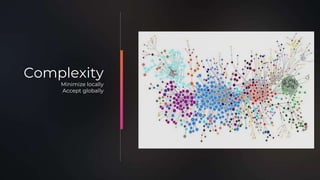
The document outlines an architecture for software autonomy, emphasizing principles such as domain-driven design, team ownership, and continuous delivery. It introduces bounded contexts with cross-functional teams to drive innovation, streamline integration, and ensure data integrity within cloud infrastructure. Additionally, it discusses decision-making frameworks to balance autonomy and oversight in technology choices among teams.