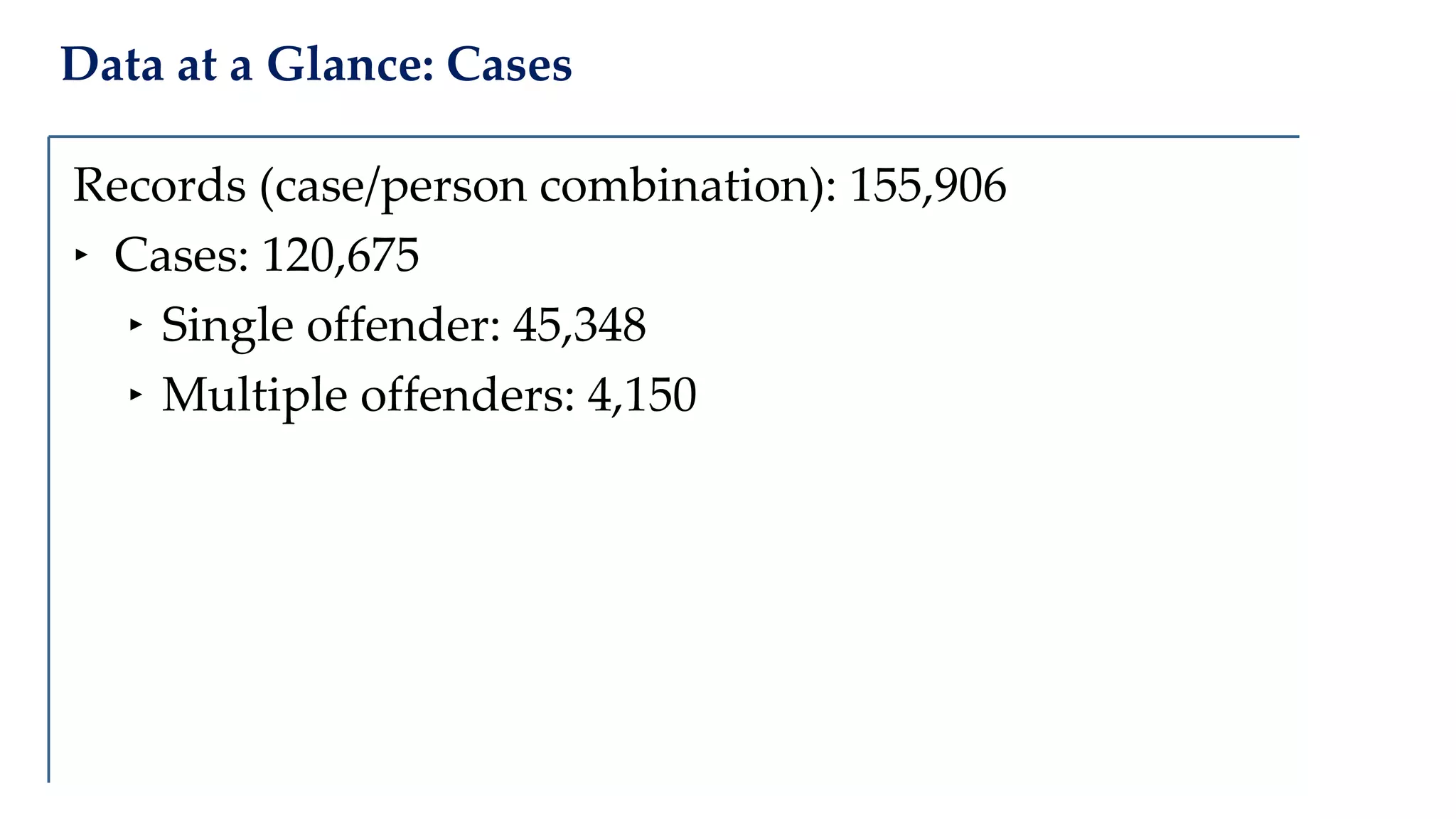
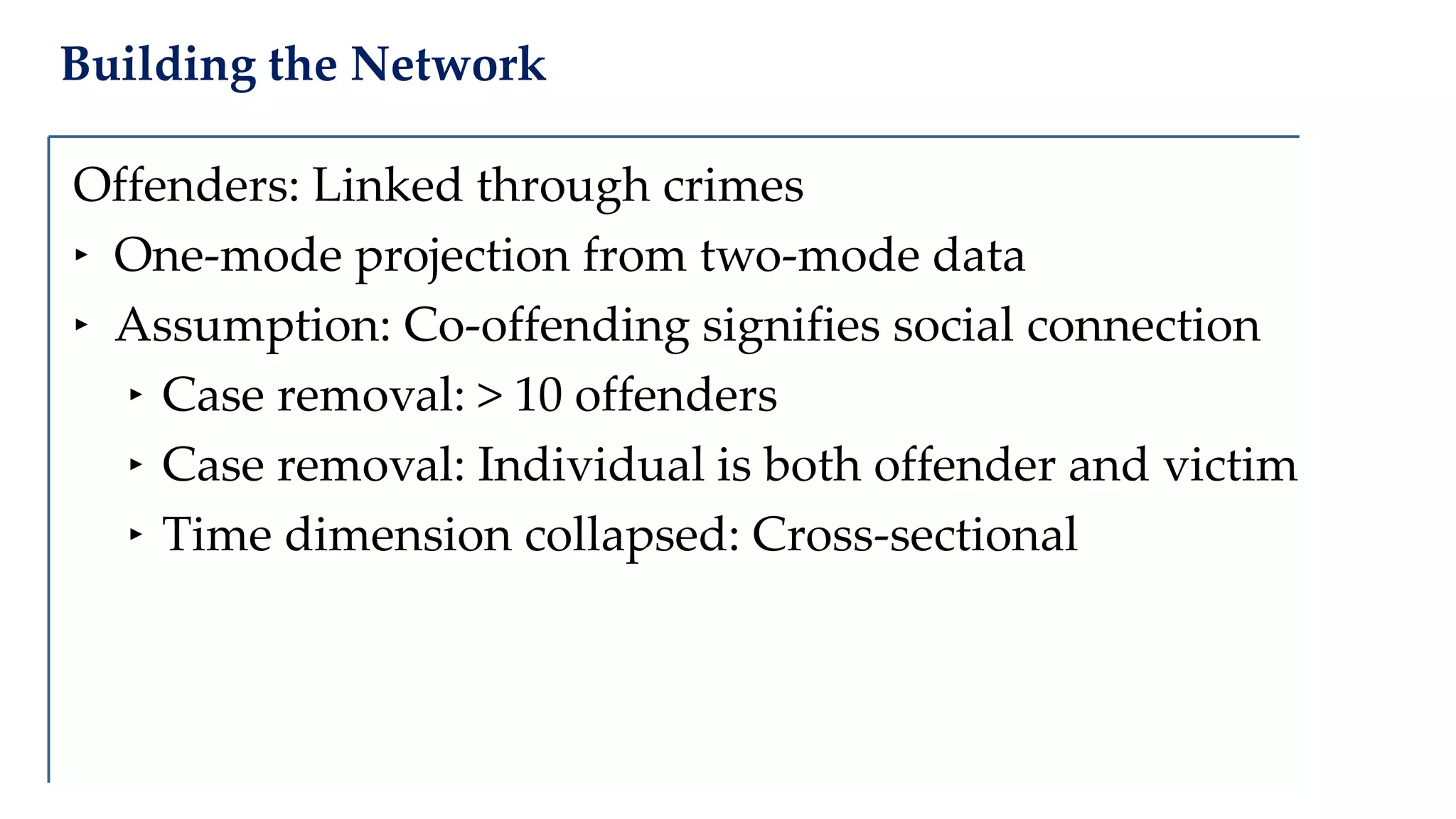
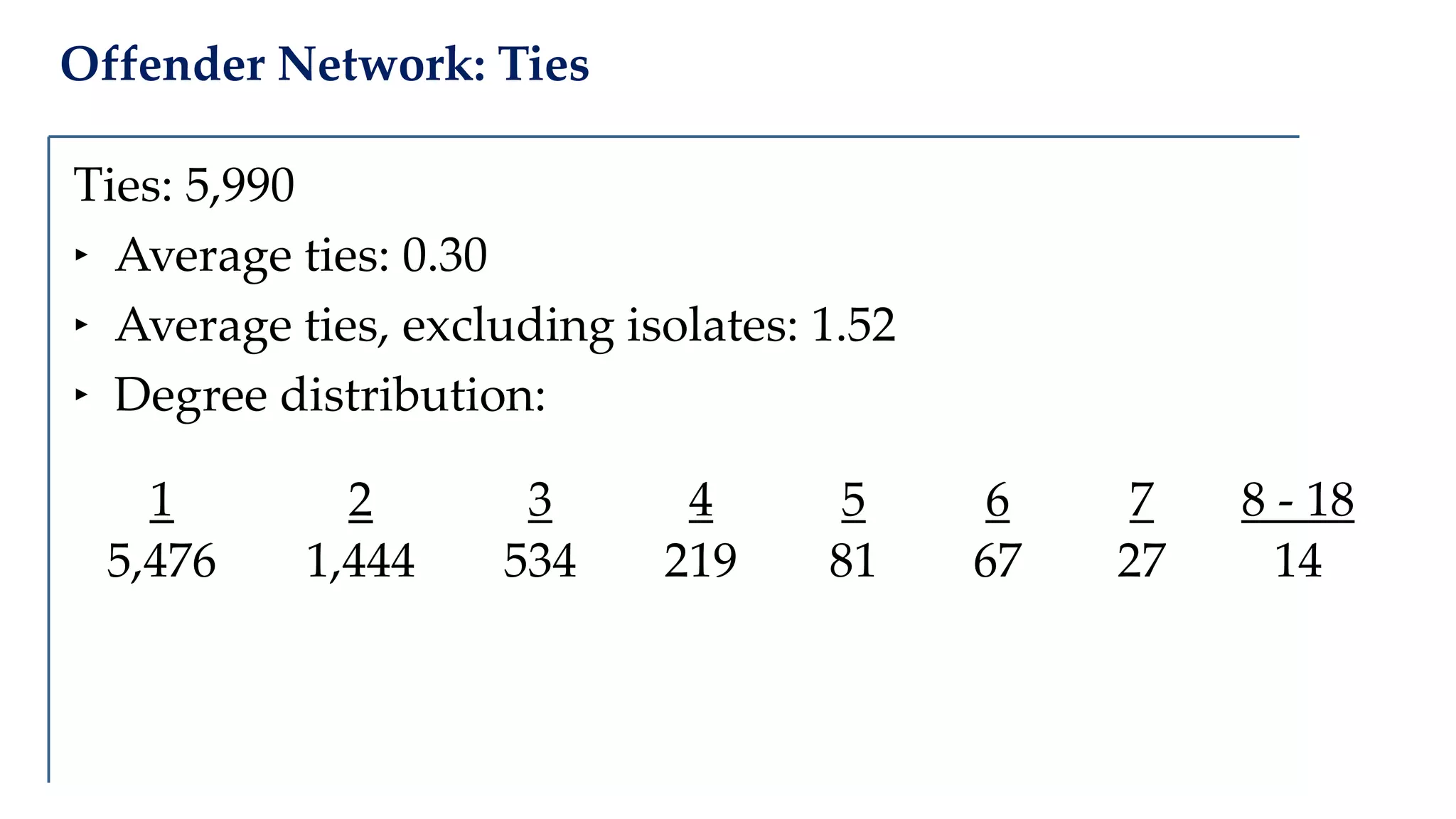
