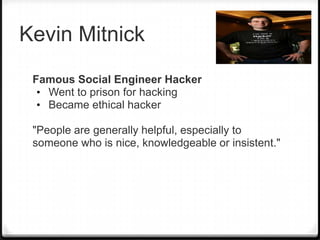
Social engineering is manipulating people into revealing confidential information through deception rather than technical hacking methods. It includes techniques like quid pro quo, phishing, baiting, pretexting, and diversion theft. Famous social engineer Kevin Mitnick emphasized that people inherently want to be helpful and trustworthy, making them vulnerable. Training and policies can help prevent social engineering by raising awareness of common tactics and restricting disclosure of private information. The human element remains the weakest link despite strong technical security defenses.