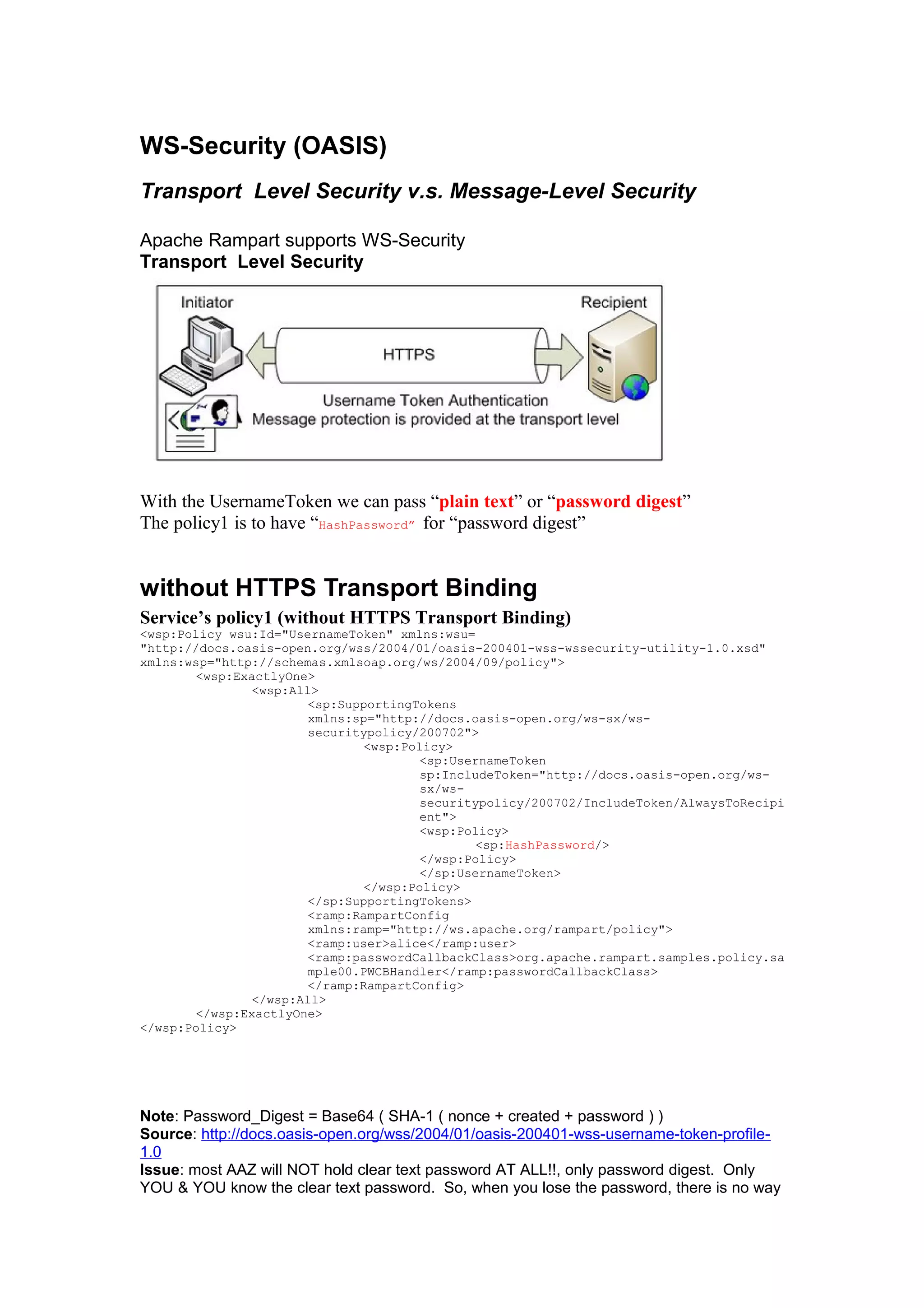
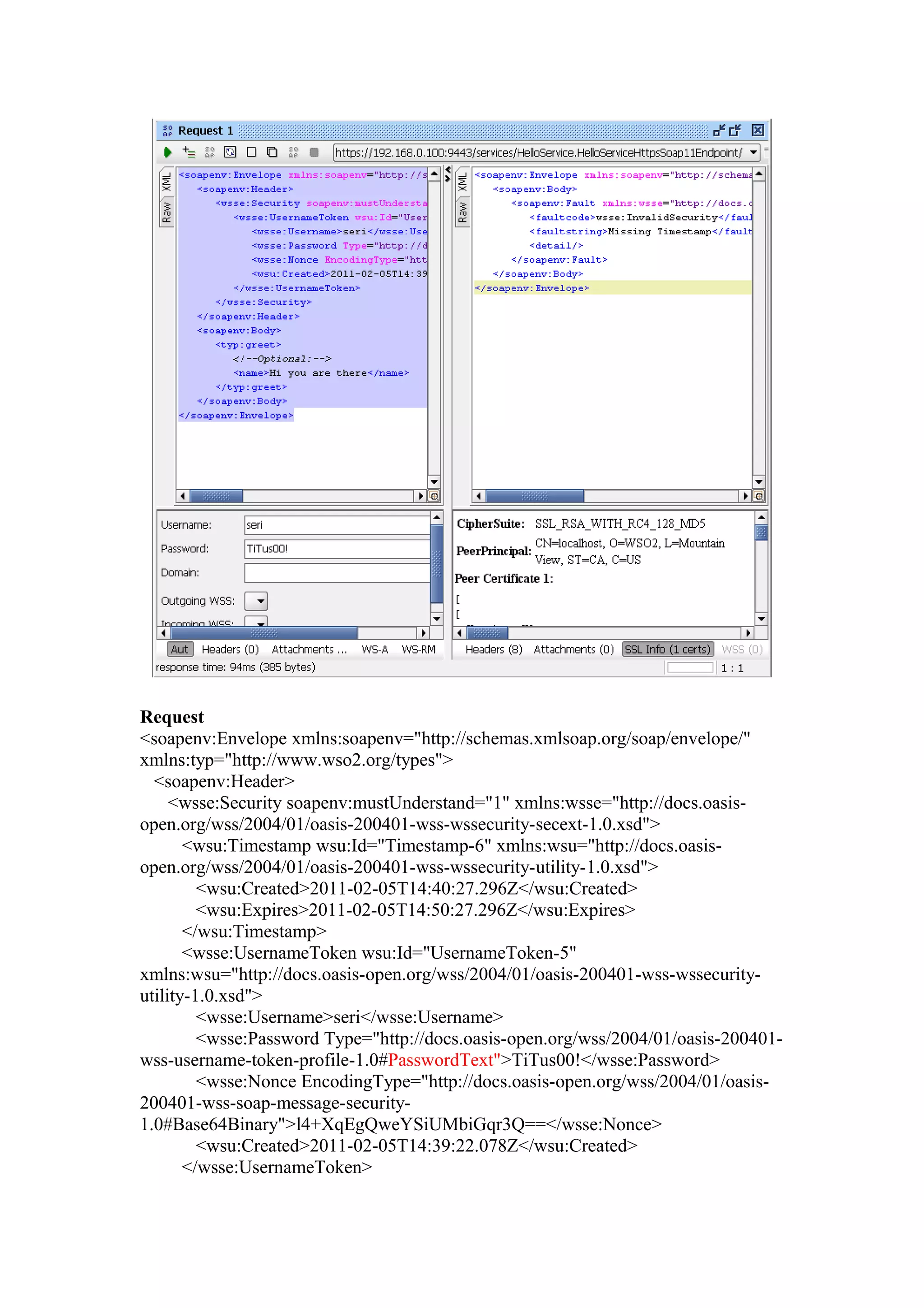
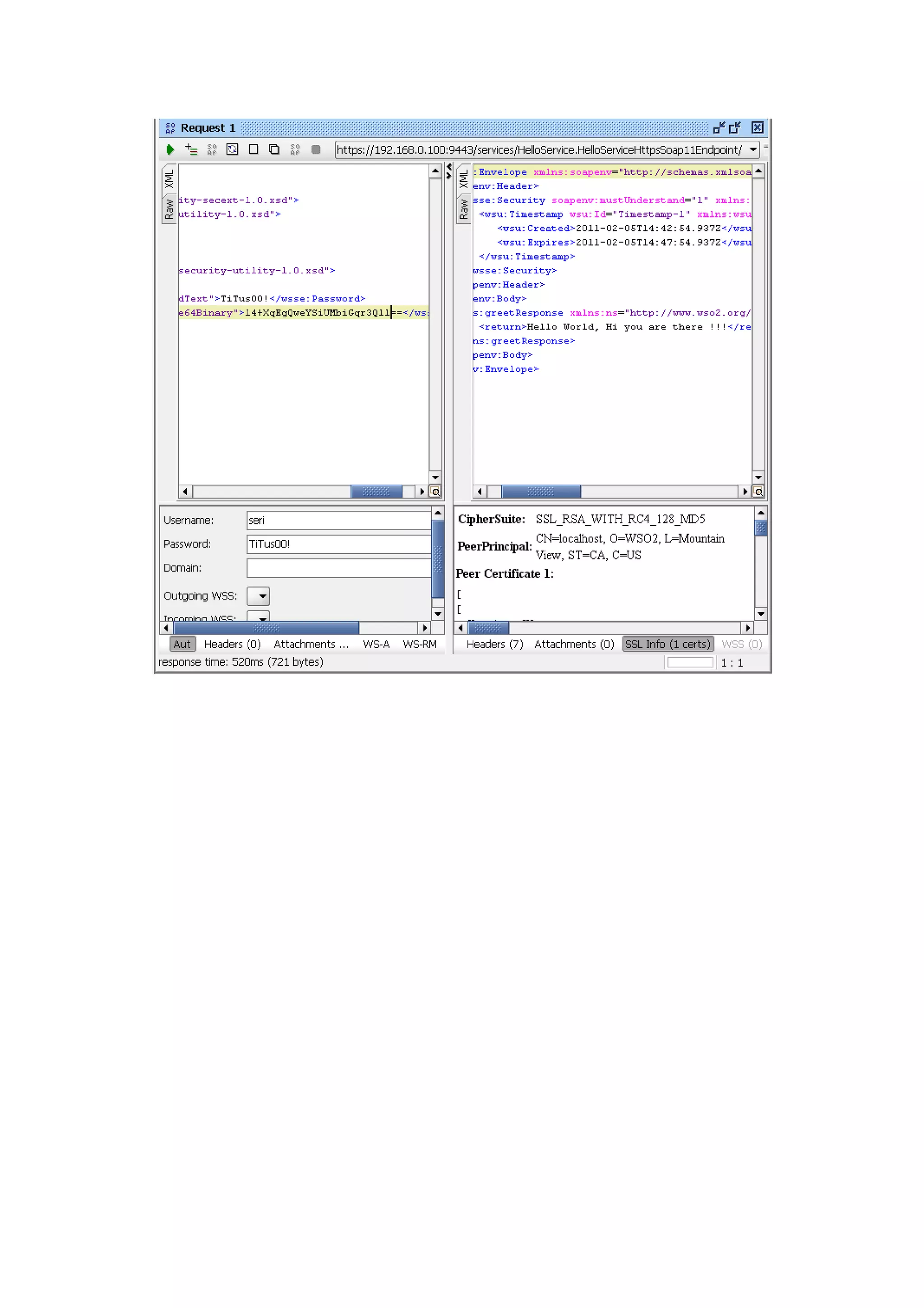
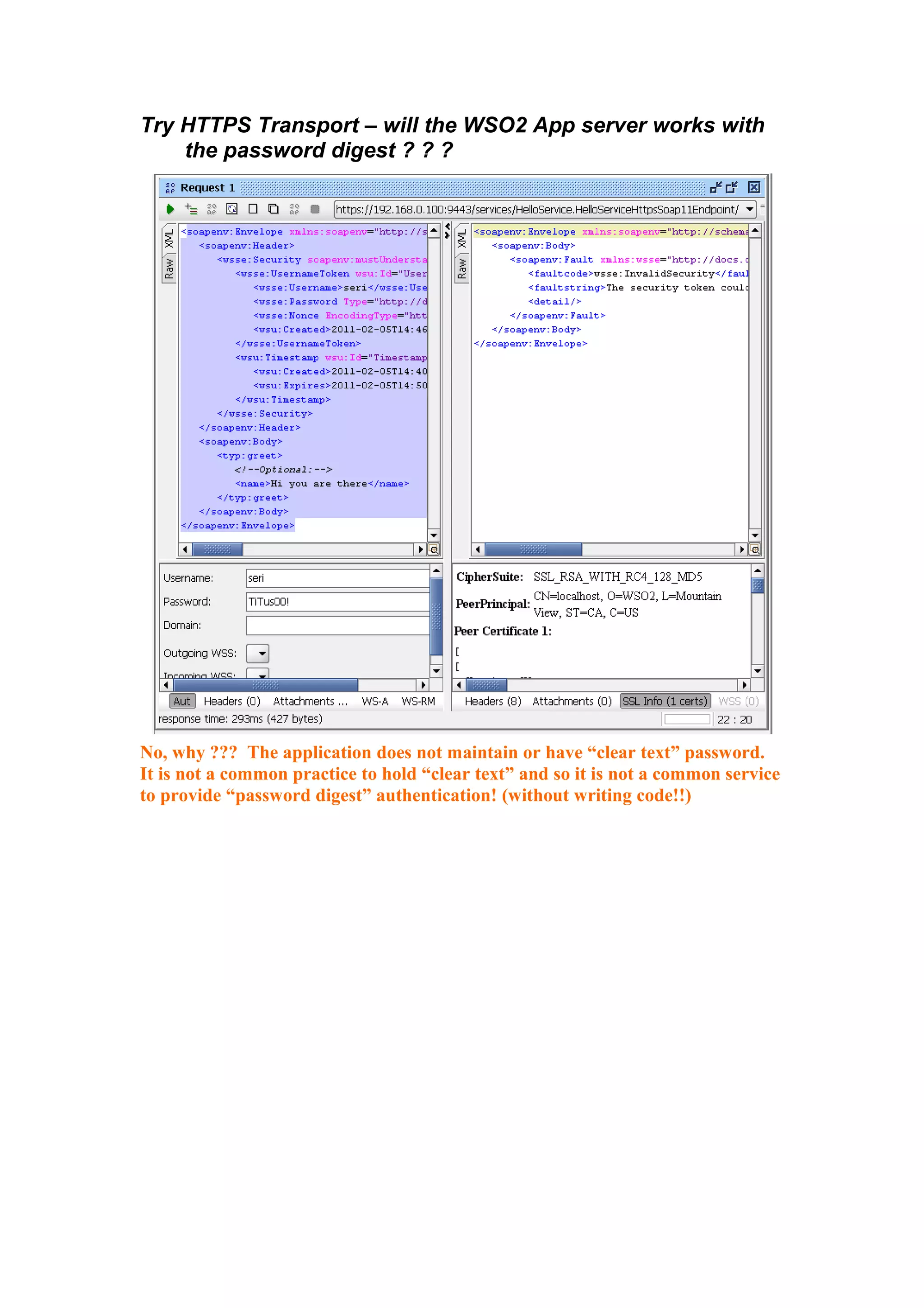
