(Spring 2013) The Impact of Dirty Fingerprints
•
0 likes•632 views
The focal point of our project is to compare the differences between dirty fingerprints and cropped fingerprints using the data we have collected. During the procedure we captured three clean and three dirty fingerprints from each person in the group. We then analyzed the score, minutiae points, core/delta, good and poor quality of each of the fingerprints. The importance of this project is to analyze the impact of dirty fingerprints on quality.
Report
Share
Report
Share
Download to read offline
Recommended
Offline signature identification using high intensity variations and cross ov...

Offline signature identification using high intensity variations and cross ov...eSAT Publishing House
More Related Content
Similar to (Spring 2013) The Impact of Dirty Fingerprints
Offline signature identification using high intensity variations and cross ov...

Offline signature identification using high intensity variations and cross ov...eSAT Publishing House
Similar to (Spring 2013) The Impact of Dirty Fingerprints (20)
Comparative study of various enhancement techniques for finger print images

Comparative study of various enhancement techniques for finger print images
Comparative study of various enhancement techniques for finger print images

Comparative study of various enhancement techniques for finger print images
Proposed Method for Off-line Signature Recognition and Verification using Neu...

Proposed Method for Off-line Signature Recognition and Verification using Neu...
International Journal of Computational Engineering Research(IJCER)

International Journal of Computational Engineering Research(IJCER)
Detecting and Improving Distorted Fingerprints using rectification techniques.

Detecting and Improving Distorted Fingerprints using rectification techniques.
IRJET- Leaf Quality Detection for Rudimentary Urban Home Gardeners using Imag...

IRJET- Leaf Quality Detection for Rudimentary Urban Home Gardeners using Imag...
OSPCV: Off-line Signature Verification using Principal Component Variances

OSPCV: Off-line Signature Verification using Principal Component Variances
IRJET- Credit Card Fraud Detection using Isolation Forest

IRJET- Credit Card Fraud Detection using Isolation Forest
Offline signature verification based on geometric feature extraction using ar...

Offline signature verification based on geometric feature extraction using ar...
Detection and rectification of distorted fingerprint

Detection and rectification of distorted fingerprint
Offline signature identification using high intensity variations and cross ov...

Offline signature identification using high intensity variations and cross ov...
COMPARATIVE ANALYSIS OF MINUTIAE BASED FINGERPRINT MATCHING ALGORITHMS

COMPARATIVE ANALYSIS OF MINUTIAE BASED FINGERPRINT MATCHING ALGORITHMS
RELATIVE STUDY ON SIGNATURE VERIFICATION AND RECOGNITION SYSTEM

RELATIVE STUDY ON SIGNATURE VERIFICATION AND RECOGNITION SYSTEM
More from International Center for Biometric Research
An Investigation into Biometric Signature Capture Device Performance and User...

An Investigation into Biometric Signature Capture Device Performance and User...International Center for Biometric Research
Advances in testing and evaluation using Human-Biometric sensor interaction m...

Advances in testing and evaluation using Human-Biometric sensor interaction m...International Center for Biometric Research
(2010) Fingerprint recognition performance evaluation for mobile ID applications

(2010) Fingerprint recognition performance evaluation for mobile ID applicationsInternational Center for Biometric Research
More from International Center for Biometric Research (20)
An Investigation into Biometric Signature Capture Device Performance and User...

An Investigation into Biometric Signature Capture Device Performance and User...
Best Practices in Reporting Time Duration in Biometrics

Best Practices in Reporting Time Duration in Biometrics
Advances in testing and evaluation using Human-Biometric sensor interaction m...

Advances in testing and evaluation using Human-Biometric sensor interaction m...
(2010) Fingerprint recognition performance evaluation for mobile ID applications

(2010) Fingerprint recognition performance evaluation for mobile ID applications
Recently uploaded
Recently uploaded (20)
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
(Spring 2013) The Impact of Dirty Fingerprints
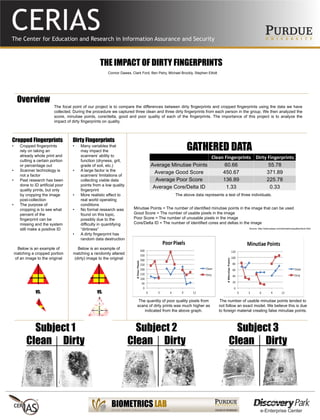
- 1. THE IMPACT OF DIRTY FINGERPRINTS The focal point of our project is to compare the differences between dirty fingerprints and cropped fingerprints using the data we have collected. During the procedure we captured three clean and three dirty fingerprints from each person in the group. We then analyzed the score, minutiae points, core/delta, good and poor quality of each of the fingerprints. The importance of this project is to analyze the impact of dirty fingerprints on quality. Connor Dawes, Clark Ford, Ben Petry, Michael Brockly, Stephen Elliott Overview Subject 1 Clean Dirty Subject 2 Clean Dirty Subject 3 Clean Dirty Cropped Fingerprints • Cropped fingerprints rely on taking an already whole print and cutting a certain portion or percentage out • Scanner technology is not a factor • Past research has been done to ID artificial poor quality prints, but only by cropping the image post-collection • The purpose of cropping is to see what percent of the fingerprint can be missing and the system still make a positive ID Dirty Fingerprints • Many variables that may impact the scanners’ ability to function (dryness, grit, grade of soil, etc.) • A large factor is the scanners’ limitations of collecting viable data points from a low quality fingerprint • More realistic effect to real world operating conditions • No formal research was found on this topic, possibly due to the difficulty in quantifying “dirtiness” • A dirty fingerprint has random data destruction VS. VS. GATHERED DATA Clean Fingerprints Dirty Fingerprints Average Minutiae Points 60.66 55.78 Average Good Score 450.67 371.89 Average Poor Score 136.89 225.78 Average Core/Delta ID 1.33 0.33 The above data represents a test of three individuals. The quantity of poor quality pixels from scans of dirty prints was much higher as indicated from the above graph. The number of usable minutiae points tended to not follow an exact model. We believe this is due to foreign material creating false minutiae points. Minutiae Points = The number of identified minutiae points in the image that can be used Good Score = The number of usable pixels in the image Poor Score = The number of unusable pixels in the image Core/Delta ID = The number of identified cores and deltas in the image Below is an example of matching a cropped portion of an image to the original Below is an example of matching a randomly altered (dirty) image to the original Source: http://www.aware.com/biometrics/qualitycheck.html
