This document discusses the vulnerabilities of an older model smart TV from Samsung, highlighting a denial of service (DoS) attack related to its Samsung Wireless Link (SWL) feature. It emphasizes the importance of extending the lifecycle of such devices to prevent planned obsolescence and recommends vendor support for addressing these security issues. The paper also details the processes of connecting devices via WPS (Wi-Fi Protected Setup) and the security implications involved.

![Table of Contents
1. Motivation.................................................................................................3
2. SWL [Samsung Wireless Link].................................................................3
2.1. Wireless Spores...................................................................................4
2.2. Air Dress Code....................................................................................7
2.2.1. Windows WPS to WPA/2.............................................................9
2.2.2. Linux WPS to WPA/2.................................................................12
2.3. Host offerings to Guests....................................................................15
3. D o S Attack............................................................................................16
3.1. (pixied) Bully....................................................................................18
3.1.1. Videometer..................................................................................19
3.1.2. PostMortem.................................................................................20
3.2. (bits) Reaver......................................................................................23
3.2.1. Time Thief...................................................................................24
4. Conclusions.............................................................................................26
5. References...............................................................................................29
2](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-2-320.jpg)
![1. Motivation
On a typical standard day of my life, I was watching my Smart TV when suddenly
rebooted without any previous notice. At this moment, my thoughts were about has not
enough hardware resources like RAM, CPU or other related errors, because perhaps the
TV was very old and electronic components started to degrade. I had the SWL (Samsung
Wireless Link) [1] by mistake activated because I were doing some “pen-tests” and
inventory tasks.
Figure 1: SWL (Samsung Wireless Link) option on Menu Settings
I felt some concern so decided to do research about the vulnerabilities this Smart TV
has. Found one affecting to the SWL component when is activated, generating a Wi-Fi
Access Point [2] [3]. Normally, when someone found a vulnerability and shares
publicly, an identification number is created to identify properly. In this case, there is no
CVE ID assigned but, there is a VulDB (strange/odd because VulDB cooperates with
Mitre and the corresponding CNA). The security researchers [2] [3] said using the
reaver tool [4] (an WPS auditor toolkit) was able to break the WPA2 password in a few
seconds (default pin was all zeroes according to the researcher’s tests). TV uses WPS
mechanism to establish the connection with the client using the PBC (Push Button
Configuration) [5] method.
Decided to try replicate to see if the TV gained the “enough intelligent” to be protected
against these bad situations. We will talk later about the problem we found.
2. SWL [Samsung Wireless Link]
Is the given name for the HotSpot/AccessPoint functionality of the TV to let devices
share content through this “hotline”. Smart TV offers it too when there is no
infrastructure mode (meaning TV is not connected to a network) so devices cannot be
added to the same network or, TV is in contact with a network through Ethernet but Wi-
Fi devices don’t want establish a connection through an AP that not belongs to the TV
infrastructure for several reasons.
3](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-3-320.jpg)
![This function seems reside in OFF mode with the help of last firmwares updates in
order to not to disturb with their powerful/strong signal [6] and to protect your network
against unwanted intruders [3]. Of course, we are always curious about the way it is
build and decide to check it out, you can turn it ON through the remote control easily
following the steps below:
Menu - Network - SWL(Samsung Wireless Link) - SWL(Samsung Wireless Link) –
Activate
Note: I operated with these commands under Spanish TV language. Some word action
may differ.
2.1. Wireless Spores
When you want to connect to a wireless network, what is the first thing you looking for,
their SSID name or the emitting power? Probable has more sense figure out on the
power of their emission because we don’t know about their name, it doesn’t show on
any place of the process but has a name, and this Wi-Fi is not hidden. It shows as:
SEC_LinkShare_XXXXXX
Where “X” represents the last 6 digits of the MAC of the… Wi-Fi interface? No, about
the Ethernet interface.
If using a nowadays Windows 10, you will be aware about the PBC (Push Button
Configuration) function because it supports WPS.
