Man In The Middle - Hacking Illustrated
- 1. Man in The Middle Demystified Keatron Evans Senior Instructor
- 2. Still one of the most dangerous attacks. While most security professionals and administrators understand MiTM conceptually, few can actually execute it and prove to the laymen that it is a valid and real threat. In this presentation I’ll give a step by step complete with screenshots on exactly how it’s done.
- 4. This request is broadcast to everyone on the LAN and depends on the only response coming from the true holder of said IP address.
- 5. The protocol has no built-in functionality to tell if the response comes from the true source.
- 7. One server will authenticate to another via ftp.
- 8. We’ll use Backtrack and arpspoof them both.
- 9. The arpspoof makes each victim 1 believe I’m victim 2 and make victim 2 believe I’m victim 1.
- 10. Once we’ve got this in place, I’ll turn on ip forwarding on Backtrack which allows me to route the packets on to the intended recipient, while still allowing me to “see” the packets.
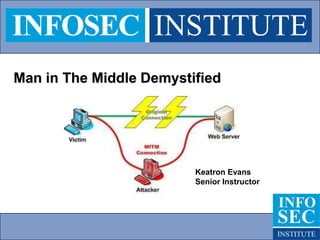
- 12. Communications after attack Desired traffic flow Victim 2 IP address 192.168.2.138 Victim 1 IP address 192.168.2.128 Man in The Middle IP address 192.168.2.135
- 13. Step 1 Let’s setup Backtrack properly first. There is chance that once you start it, you didn’t get an ip or your ethernet/or wireless interface wasn’t enabled. We’ll need to bring the interface up first. Then we’ll need to have it get an ip address via dhcp. So let’s do those things.
- 15. Eth0 interface is down so let’s bring it up;
- 16. After the up command we enter ifconfig again and see that eth0 is now up.
- 17. Now we need to tell it to get an ip address via a dhcp request. The command is /etc/init.d/networking restart
- 18. It gets an ip address from your dhcp server. Verify it with ifconfig again. We see we have an ip of 192.168.2.135.
- 19. Now we go to our first victim and see that its’ ip is 192.168.2.128.
- 20. Victim 2 has an ip address of 192.168.2.138.
- 21. Here’s the Filezilla ftp server running on victim 1.
- 22. Let’s verify that the two victims can communiate. I’m issuing a continuos ping from victim 2 (.138) to victim 1 (.128). We’ll let this ping run continously because we’re going to interrupt it with our arpsoof and verify our spoof is working.
- 23. Now we go back to our Backtrack and open three terminal shells (you’ll need all three). First arpspoof victim 2 to victim 1. In other words, make victim 1 think you’re victim 2. Now in the second terminal, do the exact opposite. See below.
- 24. Once you hit enter on both terminal windows, you’ll see that it’s telling victim 1 that .138 is at the Backtrack mac address, while also telling victim 2 that .128 is at the Backtrack mac address.
- 25. We verifty that the spoof is working by seeing if the pings we started earlier on victim 2 are now failing. See below.
- 26. We have now successfully diverted both victims traffic to our Backtrack. Now we need to enable ip forwarding so we can now route this traffic to it’s intended destination.
- 27. Once we’ve enabled ip forwarding, go back and check your pinging victim 2 and see that the pings are now successful again. Congrats! You’re now man in the middling. But we need to grab credentials. So we’ll need another tool for that.
- 28. To grab authentication credentials, we’ll start up dsniff. See below.
- 29. Now go to victim 2 and stop your pings. Then ftp to the ftp server running on victim 1.
- 30. Next login with whatever credentials you’ve set up on it.
- 31. Once you’ve successfully logged in you should see whatever files you have in your ftp store.
- 32. Here’s the important part. Dsniff needs to see the entire session to get the credentials. Entire session includes the disconnection or logging off. So you have to end the session before the credentials are actually grabbed. Close your ftp session, then go back to your Backtrack terminal and see the login information. Feeling l33t yet?
- 33. Closing Lessons. It is a classic mistake for the laymen and sometimes even security professionals to think that the answer is always the use of strong passwords. In the case of a man in the middles attack a strong 20 character complex password with numbers, letters, and special characters, is obtained just as easily and quickly as a 5 character letters only password. Join us in one of our Ethical Hacking classes where I or another of our world class instructors will teach you how to perform man in the middle against encrypted protocols such as SSL. Thanks for watching! Keatron Evans THIS PRESENTATION ALSO AVAILABLE ON Resources.InfosecInstitute.com
