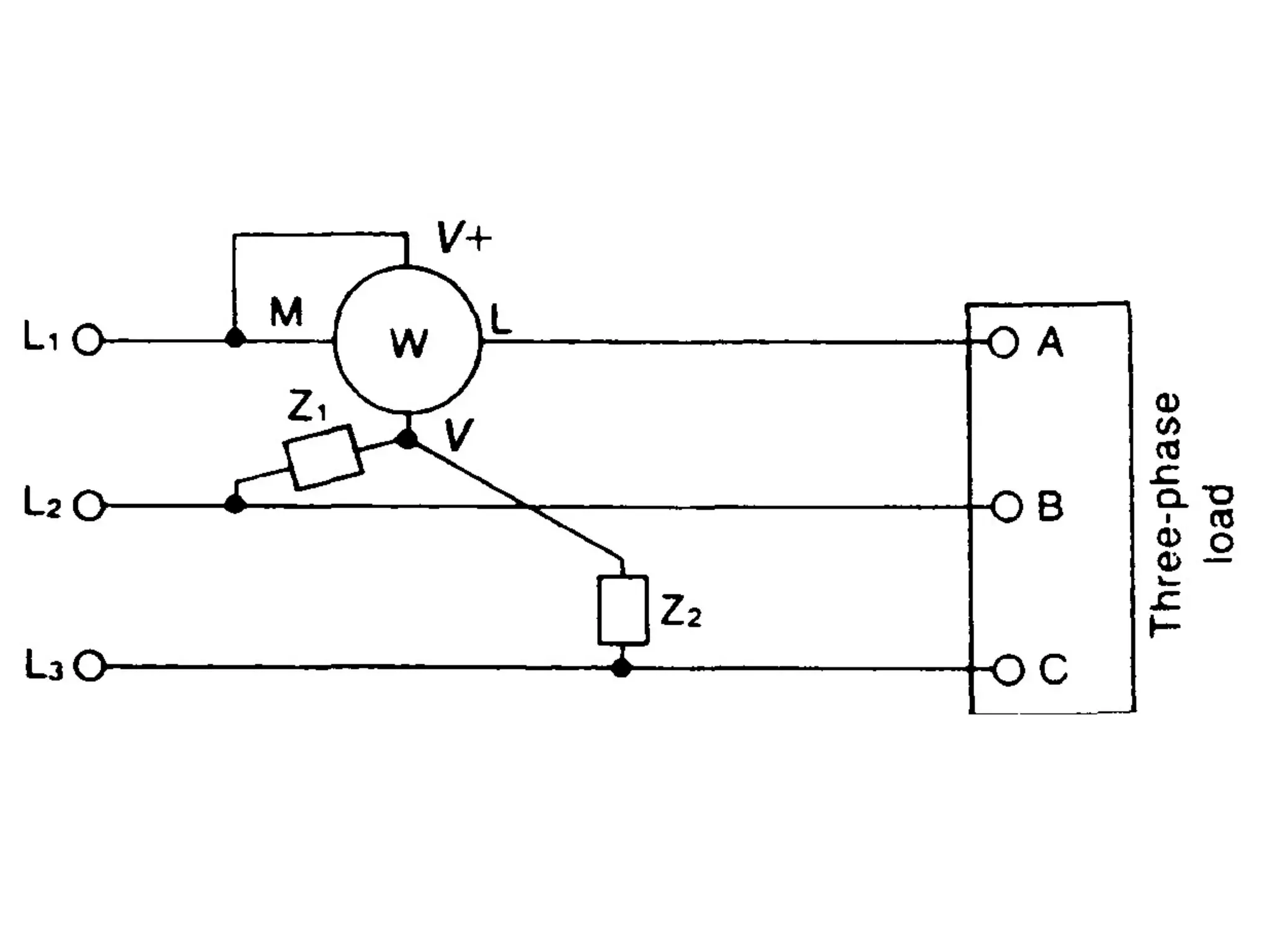
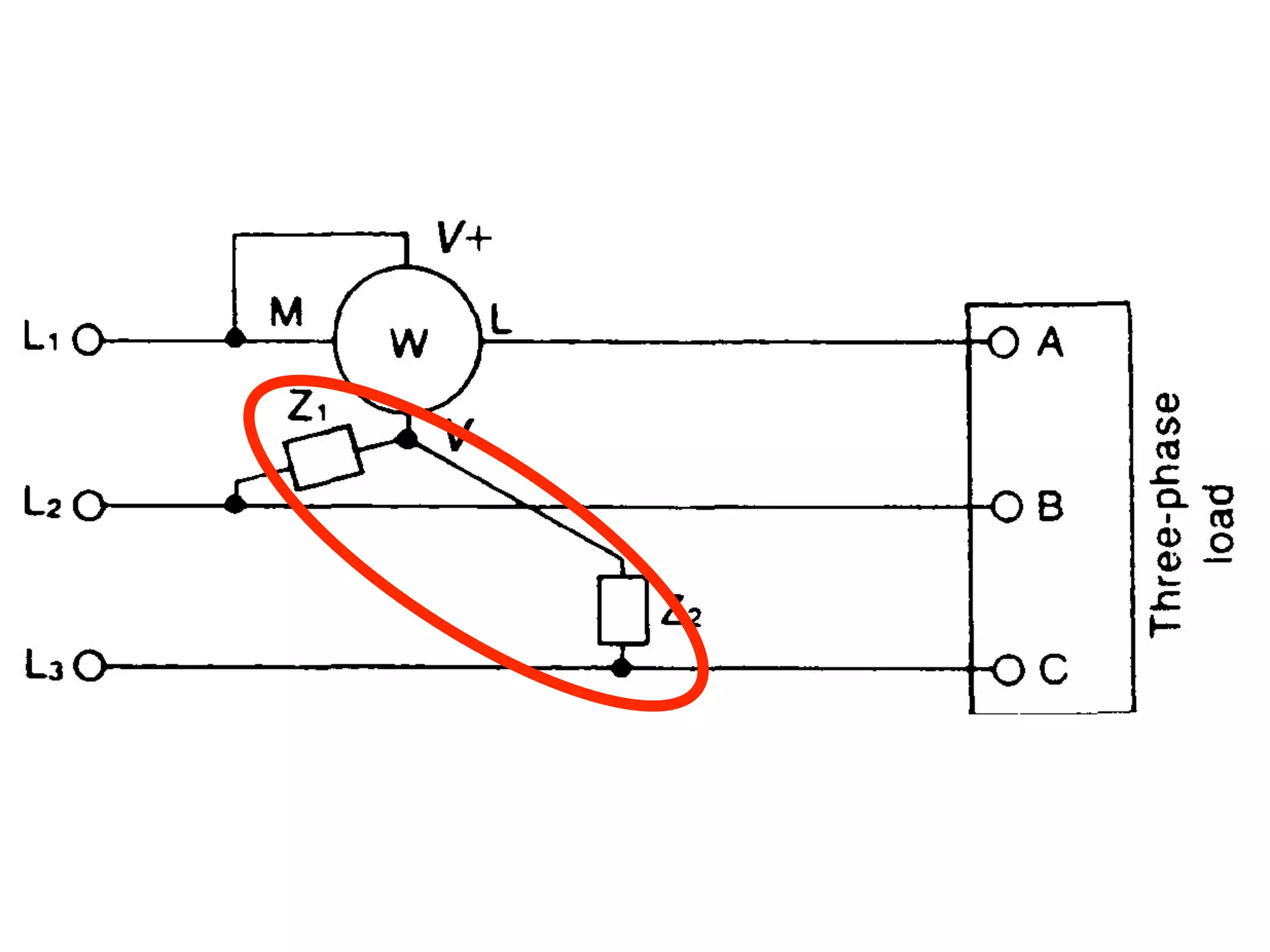
