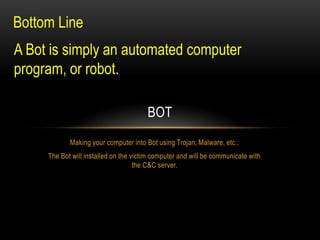
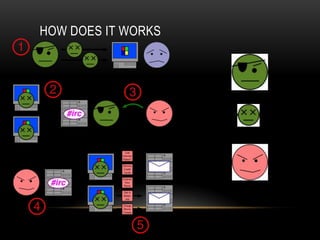
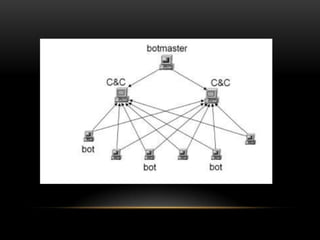
This document provides an overview of botnets, including what they are, how they work, and examples of real botnets. It defines a botnet as a network of compromised computers called bots that are controlled remotely and in a coordinated way without the owner's consent. The document discusses how botnets infect computers using malware, how they communicate with command and control servers, how they are used to conduct DDoS attacks, steal money and personal information, and ways that botnets can be detected and mitigated.