4](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-4-320.jpg)


![Figure 5: Probe Response comparison: rest mode (left) and pairable PBC mode (right)
Continuing with Probe Responses comparison;
The incremental on size is still 17 bytes (364-347) and it adds same 3 more packets
added in Tag: vendor Specific: Microsoft Corp.: WPS but not after the last tag, in that
case is between Wifi Protected Setup State: Configured (0x02) and Response Type: AP
(0x03)
If the goal of client is only needed to know the rest of WPS modes, it doesn’t need to
interact in case of AP is ready to pair (only wait to capture for a Beacon Frame is more
than enough) or wait until get a Probe Response that does not belong to client whose is
interested in.
2.2. Air Dress Code
There are places like: special events, restaurants, etc. that demands some requirements
for their access. One type of term used for this is the dress code and consist of bring a
proper wearing to attend. In the case to connect to the AP, need some similar
requirement like the case of the dress code type. For example, for an Android in order to
have the minimum requirements, need to be a compatible version because WPS was
deprecated in Android 9 [7] or you can use other compatible devices having Windows
10 as OS for example to get luck in the connection.
For start the connection, the first steps to implement are through the TV, need enable
the compatible WPS AP to allow clients to connect;
- Step 1: Enable SWL. The status by default, is OFF (can be seen at chapter 1.) need to
follow the steps at the end of the chapter 2 to put it ON. The result is shown in next
figure.
7](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-7-320.jpg)





![Figure 12: Kali Linux; showing the detailed version
We prefer inserting the corresponding version just in case these commands differ if
another edition (Kali distribution) is used (old or newer).
Two processes are mandatory and executed in separate command line windows,
wpa_supplicant and wpa_cli will be our toolchain. But first, need to stop any process
that can be conflicting with the help of airmon-ng (also used to put an interface into
monitor mode).
Figure 13: Kali Linux: Killing Wi-Fi processes
A configuration file must be created before starting, this is like a “cue file” for
wpa_supplicant with the minimum setup.
Figure 14: Kali Linux; Creating the .conf file for wpa_supplicant
Following the good standards (or best practices) the .conf file name is called
wpa_supplicant.conf and saved in a recommended path [8]. With the help of echo
command, the file can be created “on the fly” and 2 lines are needed:
ctrl_interface; Tell to use wpa_supplicant mechanism
13](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-13-320.jpg)
![update_config; Allows to save the key WPA2 passphrase in the wpa_supplicant.conf
file.
Last line commands are for invoke/initialize the wpa_supplicant with a pair of
parameters.
-i; Choosing the interface which wpa_supplicant is going to move from.
-c; Choose and location of the .conf file.
Is all ready to use the second tool in a separate window, the wpa_cli [9]
Figure 15: Kali Linux; Complete steps to the connection of a WPS-PBC network
14](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-14-320.jpg)
![As the WPS Wi-Fi network is PBC type, indicating the first command observed in the
above figure, it’s the only necessary. Joined to the wireless without an IP? OK…
Staying under the TV Wi-Fi umbrella is one thing, other thing is the way how to obtain
this configuration with the help of other tools, wpa_cli tool will not do for you but don’t
worry, the dhclient comes by default and you will retrieve an IP fastly from the DHCP
server of the TV! After that, a check can be carried out with a simple ifconfig issuing.
All command steps are optional except for the first one of the wpa_cli. If result was OK,
password can be retrieved showing the content of the wpa_supplicant.conf. Cat tool
reveals the psk line.
2.3. Host offerings to Guests
Generally, when you are invited by a friend or other person in their home, is common
(in many situations) that they offer you something to drink or eat as a gesture of thanks.
What TV AP is offering? Let’s look at the network parameters!
Figure 16: Windows 10; ipconfig/all showing the network Wi-Fi interface parameters
It delivers a DHCP service that provision with the IP 10.123.12.128 (if you are the first
device which requested for a connection). Is a /24 class C IP range. Gateway and
DHCP server are the TV IP which hangs the services in same container but… the DNS
server is different, why? It has an explanation. According to the article mentioned
before in chapter 1 & 2 [3], TV can act as a router. To convert it, the Ethernet interface
must be connected to another router so, DNS is the same as the router connected. A
small test can be done to figure this out (pinging to google is more than enough to check
internet connectivity).
