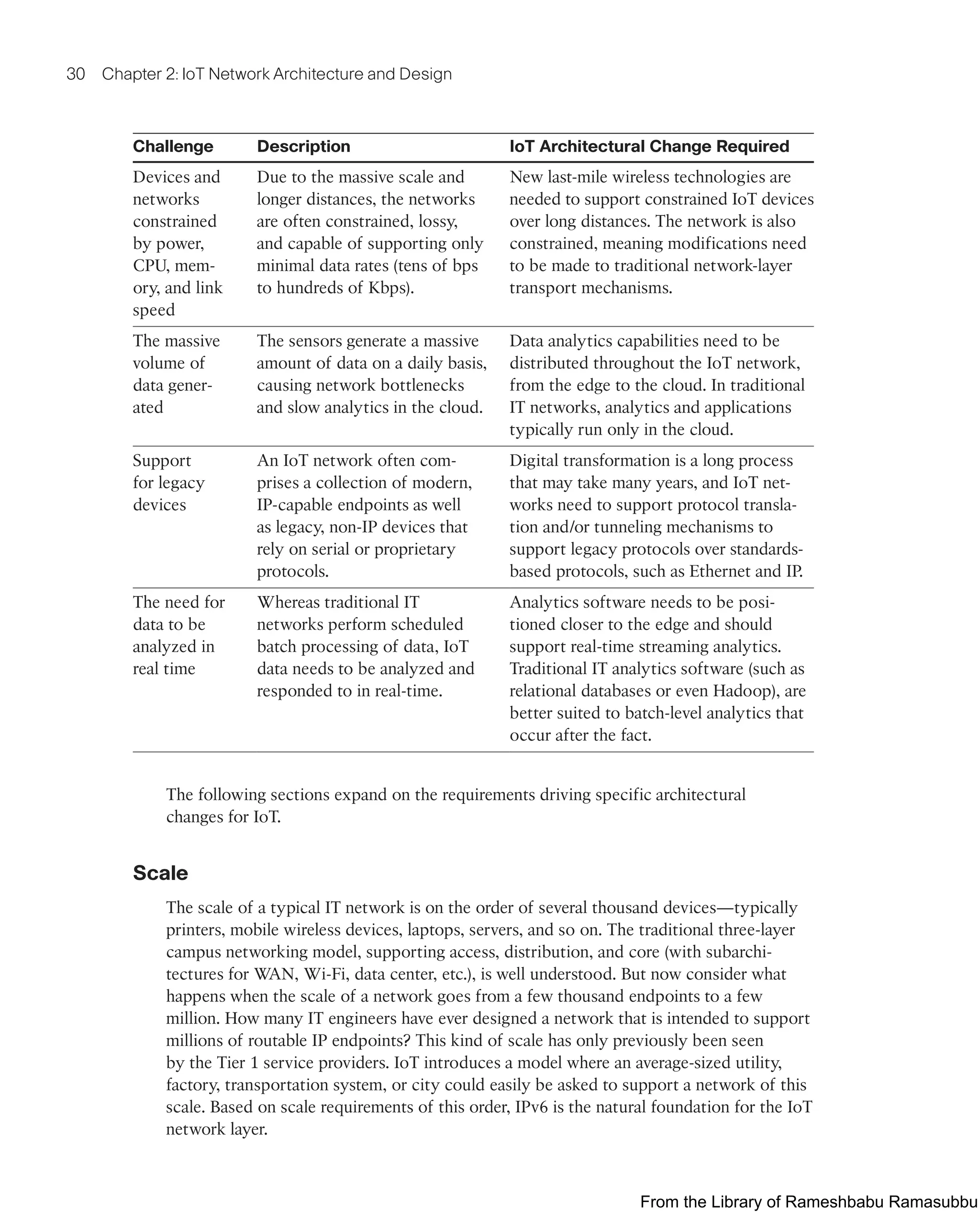
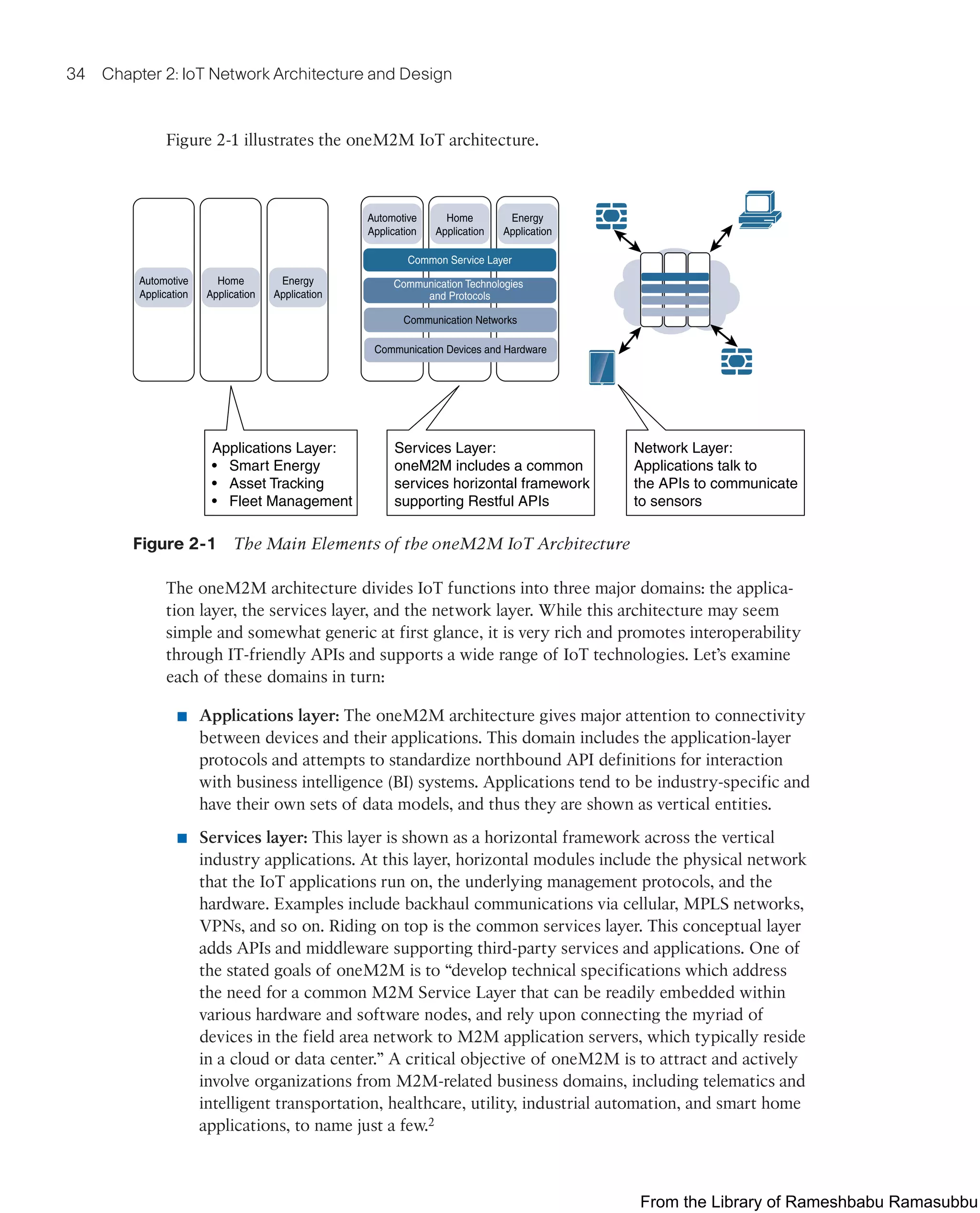
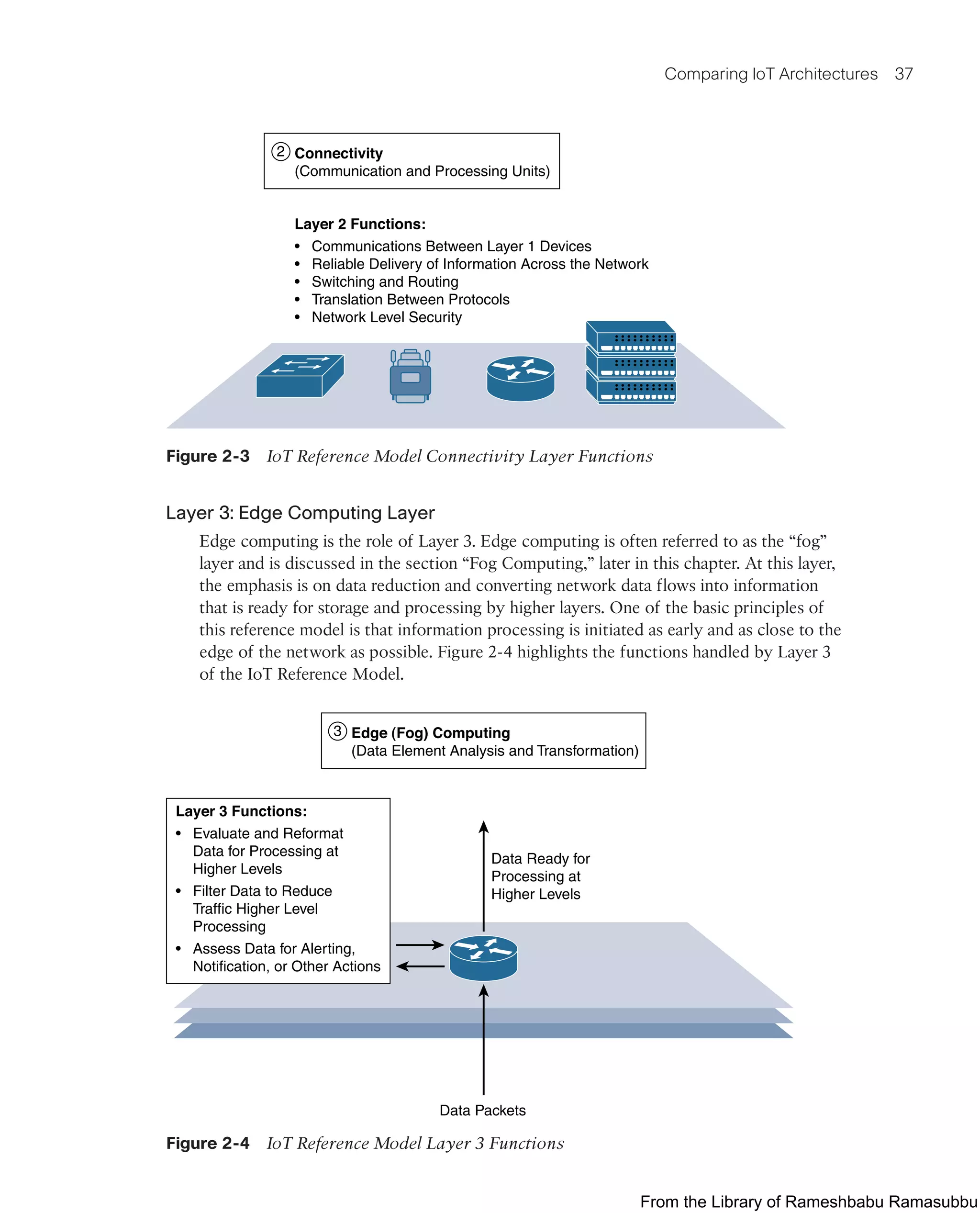
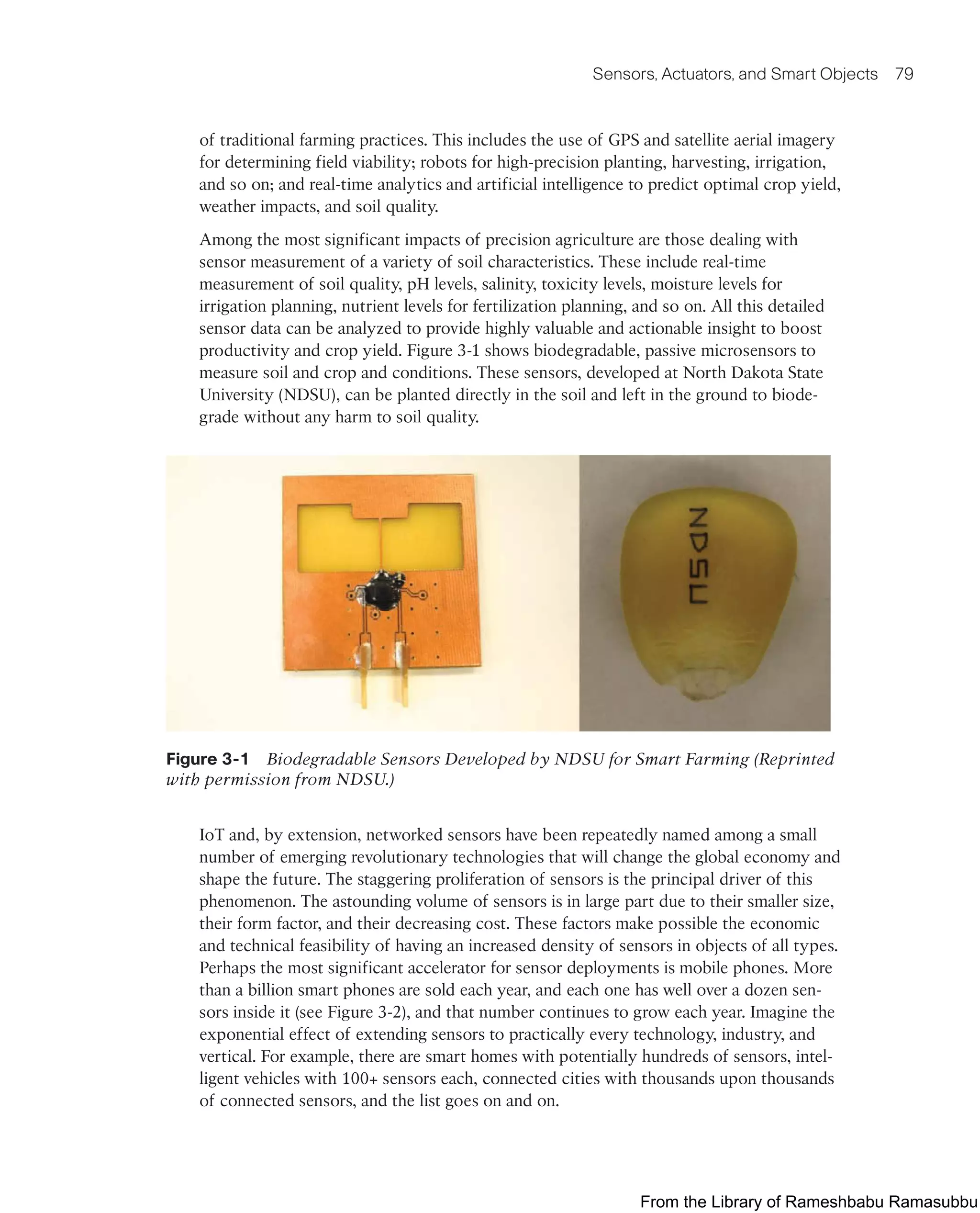
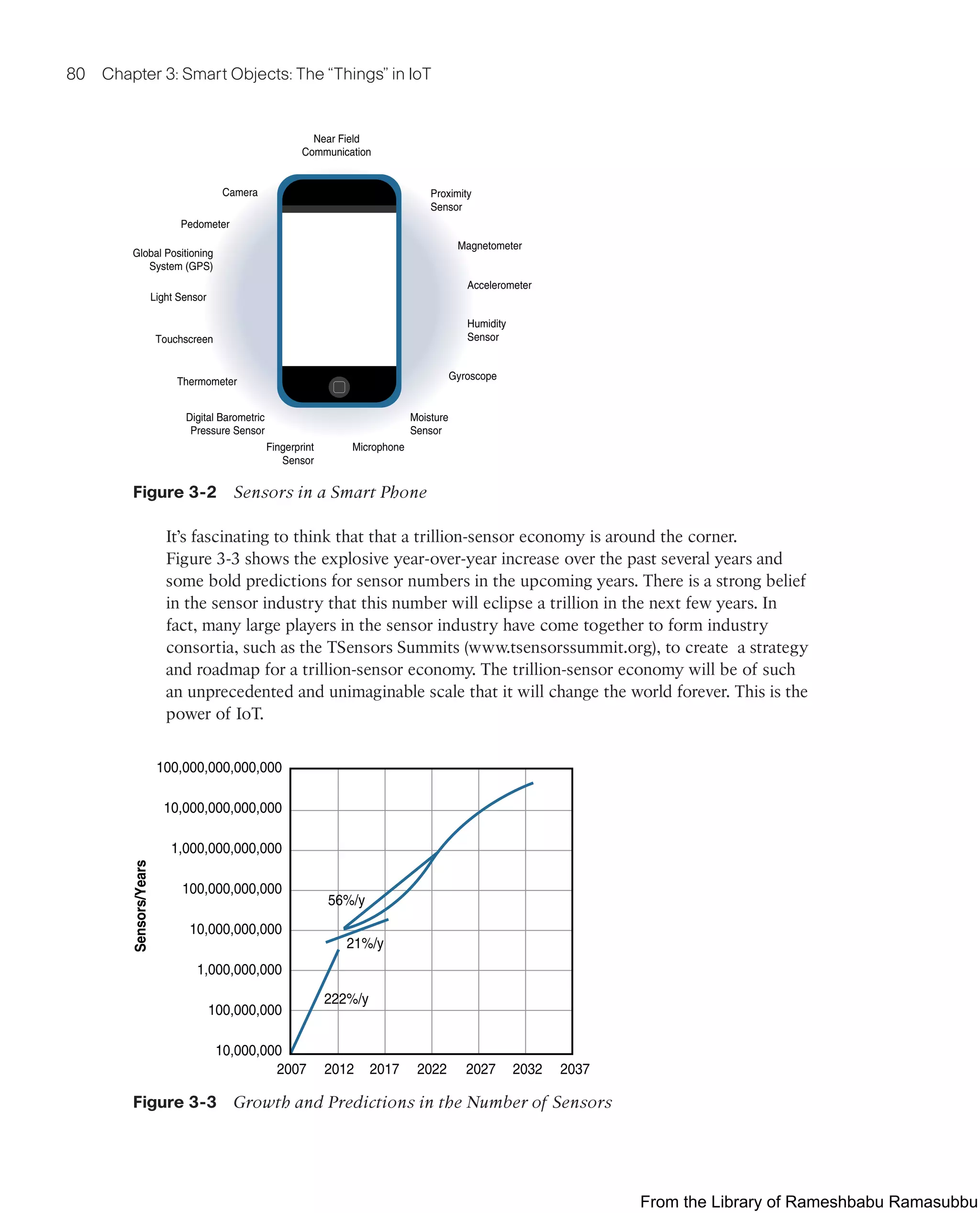
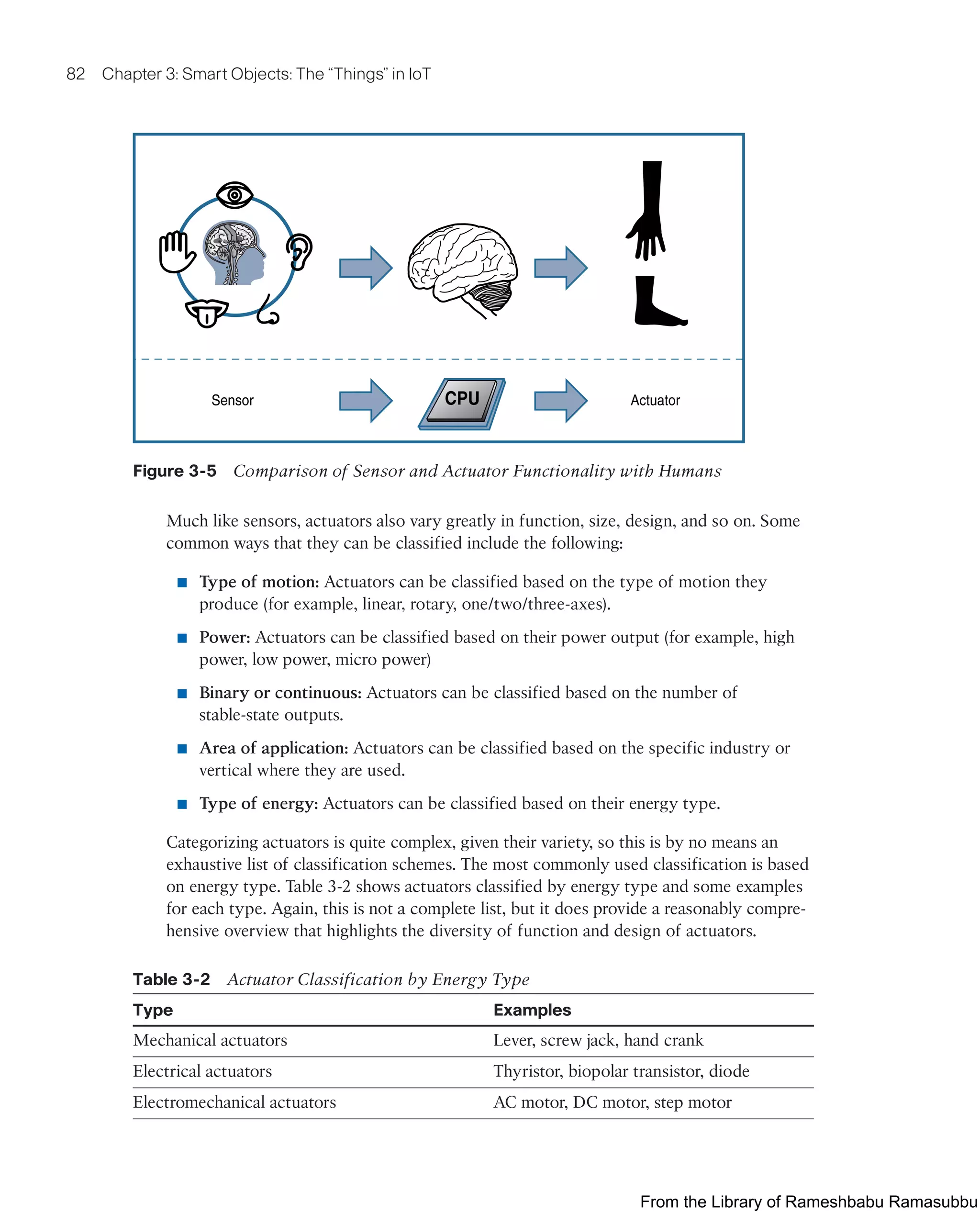
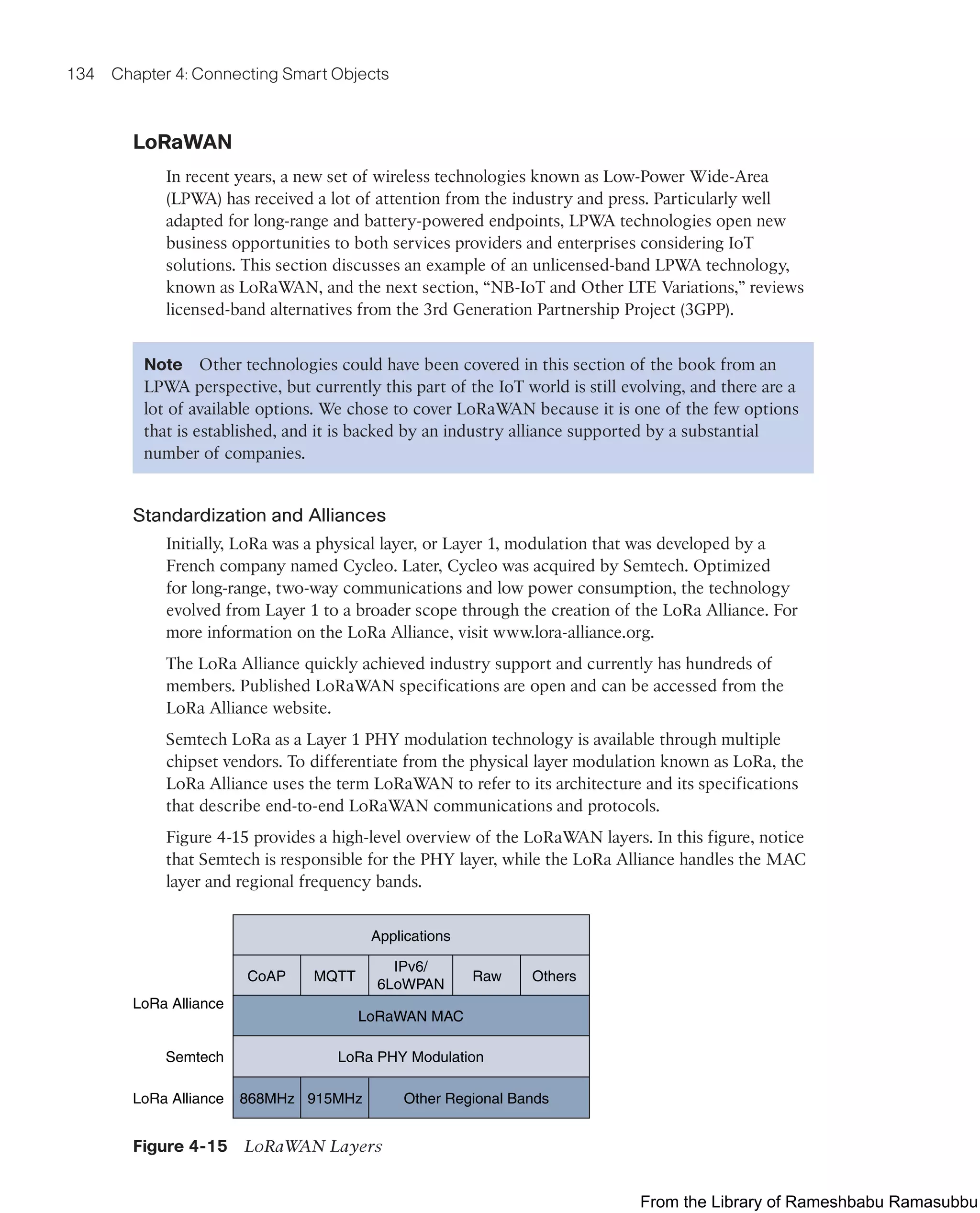
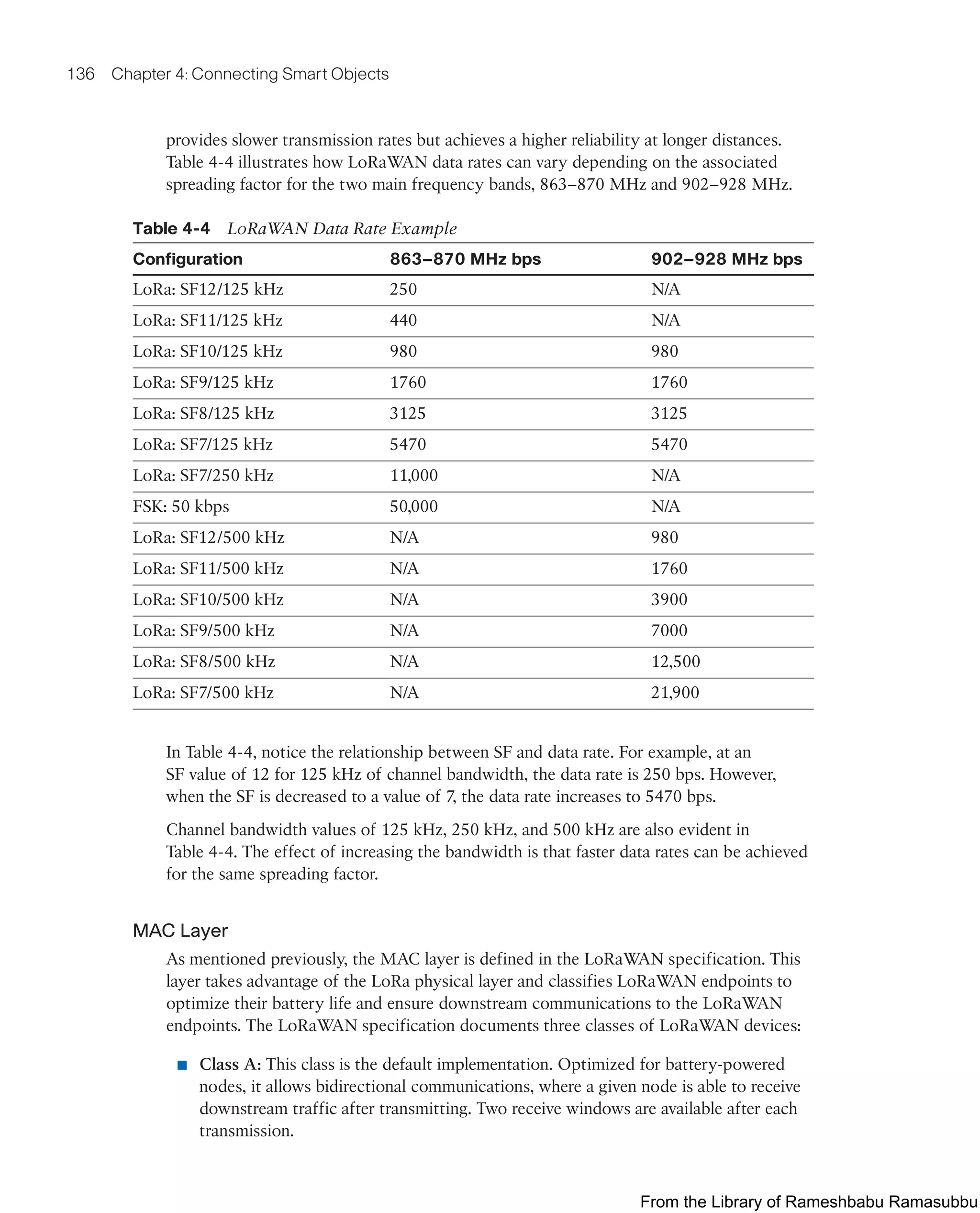
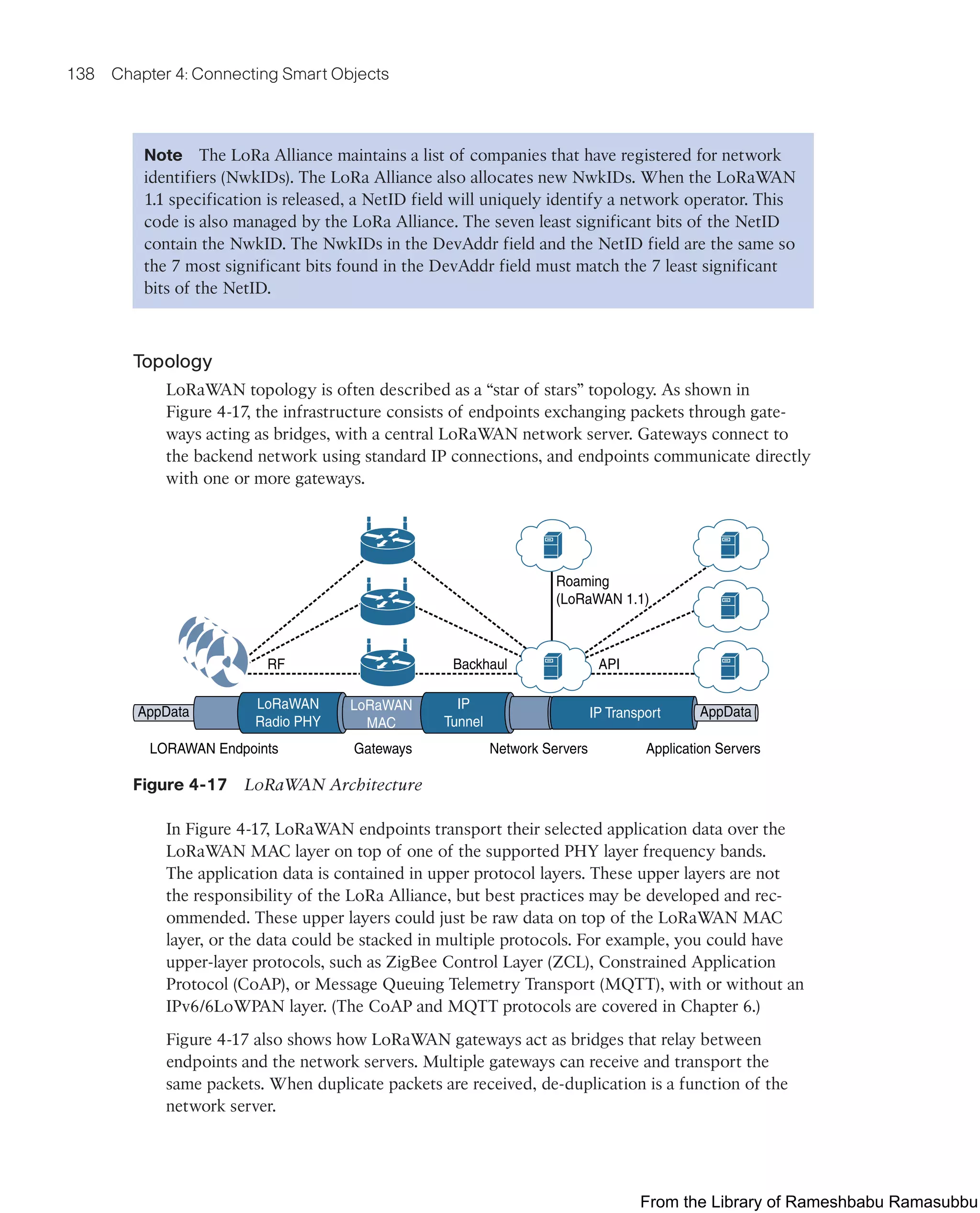
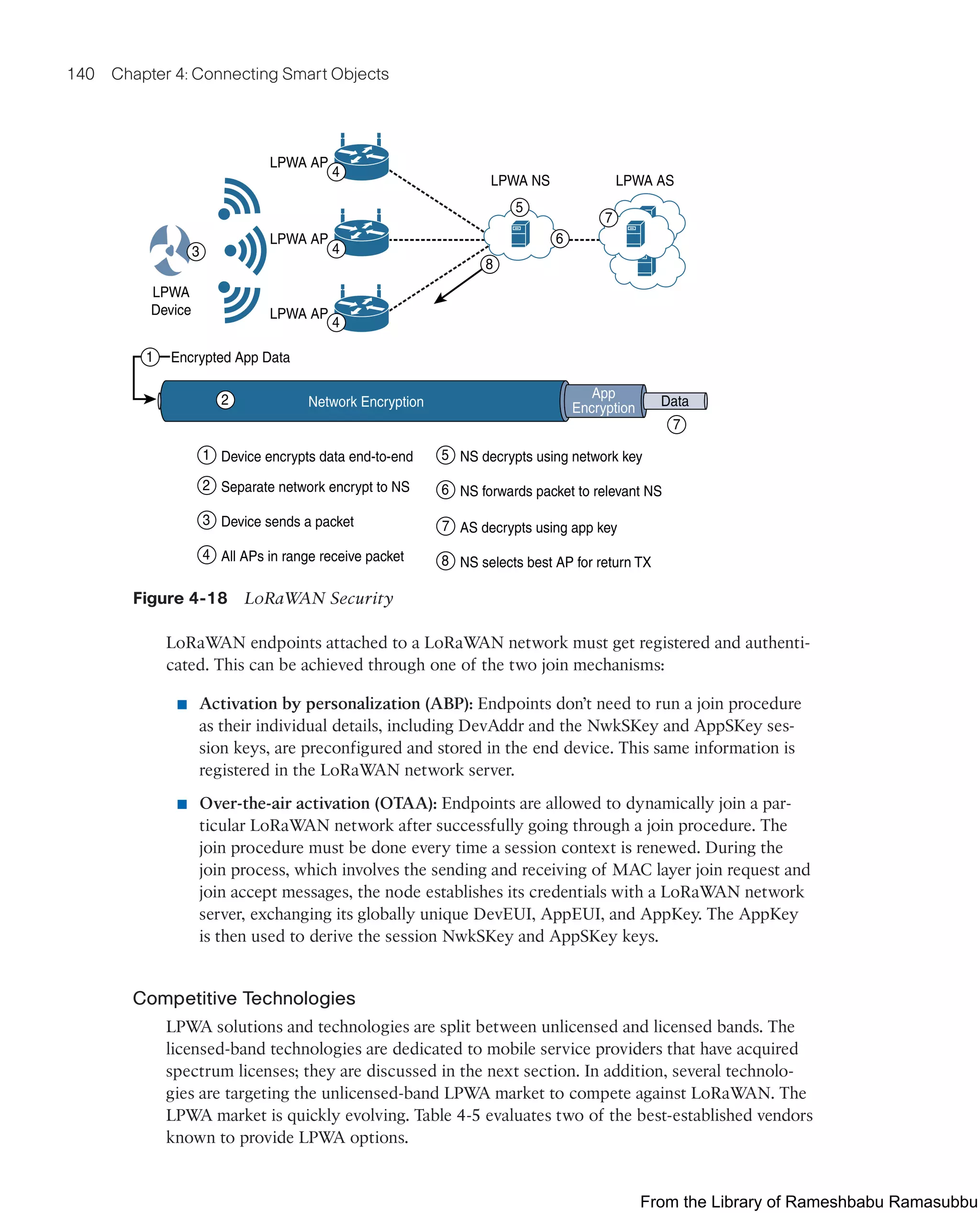