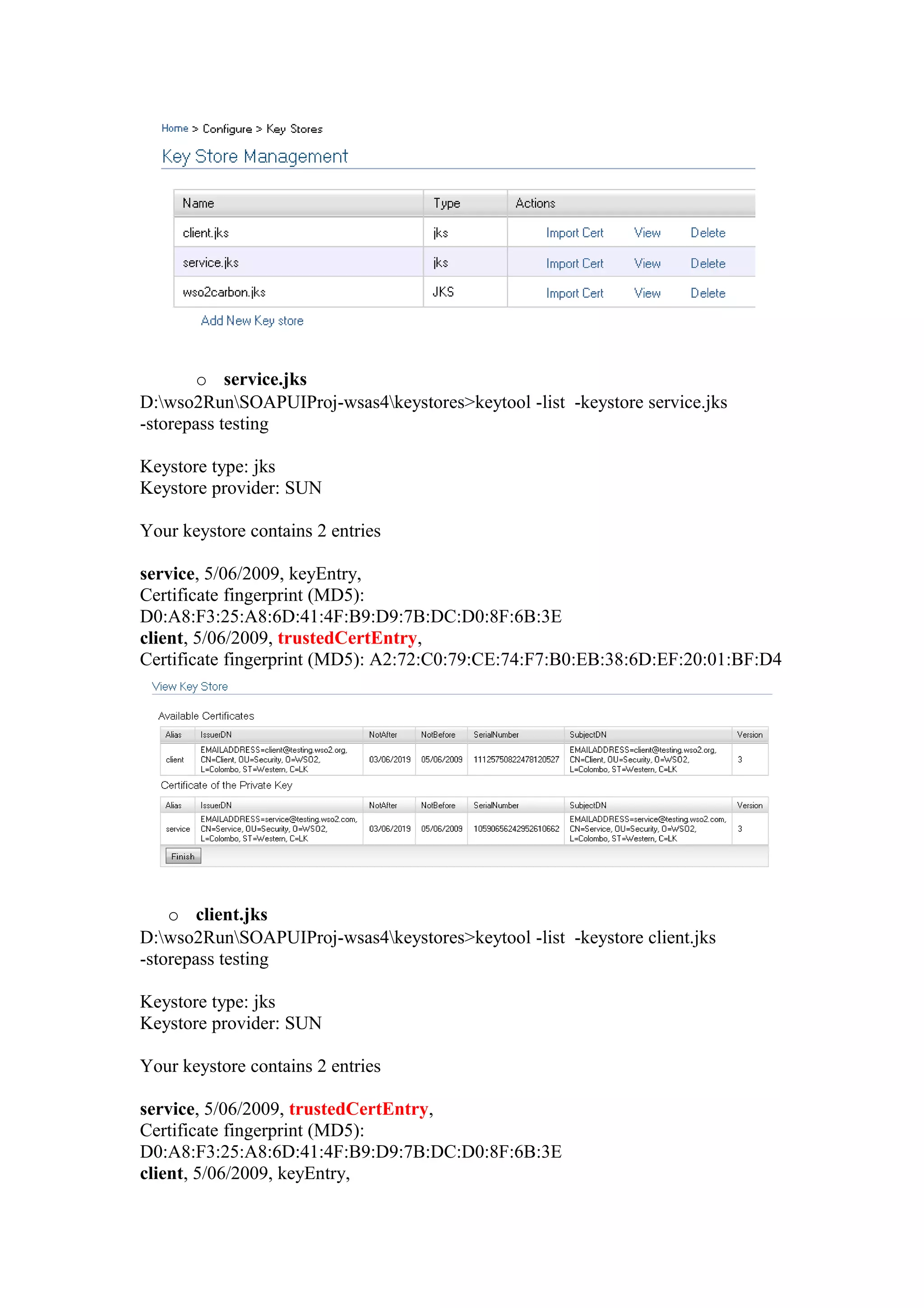
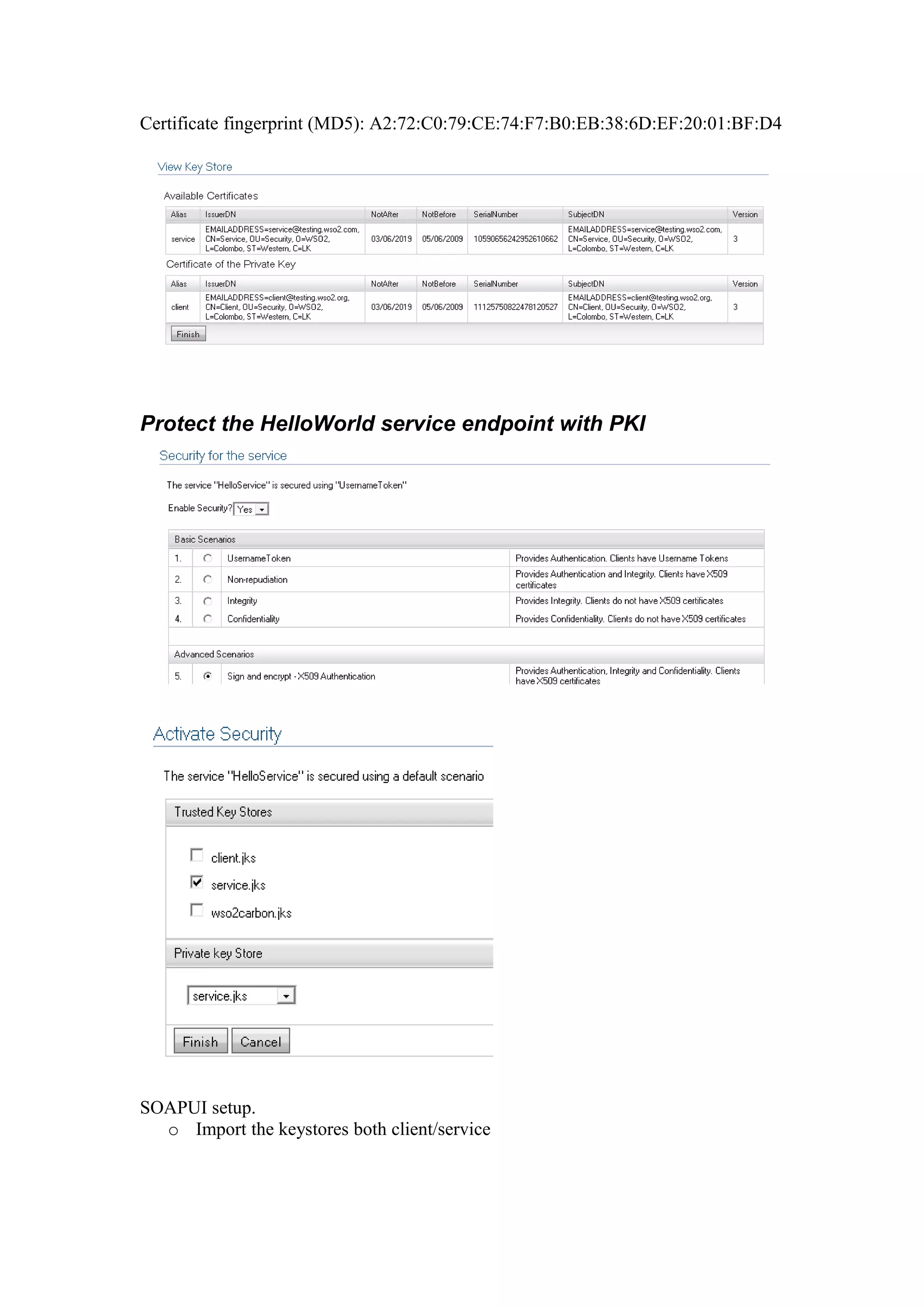
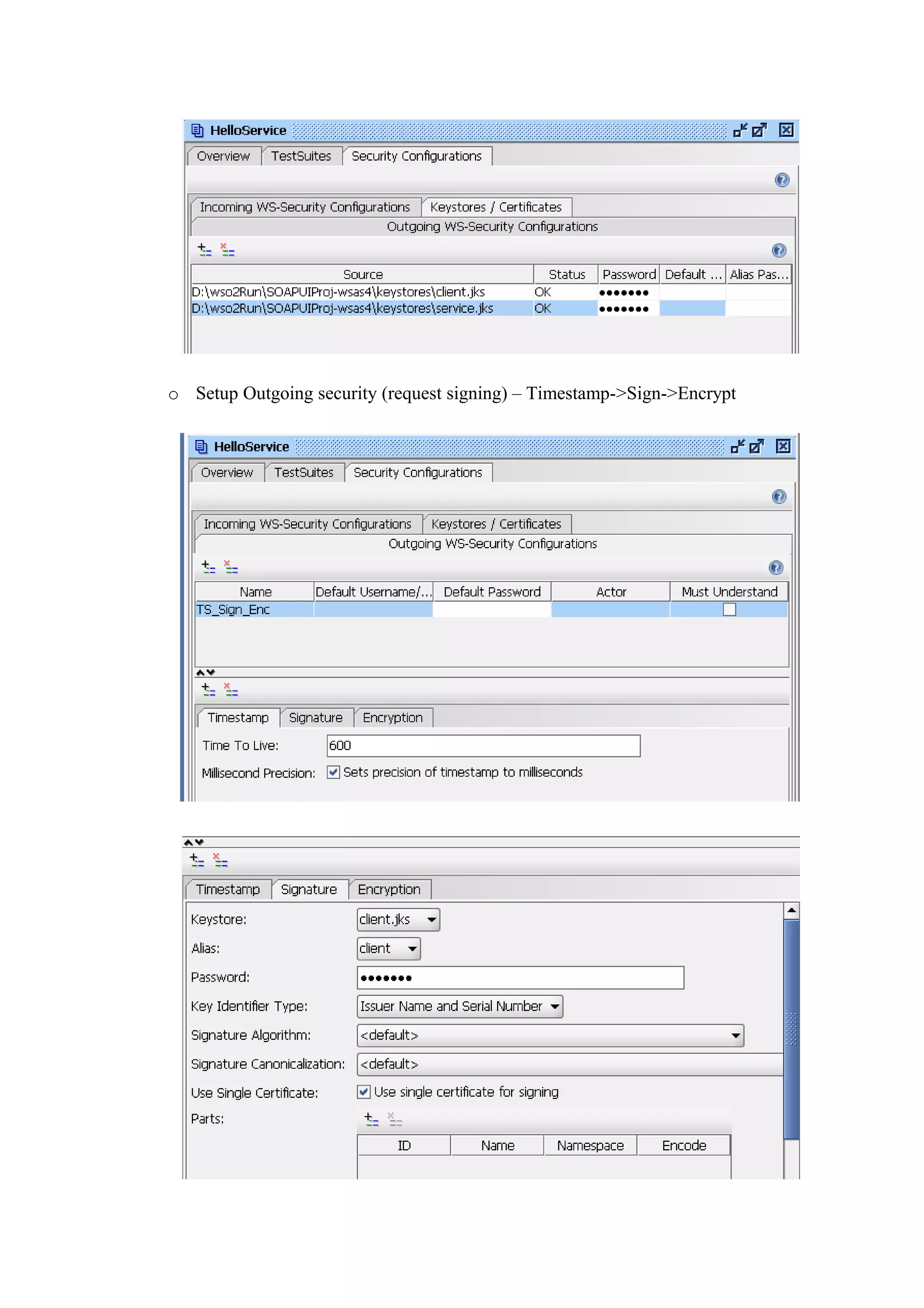
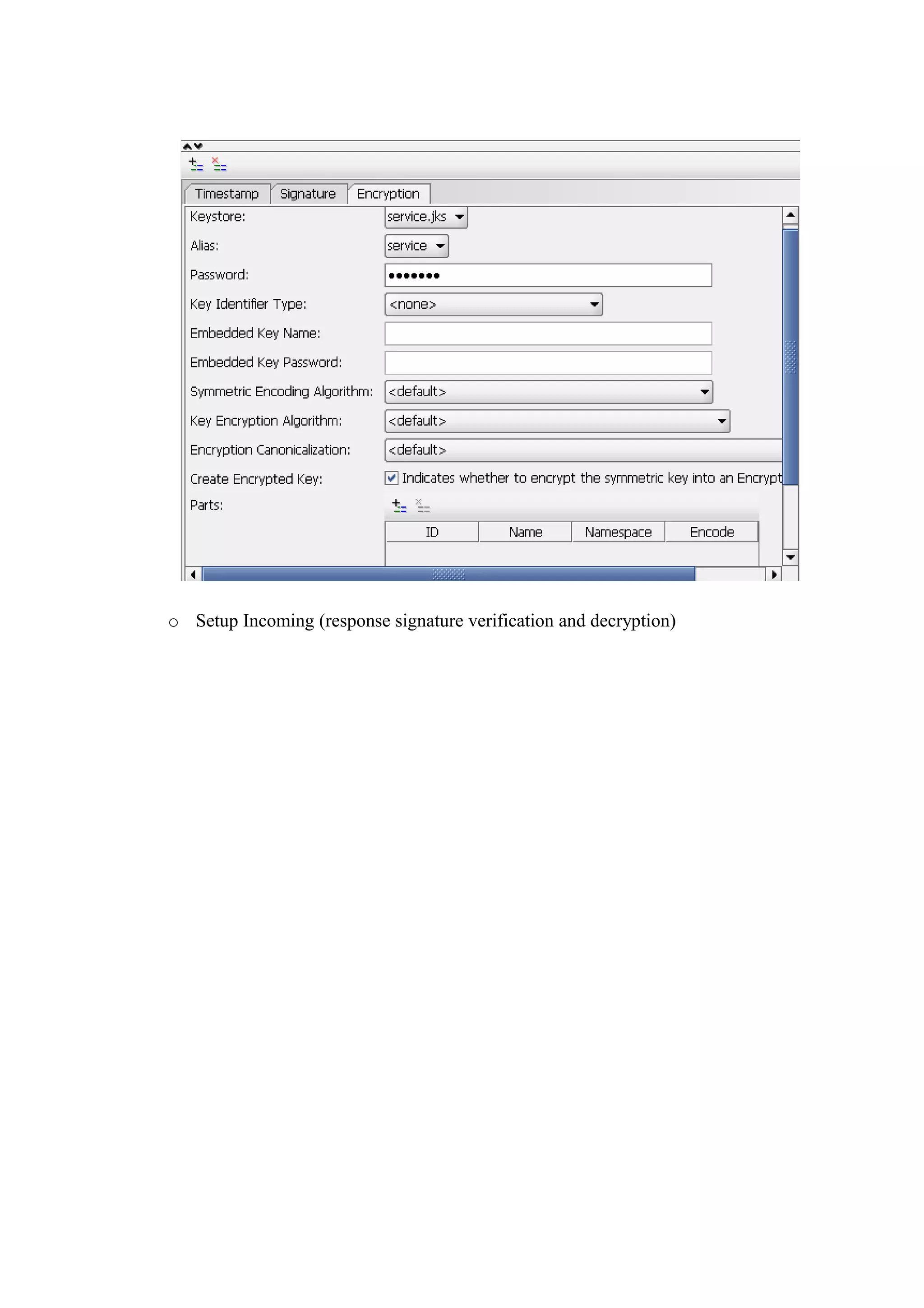
The document discusses transport level security versus message level security using WS-Security and Apache Rampart. It provides an example security policy that uses a username token with a hashed password for message level authentication without HTTPS. The document then demonstrates creating and validating a request with a username token containing a plaintext and hashed password.
