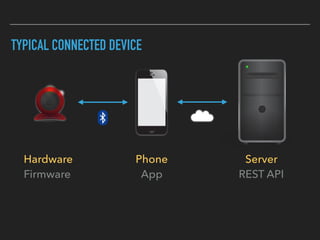
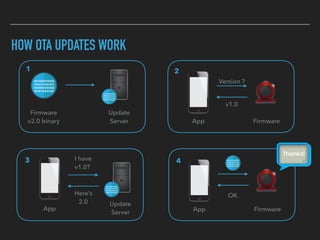
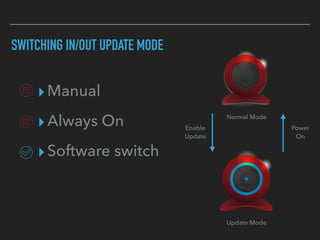
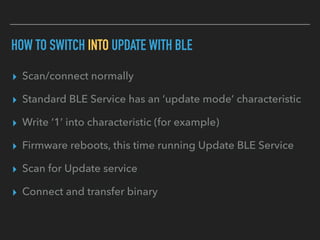
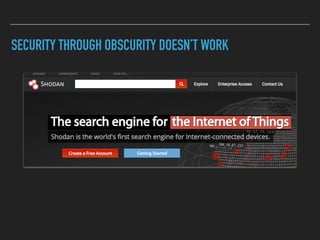
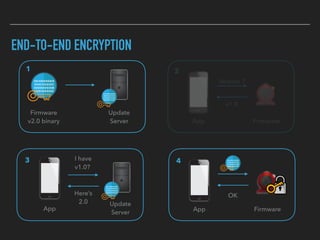
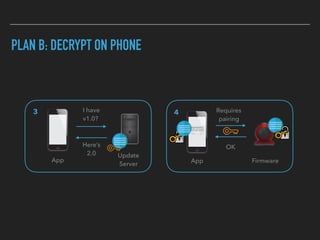
The document discusses the importance of over-the-air (OTA) firmware updates for embedded devices, detailing the process and requirements for successful implementation. It emphasizes the necessity for security, using encryption and proper device management to prevent issues during updates. The speaker also highlights best practices for firmware deployment and encourages proactive planning for firmware support to avoid pitfalls.