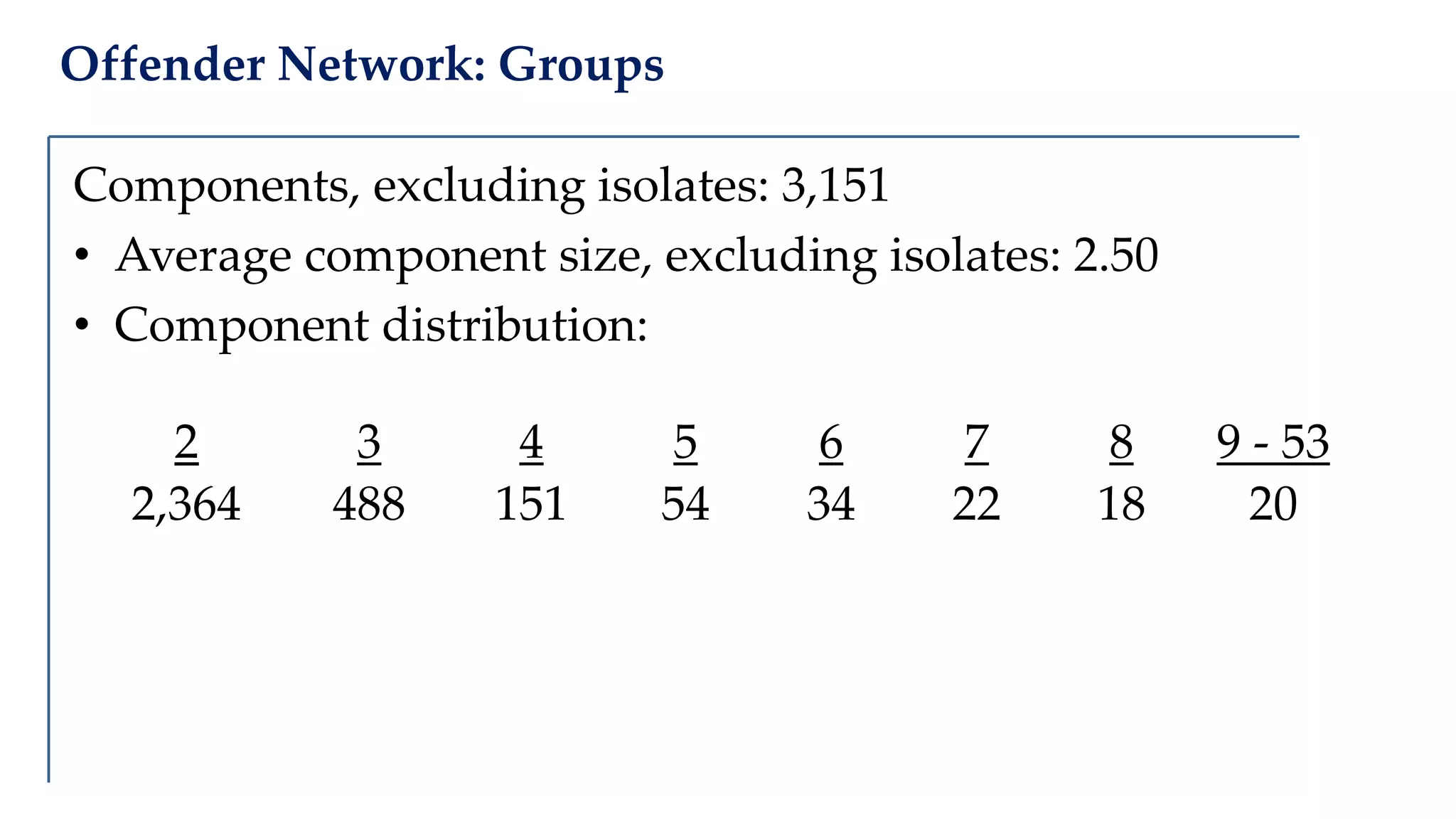
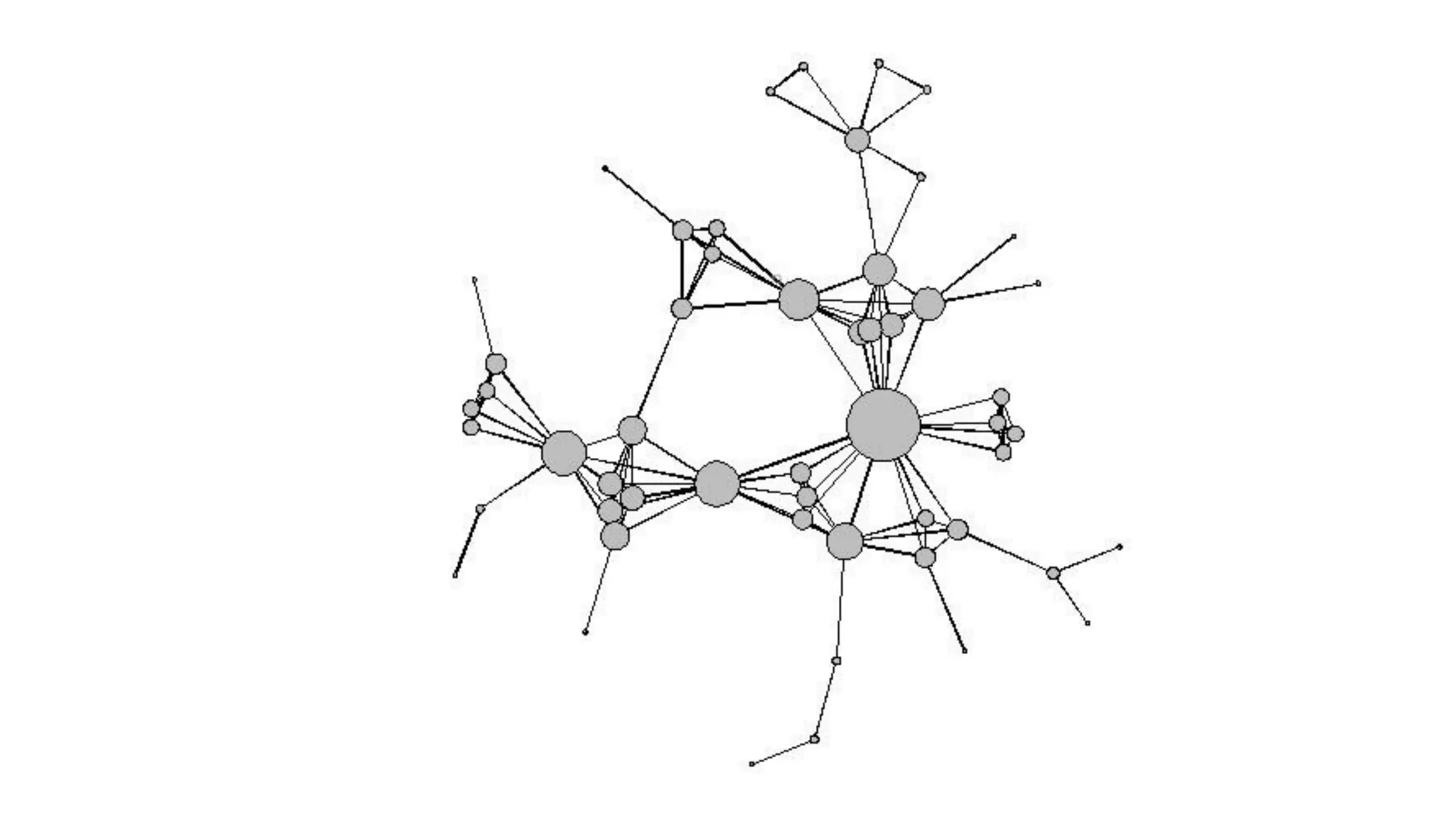
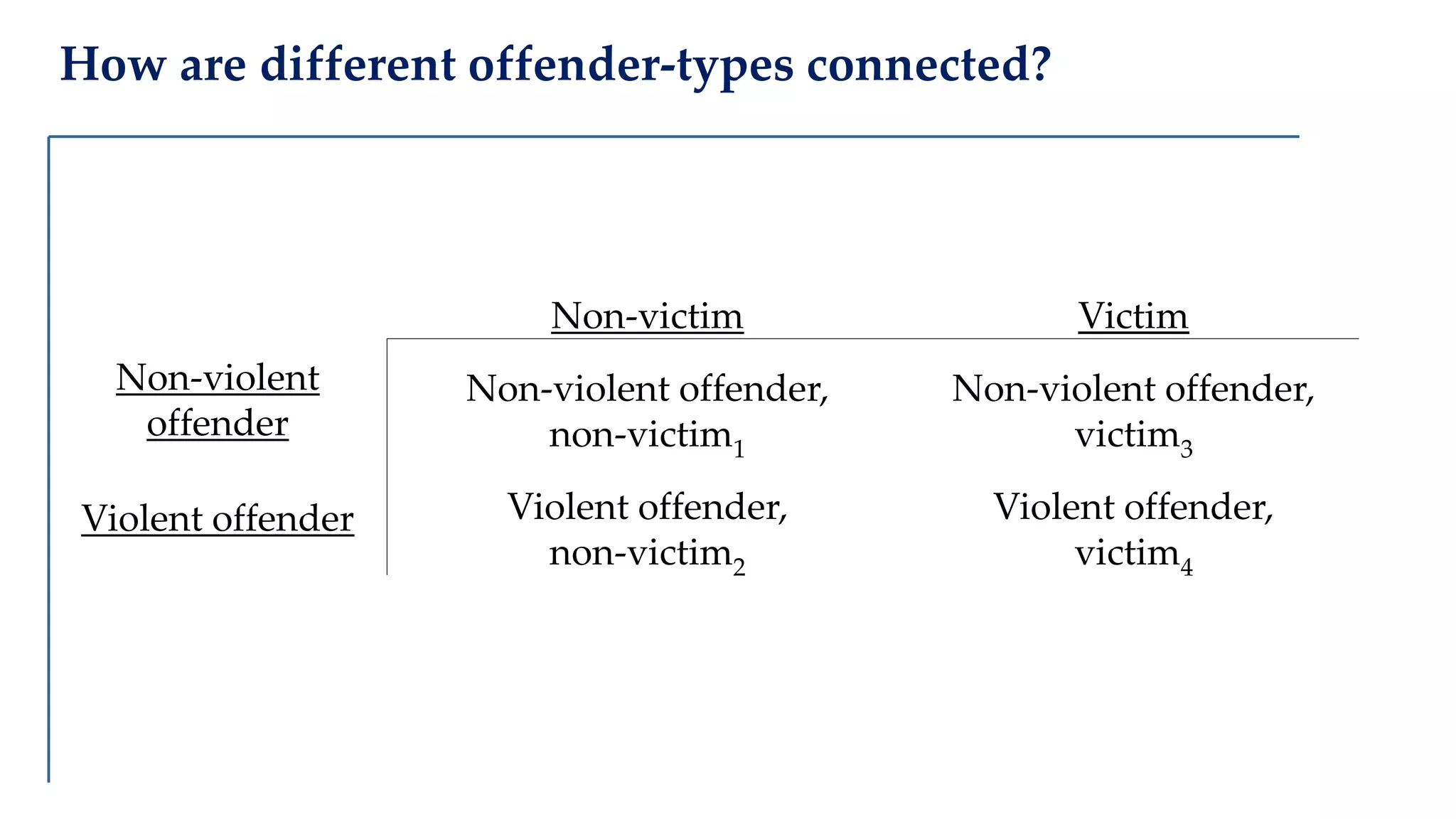
