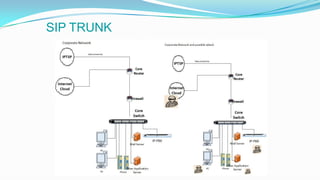
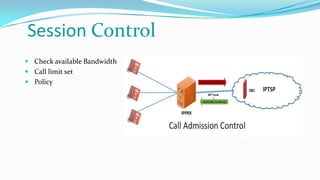
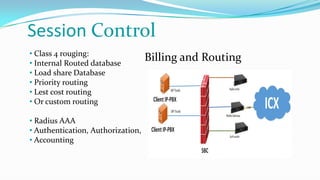
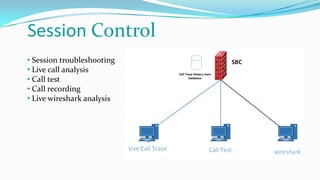
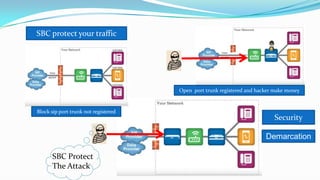
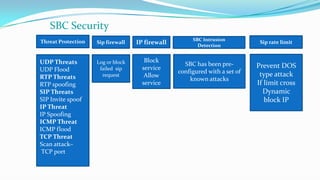
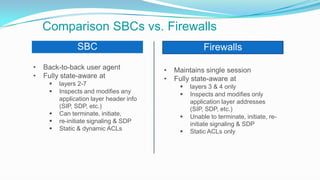
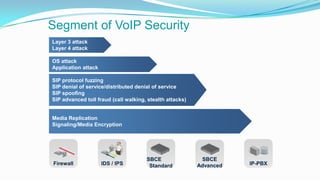
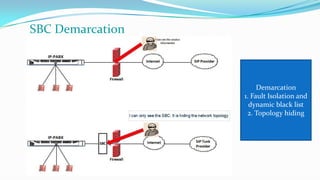
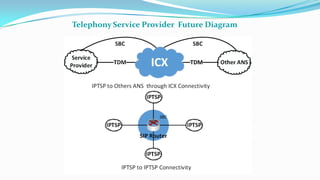
This document discusses the importance of Session Border Controllers (SBCs) for Voice over Internet Protocol (VoIP) networks. It outlines how SBCs provide session control, security, interoperability, and demarcation. SBCs help protect against various VoIP threats like denial of service attacks, spoofing, and toll fraud. They can filter traffic, authenticate users, and enforce policies to secure VoIP infrastructure and services. The document also compares SBCs to traditional firewalls and explains how SBCs can better handle real-time multimedia communications.