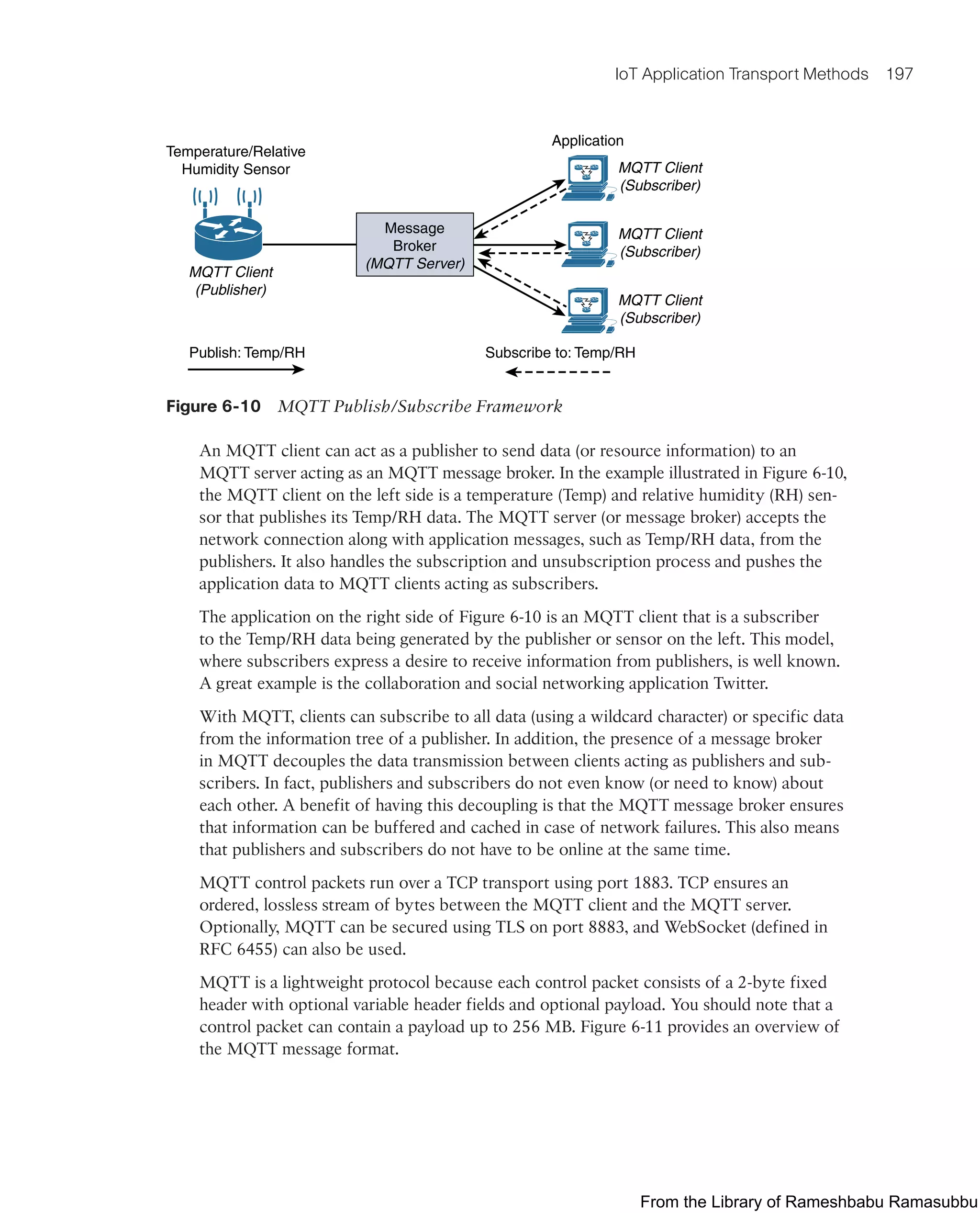
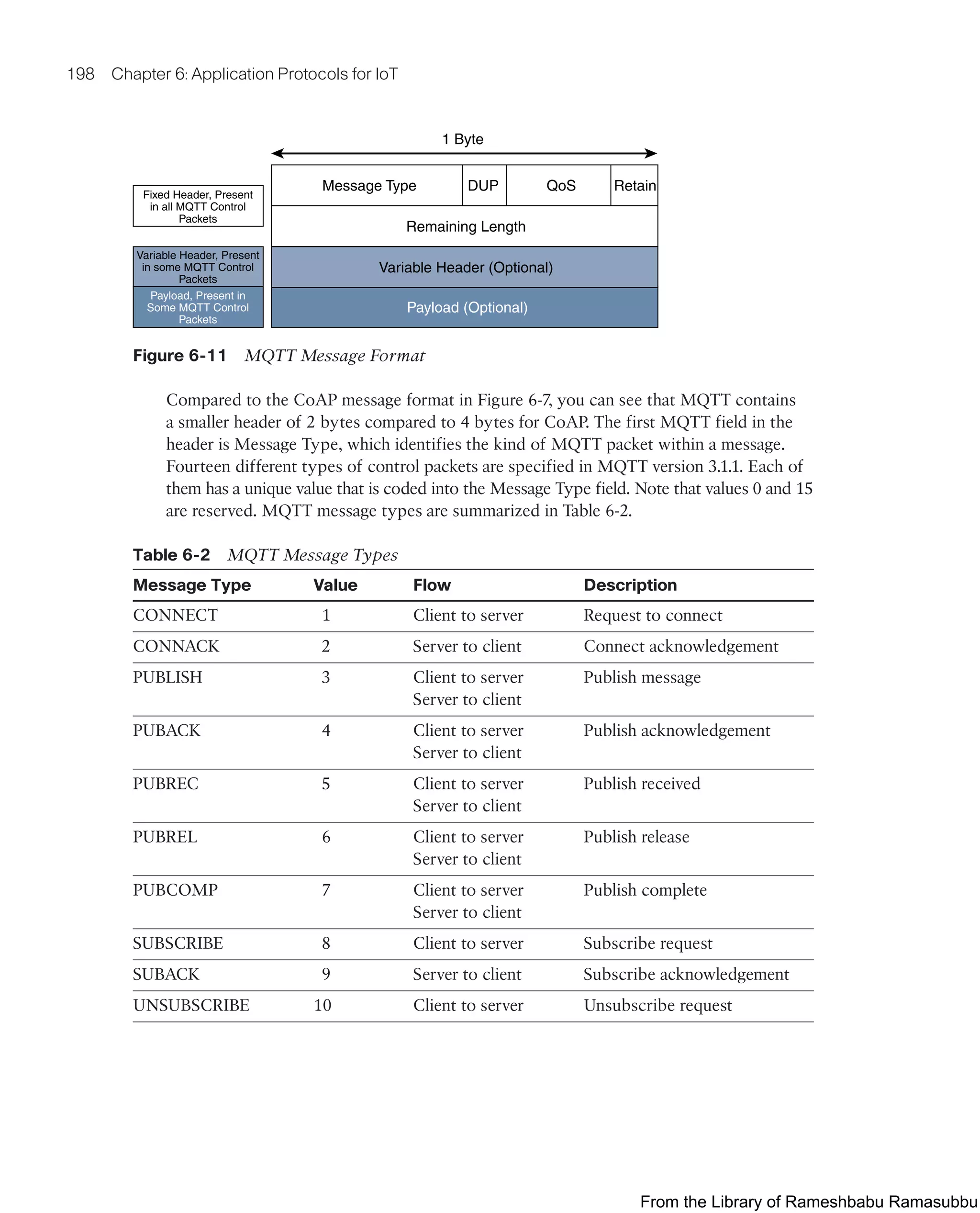
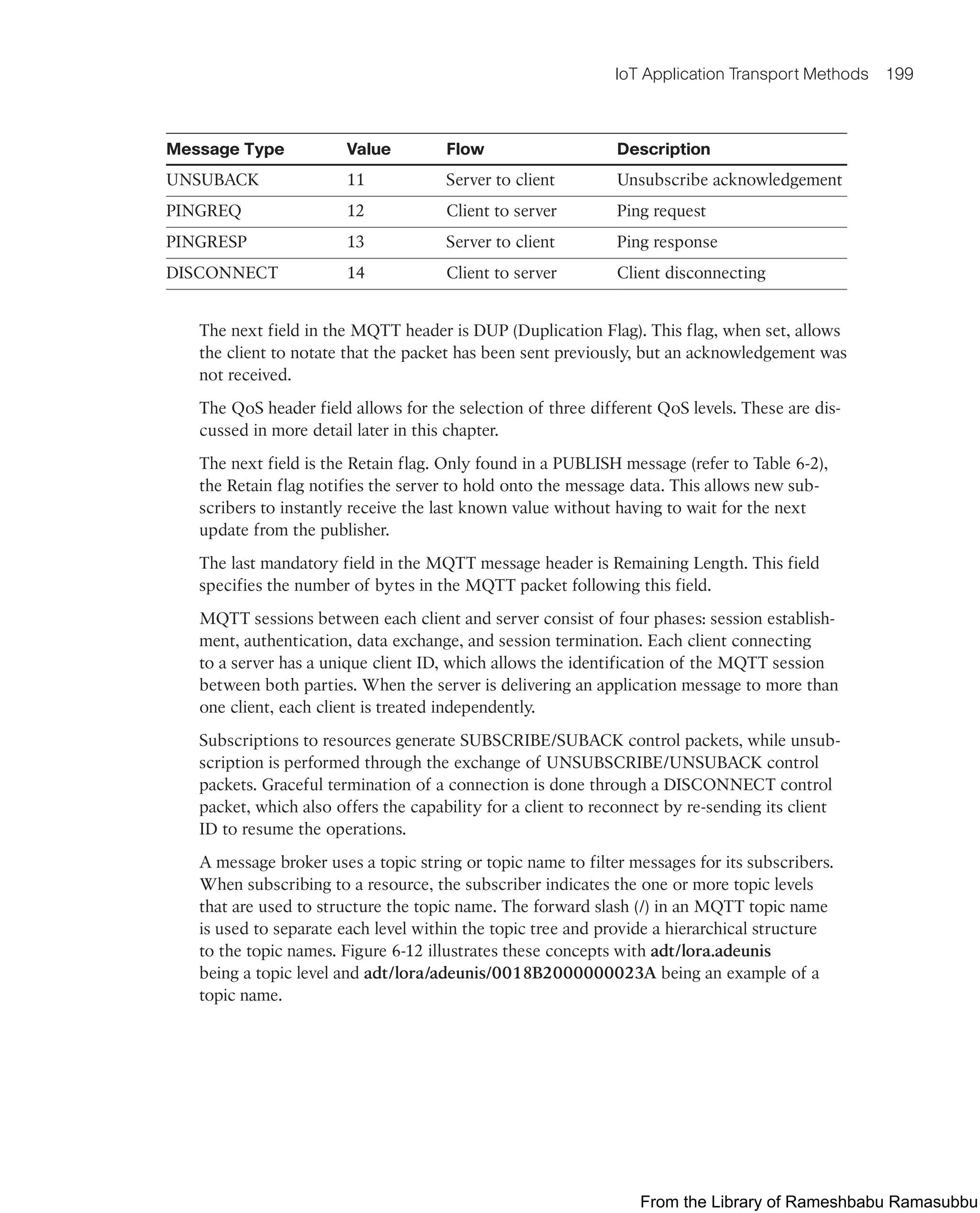
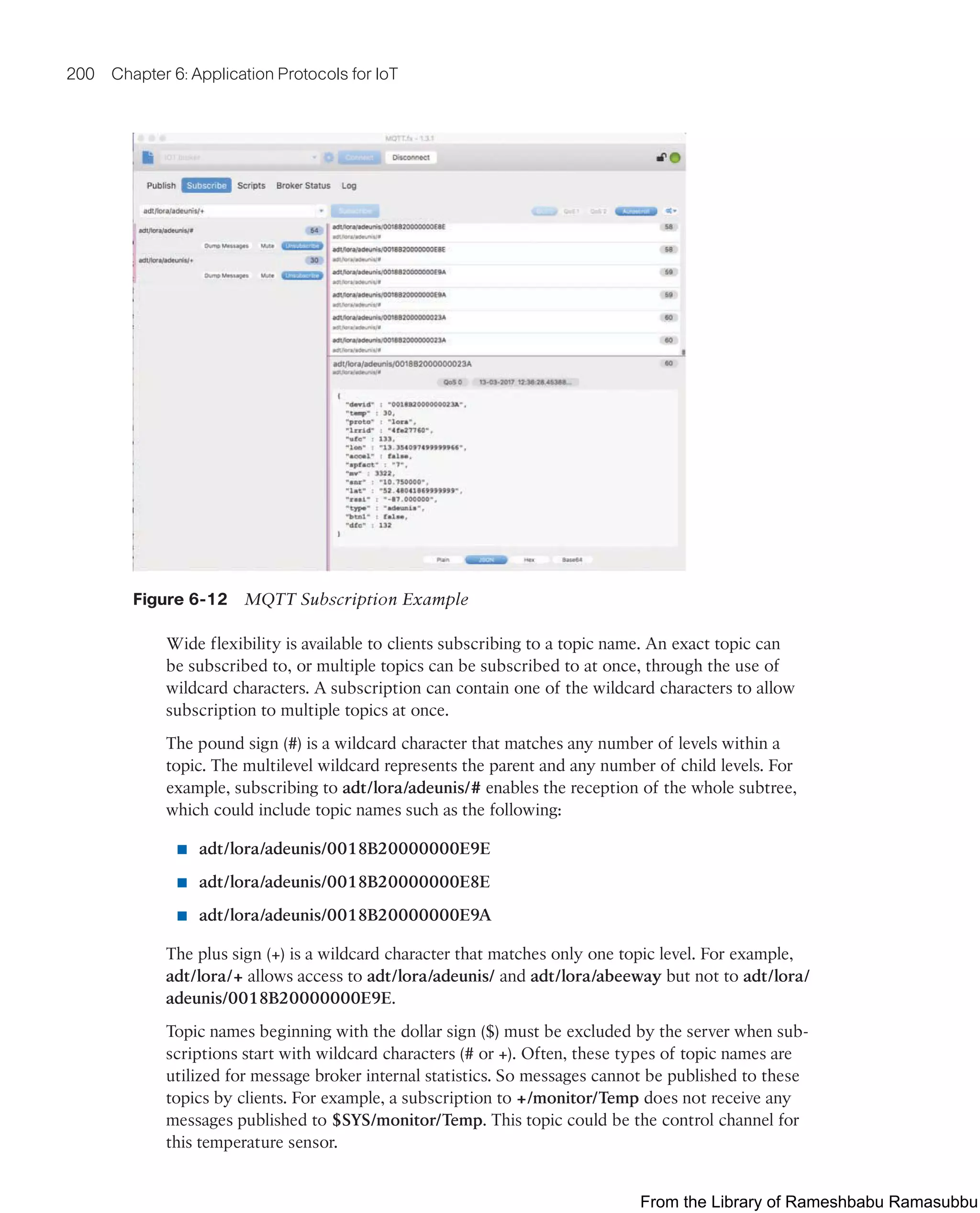
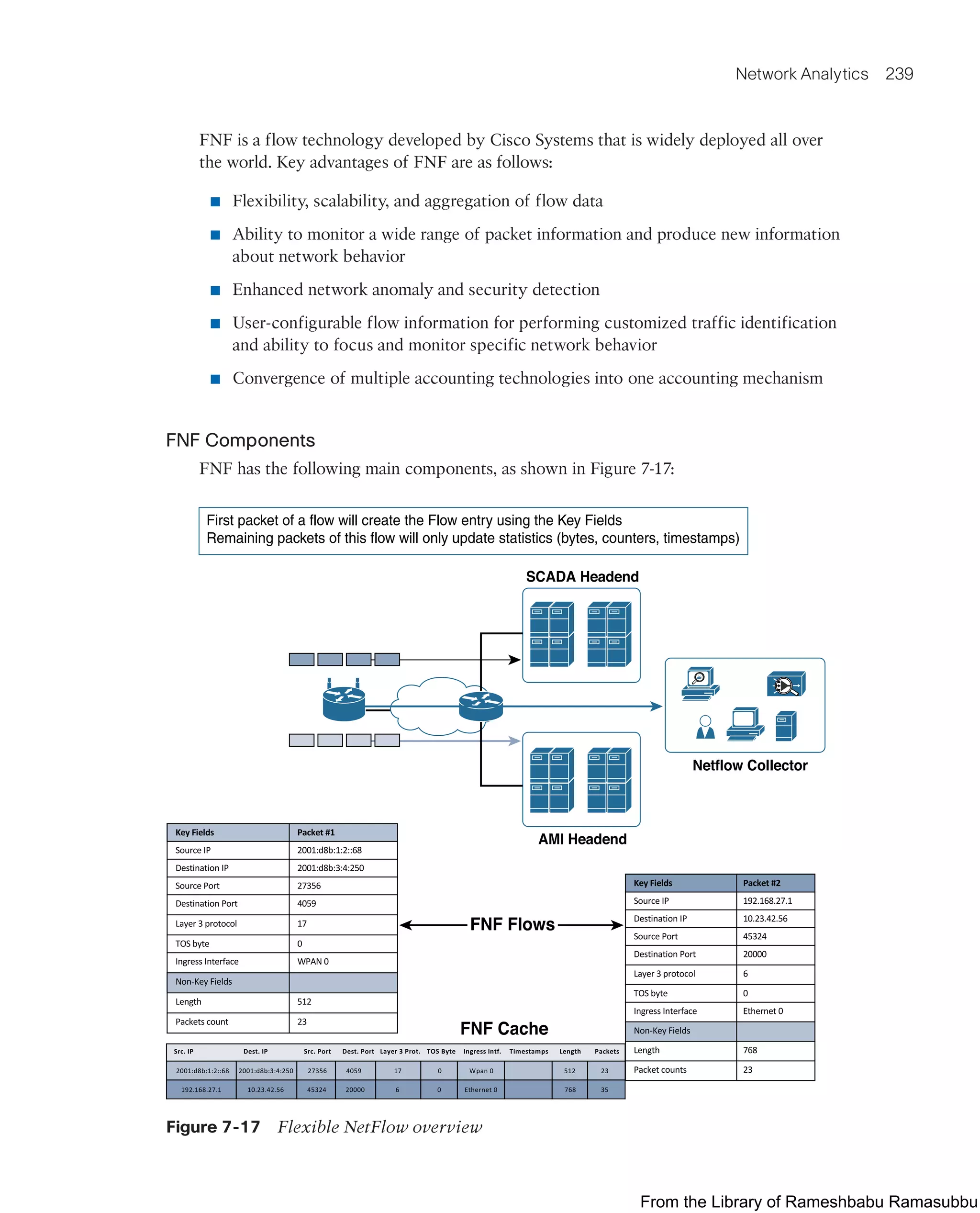
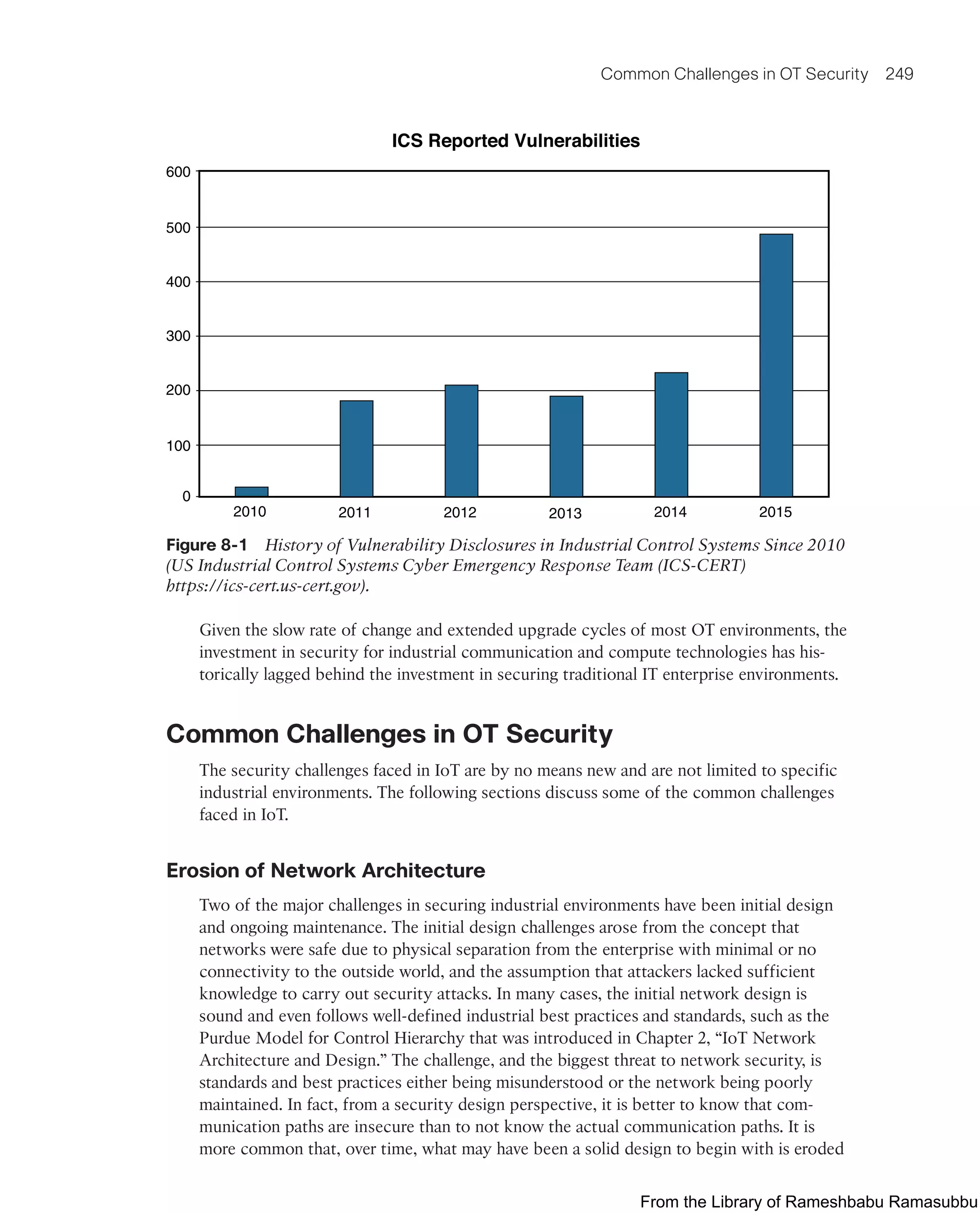
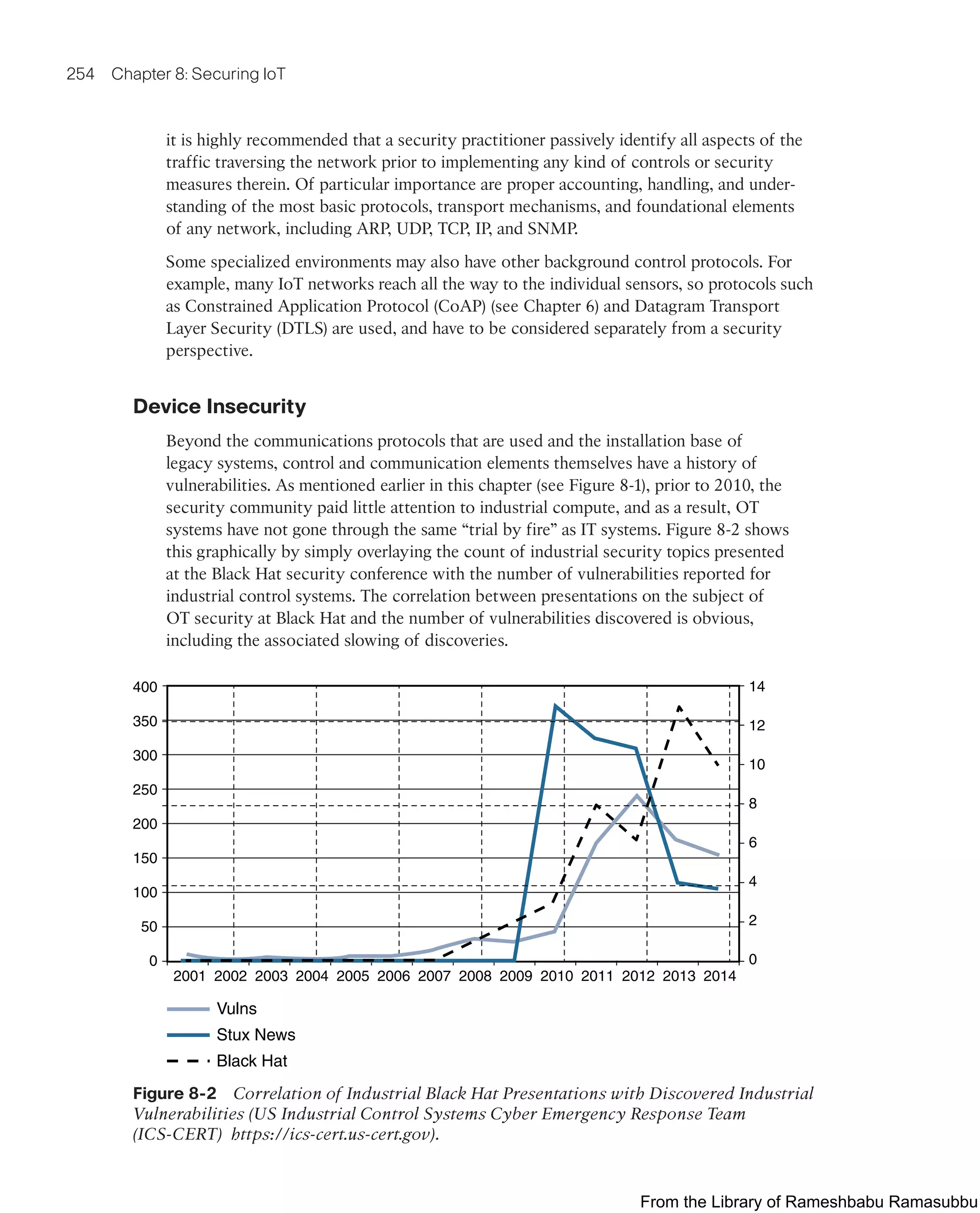
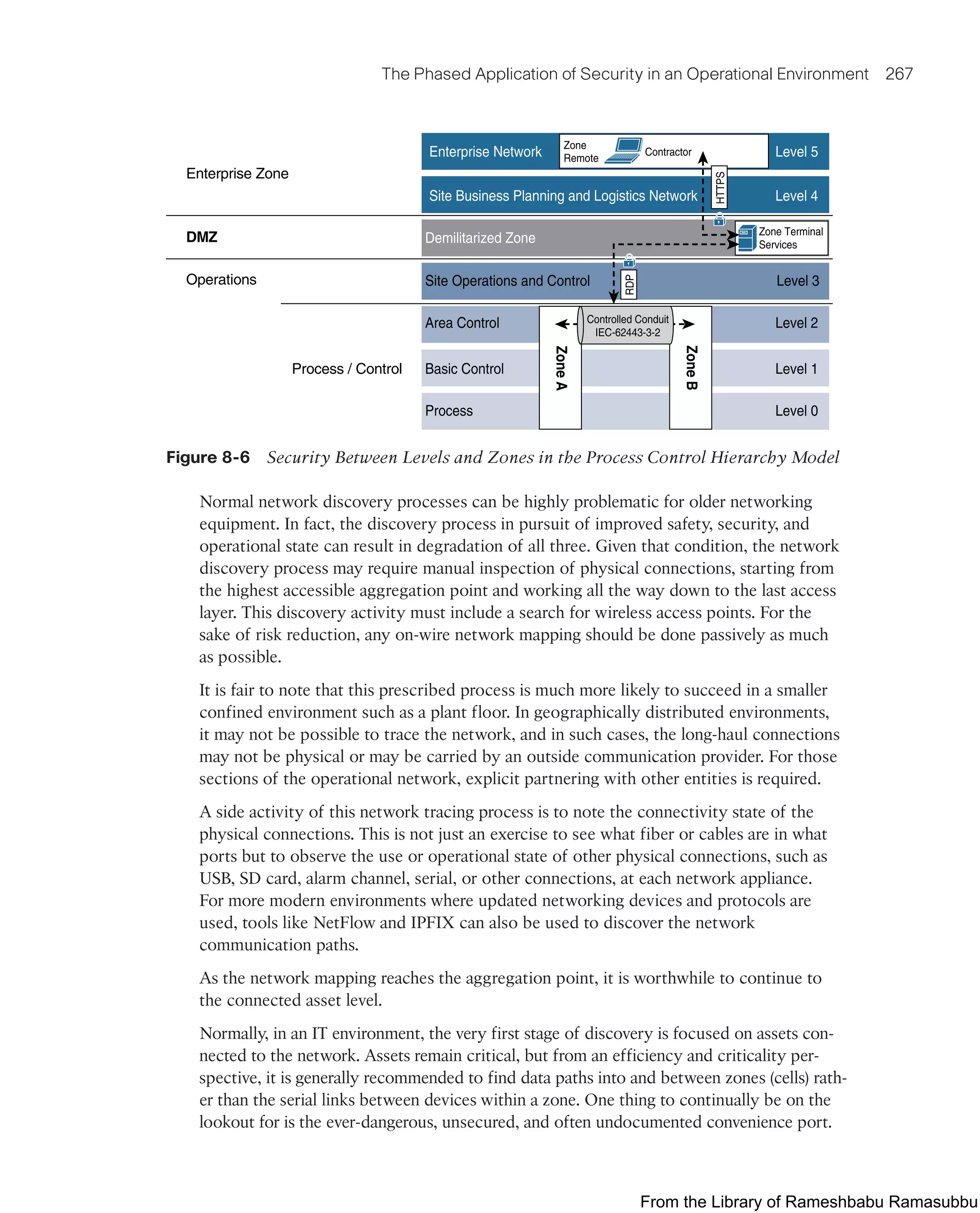
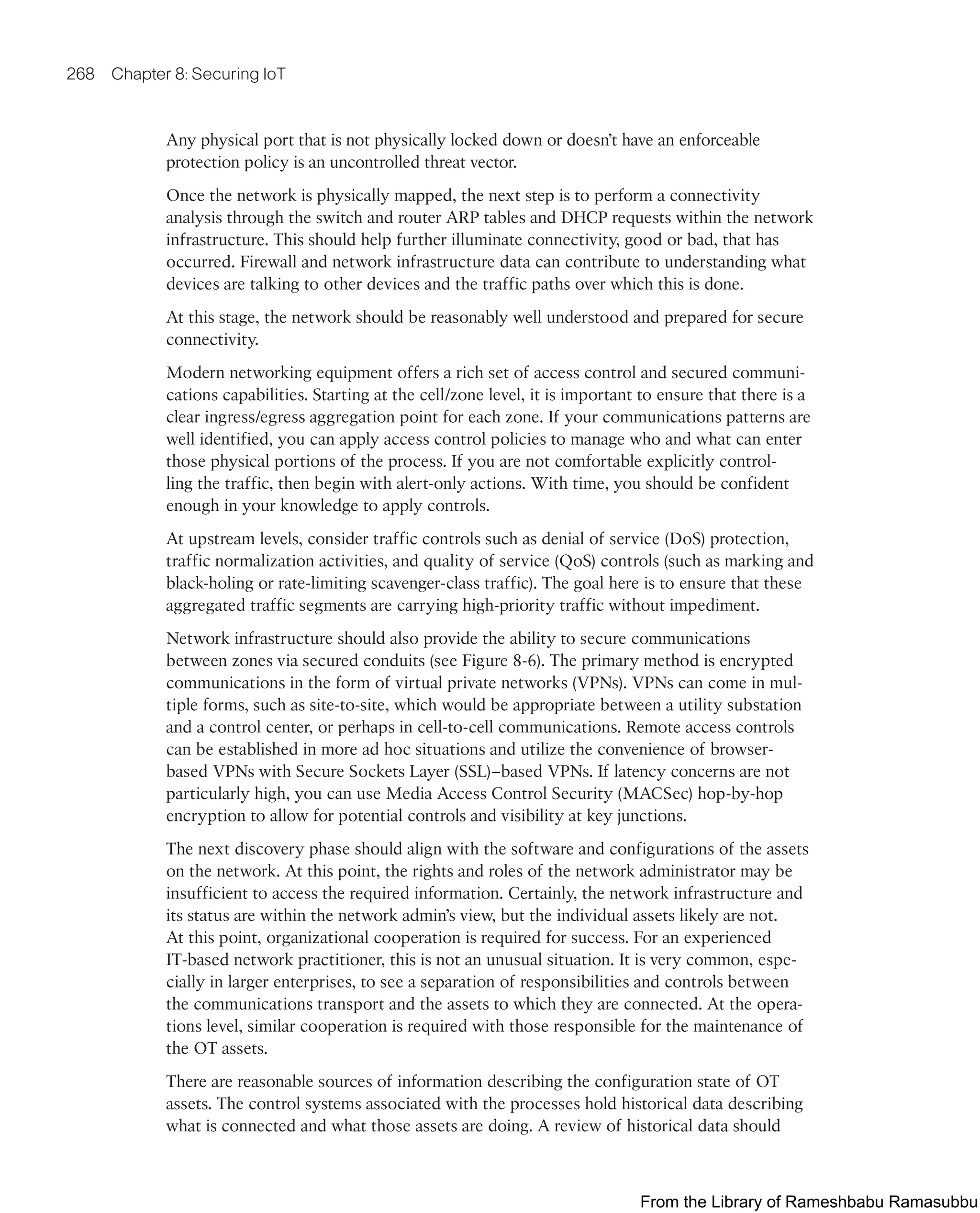
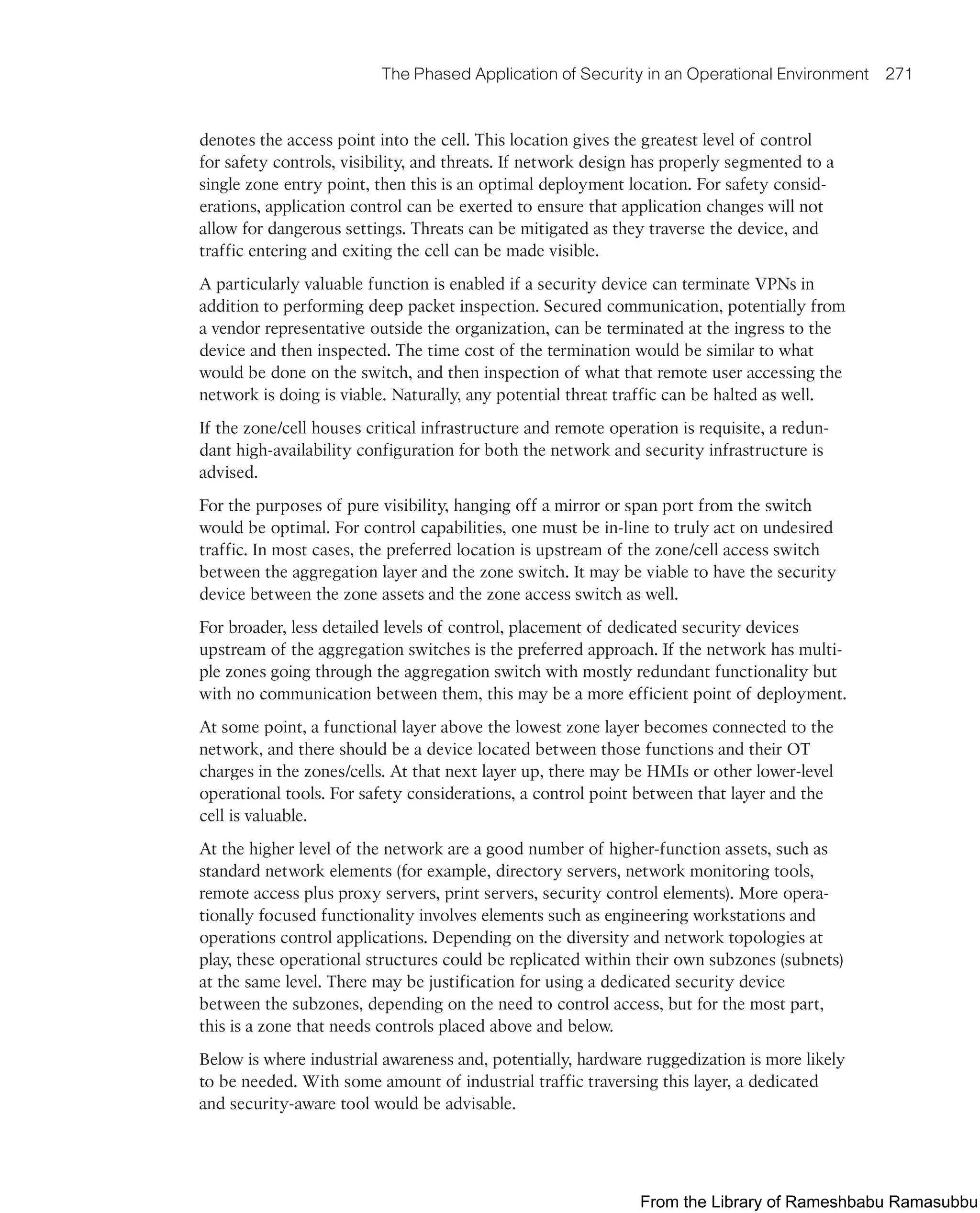
