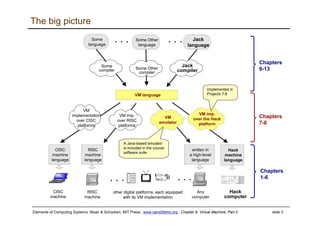
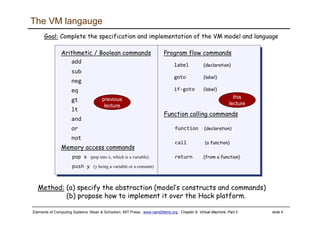
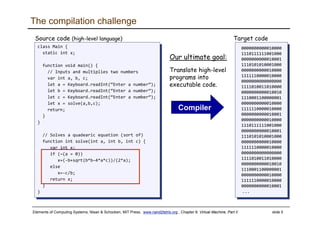
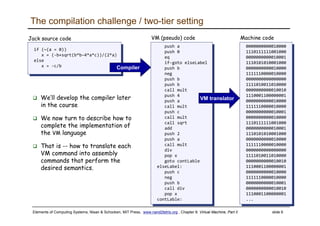
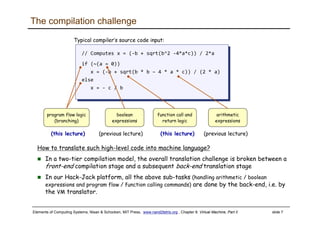
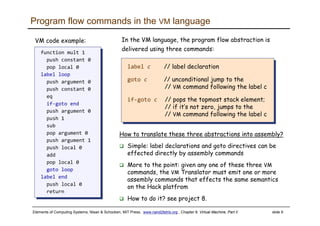
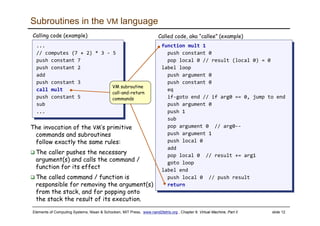
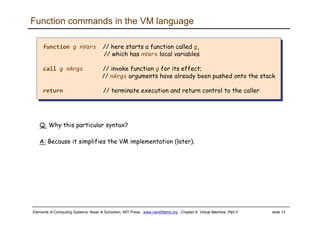
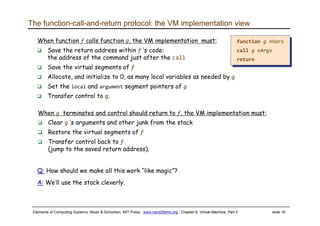
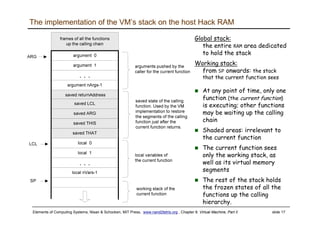
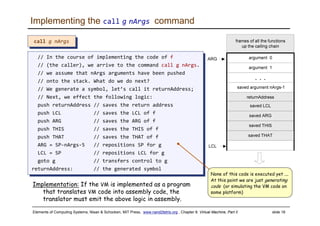
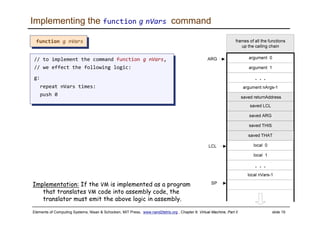
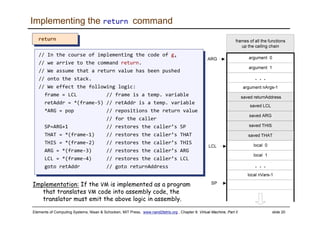
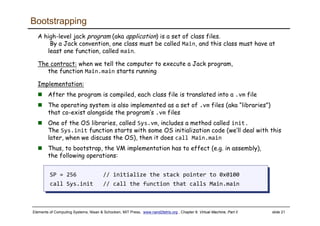
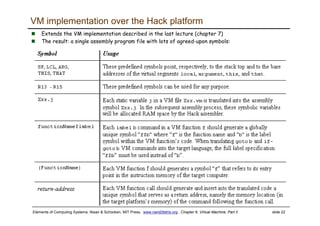
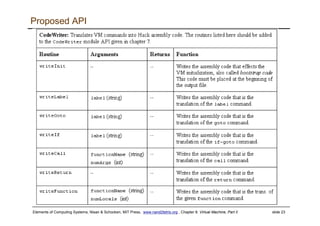
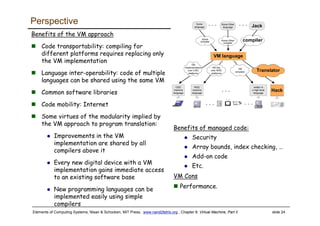
The document discusses the virtual machine (VM) model and language. It explains that the VM acts as an abstract interface between software and hardware, providing a standardized programming model. The VM language specification includes arithmetic, boolean, memory access, and program flow commands. It also discusses how a two-tier compilation model can be used to translate a high-level language to VM code and then to machine language through a compiler and VM translator. The lecture will focus on how to implement the program flow commands in the VM language by emitting appropriate assembly code commands.