![<soapenv:Fault xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-
1.0.xsd">
<faultcode>wsse:InvalidSecurity</faultcode>
<faultstring>The security token could not be authenticated or authorized; nested exception is:
javax.security.auth.callback.UnsupportedCallbackException: check failed</faultstring>
<detail/>
</soapenv:Fault>
</soapenv:Body>
</soapenv:Envelope>
Tomcat’s log
at org.apache.rampart.RampartEngine.process(RampartEngine.java:124)
at org.apache.rampart.handler.RampartReceiver.invoke(RampartReceiver.jav
a:92)
... 19 more
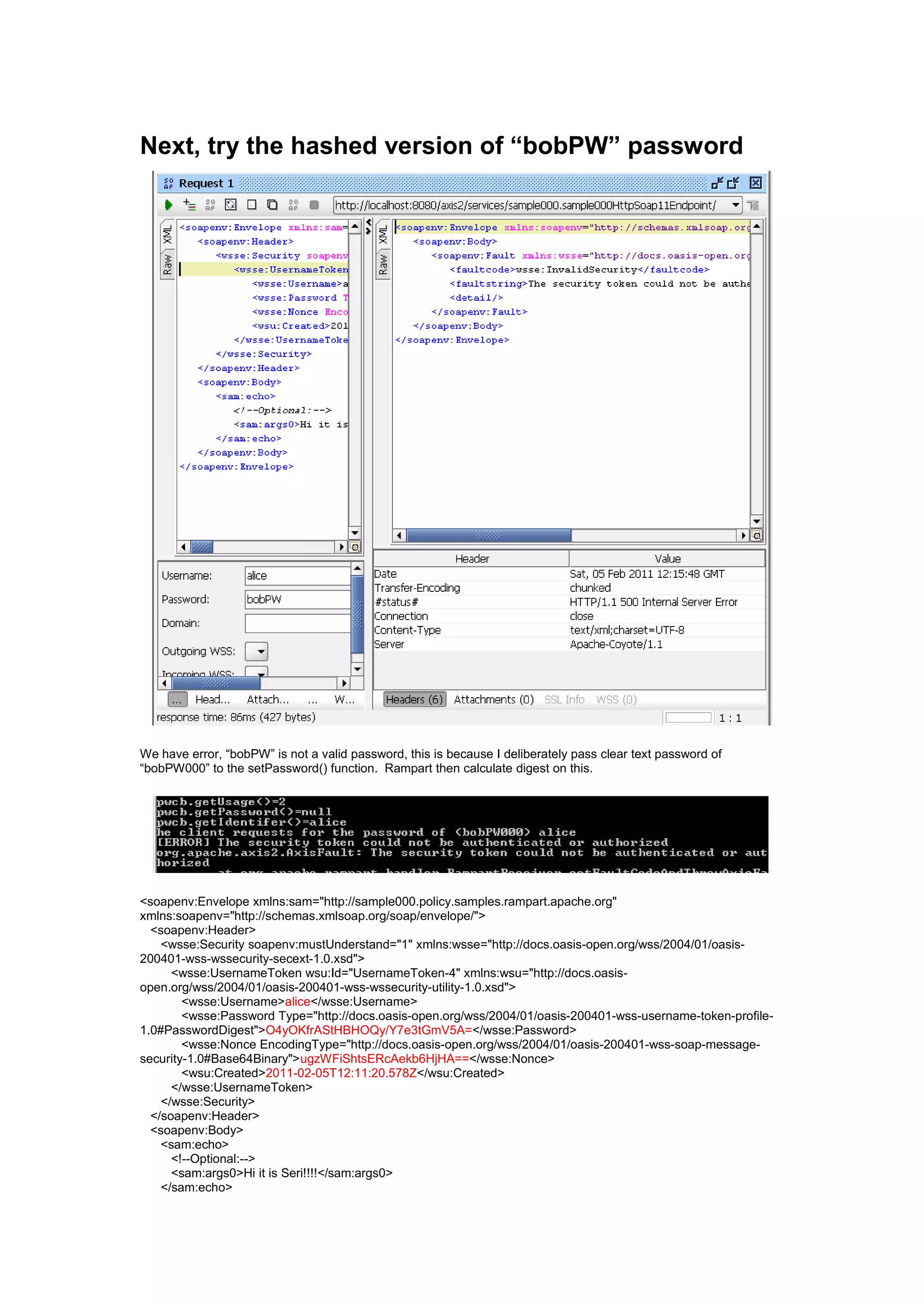
pwcb.getUsage()=5
pwcb.getPassword()=
wrong password
pwcb.getIdentifer()=alice
UnsupportedCallbackException!!!
[ERROR] The security token could not be authenticated or authorized; nested exce
ption is:
javax.security.auth.callback.UnsupportedCallbackException: check failed
org.apache.axis2.AxisFault: The security token could not be authenticated or aut
horized; nested exception is:
javax.security.auth.callback.UnsupportedCallbackException: check failed
at org.apache.rampart.handler.RampartReceiver.setFaultCodeAndThrowAxisFa
ult(RampartReceiver.java:166)
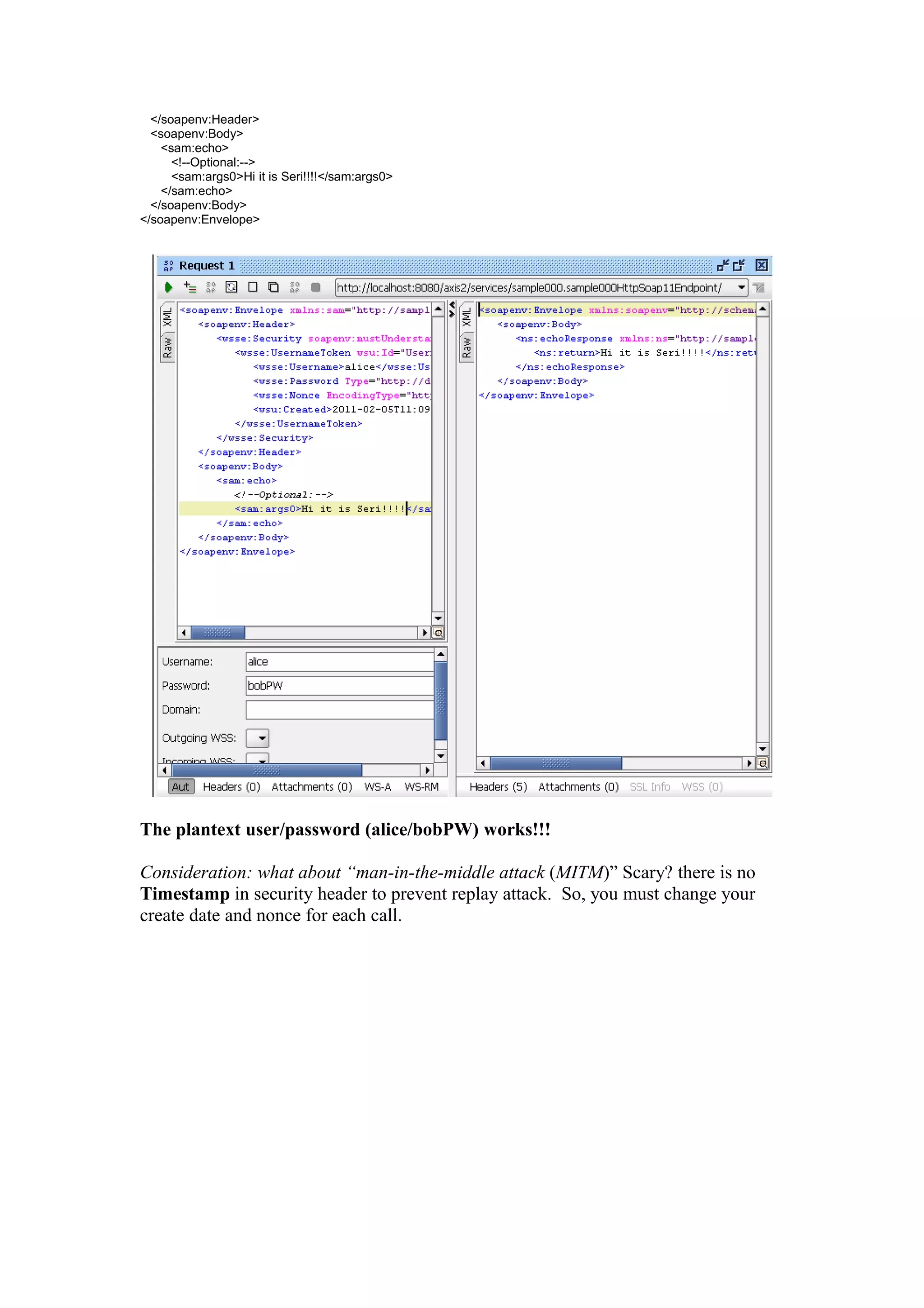
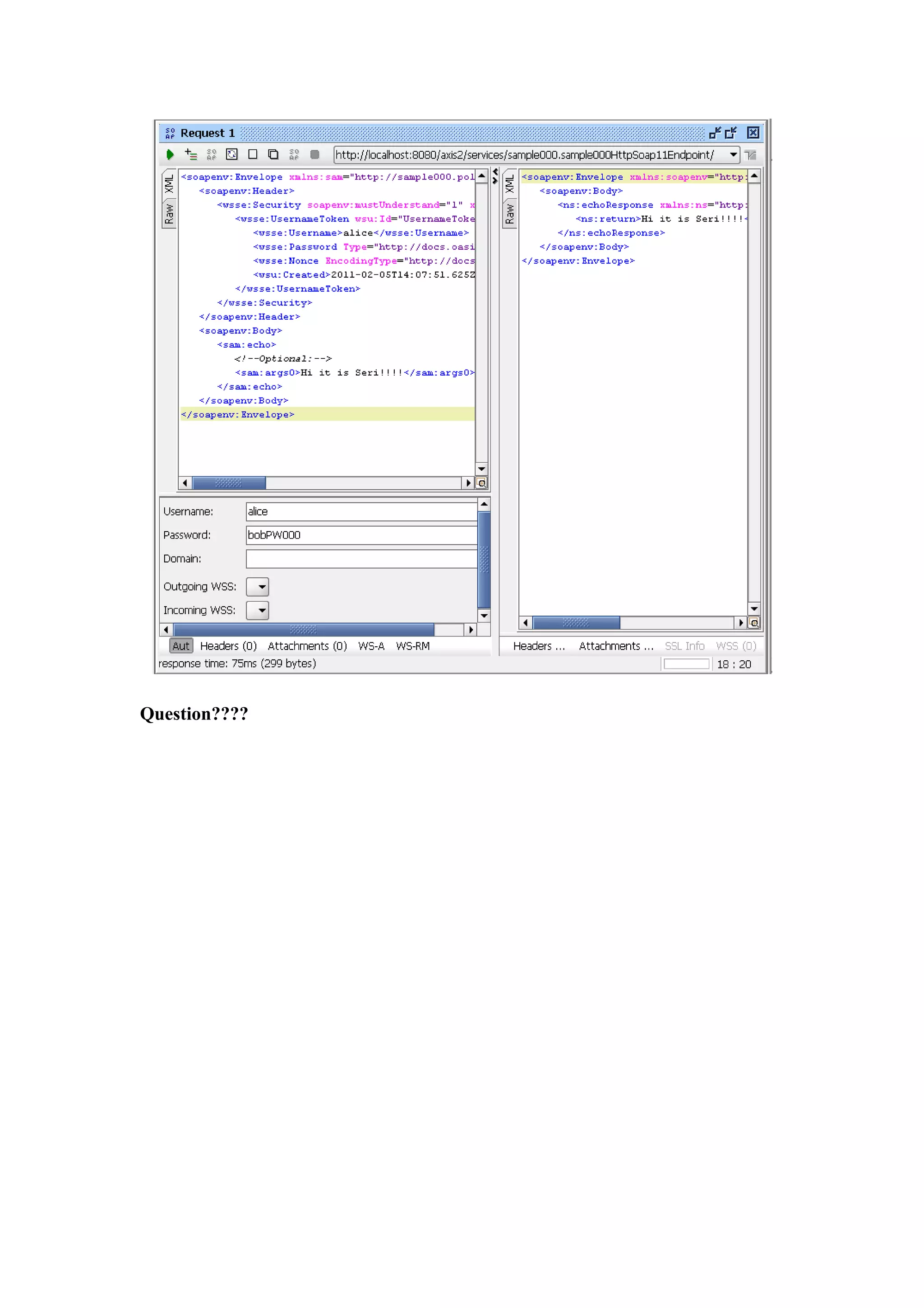
Try2: using valid user/password
But, let find out the password first, just decompile it! (alice/bobPW)
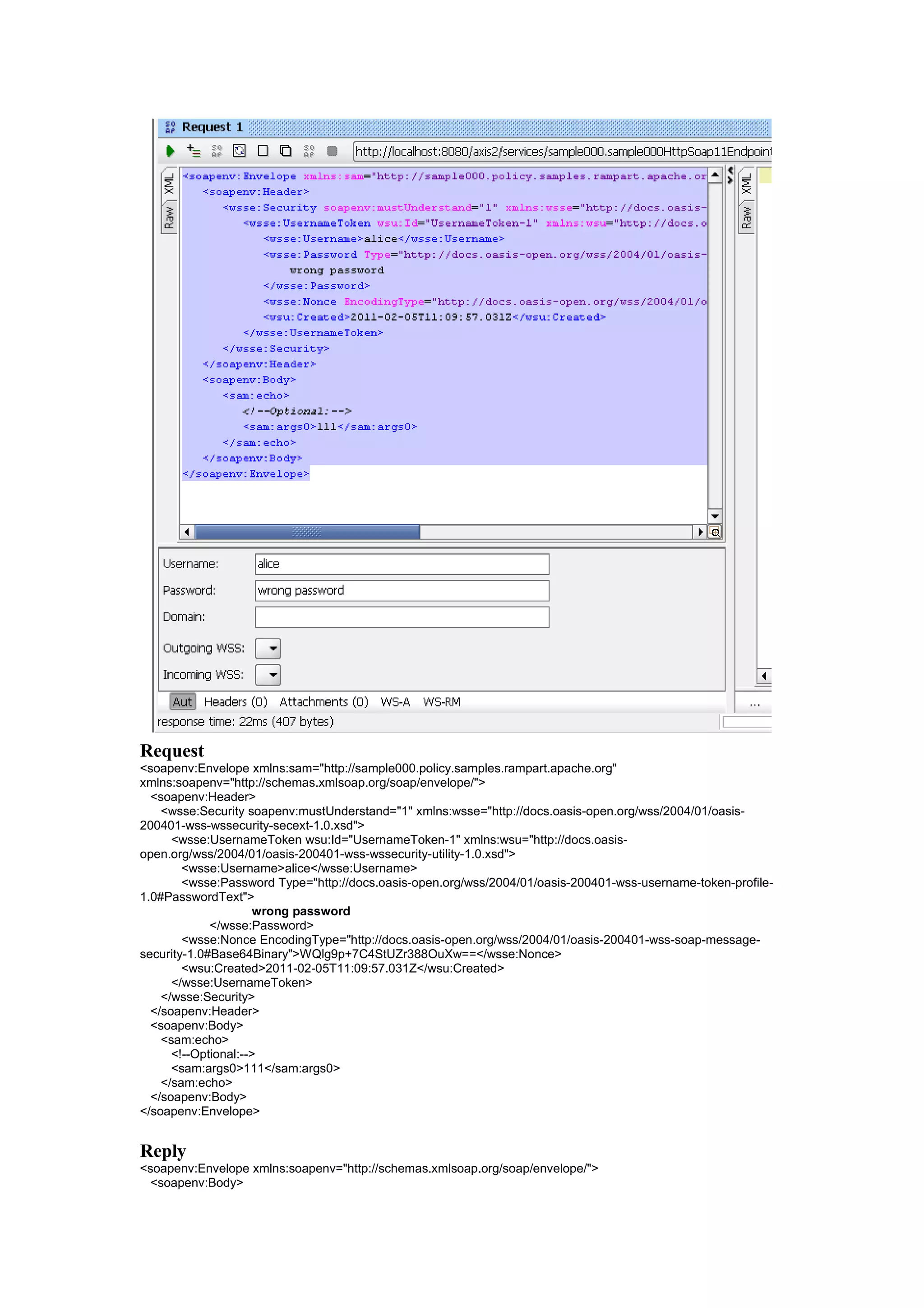
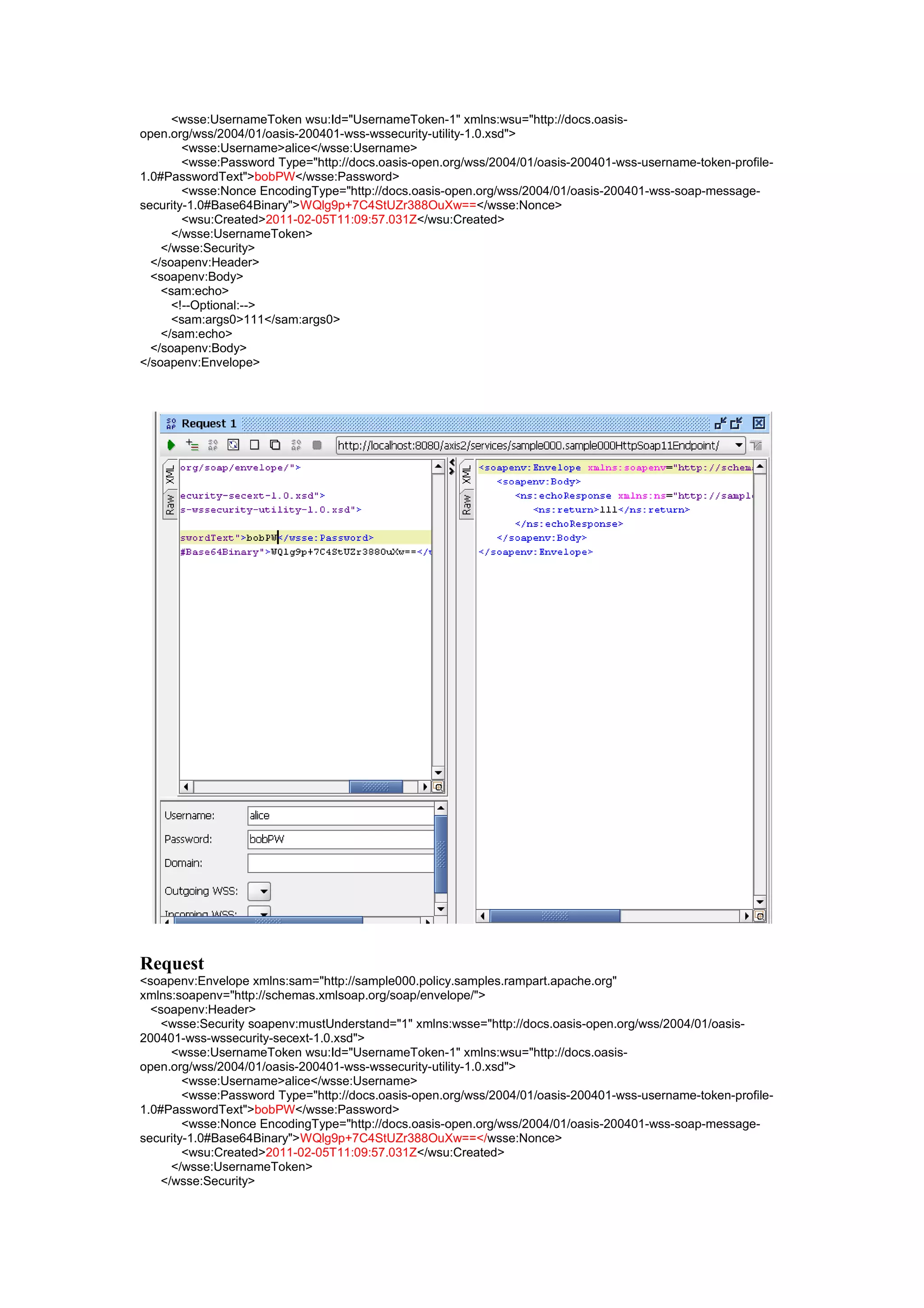
Request
<soapenv:Envelope xmlns:sam="http://sample000.policy.samples.rampart.apache.org"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<wsse:Security soapenv:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-
200401-wss-wssecurity-secext-1.0.xsd">](https://image.slidesharecdn.com/ws-securitywithopensourceplatform-120927064949-phpapp02/75/Ws-security-with-opensource-platform-5-2048.jpg)








![• {signed-element-ids=[Timestamp-34, SigConf-35, Id-19879731], signature-
value=[B@312737, principal=EMAILADDRESS=service@testing.wso2.com,