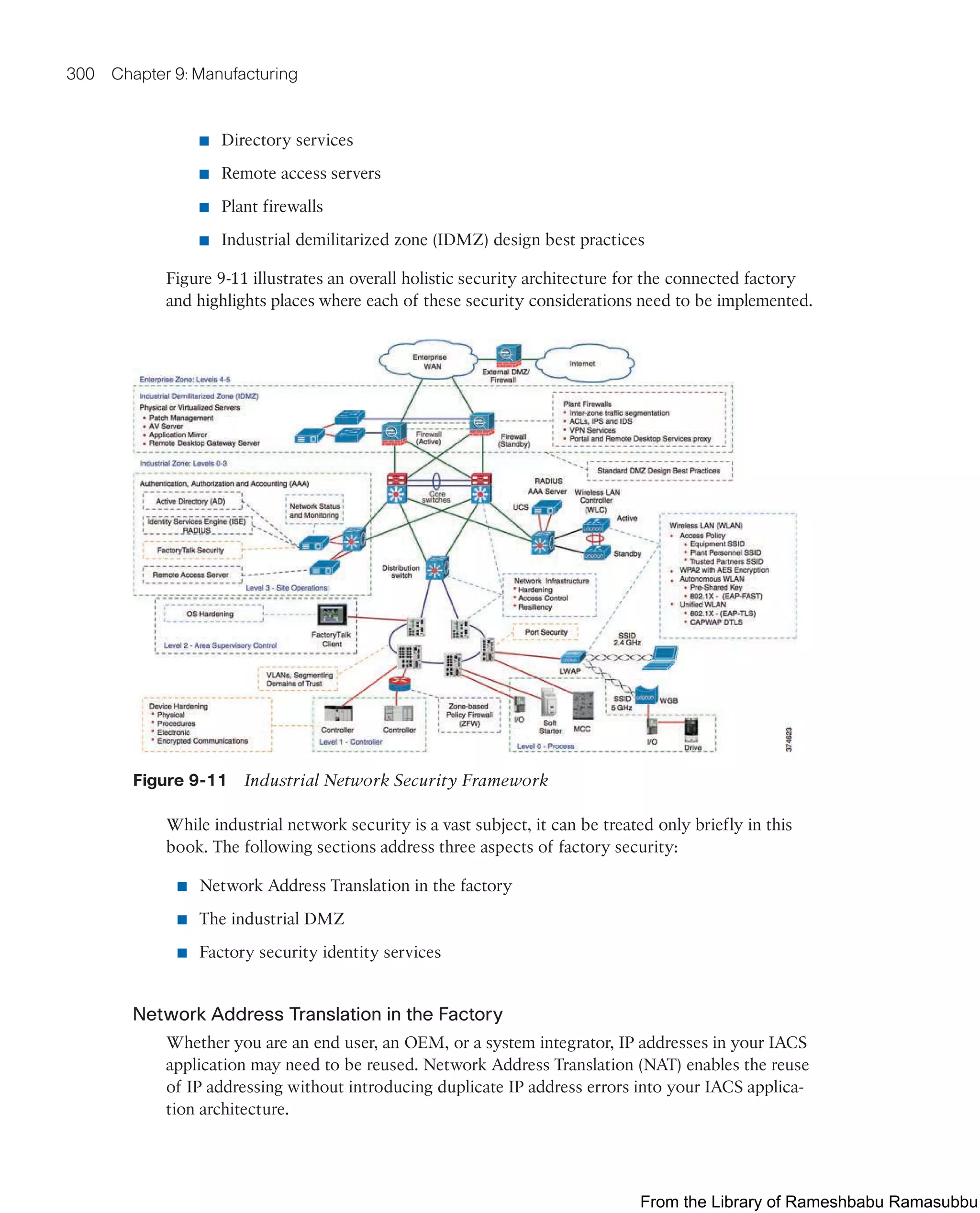
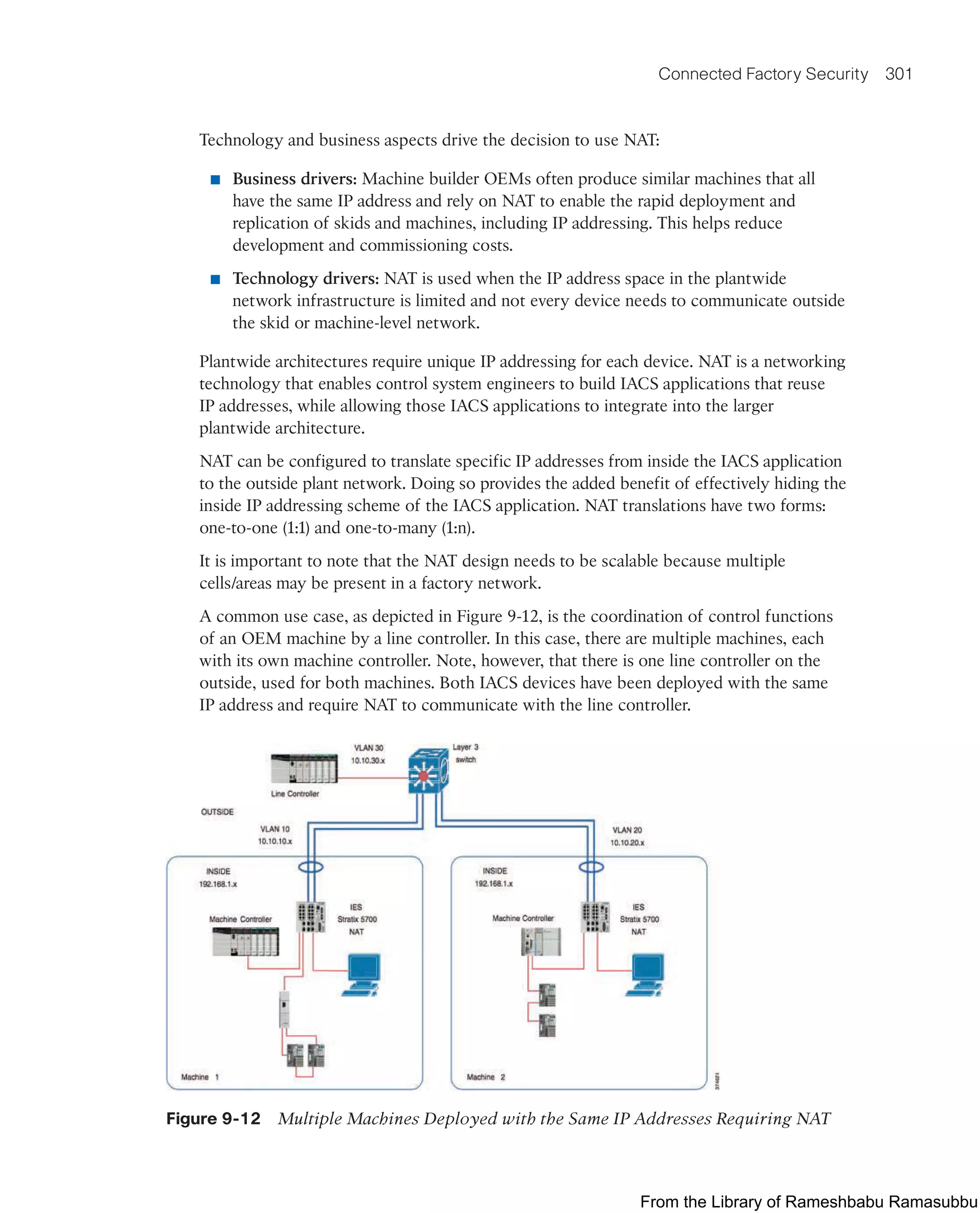
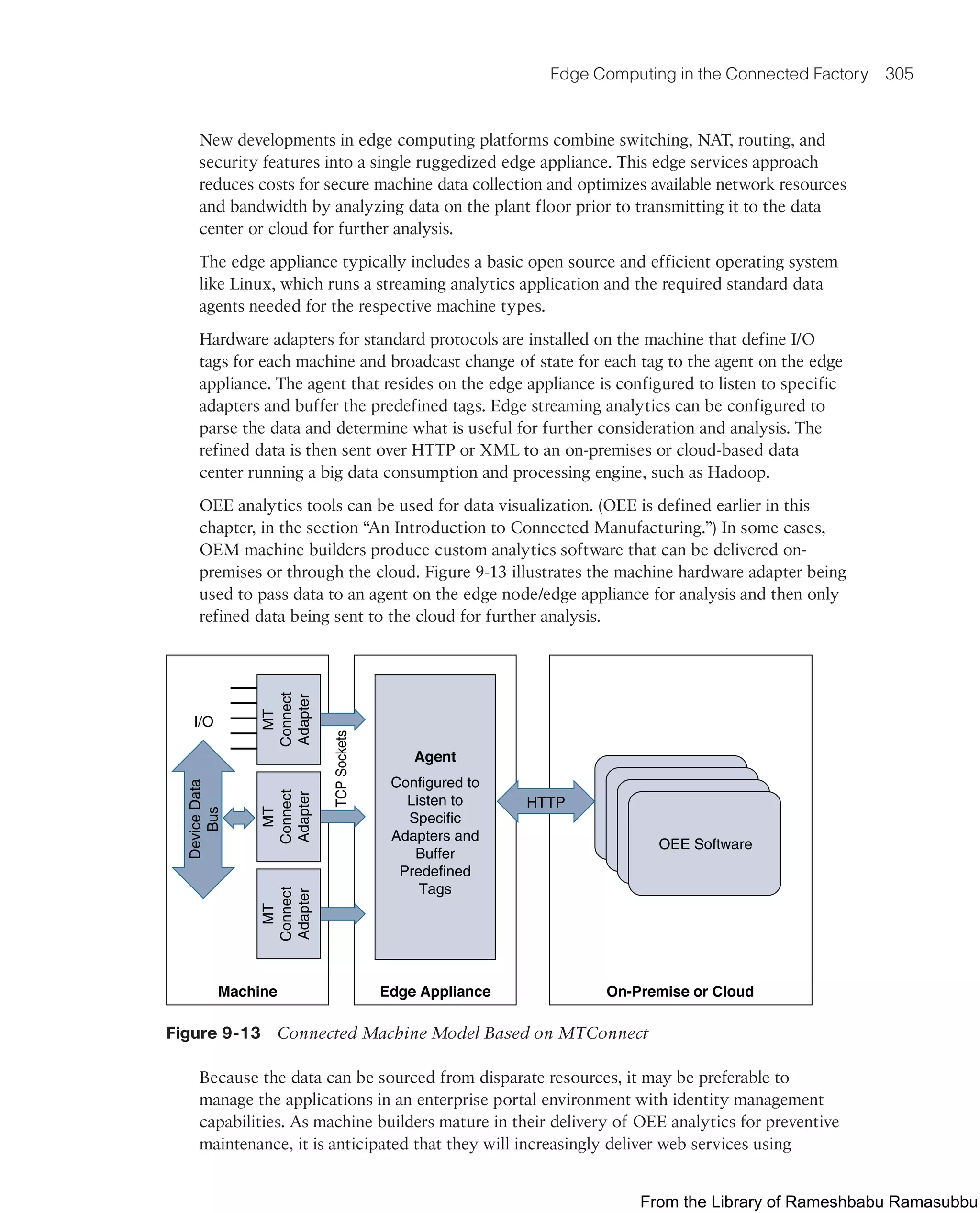
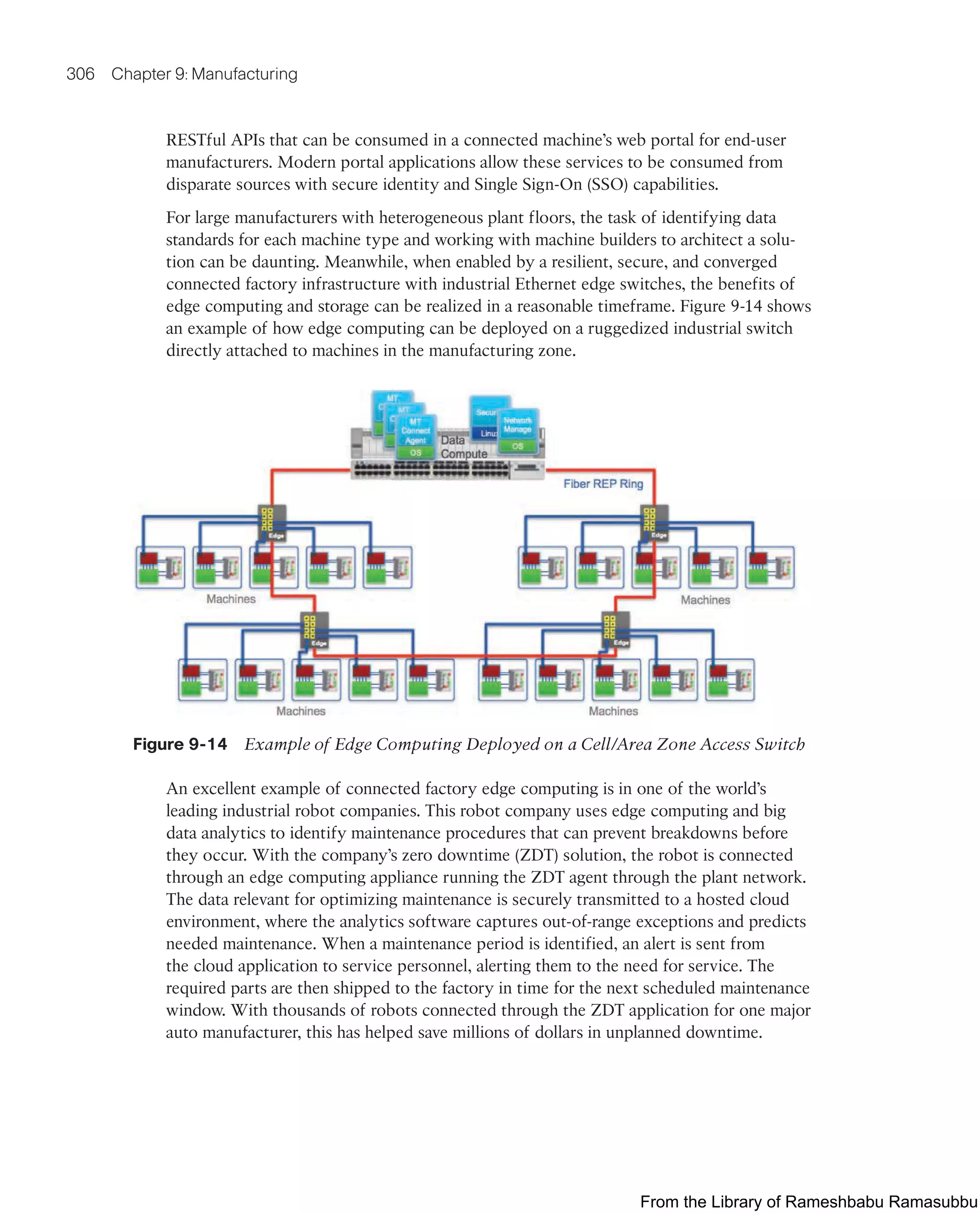
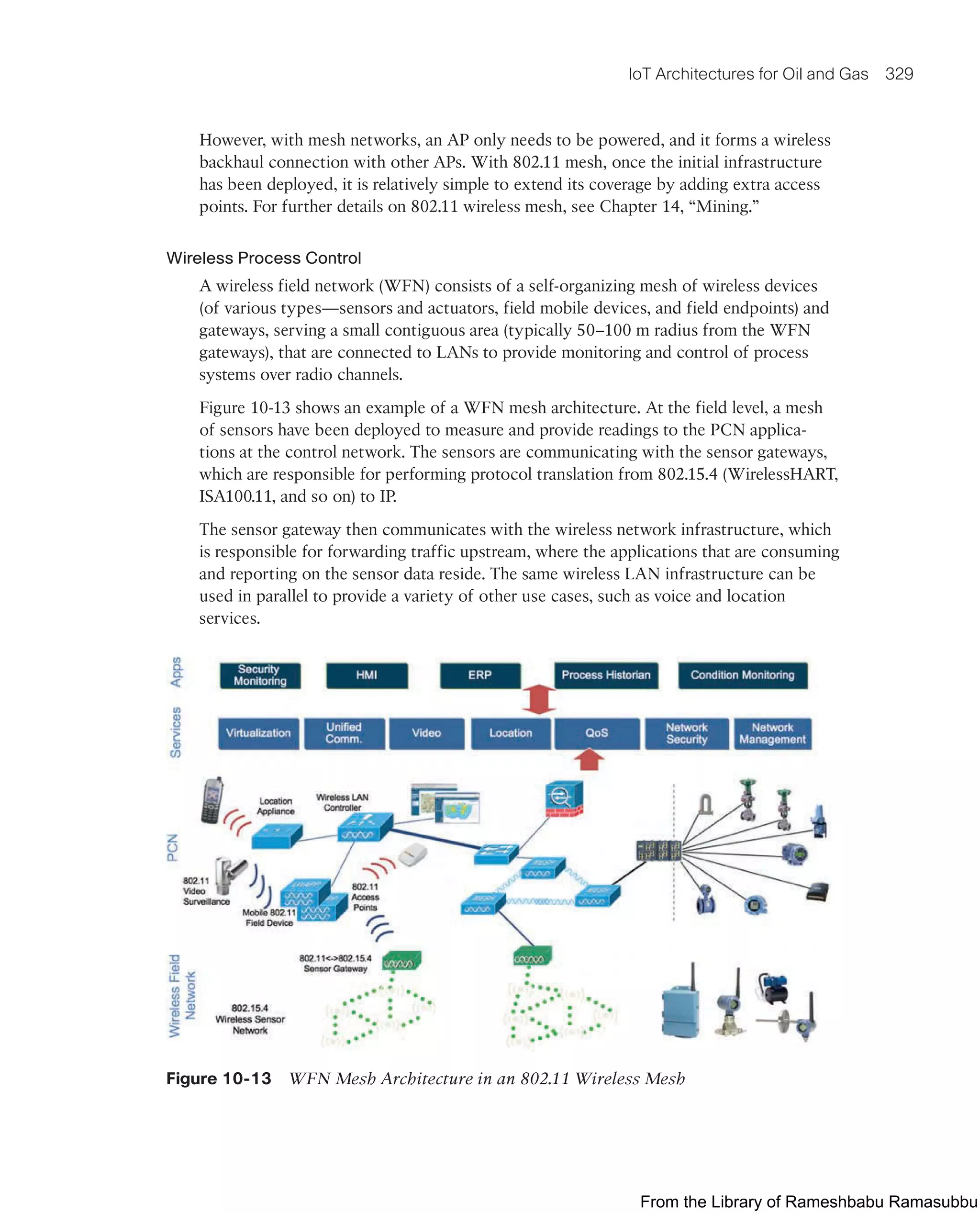
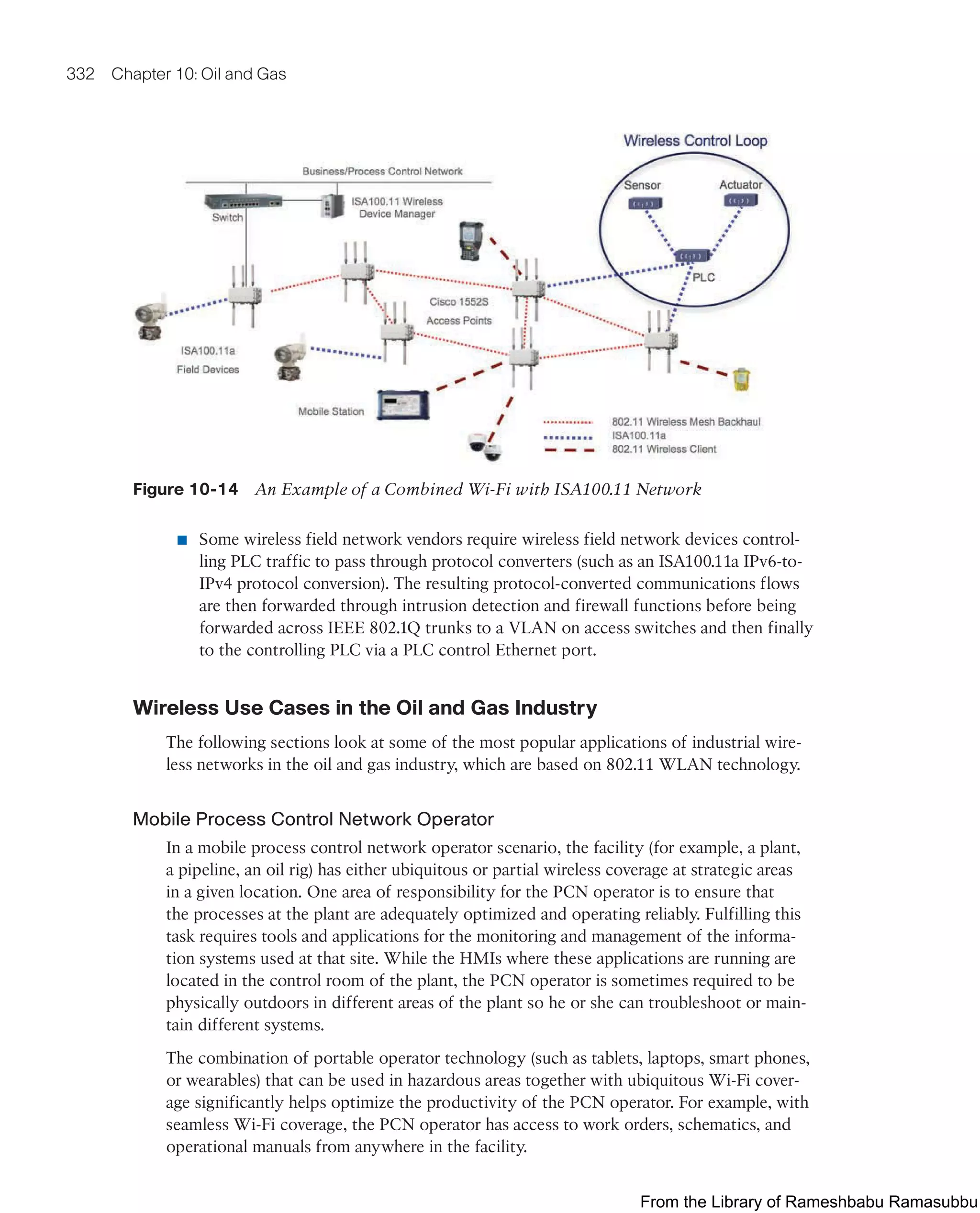
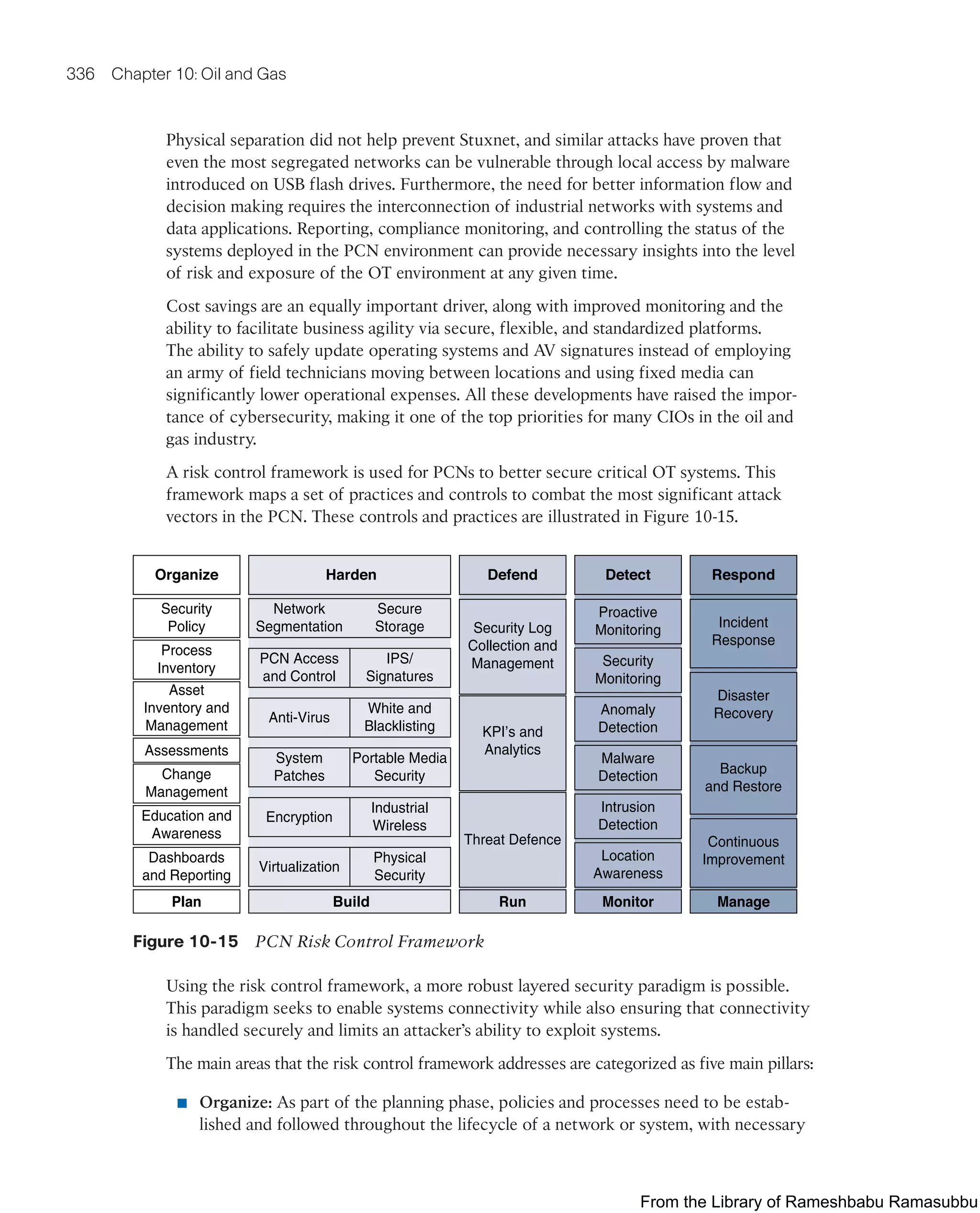
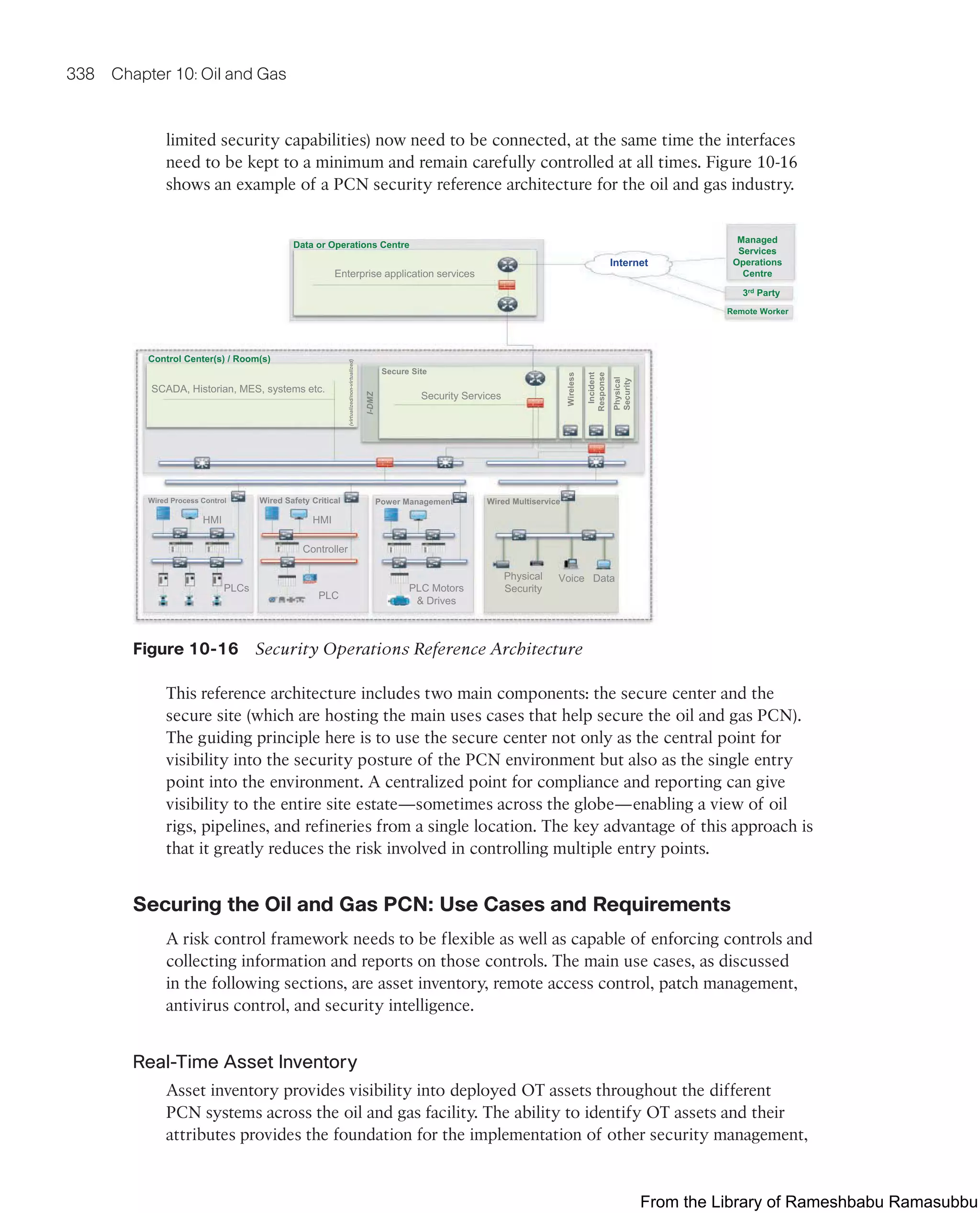
This document provides an overview of the book "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things" by David Hanes, Gonzalo Salgueiro, Patrick Grossetete, Robert Barton, and Jerome Henry. The book covers core IoT technologies including networking, protocols, and use cases. It is published by Cisco Press and copyrighted in 2017.























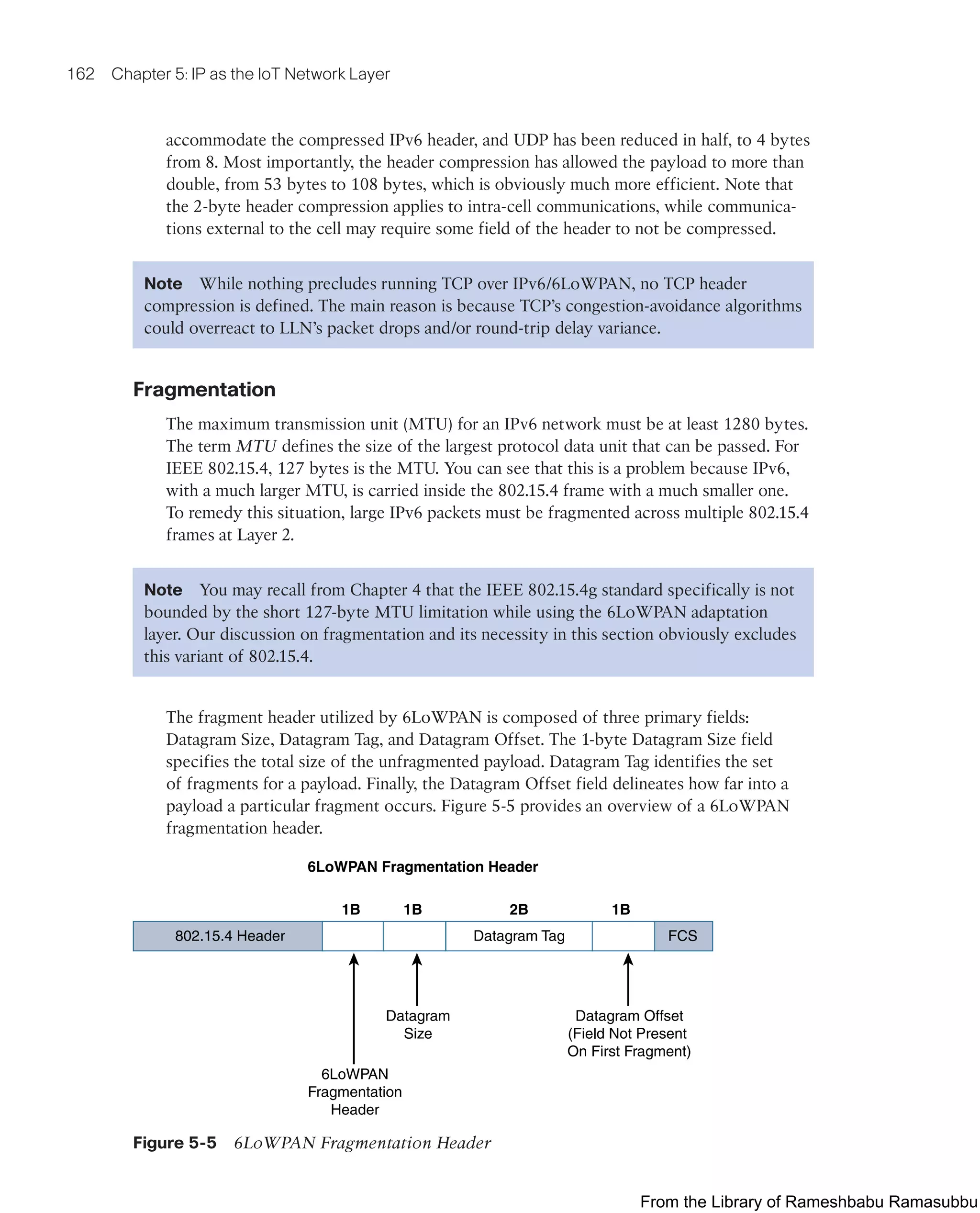
![xxv
Icons Used in This Book
Router Switch Cloud File/
Application Server
