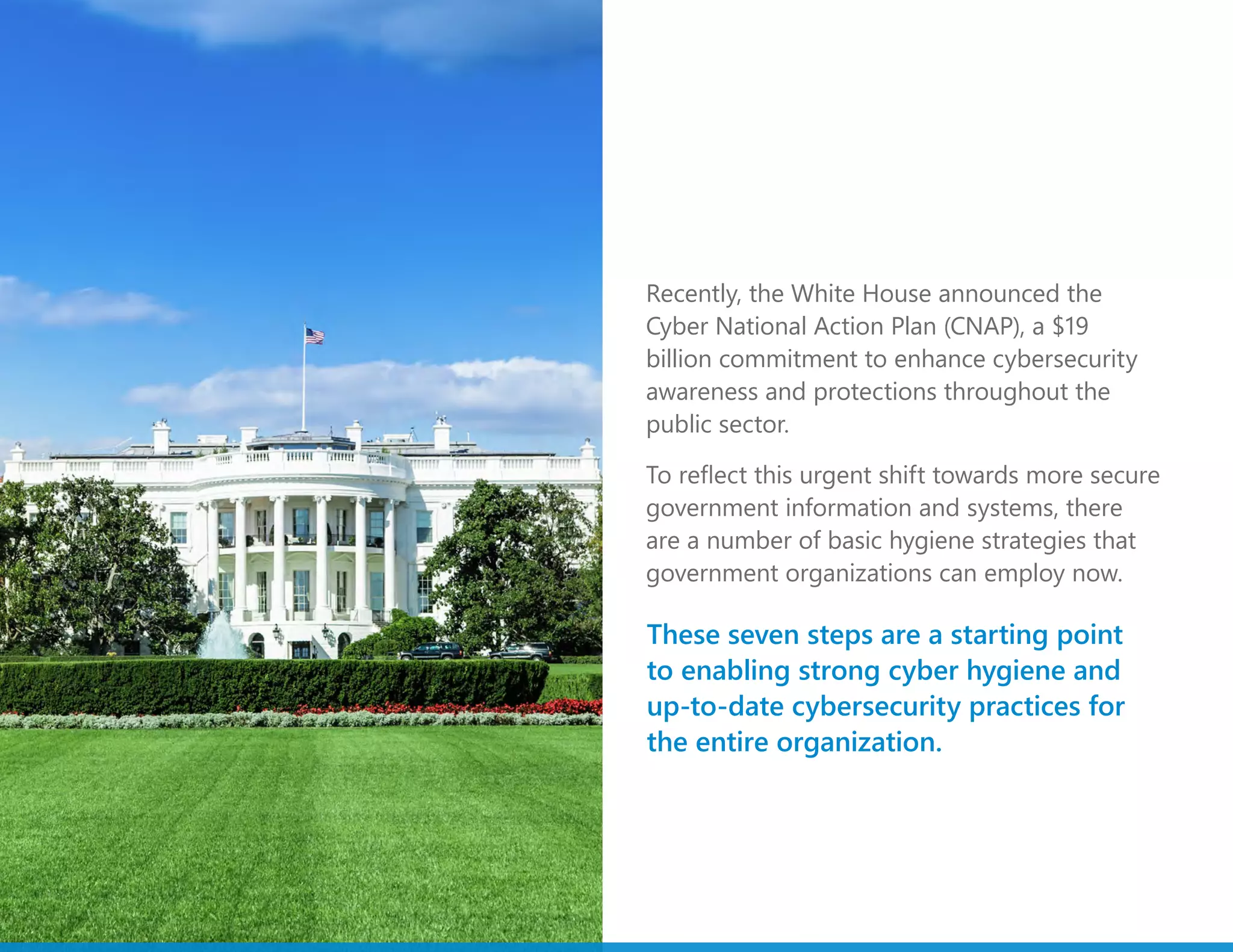
The document outlines seven essential cybersecurity hygiene steps for government organizations following the White House's Cyber National Action Plan, emphasizing the need for stronger identification methods, system patching, and employee education. It highlights the importance of data classification, encryption, and incident response simulations to protect sensitive information. Ultimately, these strategies form part of a broader commitment to enhancing cybersecurity across the public sector.