CN=Service, OU=Security, O=WSO2, L=Colombo, ST=Western, C=LK,
x509-certificate=[ [ Version: V3 Subject:
EMAILADDRESS=service@testing.wso2.com, CN=Service, OU=Security,
O=WSO2, L=Colombo, ST=Western, C=LK Signature Algorithm:
SHA1withRSA, OID = 1.2.840.113549.1.1.5 Key: Sun RSA public key, 1024
bits modulus:
142787805887320168542756913024439565736989257239165007008662260
193547498928736096603124059603215869018576688878929314609149290
485371788007153295892396211768440847822078708792134872328877577
461616678984794572805792551131582166323949869010712947644117382
585954355741145836197196574350626777457965611383098455857 public
exponent: 65537 Validity: [From: Fri Jun 05 01:50:54 EST 2009, To: Mon Jun
03 01:50:54 EST 2019] Issuer:
EMAILADDRESS=service@testing.wso2.com, CN=Service, OU=Security,
O=WSO2, L=Colombo, ST=Western, C=LK SerialNumber: [ 92f991bd
c376a366] Certificate Extensions: 3 [1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [ KeyIdentifier [ 0000: 2A 92 B8 8F EB 5B FF FA B2
9F AE 3B B6 8F 30 F9 *....[.....;..0. 0010: AB 04 11 2F .../ ] ] [2]: ObjectId:
2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 2A
92 B8 8F EB 5B FF FA B2 9F AE 3B B6 8F 30 F9 *....[.....;..0. 0010: AB 04
11 2F .../ ] [EMAILADDRESS=service@testing.wso2.com, CN=Service,
OU=Security, O=WSO2, L=Colombo, ST=Western, C=LK] SerialNumber:
[ 92f991bd c376a366] ] [3]: ObjectId: 2.5.29.19 Criticality=false
BasicConstraints:[ CA:true PathLen:2147483647 ] ] Algorithm:
[SHA1withRSA] Signature: 0000: AD C7 FA 2A CA 4D C5 FC 28 08 7C 60
77 8C D7 F4 ...*.M..(..`w... 0010: 99 A1 77 1A 8E 9D 95 4C 40 A2 47 BE 10
76 26 82 ..w....L@.G..v&. 0020: EF 42 C1 B5 79 E8 CD 4B 60 D7 72 5B BD
66 88 24 .B..y..K`.r[.f.$ 0030: 5C 64 D1 F8 BD 06 C3 AE 01 EC 61 D8 03 0F
E6 4C d........a....L 0040: 77 ED 3D D9 D0 EB 6C 38 3F AF 11 E3 10 23 F6
D9 w.=...l8?....#.. 0050: 5A 35 8F 2F 1A 7C BC E6 A8 76 D6 47 70 D1 E6
CD Z5./.....v.Gp... 0060: 98 5C A6 25 BE 87 32 00 37 5A C0 39 42 BD 09