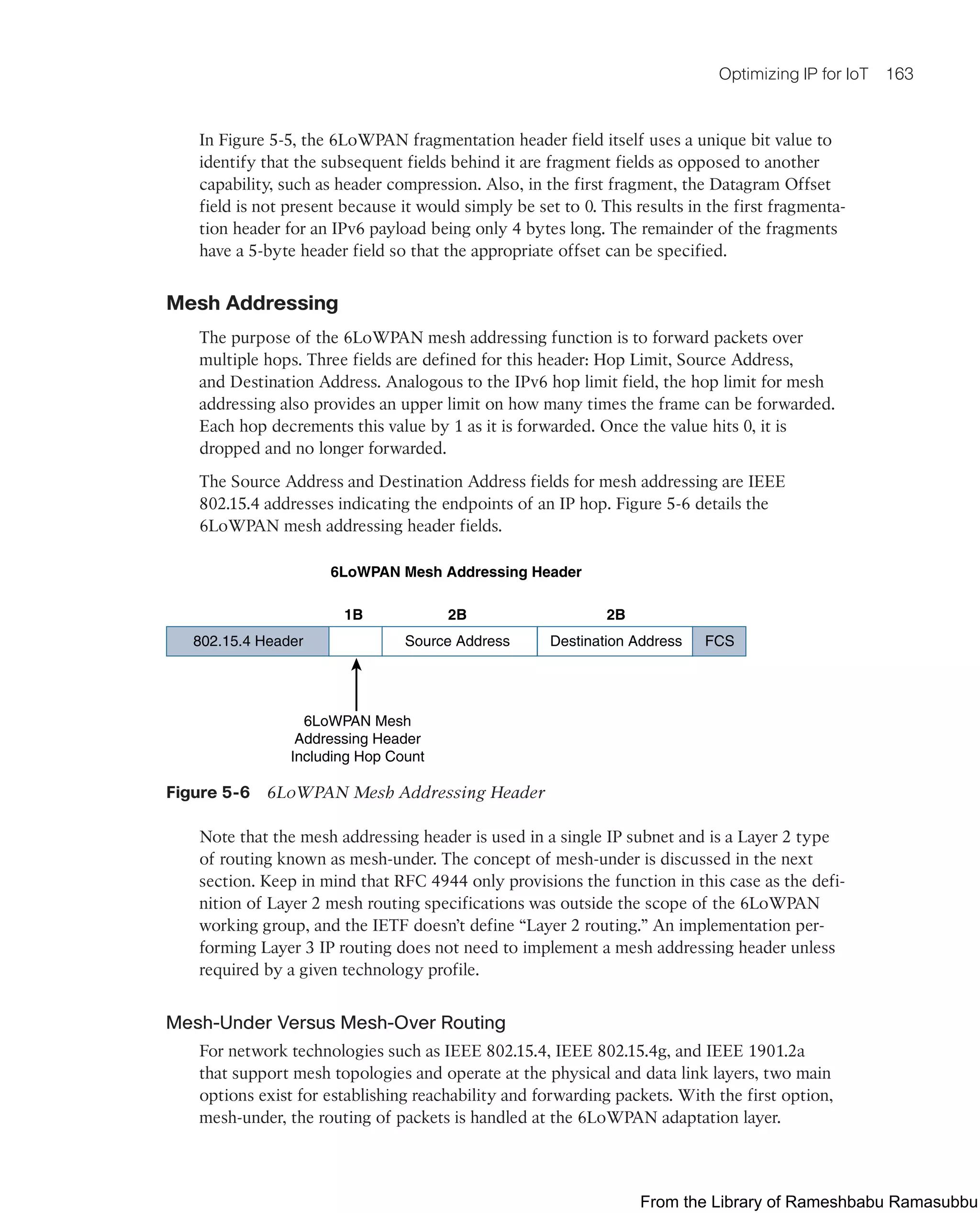
Command Syntax Conventions
The conventions used to present command syntax in this book are the same conventions
used in the IOS Command Reference. The Command Reference describes these
conventions as follows:
■ Boldface indicates commands and keywords that are entered literally as shown. In
actual configuration examples and output (not general command syntax), boldface
indicates commands that are manually input by the user (such as a show command).
■ Italic indicates arguments for which you supply actual values.
■ Vertical bars (|) separate alternative, mutually exclusive elements.
■ Square brackets ([ ]) indicate an optional element.
■ Braces ({ }) indicate a required choice.
■ Braces within brackets ([{ }]) indicate a required choice within an optional element.
