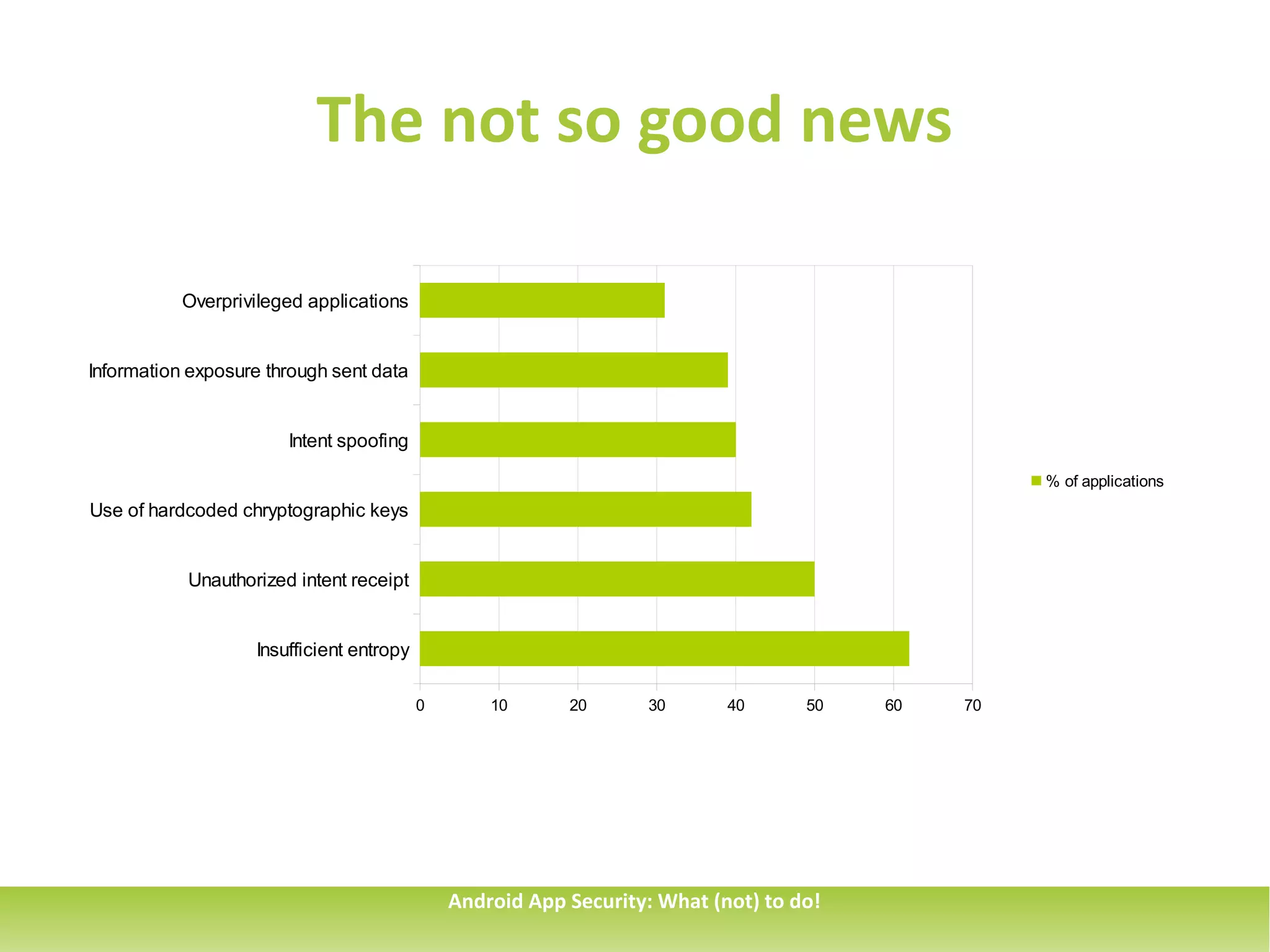
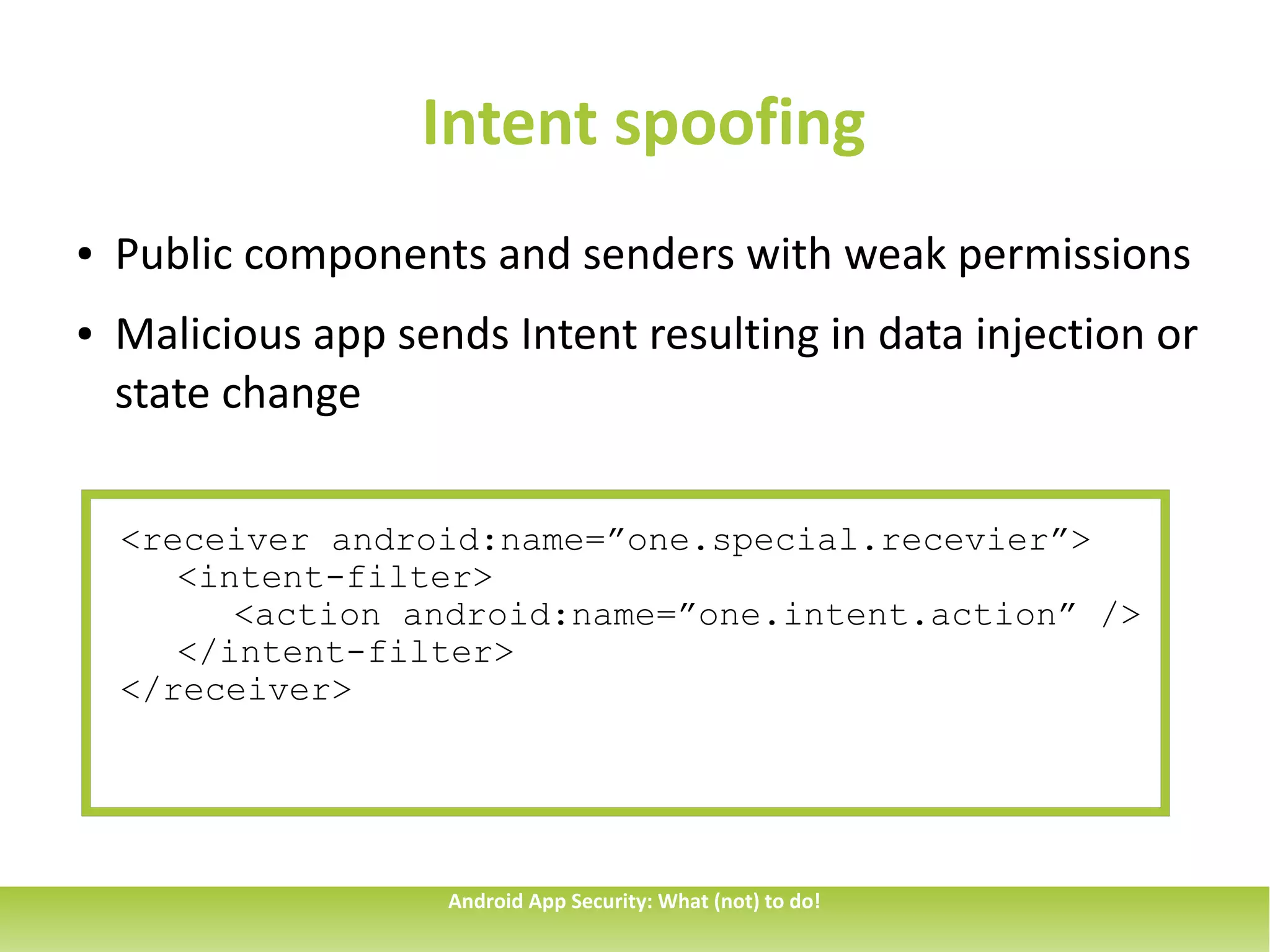
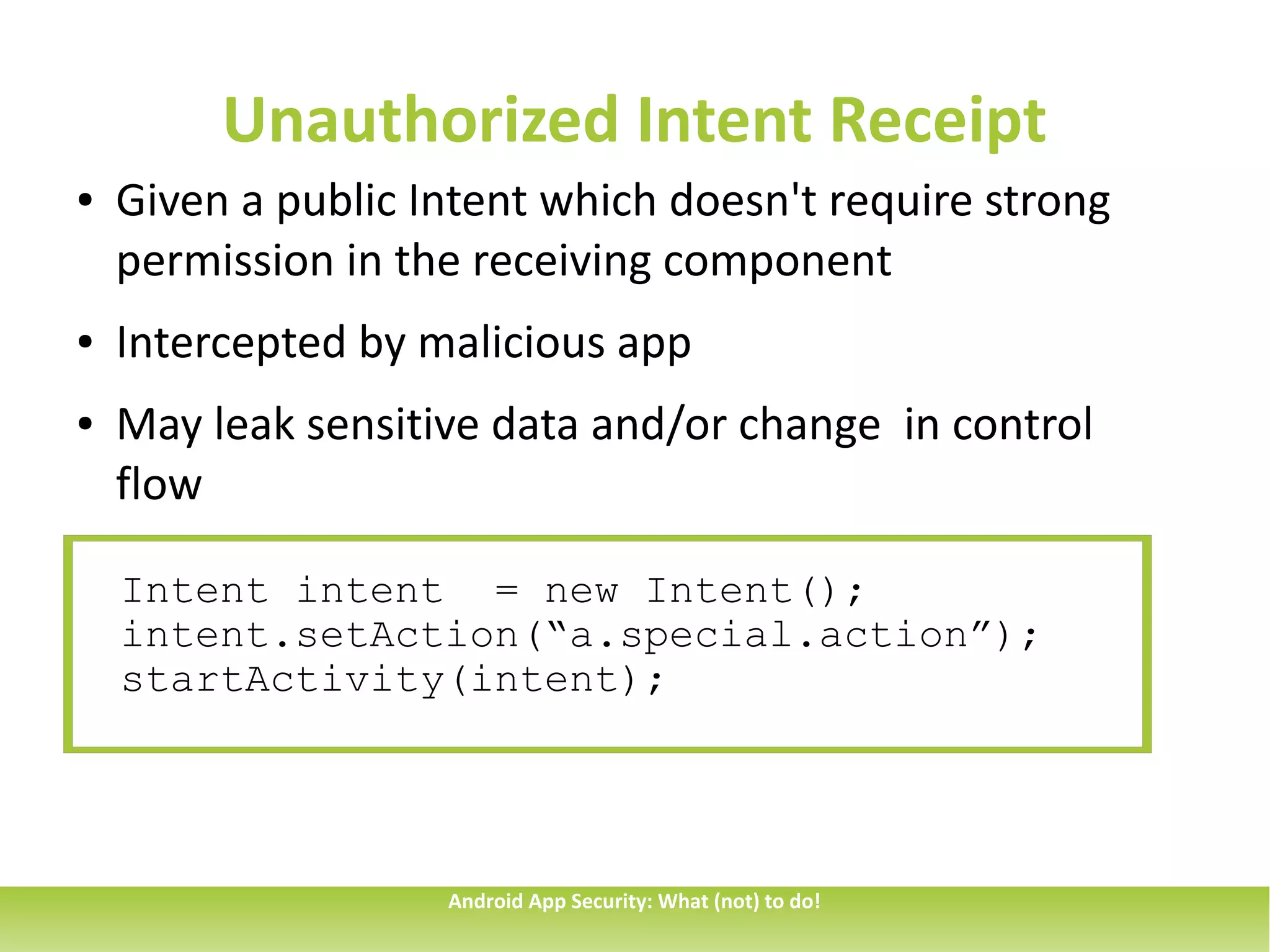