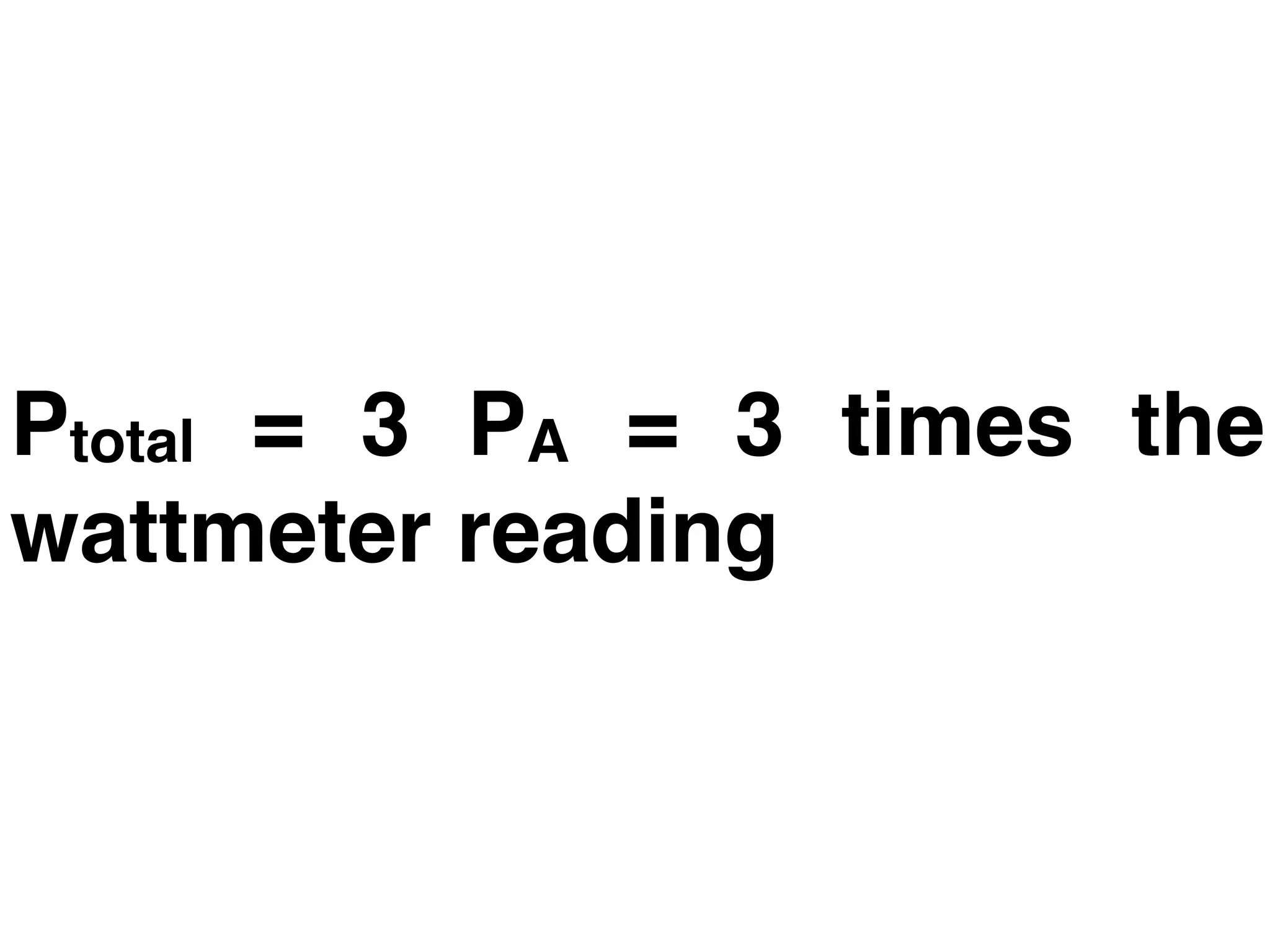
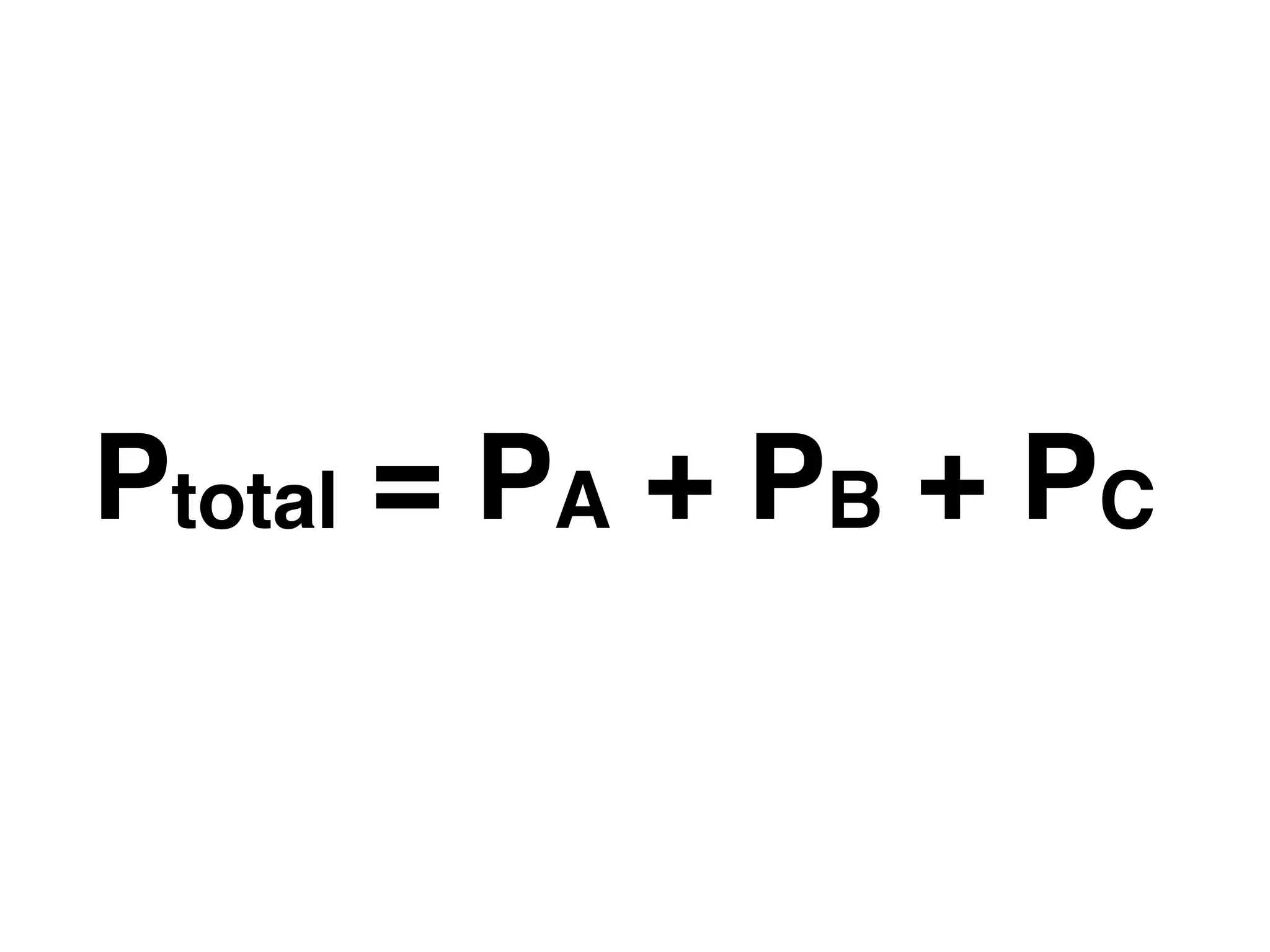