15](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-15-320.jpg)
![Figure 17: Smart TV architecture acting as router
Situating in above figure, P1 is a device under the TV network and P2 is under the
home router user network. P1 can contact directly with P2 but not in reversal way (P2
cannot go to P1 “by default”). TV is between the 2 networks and has enough
information to route packets to the Ethernet part doing a NAT (it means, P2 can see the
IP 192.168.1.X Ethernet TV interface). Unless a route exists in the router (who has
192.168.1.1 IP), P2 will not be able to reach P1.
3. D o S Attack
It can be said that the attack appears suddenly magically by tools designed to test the
vulnerabilities of WPS. The objective of them is looking to get WPA key by brute
forcing the first & second stage of PIN code (a total of 8 digit). An offline brute force of
the pin is possible with the discover of Dominique Bongard [10], another tool was born
called pixiewps (“pixie-dust attack”) [11]. Due to their efficiency, was implemented
under modified version of Reaver [4] and also implemented in Bully [12].
We are going to use both (Bully and Reaver respectively) to do a comparison of the
performance and the time it taken. Is important to mention that first intention of this was
test the security against Smart TV, WPA2 password is not possible to be retrieve under
any of these tools because instead of this, it gets rebooted again and again!
Let’s check the model and versions of the TV and computer used for these DoS attacks.
TV:
- Model Code: UE40D7000
- Software/Firmware Version: T-GAPDEUC-1033.2
16](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-16-320.jpg)
![Figure 18: Smart TV: Model and Software version under Contact section
These parameters can be retrieved in the TV’s Menu. This is the last firmware known.
Computer/Laptop:
A Kali Linux ISO 2020.4 running in Live mode, same that exposed in figure 12 of the
chapter 2.2.2.
How to figure it out there is a vulnerable Smart TV before starting the attack? Put the
WiFi interface into monitor mode first...
Figure 19: Kali Linux; Airmon-ng tool: Putting interface into monitor mode
Then, wash tool will tell you how (part of the tool Reaver [4] pack).
Figure 20: Kali Linux; Wash tool to scan for WPS AP’s
SSID is the key parameter to be aware around you, we use grep to do a clean filter in
search of what is necessary and essential. Putting WPS as part of the filter, the word is
marked in red on column to use as a guide.
17](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-17-320.jpg)
![The rest of the show (Proof of Concept) continues with the inspection and use of the
tools.
3.1. (pixied) Bully
This tool doesn't seem to be as famous as the other, reaver but has their own look and
feel showing a bulldog as a logo in Kali Linux tools [13].
This is a targeted attack so in order to start fast, BSSID and channel must be known.
Figure 21: Kali Linux; Bully tool in action
The command bully is written in terminal with 3 parameters:
-b: BSSID (or MAC of the AP).
-c: The channel where Access Point is working.
-v: Verbosity, will show you more info if the level established is set to maximum (in
that case, 4 is the maximum).
wlan0mon: The interface after “be converted” into monitor mode.
Last lines show a column indicating “timeouts” means TV doesn’t answer in proper
time. Before start the first Rx(Beacon)... line, TV was rebooted. Why not measure these
times, right?
18](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-18-320.jpg)


![Figure 23: Interaction Diagram between laptop & TV under Bully attack
The general difference in comparison with figure 9 is that at the beginning of the
petitions, there is no beacon frame reflected nor the probe pair. This is because client,
Bully, doesn’t seem need any beacon frame to start the attack because it knows the
BSSID and channel (acquired from many ways, in that case through wash tool).
However, according to what can be seen in the tool's log, it makes sure to receive a
beacon before starting the attack.
The DoS attack produces when EAPOL packets thrown. After the request identities, TV
has the “poison inside” and it's a matter of time before it falls. Under this period, more
packets are sending (showed in red). Is like a boxer when is on the ground and the
countdown starts. The WSC_NACK tries to get configuration from AP. Under this state
[14] the rest of packets enter into a sequence and/or a loop, 6 packets in total, they are:
Deauthentication, Authentication x2, Association Request-Response and EAPOL –
Start.