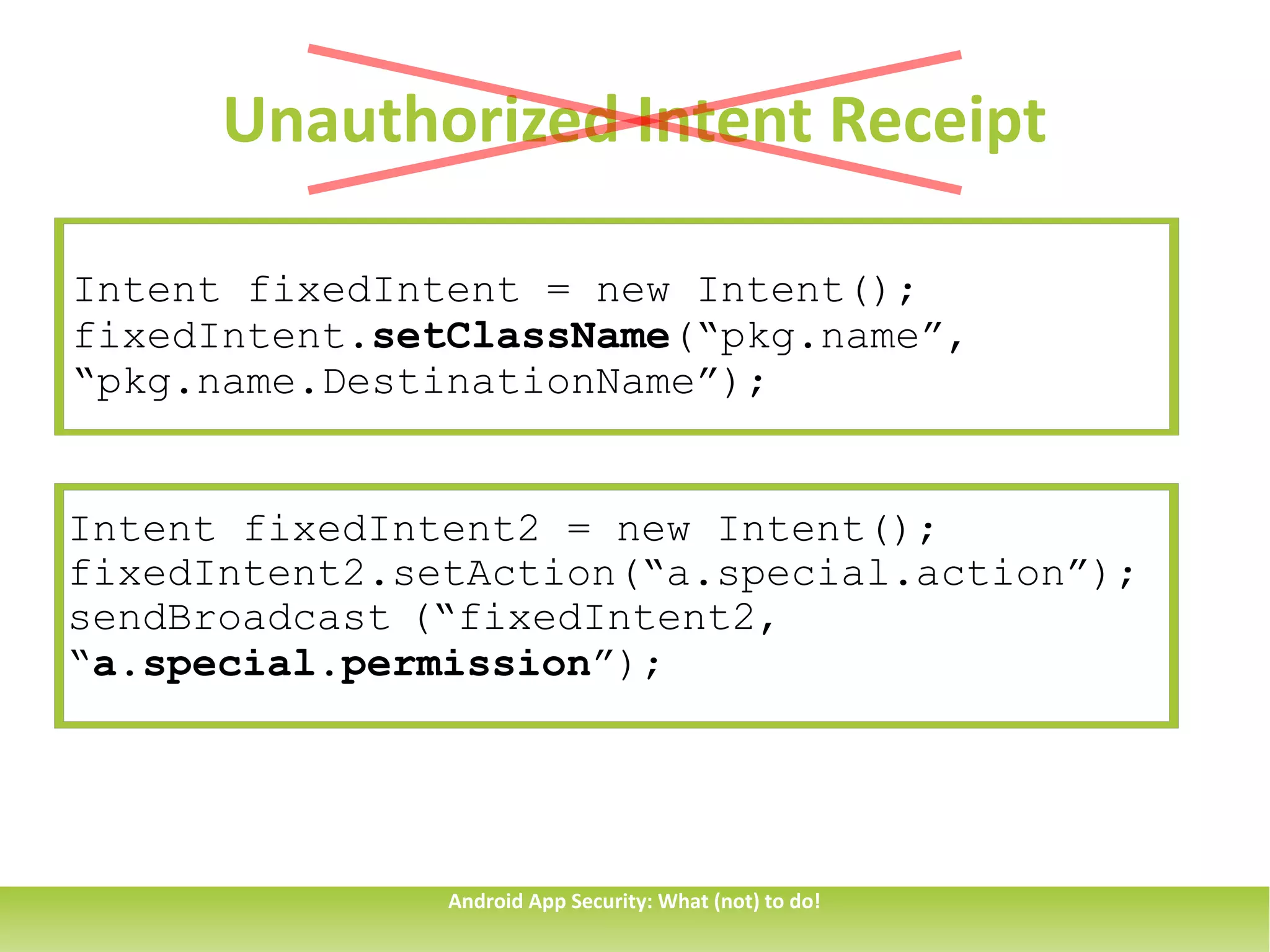
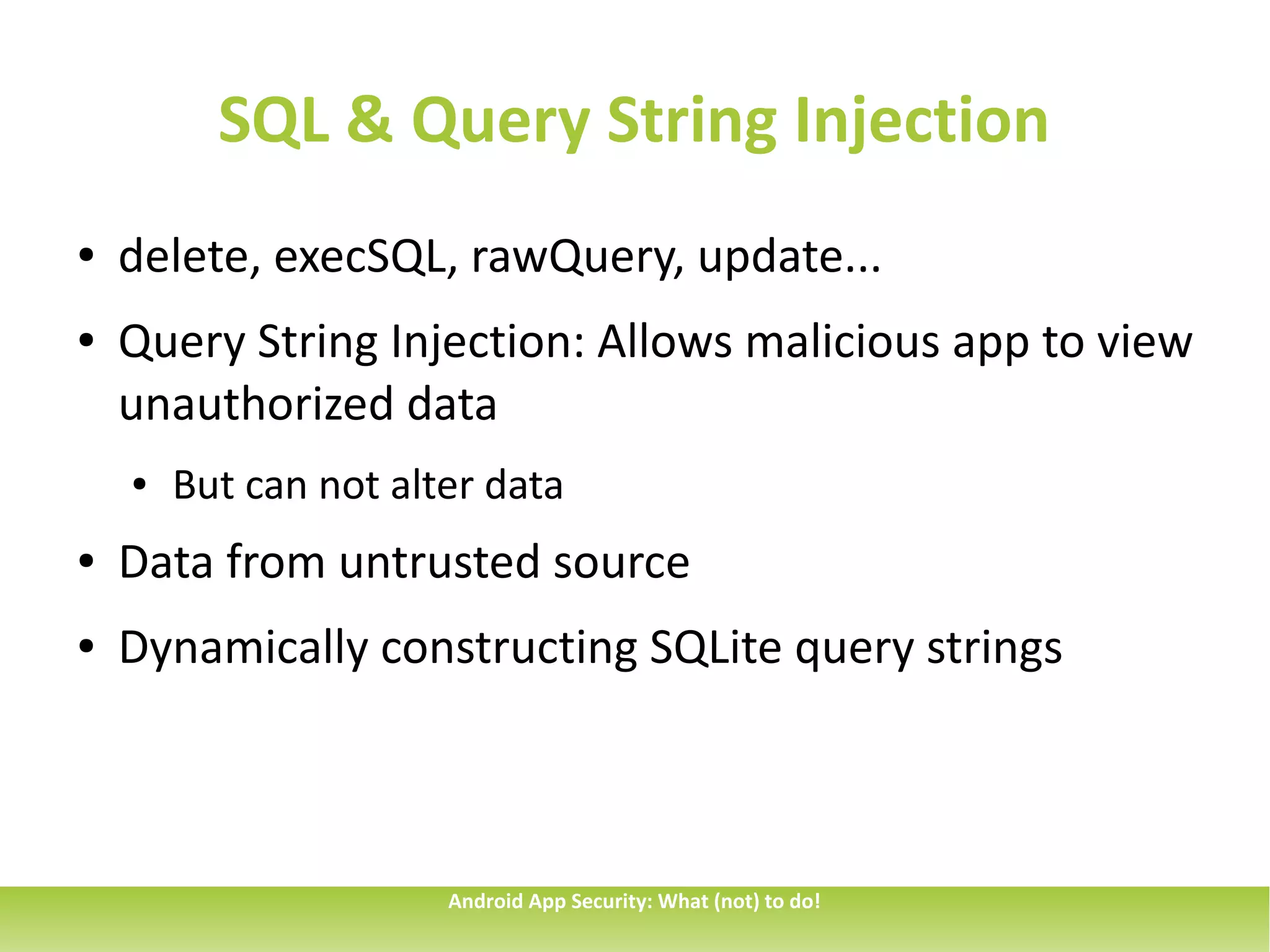
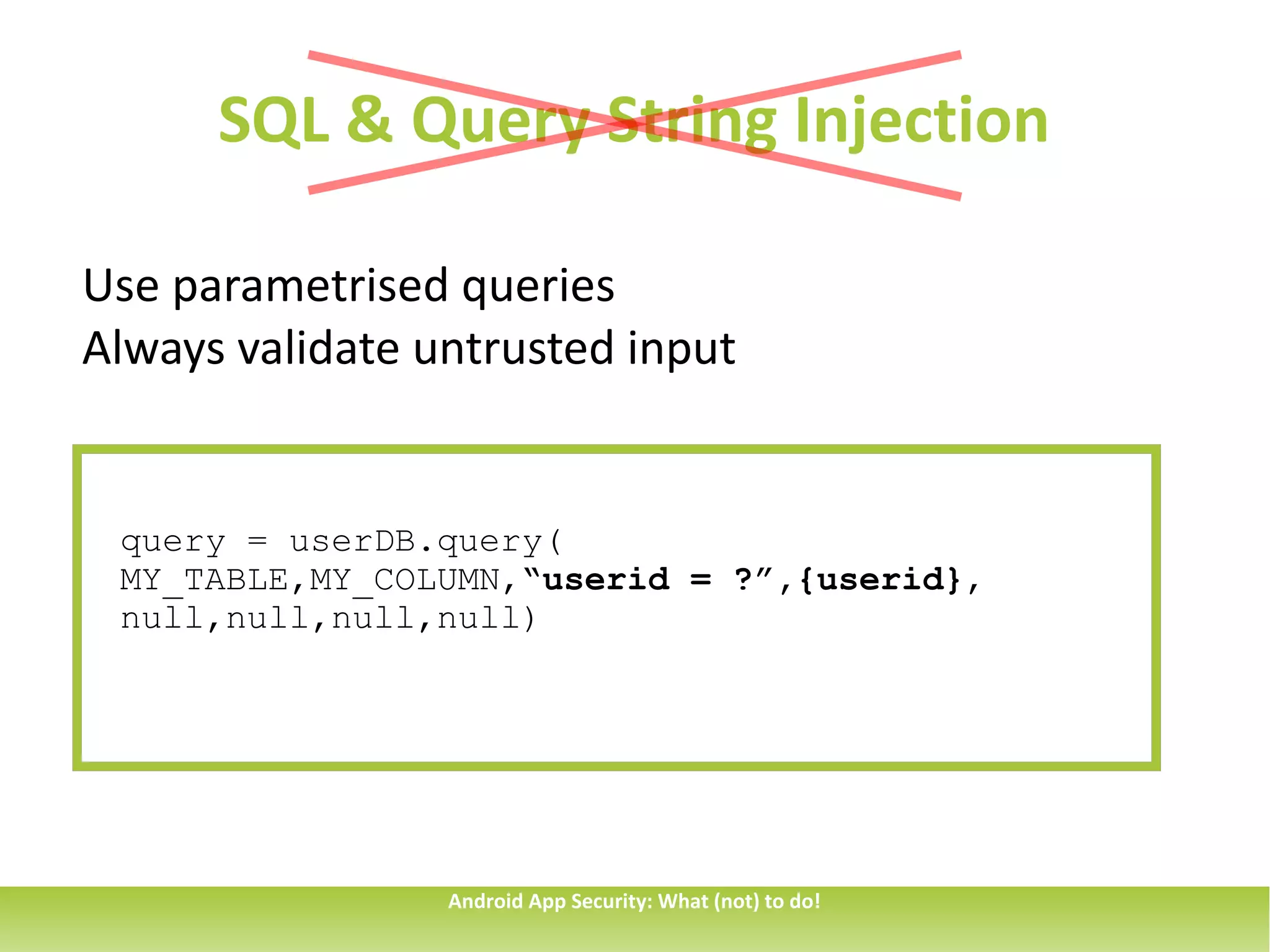
This document discusses common security issues for Android apps and provides recommendations to address them. It identifies issues such as overprivileged apps, information exposure through sent data, intent spoofing, unauthorized intent receipt, insufficient entropy, and use of hardcoded cryptographic keys. The document recommends techniques like using permissions and explicit intents to prevent spoofing, validating untrusted inputs, and parametrized queries to prevent SQL injection. It also cautions against sending sensitive data in sticky broadcasts.