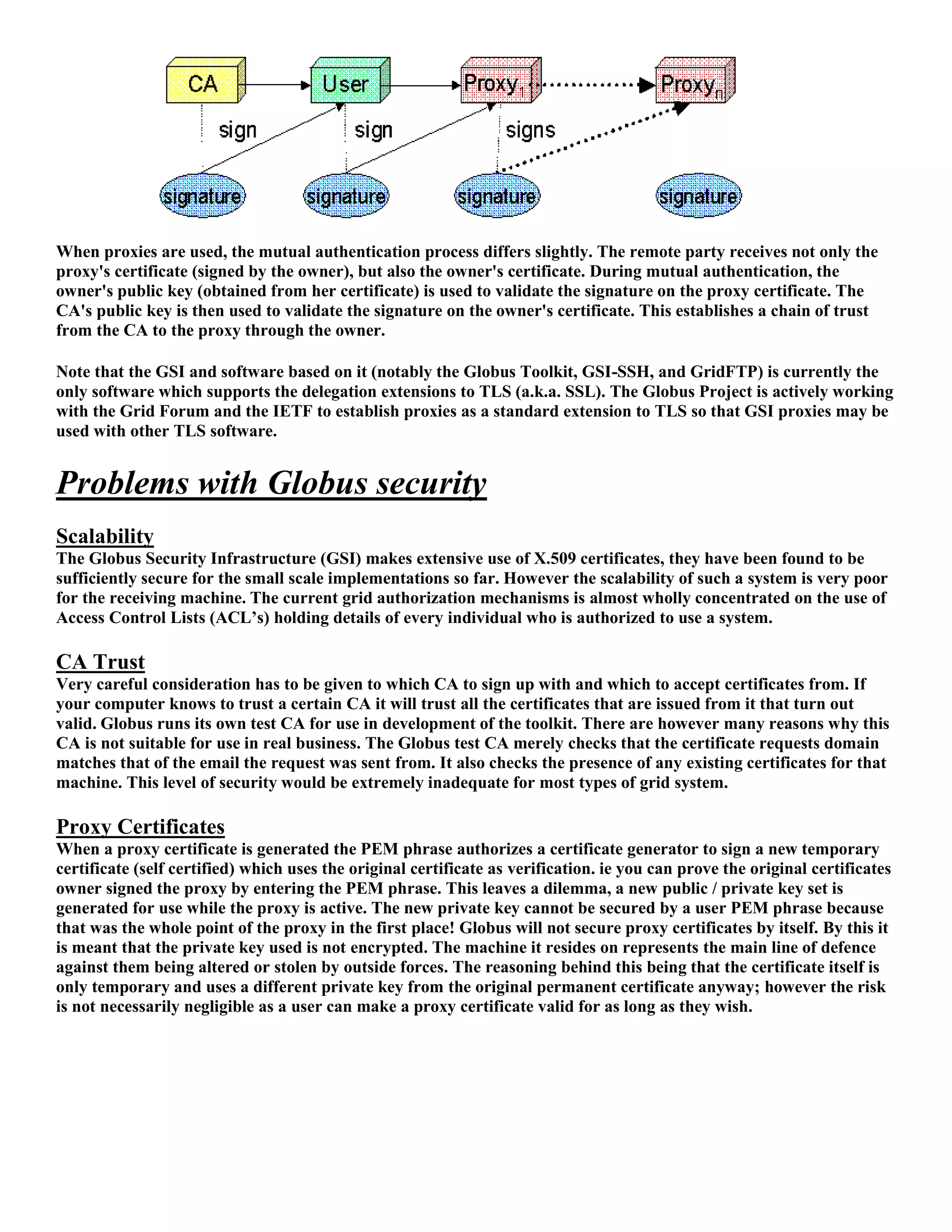
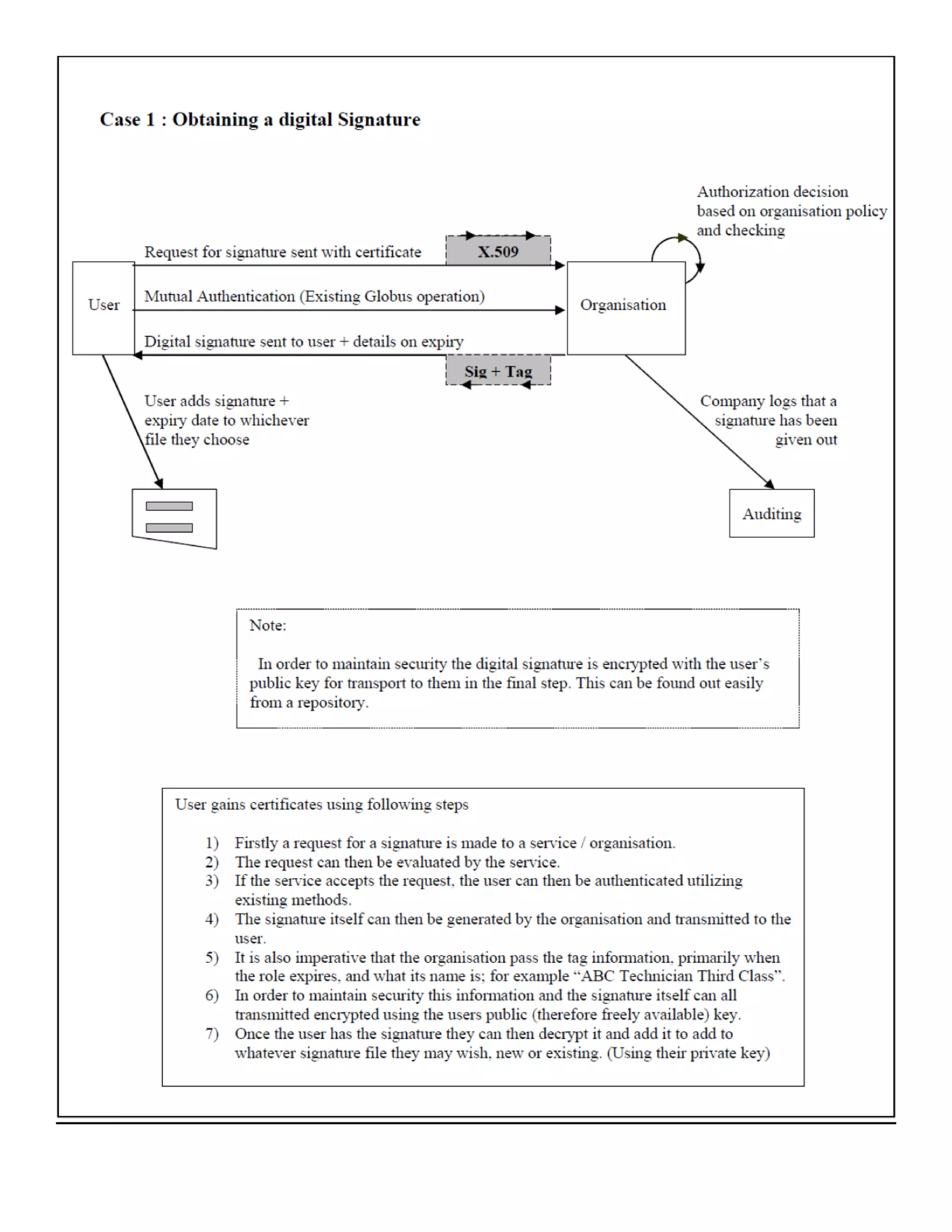
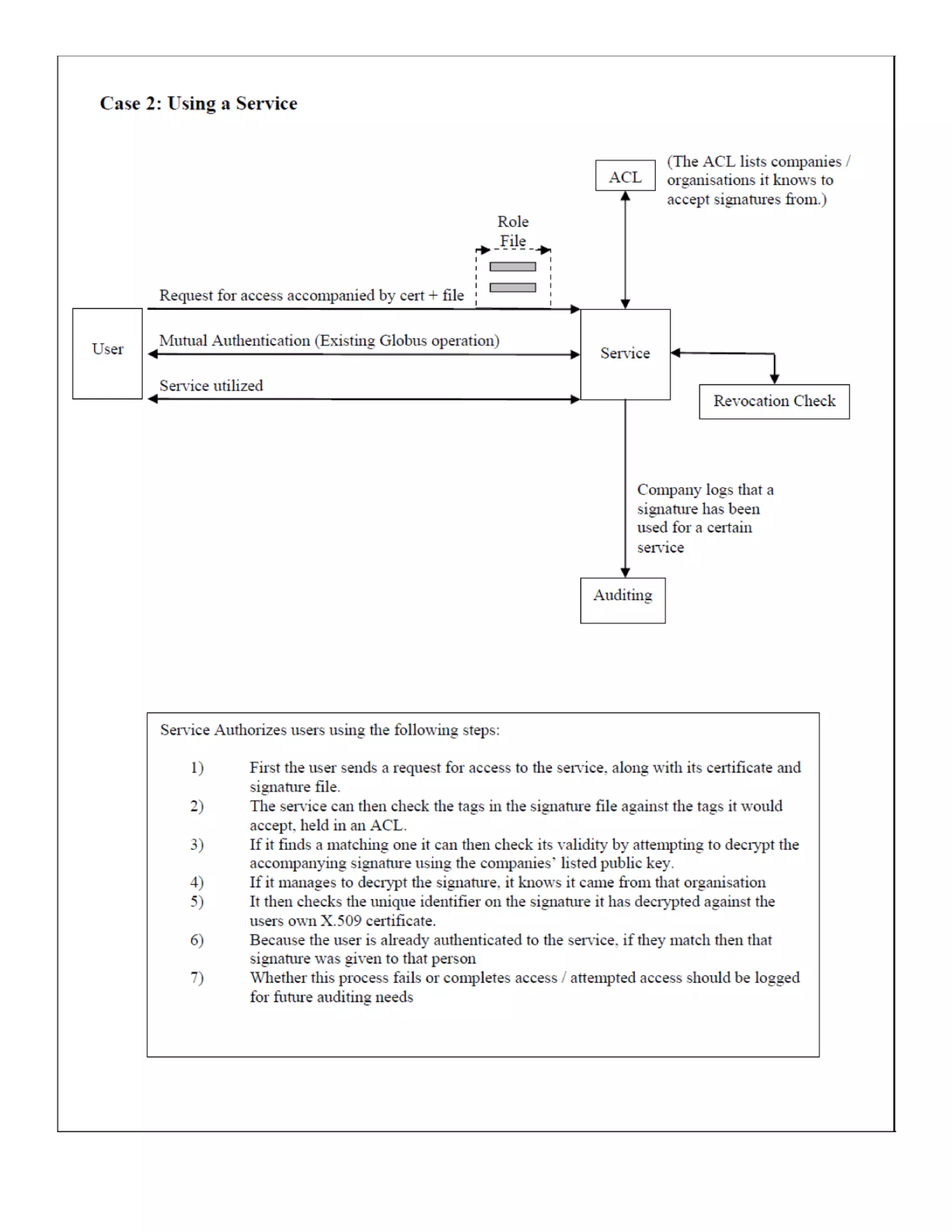
1) The document discusses security requirements for computational grids, including authentication, authorization, integrity and confidentiality. It focuses on the use of X.509 certificates.
2) The introduction defines a computational grid as a system that coordinates distributed resources across administrative domains to provide quality of service.
3) The security model section explains the Globus security model, including the use of public key cryptography, digital signatures, certificates, and mutual authentication using SSL.