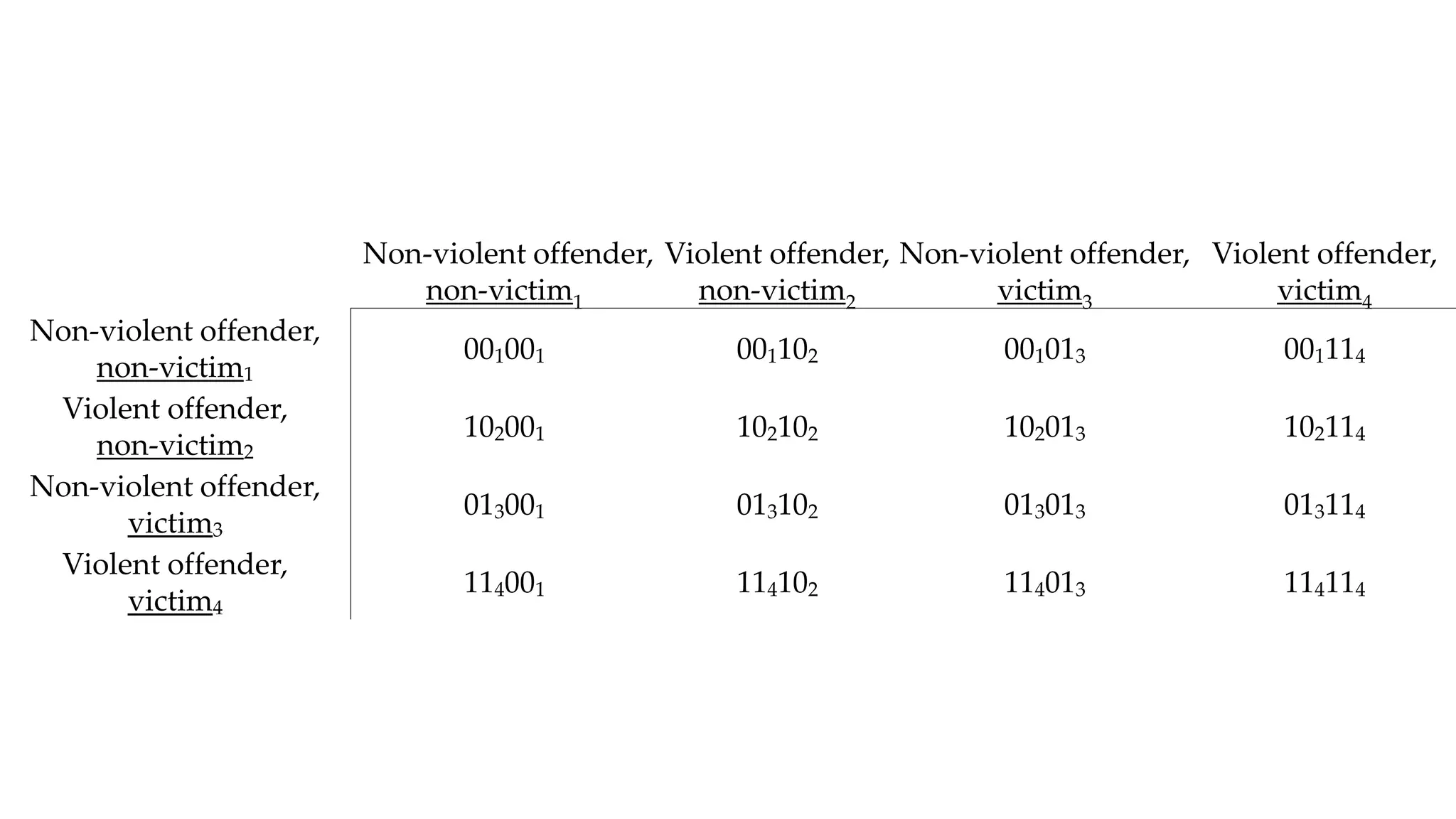
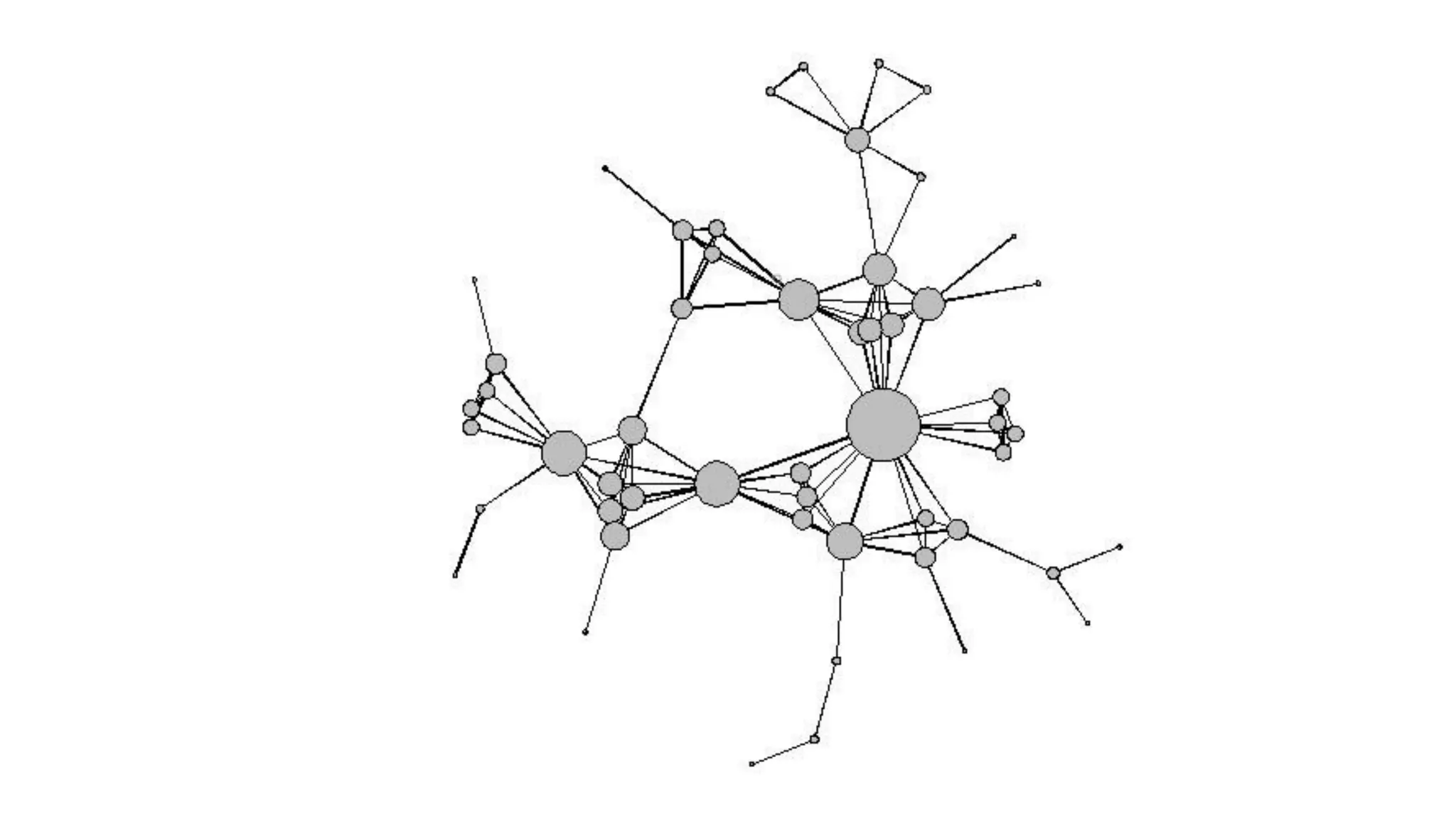
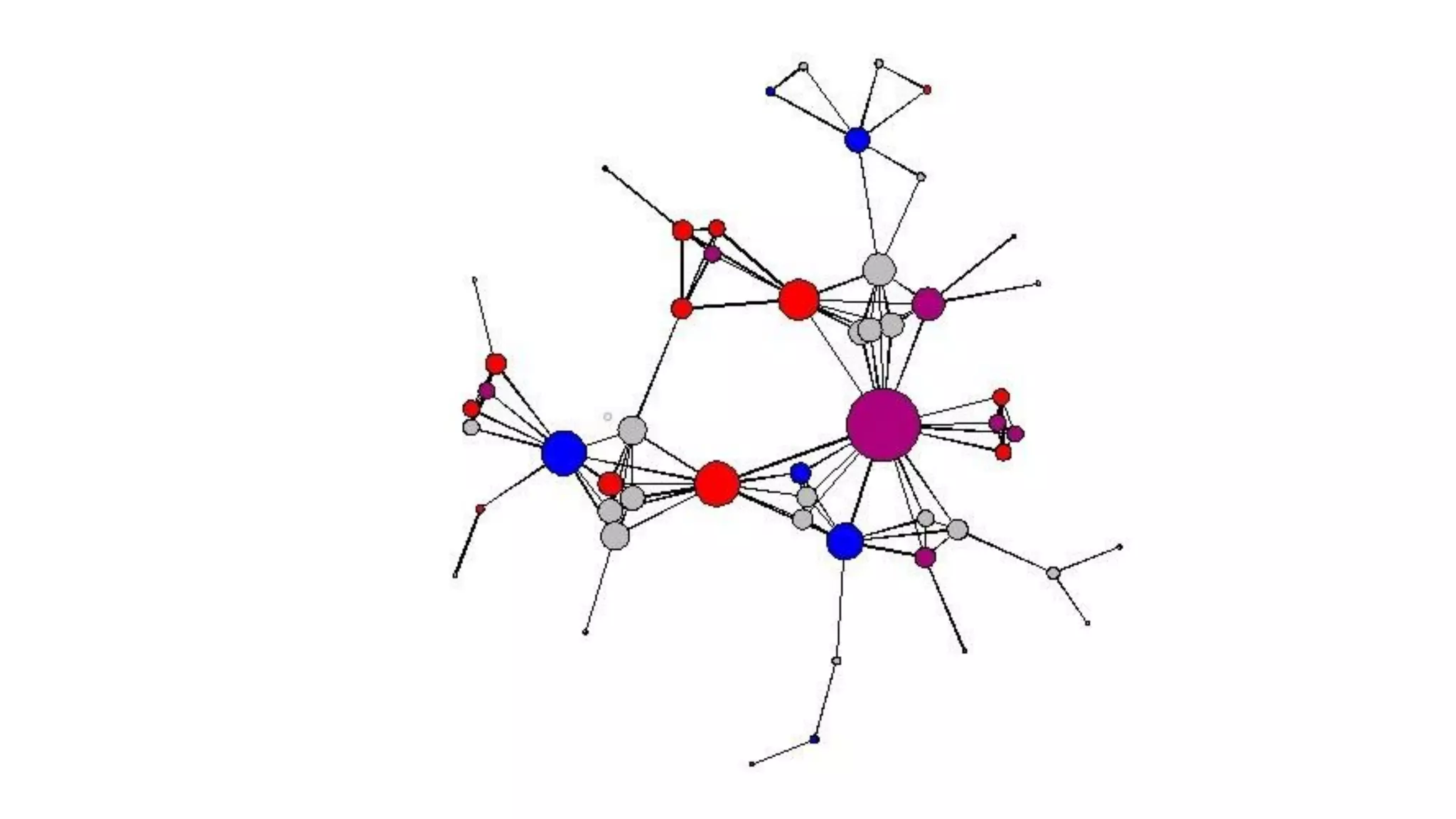
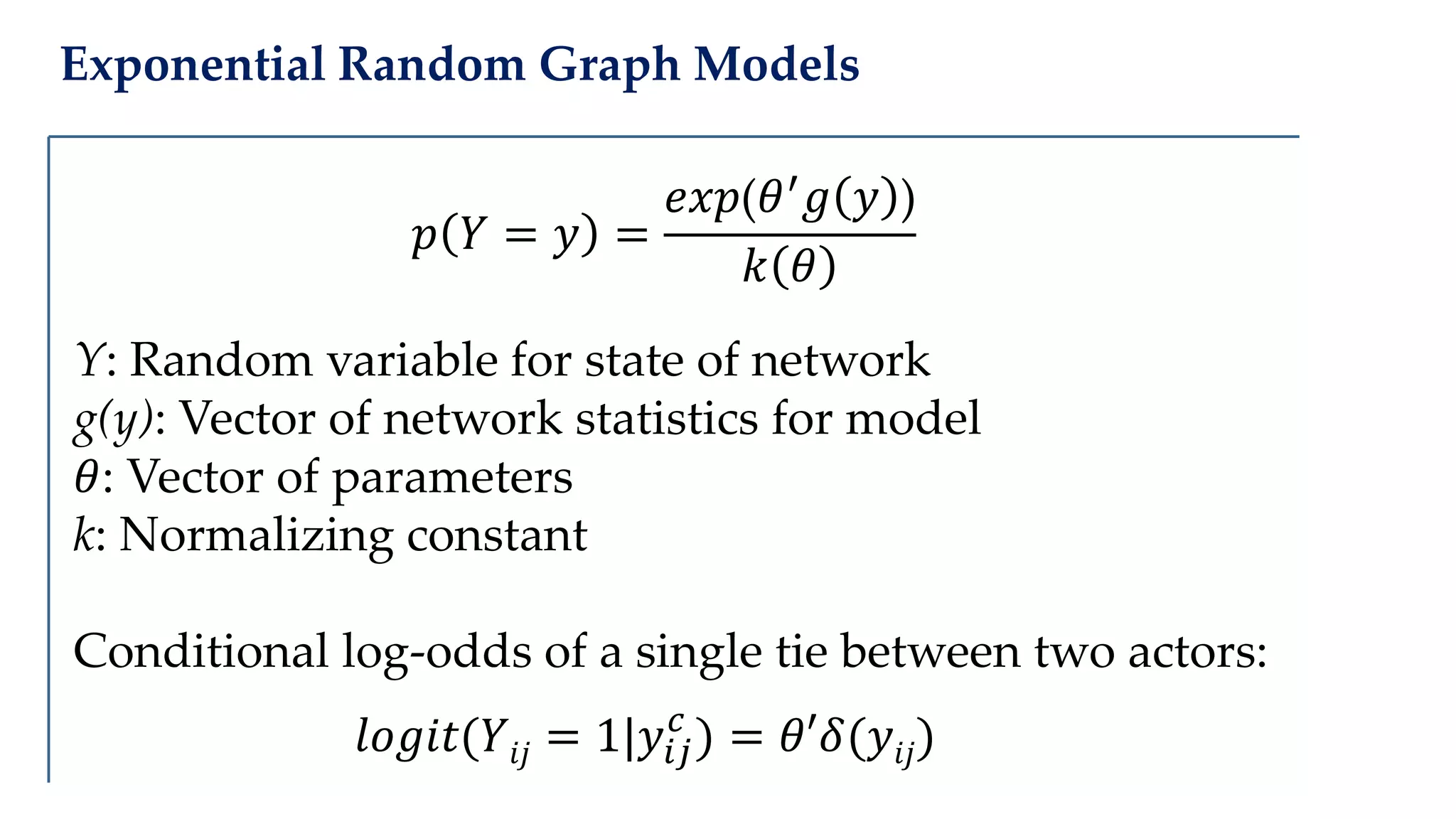