As we had the .cap we have the ability to do more things and decided to take a
graphic/diagram using this function into Wireshark [15]. On a traffic packet inspection,
is highly recommended filter for what needed, however, graphics can say things not
seeing easily by text only mode.
21](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-21-320.jpg)


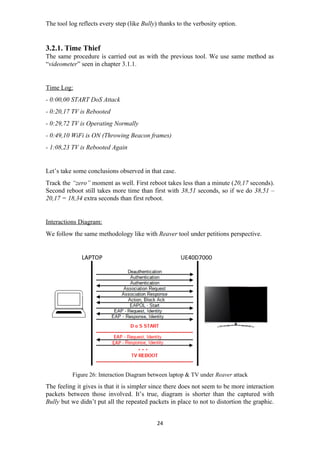
![Later in the Wireshark I/O Graph, we can see a bit deeper in packet context vs time
taken.
The start sequence of requests-responses is equal than Bully but, a new packet is
introduced and different (not seen in Figure 23). This is an action packet that has as a
mission block the acknowledges, what it means and what role does it play here? Block
Ack is intended to be more efficiency avoiding so many ack packets and instead, be put
all of them in one frame [16]. This must be negotiated between two parties, here exist a
request but not a respond/answer from laptop so the mechanism didn’t initiate.
Into the DoS phase, there is only a pair of EAP request-response reflected but here are
ellipses, meaning the pair is repeating into a loop until TV is rebooted. The mechanism
is simpler, short but intense.
It’s the Wireshark I/O Graph turn!
Figure 27: Wireshark: I/O Graph of Reaver attack until first TV reboot
The description is the same as seen in figure 24. In order to do a fair comparison. The
size of the graph is the same, as well as the number of packets per half second.
Here the max packets are 301 and total time is no more than 21 seconds.
The legend is almost the same but plus Action (Block Ack) packets;
- Purple line: Action – Block Ack packets. The filter applied is;
wlan.fc.type_subtype == 0x000d && wlan.addr == f0:d5:bf:xx:xx:xx
We can see differences in how the software’s manage the packets through the time.
Note: In order to present same type of data in each software case, the SWL function of
the TV was reset (turn OFF – turn ON) and TV turned OFF and ON to stay sure there
were not something in memory, buffer,…
25](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-25-320.jpg)


![different color indicates the color of the previous action. When the time is in the
opposite column (having two times) means the additional more time respect the
previous category (actual time less previous category).
The things that can be seen in overall view of the diagram are the total time for both,
ends at similar time, differs from 5,81 seconds making Reaver a few slow than Bully.
The almost same difference it produces at the beginning, in first reboot, time differs
from 5,82. In all cases Reaver takes more time in each action respect Bully but respect
their own previous action, Reaver takes less time in orange and green categories.
One important lesson to learn here is you should not activate functions which behavior
is unknown or/and not used. Unless it is to carry out research of this kind, as a user of a
product not manufactured by yourself, it is better to use those parts of which you have
knowledge. Does it mean the fault is yours? Oh, of course not… This is just a way to
mitigate issues that are not easily resolved by third parties. We understand these devices
have a useful life, but what if life gives them a break like a human being who can reach
his hundred years and more? Would you leave your relative banished at a predetermined
age even though his health is good? We believe that the answer here is more than
implicit right? If this is clear enough, why not apply same for devices? We know there
is no comparison, but it deserves some kind of fix to cure that annoyance.
We tried get the password remotely but with the pair of tools mentioned had no luck, so
at less, nobody can retrieve your WPA2 “non-changeable” password (don’t forget WPS
born insecure, Stefan Viehböck make it publicly [17]) but, you need take into account
that... if you have the Ethernet interface connected to your home router (according to the
chapter 2.3) your home router’s network is accessible from Smart TV network (if you
trying to isolate, using the TV AP isn’t good idea!).
