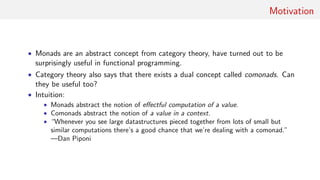
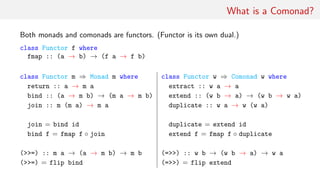
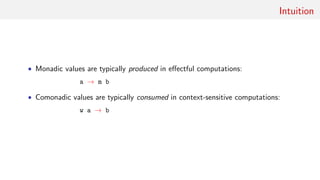
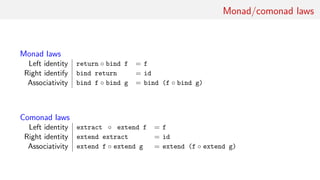
This document discusses comonads, a concept from category theory that serves as the dual of monads in functional programming. It outlines the definitions, laws, examples, and applications of comonads, including their use in data structures like streams and arrays, as well as in computational contexts such as cellular automata and image processing. The author emphasizes the potential usefulness of comonads in various programming paradigms and provides further reading resources.


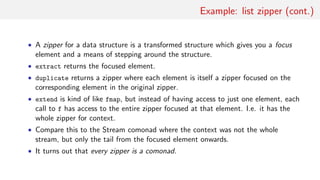
![Example: list zipper
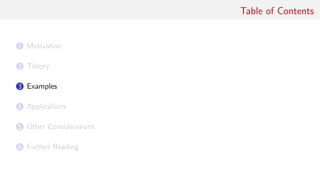
data Z a = Z [a] a [a]
left, right :: Z a → Z a
left (Z (l:ls) a rs) = Z ls l (a:rs)
right (Z ls a (r:rs)) = Z (a:ls) r rs
instance Functor Z where
fmap f (Z l a r) = Z (fmap f l) (f a) (fmap f r)
iterate1 :: (a → a) → a → [a]
iterate1 f = tail ◦ iterate f
instance Comonad Z where
extract (Z a ) = a
duplicate z = Z (iterate1 left z) z (iterate1 right z)
extend f z = Z (fmap f $ iterate1 left z) (f z)
(fmap f $ iterate1 right z)](https://image.slidesharecdn.com/comonad-140703194509-phpapp01/85/Comonads-in-Haskell-13-320.jpg)
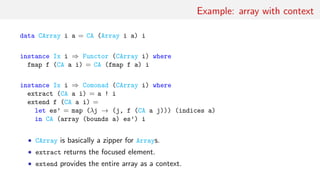
![Application: 1-D cellular automata – Wolfram’s rules
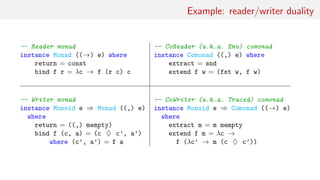
rule :: Word8 → Z Bool → Bool
rule w (Z (a: ) b (c: )) = testBit w (sb 2 a .|. sb 1 b .|. sb 0 c) where
sb n b = if b then bit n else 0
move :: Int → Z a → Z a
move i u = iterate (if i < 0 then left else right) u !! abs i
toList :: Int → Int → Z a → [a]
toList i j u = take (j - i) $ half $ move i u where
half (Z b c) = b : c
testRule :: Word8 → IO ()
testRule w = let u = Z (repeat False) True (repeat False)
in putStr $ unlines $ take 20 $
map (map (λx → if x then ’#’ else ’ ’) ◦ toList (-20) 20) $
iterate (=>> rule w) u](https://image.slidesharecdn.com/comonad-140703194509-phpapp01/85/Comonads-in-Haskell-17-320.jpg)
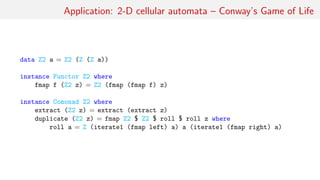
![Application: 2-D cellular automata – Conway’s Game of Life
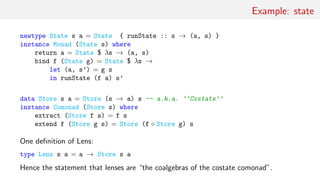
countNeighbours :: Z2 Bool → Int
countNeighbours (Z2 (Z
(Z (n0: ) n1 (n2: ): )
(Z (n3: ) (n4: ))
(Z (n5: ) n6 (n7: ): ))) =
length $ filter id [n0, n1, n2, n3, n4, n5, n6, n7]
life :: Z2 Bool → Bool
life z = (a && (n == 2 | | n == 3))
| | (not a && n == 3) where
a = extract z
n = countNeighbours z](https://image.slidesharecdn.com/comonad-140703194509-phpapp01/85/Comonads-in-Haskell-19-320.jpg)



![Cofree comonads
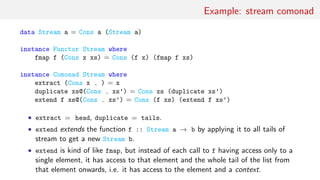
-- Free monad
data Free f a = Pure a | Free (f (Free f a))
instance Functor f ⇒ Monad (Free f) where
return = Pure
bind f (Pure a) = f a
bind f (Free r) = Free (fmap (bind f) r)
-- Cofree comonad
data Cofree f a = Cofree a (f (Cofree f a))
instance Functor f ⇒ Comonad (Cofree f) where
extract (Cofree a ) = a
extend f w@(Cofree r) = Cofree (f w) (fmap (extend f) r)
• Cofree Identity is an infinite stream.
• Cofree Maybe is a non-empty list.
• Cofree [] is a rose tree.](https://image.slidesharecdn.com/comonad-140703194509-phpapp01/85/Comonads-in-Haskell-26-320.jpg)