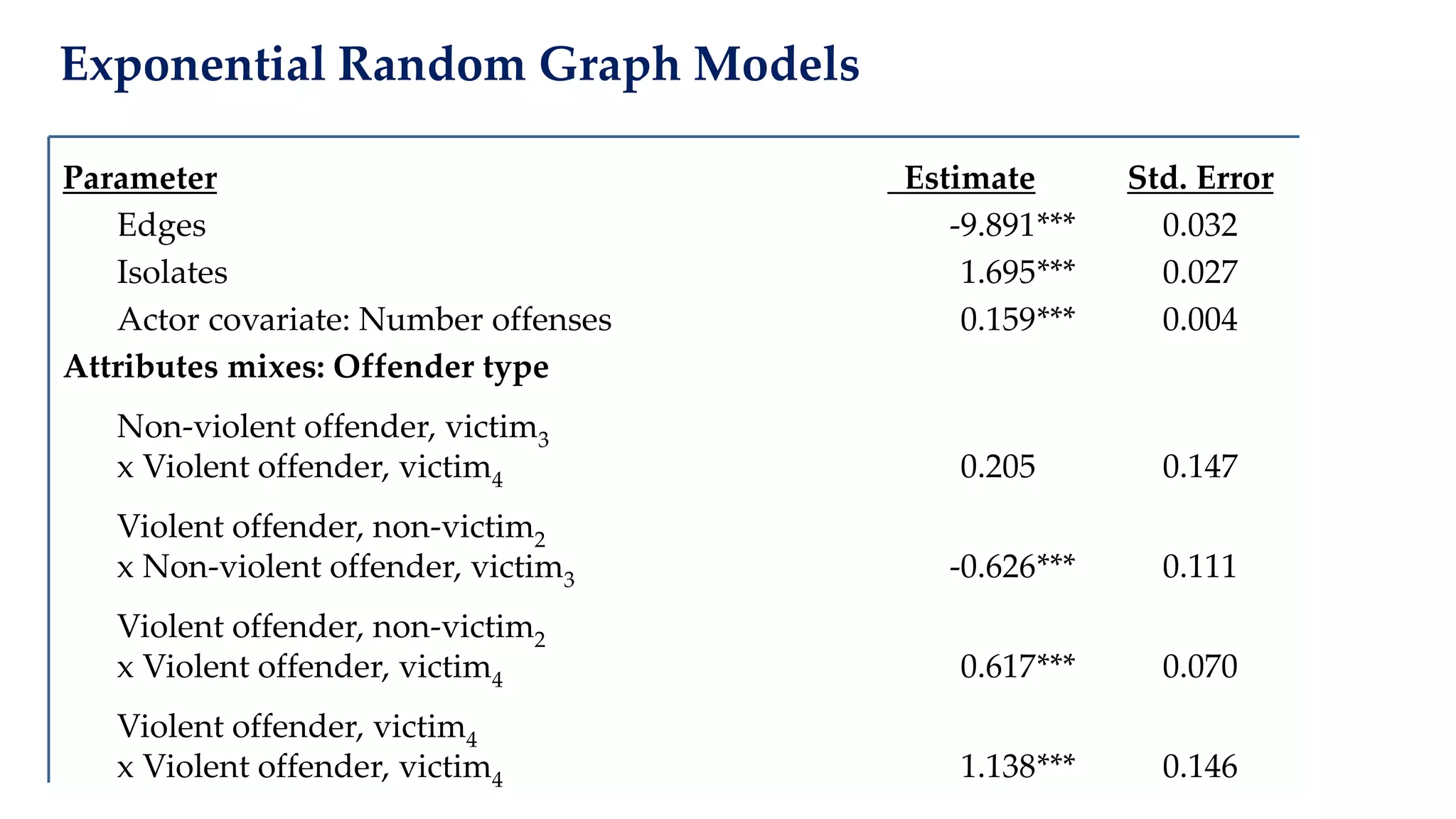
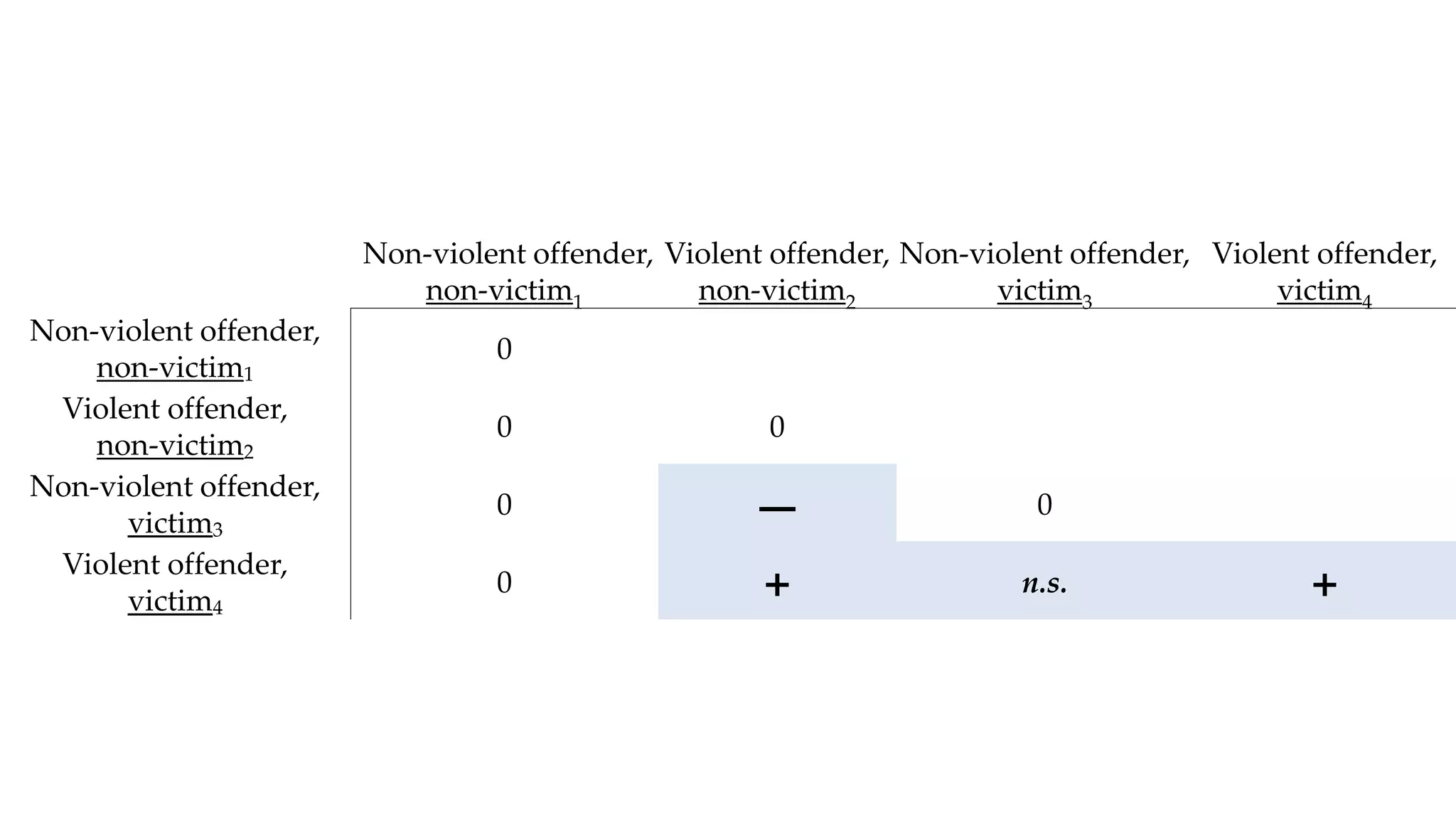
The document examines the relationship between criminal networks and violent victimization, focusing on Albuquerque, New Mexico, over three years of crime-related data. It explores how connections among offenders and the presence of victim ties inform the understanding of violence, highlighting the potential for identifying patterns and risks in criminal behavior. The findings suggest a sparse but significant presence of offender networks, indicating clustering of violence and raising questions about selection versus spread of violence within these networks.