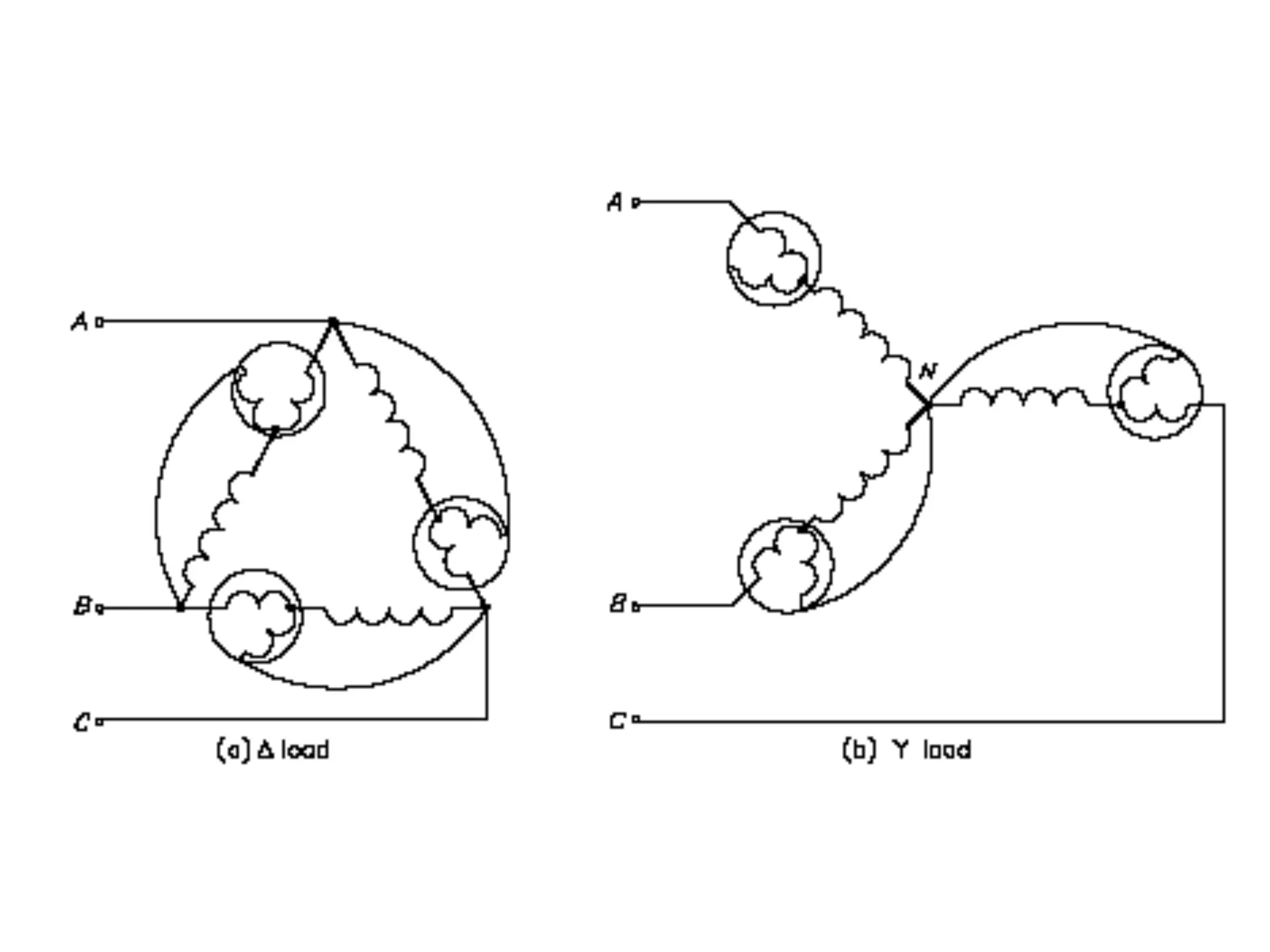
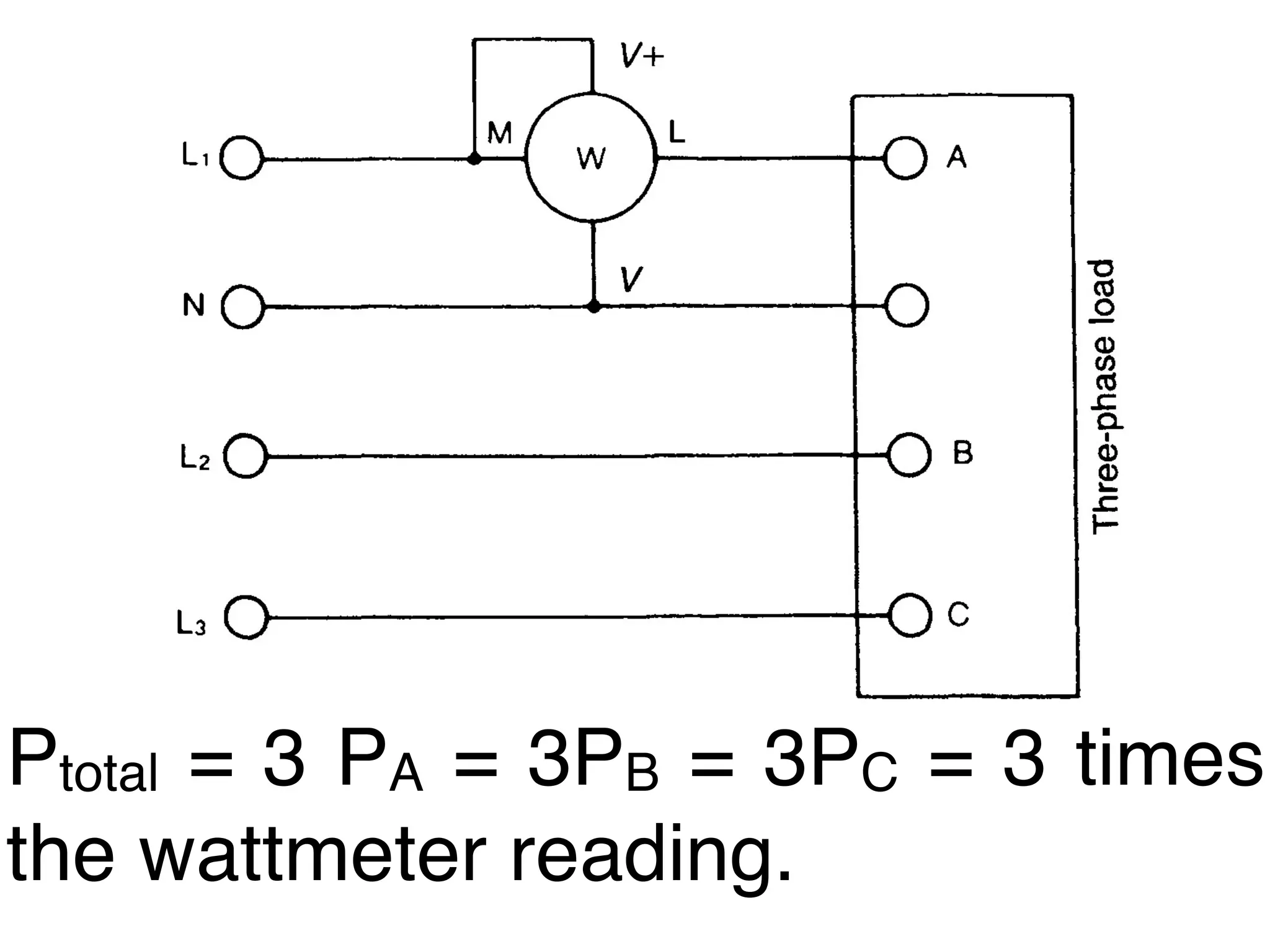