88 ..%..2.7Z.9B... 0070: 9C 70 35 D7 06 6B 37 CF 4D 95 76 0D 03 8C 19 E9](https://image.slidesharecdn.com/ws-securitywithopensourceplatform-120927064949-phpapp02/75/Ws-security-with-opensource-platform-35-2048.jpg)
![.p5..k7.M.v..... ], data-ref-uris=[org.apache.ws.security.WSDataRef@8c3eb8,
org.apache.ws.security.WSDataRef@169baee,
org.apache.ws.security.WSDataRef@6f83e2], action=2}
• {signature-confirmation=, action=128}
• {decrypted-key=[B@c47220, x509-certificate=[ [ Version: V3 Subject:
EMAILADDRESS=client@testing.wso2.org, CN=Client, OU=Security,
O=WSO2, L=Colombo, ST=Western, C=LK Signature Algorithm:
SHA1withRSA, OID = 1.2.840.113549.1.1.5 Key: Sun RSA public key, 1024
bits modulus:
156829787087058823772740149638388103538055568357051354167337442
712330446127825134158762805864671391781756669323262925162860183
606703961194780176034603586880734475502021967653259319661122546
654797840395948823849558697600164262393888293439239666341788323
776432930742293161722065157625649824305034220675463799907 public
exponent: 65537 Validity: [From: Fri Jun 05 01:54:46 EST 2009, To: Mon Jun
03 01:54:46 EST 2019] Issuer: EMAILADDRESS=client@testing.wso2.org,
CN=Client, OU=Security, O=WSO2, L=Colombo, ST=Western, C=LK
SerialNumber: [ 9a669b6d 2151864f] Certificate Extensions: 3 [1]: ObjectId:
2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 56 80
76 A4 78 2B 20 CE 8A AC 2D AB 4F A0 E7 D8 V.v.x+ ...-.O... 0010: A6 A3
1A 06 .... ] ] [2]: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [
KeyIdentifier [ 0000: 56 80 76 A4 78 2B 20 CE 8A AC 2D AB 4F A0 E7 D8
V.v.x+ ...-.O... 0010: A6 A3 1A 06 .... ]
[EMAILADDRESS=client@testing.wso2.org, CN=Client, OU=Security,
O=WSO2, L=Colombo, ST=Western, C=LK] SerialNumber: [ 9a669b6d
2151864f] ] [3]: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:
[ CA:true PathLen:2147483647 ] ] Algorithm: [SHA1withRSA] Signature:
0000: D2 1D F6 8D 1E 40 E1 5F F9 89 4D 5D CF AE 81 00 .....@._..M]....