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-26-2048.jpg)













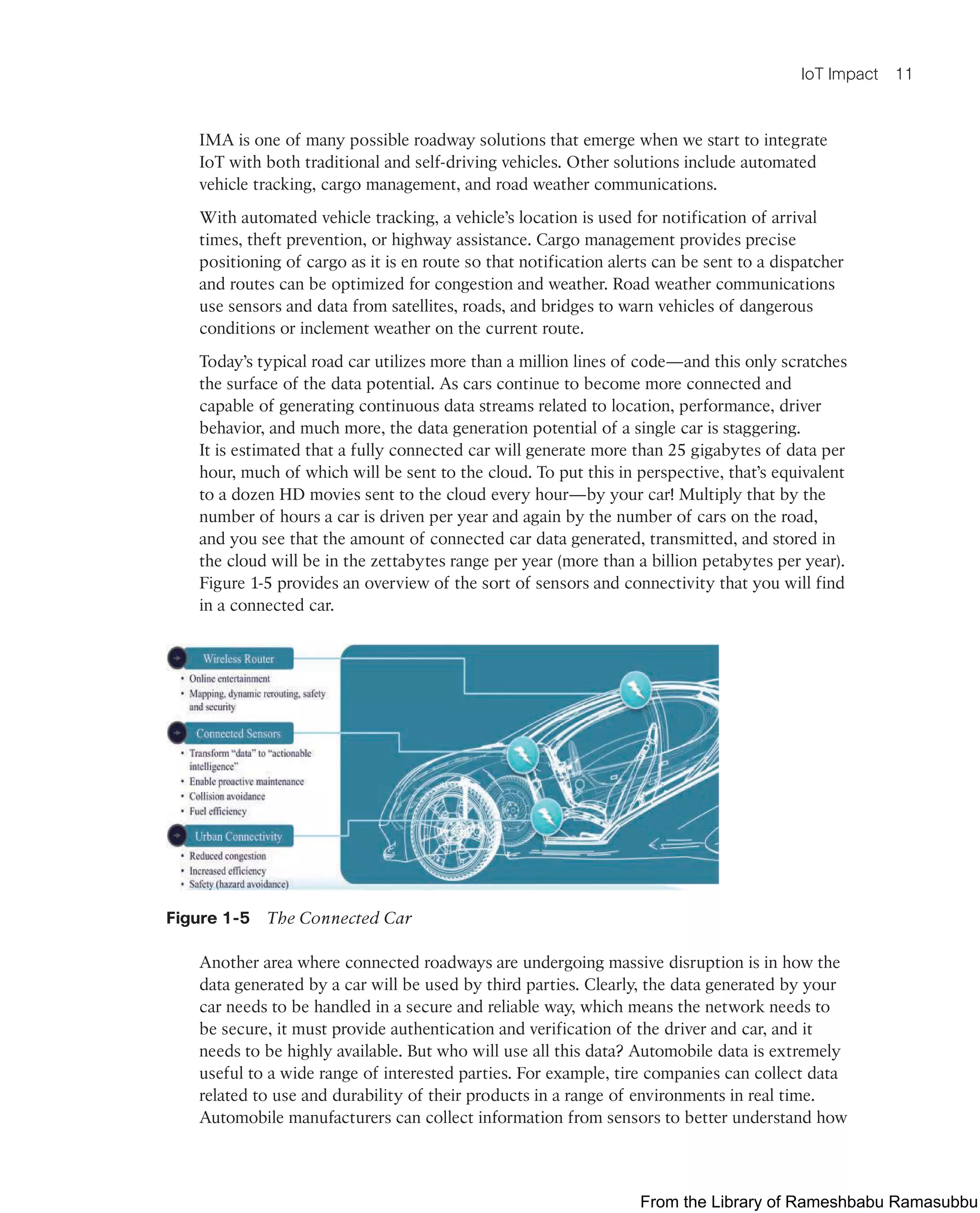










































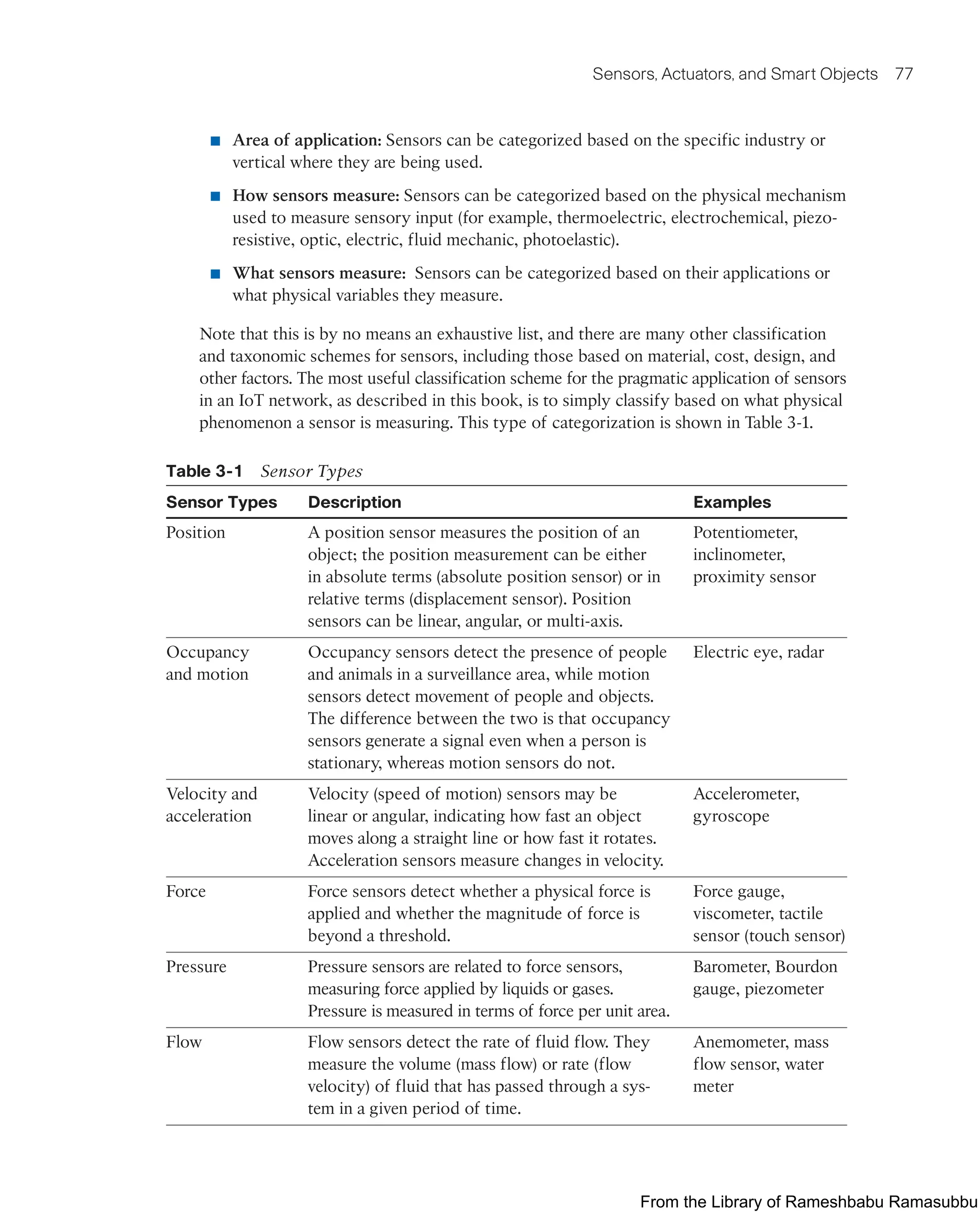
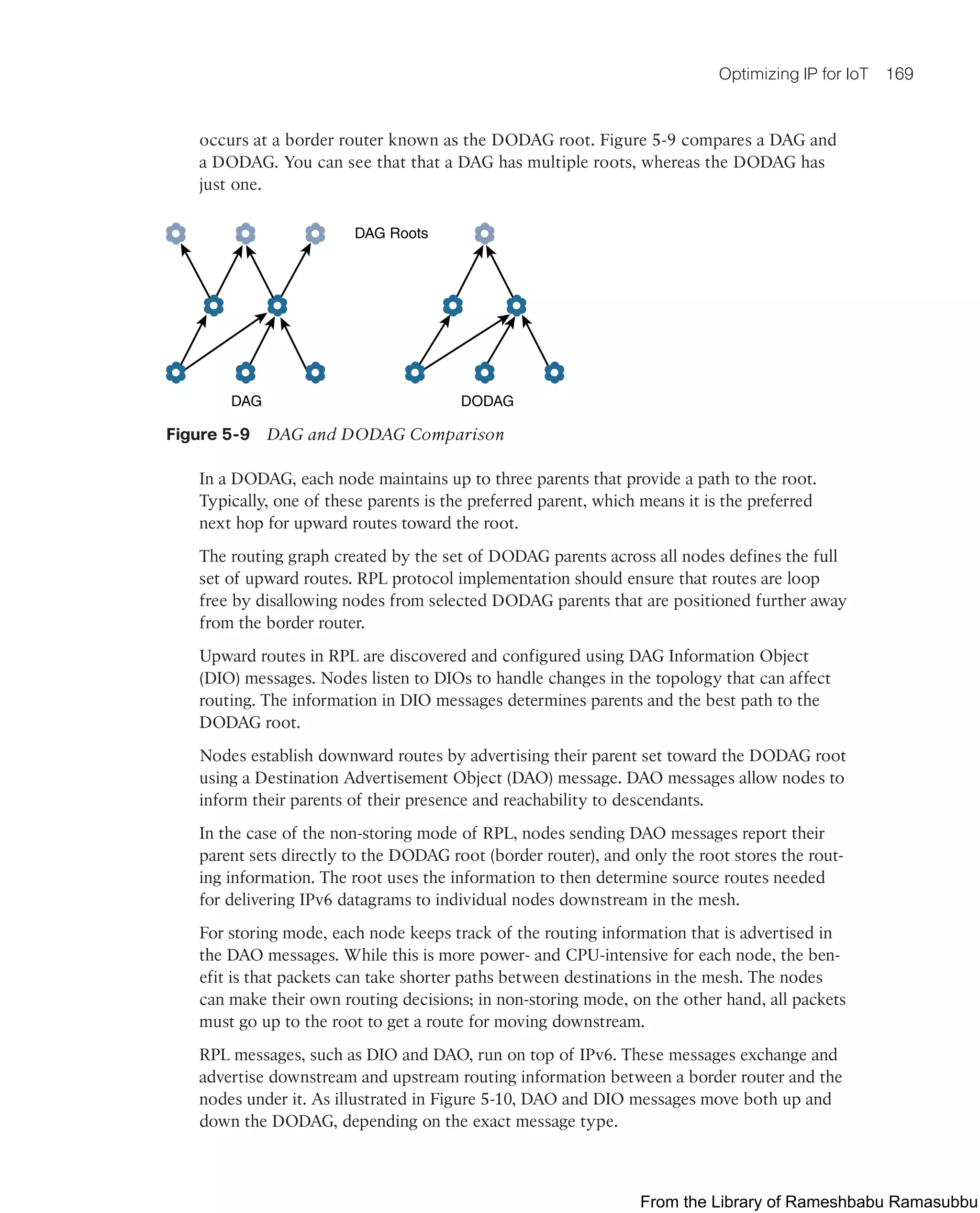
![Imagine the IoT-enabled connected vehicle and roadway highlighted in Chapter 1,
“What Is IoT?” That car has an impressive ecosystem of sensors that provides an
immense amount of data that can be intelligently consumed by a variety of systems
and services on the car itself as well as shared externally with other vehicles, the con-
nected roadway infrastructure, or even a whole host of other cloud-based diagnostic and
consumer services. From behind the steering wheel, almost everything in the car can be
checked (sensed) and controlled. The car is filled with sensors of all types (for example,
temperature, location [GPS], pressure, velocity) that are meant to provide a wealth of rich
and relevant data to, among many other things, improve safety, simplify vehicle mainte-
nance, and enhance the driver experience.
Such sensors are fundamental building blocks of IoT networks. In fact, they are the
foundational elements found in smart objects—the “things” in the Internet of Things.
Smart objects are any physical objects that contain embedded technology to sense
and/or interact with their environment in a meaningful way by being interconnected
and enabling communication among themselves or an external agent.
This chapter provides a detailed analysis of smart objects and their architecture. It also
provides an understanding of their design limitations and role within IoT networks.
Specifically, the following sections are included:
■ Sensors, Actuators, and Smart Objects: This section defines sensors, actuators, and
smart objects and describes how they are the fundamental building blocks of IoT
networks.
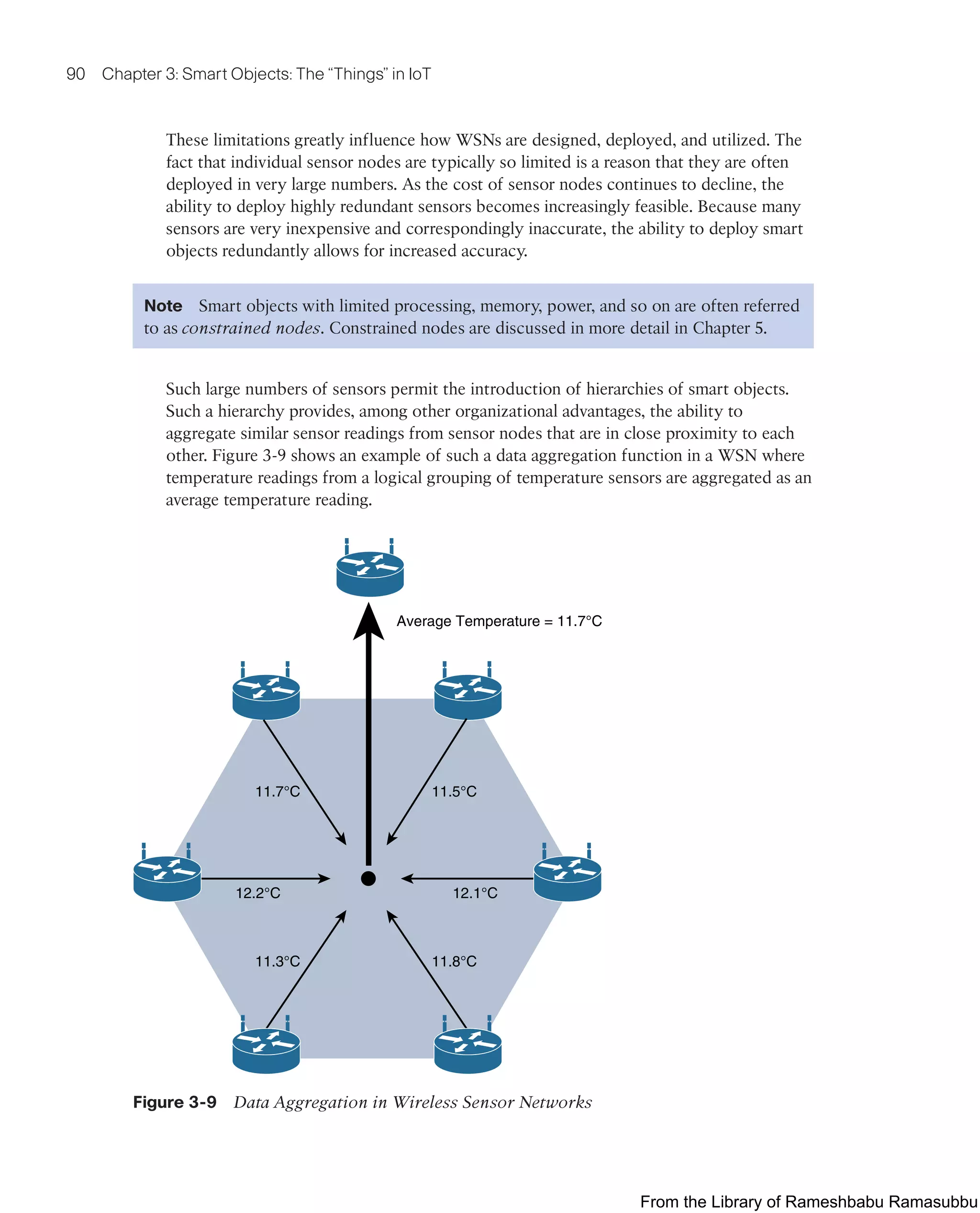
■ Sensor Networks: This section covers the design, drivers for adoption, and
deployment challenges of sensor networks.
Smart Objects: The “Things”
in IoT
Chapter 3
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-108-2048.jpg)









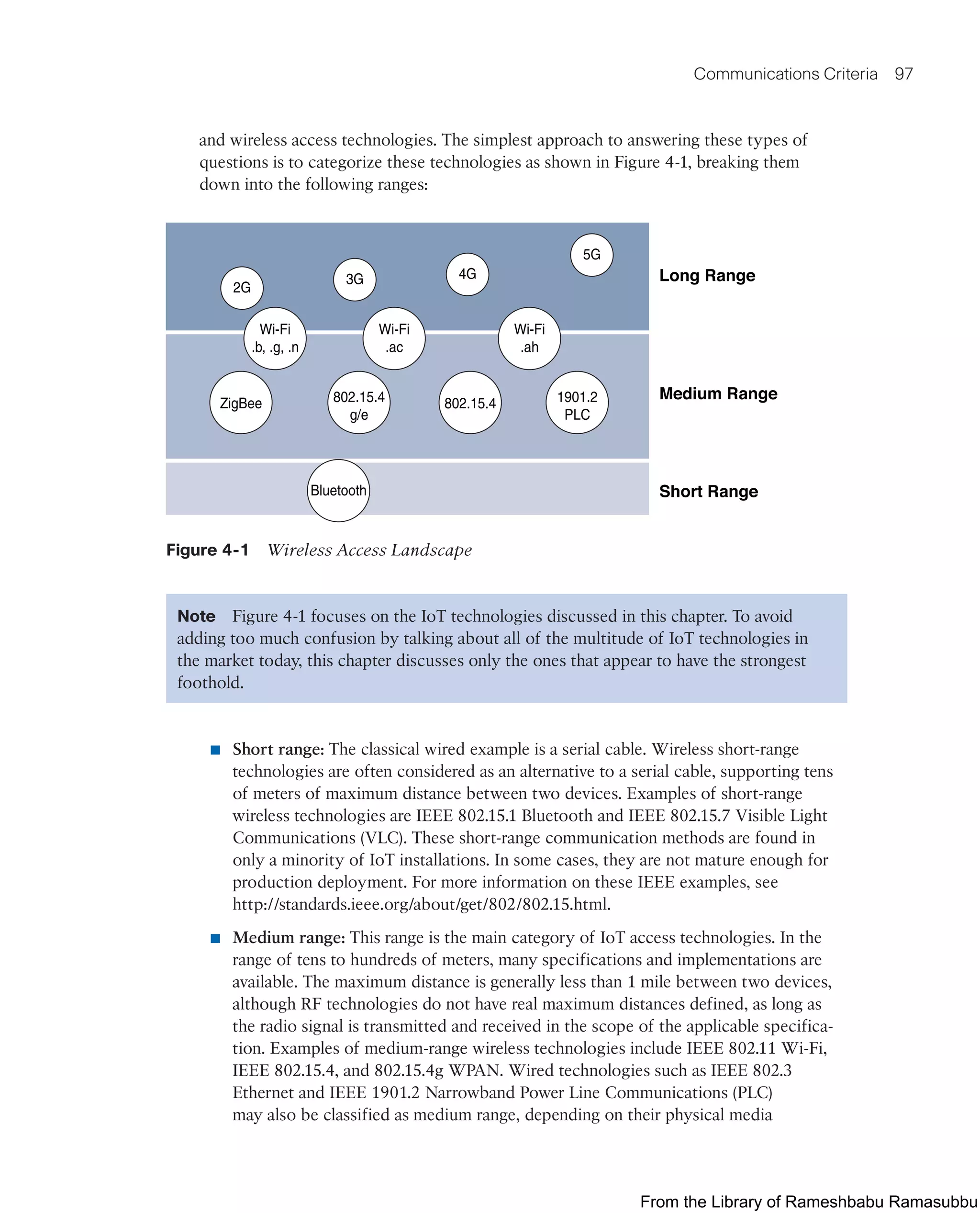










































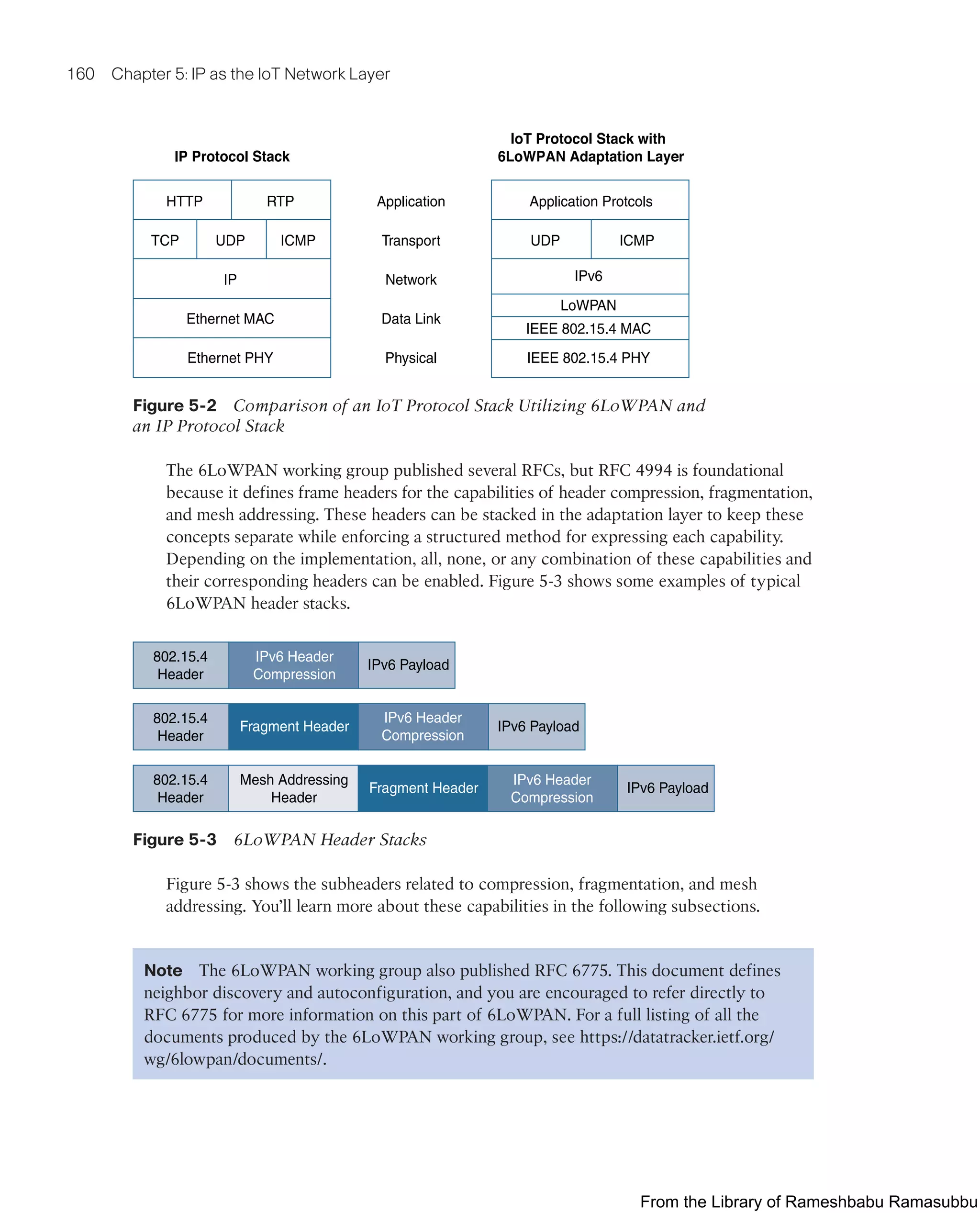







![172 Chapter 5: IP as the IoT Network Layer
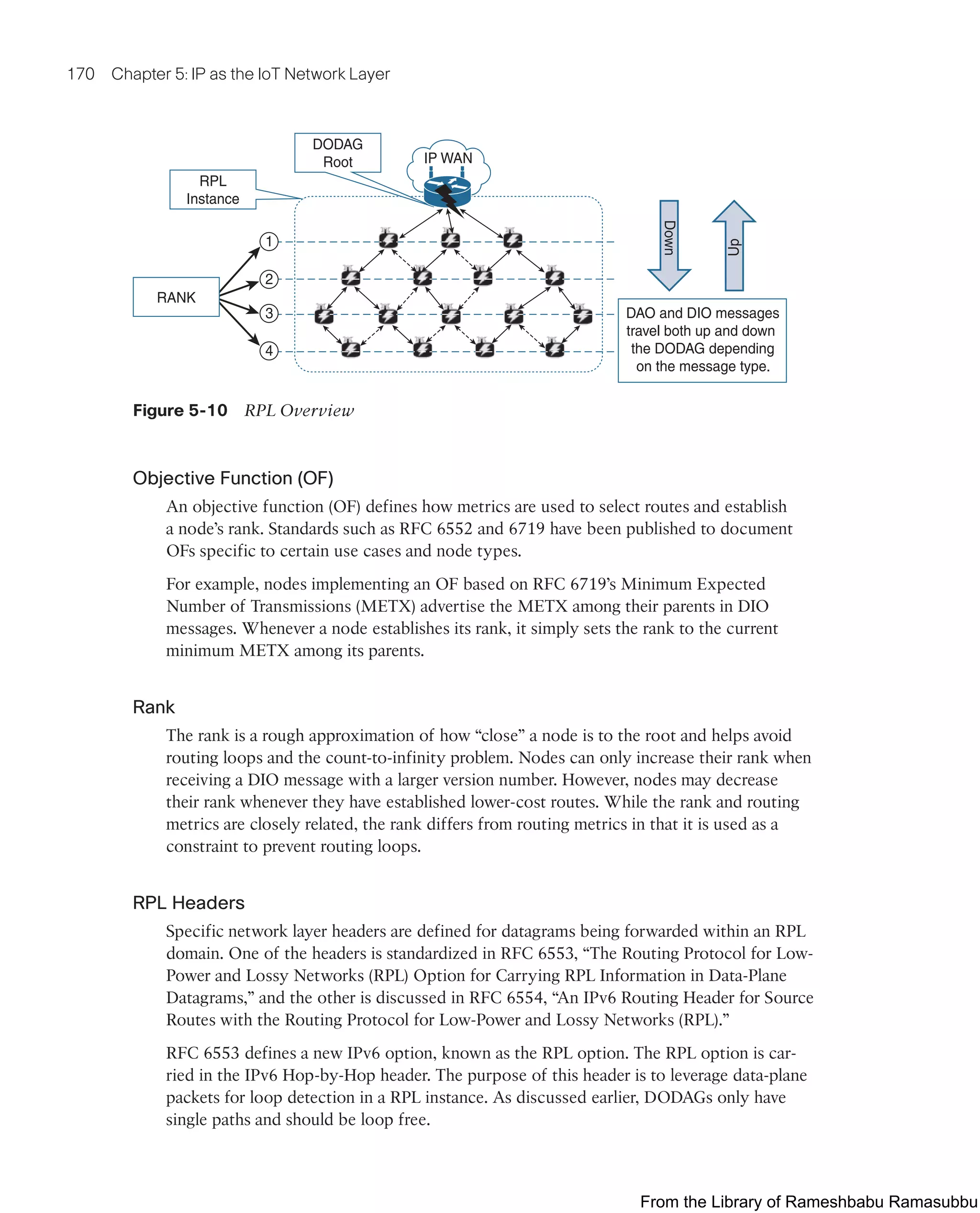
In this scenario, a DODAG root and nodes form an IEEE 802.15.4 mesh. When a node
finds a potential parent, it enters the neighbor into its routing table. However, it does not
yet use the new neighbor for routing. Instead, the node must first establish that the link
quality to its neighbor is sufficient for forwarding datagrams.
