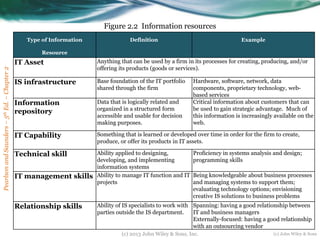
This document discusses strategic use of information resources. It provides examples of how Zara strategically uses information systems to gain advantages over competitors. Zara links customer demand data to manufacturing and distribution through a system that sends daily updates to headquarters. Managers then use this information to determine new designs and inventory management. The document also discusses Porter's five forces model and value chain model as ways for firms to identify how information resources can be used strategically. Firms can use information resources to influence competitive forces and activities in the value chain to improve efficiency and effectiveness.