0010: B4 DD 1D E6 FC 15 AC 99 62 AA 1D FF AC 7F 2B 30 ........b.....+0
0020: B6 5A 8F E7 D3 C5 12 93 D2 47 B4 36 08 FE 57 44 .Z.......G.6..WD
0030: 17 79 B1 79 05 61 17 CB 63 49 A7 3B 94 CB CD 4E .y.y.a..cI.;...N
0040: 10 2B C2 A7 85 3B 66 FB 41 28 D1 48 9B 30 E8 7F .+...;f.A(.H.0..
0050: D9 22 4D 3C 69 23 6D 10 88 D8 B2 4A F6 1E 20 D8 ."M
• {binary-security-
token=MIIDjTCCAvagAwIBAgIJAJpmm20hUYZPMA0GCSqGSIb3DQEB
BQUAMIGMMQswCQYDVQQGEwJMSzEQMA4GA1UECBMHV2VzdG
VybjEQMA4GA1UEBxMHQ29sb21ibzENMAsGA1UEChMEV1NPMjERM
A8GA1UECxMIU2VjdXJpdHkxDzANBgNVBAMTBkNsaWVudDEmMCQ
GCSqGSIb3DQEJARYXY2xpZW50QHRlc3Rpbmcud3NvMi5vcmcwHhcN
MDkwNjA0MTU1NDQ2WhcNMTkwNjAyMTU1NDQ2WjCBjDELMAkG
A1UEBhMCTEsxEDAOBgNVBAgTB1dlc3Rlcm4xEDAOBgNVBAcTB0Nv
bG9tYm8xDTALBgNVBAoTBFdTTzIxETAPBgNVBAsTCFNlY3VyaXR5
MQ8wDQYDVQQDEwZDbGllbnQxJjAkBgkqhkiG9w0BCQEWF2NsaWVu
dEB0ZXN0aW5nLndzbzIub3JnMIGfMA0GCSqGSIb3DQEBAQUAA4GNA
DCBiQKBgQDfVUF1ZoijyQ4Eg4MW9T2RKF/zgGuNiVaFWCAnb9iYtjb5
Y08YBtYgzfnVNJrPJbNwc1q3eJ+4VxVBUNXmboZahAPUx77Asheo7rR8g
6hZh/VkjF8XrQm2Sd6HOX0f2syy/nunWOpsFcW+G21cMfPvx1wFMuU4y
VEe2OtntyJkYwIDAQABo4H0MIHxMB0GA1UdDgQWBBRWgHakeCsgzo
qsLatPoOfYpqMaBjCBwQYDVR0jBIG5MIG2gBRWgHakeCsgzoqsLatPoO
fYpqMaBqGBkqSBjzCBjDELMAkGA1UEBhMCTEsxEDAOBgNVBAgTB](https://image.slidesharecdn.com/ws-securitywithopensourceplatform-120927064949-phpapp02/75/Ws-security-with-opensource-platform-36-2048.jpg)



![Appendix
PasswordDigestTest.java
import java.security.MessageDigest;
import org.apache.ws.security.util.Base64;
public class PasswordDigestTest {
public static void main(String[] args) {
/*
String nonce="UIYifr1SPoNlrmmKGSVOug==";
String created = "2009-12-03T16:14:49Z";
String password ="test8";
*/
String nonce="ugzWFiShtsERcAekb6HjHA==";
String created = "2011-02-05T12:11:20.578Z";
String password ="bobPW000";
String expectedHashPwd = "O4yOKfrAStHBHOQy/Y7e3tGmV5A=";
//String res =doPasswordDigest(nonce, created, p
assword);
String res =doPasswordDigest(args[0], args[1], args[2]);
System.out.println(expectedHashPwd + " " + res);
}
public static String doPasswordDigest(String nonce, String created, String password) {
String passwdDigest = null;
try {
byte[] b1 = nonce != null ? Base64.decode(nonce) : new byte[0];
byte[] b2 = created != null ? created.getBytes("UTF-8") : new byte[0];
byte[] b3 = password.getBytes("UTF-8");
byte[] b4 = new byte[b1.length + b2.length + b3.length];
int offset = 0;
System.arraycopy(b1, 0, b4, offset, b1.length);
offset += b1.length;
System.arraycopy(b2, 0, b4, offset, b2.length);
offset += b2.length;
System.arraycopy(b3, 0, b4, offset, b3.length);
MessageDigest sha = MessageDigest.getInstance("SHA-1");
sha.reset();
sha.update(b4);
passwdDigest = Base64.encode(sha.digest());
} catch (Exception e) {
e.printStackTrace();
}
return passwdDigest;
}
}](https://image.slidesharecdn.com/ws-securitywithopensourceplatform-120927064949-phpapp02/75/Ws-security-with-opensource-platform-40-2048.jpg)
![PWCBHandler.java
package org.apache.rampart.samples.policy.sample000;
import java.io.IOException;
import java.io.PrintStream;
import javax.security.auth.callback.Callback;
import javax.security.auth.callback.CallbackHandler;
import javax.security.auth.callback.UnsupportedCallbackException;
import org.apache.ws.security.WSPasswordCallback;
public class PWCBHandler implements CallbackHandler
{
public void handle(Callback[] paramArrayOfCallback)
throws IOException, UnsupportedCallbackException
{
for (int i = 0; i < paramArrayOfCallback.length; ++i)
{
WSPasswordCallback localWSPasswordCallback =
(WSPasswordCallback)paramArrayOfCallback[i];
System.out.println("pwcb.getUsage()=" + localWSPasswordCallback.getUsage());
System.out.println("pwcb.getPassword()=" + localWSPasswordCallback.getPassword());
System.out.println("pwcb.getIdentifer()=" + localWSPasswordCallback.getIdentifer());
if (localWSPasswordCallback.getUsage() == 5)
{
if ((localWSPasswordCallback.getIdentifer().equals("alice")) &&
(localWSPasswordCallback.getPassword().equals("bobPW")))
{
System.out.println("alice/bobPW found");
return;
}
System.out.println("UnsupportedCallbackException!!!");
throw new UnsupportedCallbackException(paramArrayOfCallback[i], "check failed");
}
//assume getUsage()==2 ie. Hashed password!!
System.out.println("The client requests for the password of (bobPW000) " +
localWSPasswordCallback.getIdentifer());
//I assumed that I somehow, somewhere I can get clear password needed for SHA-1 digest function.
//e.g I could have retrieved from LDAP and set it here for Rampart to do password digest calculation!
// Here I just use a different password ie “bobPW000”, I could have used the same password ie “bobPW” in the
setPassword() below.
localWSPasswordCallback.setPassword("bobPW000");
}
}
}](https://image.slidesharecdn.com/ws-securitywithopensourceplatform-120927064949-phpapp02/75/Ws-security-with-opensource-platform-41-2048.jpg)