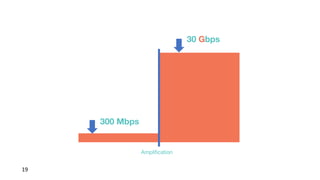
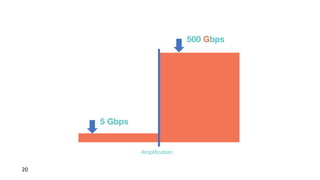
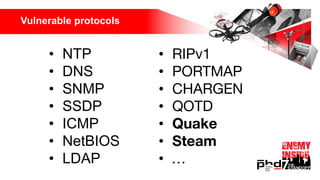
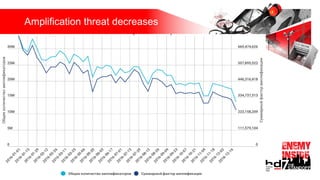
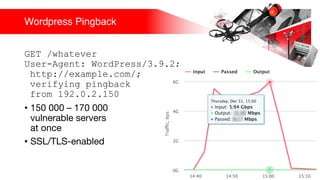
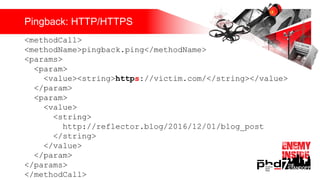
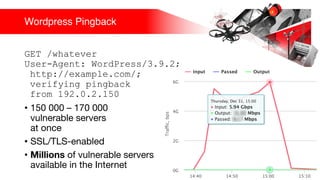
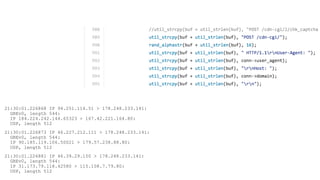
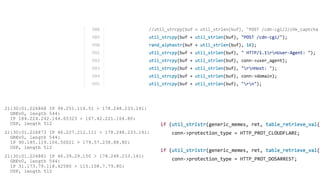
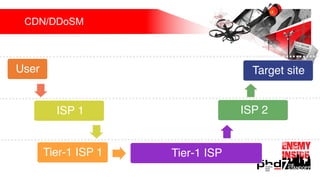
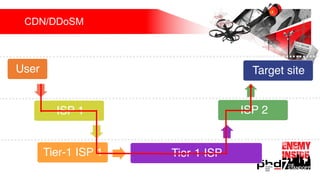
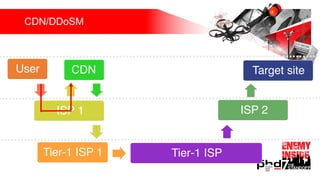
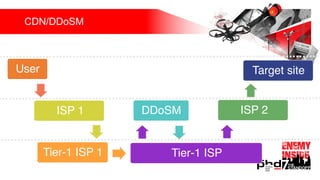
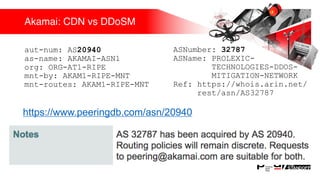
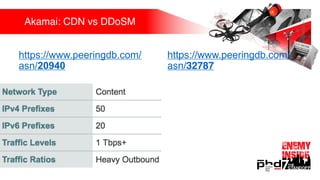
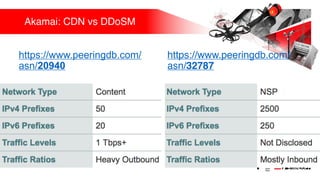
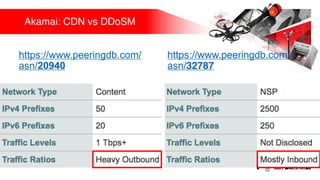
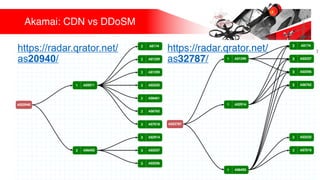
Презентация обсуждает DDoS-атаки и уязвимые протоколы, использованные в 2016-2017 годах, с примерами на основе Mirai и других ботнетов. Документ подчеркивает значимость IoT-устройств как мишени из-за их дешевого оборудования, отсутствия обновлений и стандартных логинов. Также рассматриваются стратегии противодействия DDoS-атакам и будущее изменений в архитектурах безопасности.