Embed presentation
Download to read offline





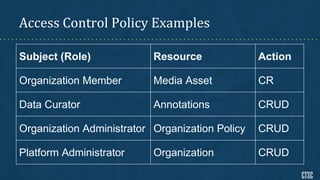







The document outlines the activities and resources provided by the NSF Cybersecurity Center of Excellence, focusing on tailored public resources, community engagements, and training. It includes examples of access control policies and guides for developing cybersecurity programs, along with acknowledgments to the National Science Foundation for their support. The opinions expressed do not necessarily reflect the official policies of the NSF.