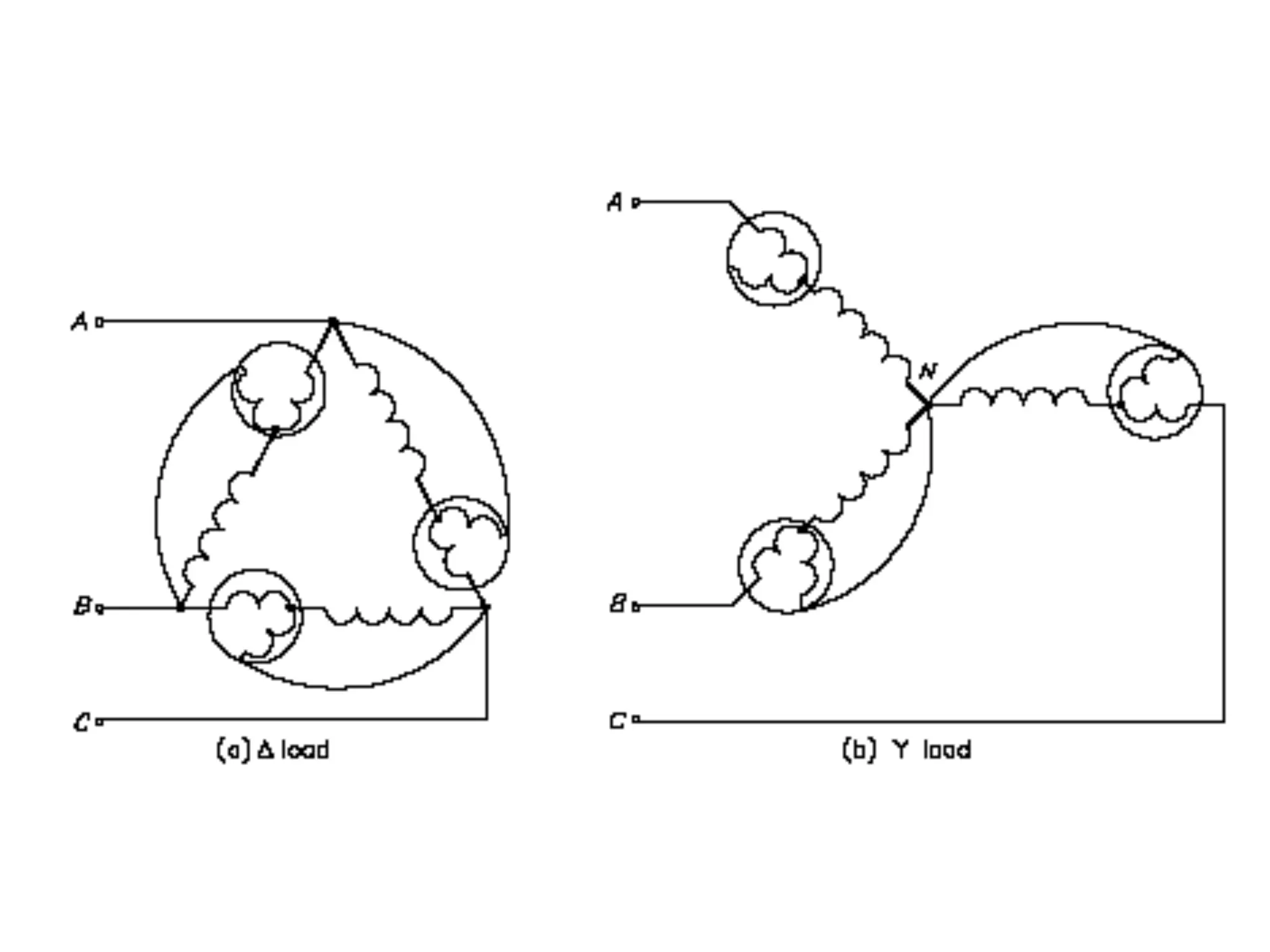

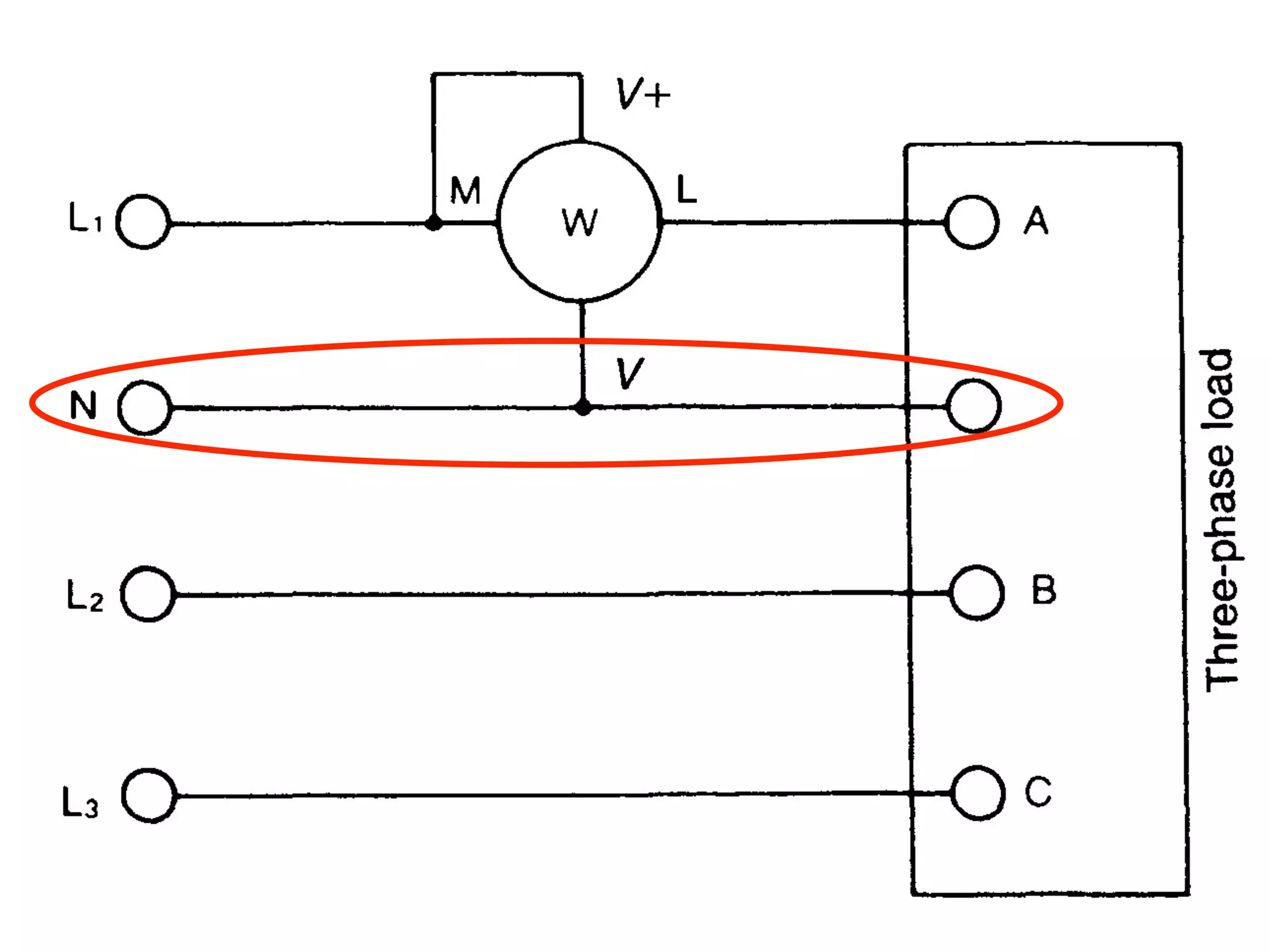
This document discusses how to calculate the total power (Ptotal) used by three devices (A, B, and C) based on a single wattmeter reading. It states that the total power is equal to the power used by device A plus the power used by device B plus the power used by device C, and that the power used by each device individually is three times the wattmeter reading.