Back to the DoS attack, we demonstrate the effectiveness recreating it by taking it to a
possible cybercrime scenario into a multimedia format (video of chapter 3.1.2). A
mother and her son are watching cartoons and suddenly TV is malfunctioning. The
mother may think there is a failure on television. TV is old and official manufacturer's
technical support will no longer take over so mother, most probably, takes the decision
to buy other (perhaps changing brand and manufacturer, losing their trust). She doesn't
know that the failure was caused by a cybercriminal…
In all tests, we were aware for the channel changing, sometimes can be 1, others is
number 11, this doesn't happen on all TV reboots but casuistry can happen (the video
only reflects against same channel without stay ready for TV’s AP channel change). Are
the tools the ability to switch from one channel to other in case it happens? Yesss! Your
tool is Bully and the command will look like this;
bully -b E4:E0:C5:XX:XX:XX -c 1,11 -v 4 wlan0mon
The solution for citizens is easy, disable the SWL TV’s functionality but we think
manufacturer should do their part, handle these internal errors correctly, be resistant to a
DoS WPS PIN attacks. It surely would increase their reputation and can also serve as a
28](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-28-320.jpg)
![good marketing strategy against your competitors. It should be an honor for them the
product can still be standing, a sign that they do things very well.
Remember…
Be Good, Be Hackers.
5. References
[1] E-MANUAL - 01_ENG_GPDVBEUA-0106.pdf; Page. 93,111.
https://downloadcenter.samsung.com/content/UM/201201/20120128101809663/01_EN
G_GPDVBEUA-0106.pdf
[2] VDB-12842 | Samsung TV SSID Authentication improper authentication.
https://vuldb.com/?id.12842
[3] Samsung Wireless Link security hole | Jumping Spider.
https://jumpingspider.co.uk/rants-2/samsung-wireless-link-or-wtf-is-sec_linkshare
[4] GitHub - t6x/reaver-wps-fork-t6x. https://github.com/t6x/reaver-wps-fork-t6x
[5] Wi-Fi Protected Setup Specification; Page. 94 -11.3 PBC Technical Description-.
https://www.wi-fi.org/file/wi-fi-protected-setup-specification
[6] SEC_LinkShare SSID is from your Samsung TV: SWL (Samsung Wireless Link).
https://wiert.me/2011/07/04/sec_linkshare-ssid-is-from-your-samsung-tv-swl-samsung-
wireless-link
[7] Wi-Fi Easy Connect | Android Open Source Project.
https://source.android.com/devices/tech/connect/wifi-easy-connect
[8] Wpa_supplicant – ArchWiki. https://wiki.archlinux.org/title/wpa_supplicant
[9] Wpa_supplicant and Wi-Fi Protected Setup (WPS).
https://w1.fi/cgit/hostap/plain/wpa_supplicant/README-WPS
[10] Offline bruteforce attack on WiFi Protected Setup (slides).
http://archive.hack.lu/2014/Hacklu2014_offline_bruteforce_attack_on_wps.pdf
[11] GitHub - wiire-a/pixiewps: An offline Wi-Fi Protected Setup brute-force utility.
https://github.com/wiire-a/pixiewps
[12] GitHub - kimocoder/bully: Bully WPS Attack Tool.
https://github.com/kimocoder/bully
[13] Bully | Kali Linux Tools. https://www.kali.org/tools/bully
[14] Wi-Fi Protected Setup Specification; Page. 109 -Configuration Error-.
https://www.wi-fi.org/file/wi-fi-protected-setup-specification
[15] Wireshark. 8.8. The “I/O Graphs” Window.
https://www.wireshark.org/docs/wsug_html_chunked/ChStatIOGraphs.html
[16] CWAP - 802.11 : Block Ack | mrn-cciew. https://mrncciew.com/2014/11/01/cwap-
802-11-block-ack
29](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-29-320.jpg)
![[17] Brute forcing Wi-Fi Protected Setup.
https://sviehb.files.wordpress.com/2011/12/viehboeck_wps.pdf
30](https://image.slidesharecdn.com/smoldtv-oldandsmart-221017224044-3b795729/85/SMOLD-TV-Old-Smart-30-320.jpg)