The node determines whether the link quality to a potential parent is sufficient by look-
ing at its programmed constraints. In this example, the configured constraints are ETX
and RSSI. If the RSSI in both directions exceeds a threshold and the ETX falls below
a threshold, then the node confirms that the link quality to the potential parent is
sufficient.
Once a node has determined that the link quality to a potential parent is sufficient, it
adds the appropriate default route entry to its forwarding table. Maintaining RSSI and
ETX for neighboring nodes is done at the link layer and stored in the link layer neighbor
table.
The results from all link layer unicast traffic are fed into the RSSI and ETX computation
for neighboring devices. If the link quality is not sufficient, then the link is not added to
the forwarding table and is therefore not used for routing packets.
To illustrate, Example 5-1 displays a simple RPL routing tree on a Cisco CGR-1000 router
connecting an IEEE 802.15.4g mesh 6LoWPAN-based subnetwork. The first IPv6 address
in this example, which ends in 1CC5, identifies the DODAG root for the RPL tree. This
DODAG root has branches to two nodes, indicated by the two IPv6 addresses ending in
924D and 6C35.
Example 5-1 show wpan <interface> rpl tree Command from a Cisco CGR-1000
pat1# show wpan 3/1 rpl tree
----------------------------- WPAN RPL TREE FIGURE [3] ---------------------------
[2013:DB8:9999:8888:207:8108:B8:1CC5] (2)
--- 2013:DB8:9999:8888:89C6:F7C9:D551:924D
--- 2013:DB8:9999:8888:95DF:2AD4:C1B1:6C35
RPL TREE: Num.DataEntries 2, Num.GraphNodes 3
RPL integration in a routing domain follows the same rules as more traditional IP routing
protocols. Route redistribution, filtering, load balancing, and dynamic rerouting can be
implemented the same way as other well-known protocols. For example, in IoT routers,
you could see routes learned via RPL being redistributed into more well-known routing
protocols, such as BGP and EIGRP.
In summary, RPL is a new routing protocol that enables an IPv6 standards-based solu-
tion to be deployed on a large scale while being operated in a similar way to today’s IP
infrastructures. RPL was designed to meet the requirements of constrained nodes and
networks, and this has led to it becoming one of the main network layer IPv6-based rout-
ing protocols in IoT sensor networks.
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-205-2048.jpg)













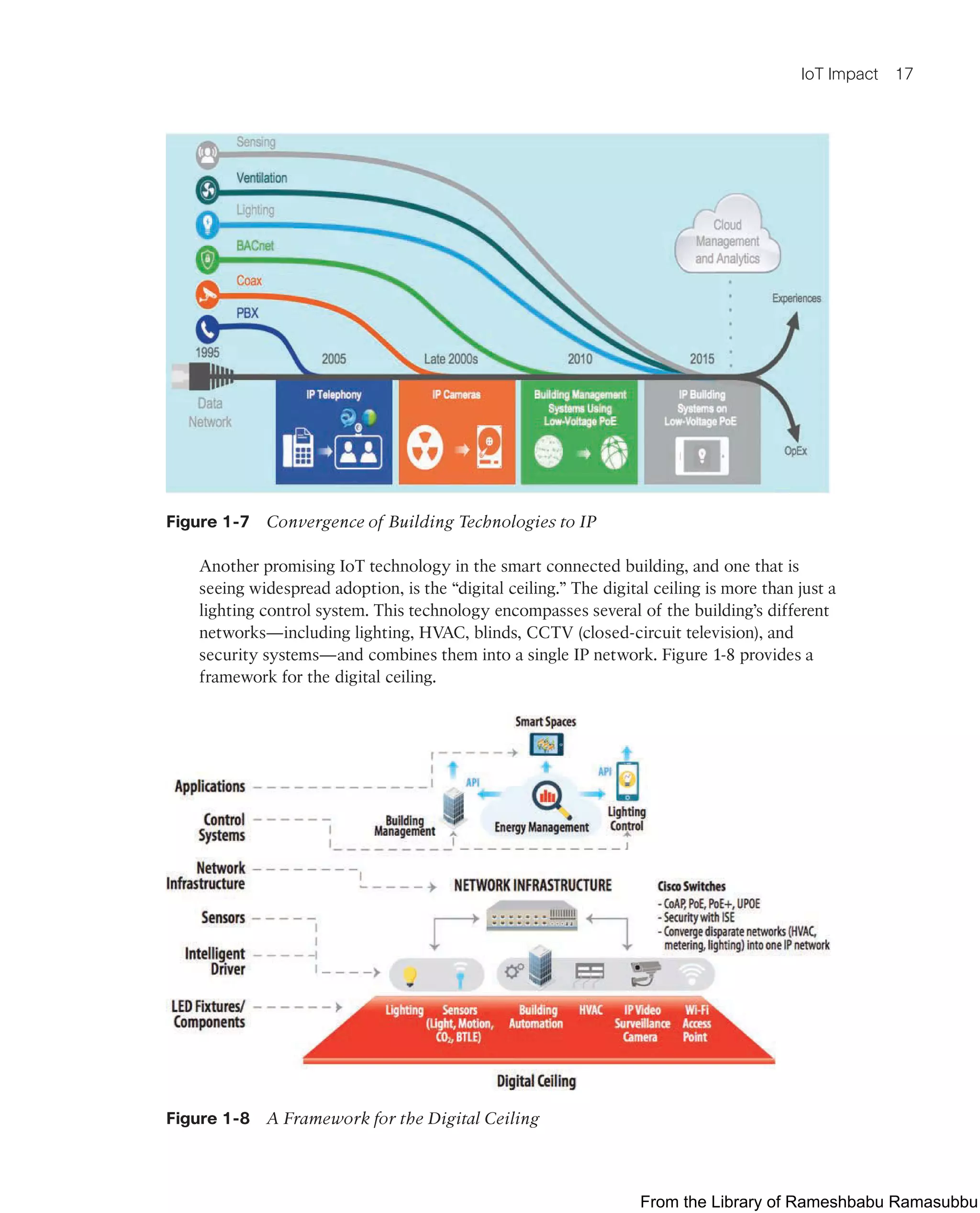
![194 Chapter 6: Application Protocols for IoT
NMS
Backhaul
HTTP-CoAP
Proxy
CoAP
CoAP
CoAP
CoAP
CoAP
CoAP
CoAP
CoAP
HTTP
Figure 6-8 CoAP Communications in IoT Infrastructures
Just like HTTP, CoAP is based on the REST architecture, but with a “thing” acting as
both the client and the server. Through the exchange of asynchronous messages, a client
requests an action via a method code on a server resource. A uniform resource identifier
(URI) localized on the server identifies this resource. The server responds with a response
code that may include a resource representation. The CoAP request/response semantics
include the methods GET, POST, PUT, and DELETE.
Example 6-2 shows the CoAP URI format. You may notice that the CoAP URI format
is similar to HTTP/HTTPS. The coap/coaps URI scheme identifies a resource, including
host information and optional UDP port, as indicated by the host and port parameters in
the URI.
Example 6-2 CoAP URI format
coap-URI = "coap:" "//" host [":" port] path-abempty ["?" query]
coaps-URI = "coaps:" "//" host [":" port] path-abempty ["?" query]
CoAP defines four types of messages: confirmable, non-confirmable, acknowledge-
ment, and reset. Method codes and response codes included in some of these messages
make them carry requests or responses. CoAP code, method and response codes, option
numbers, and content format have been assigned by IANA as Constrained RESTful
Environments (CoRE) parameters. (For more information on these parameters, see www.
iana.org/assignments/core-parameters/core-parameters.xhtml.)
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-227-2048.jpg)

























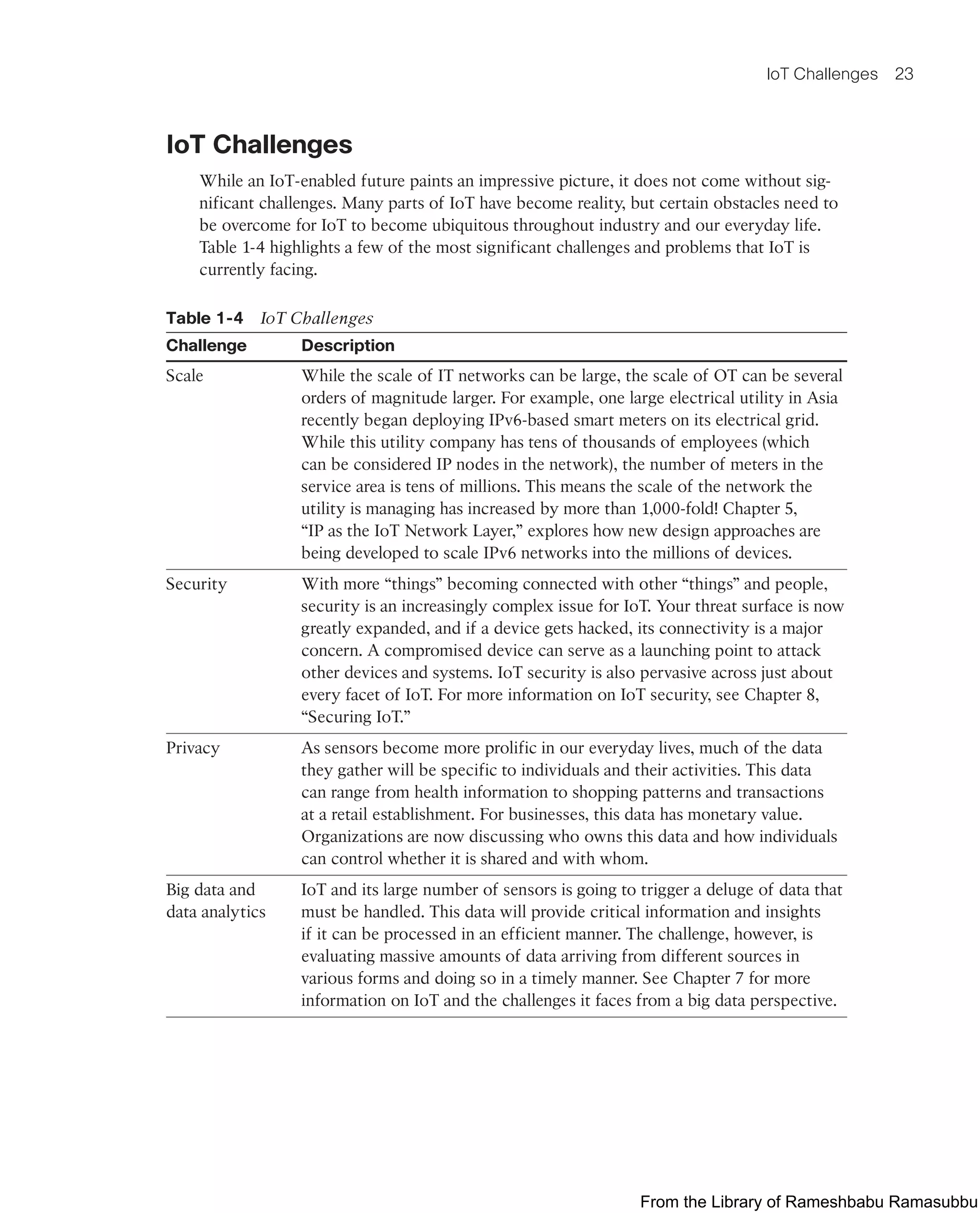
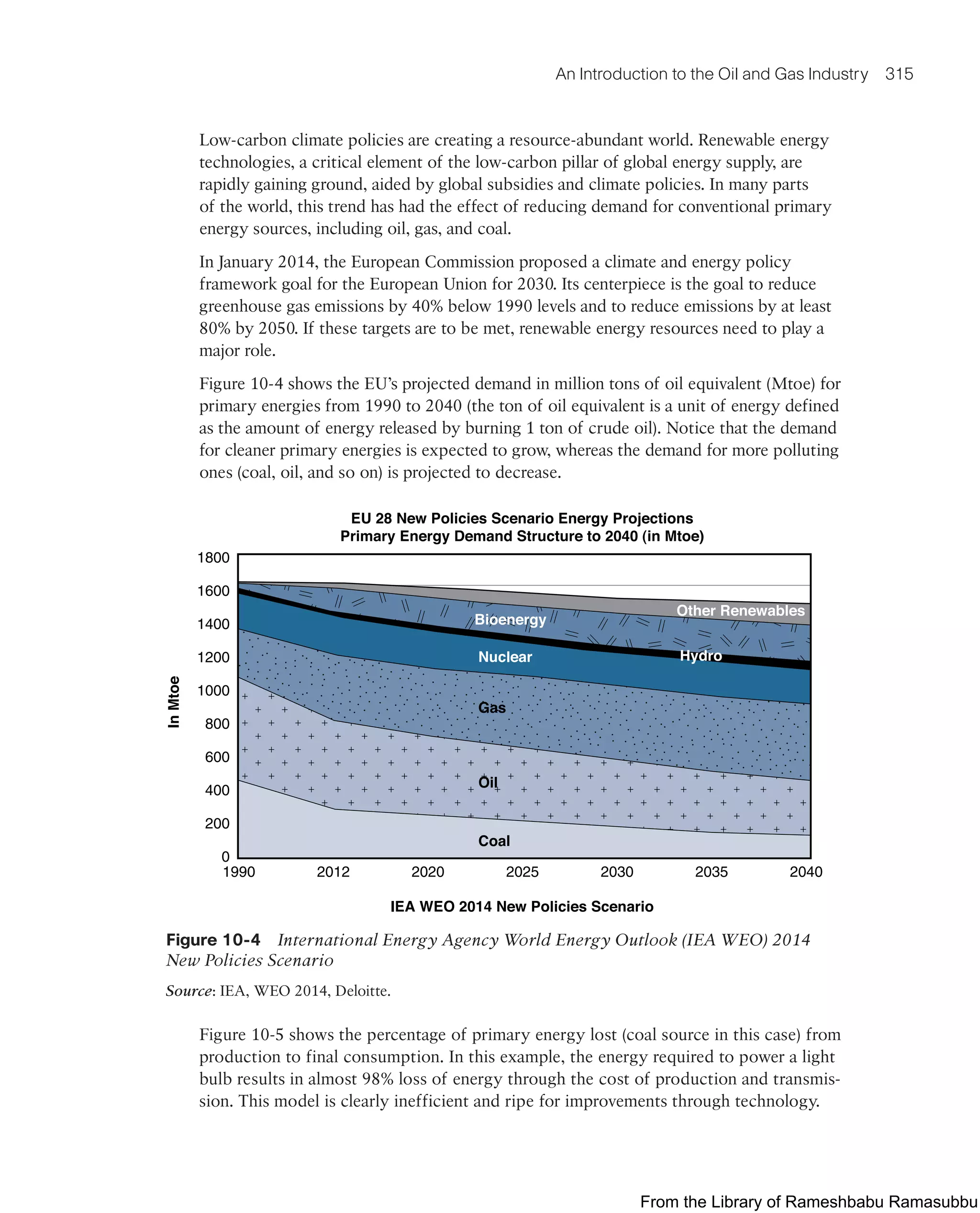
![Network Analytics 241
■ Flow export timers: Timers indicate how often flows should be exported to the
collection and reporting server.
■ NetFlow export format: This simply indicates the type of flow reporting format.
■ NetFlow server for collection and reporting: This is the destination of the flow
export. It is often done with an analytics tool that looks for anomalies in the traffic
patterns.
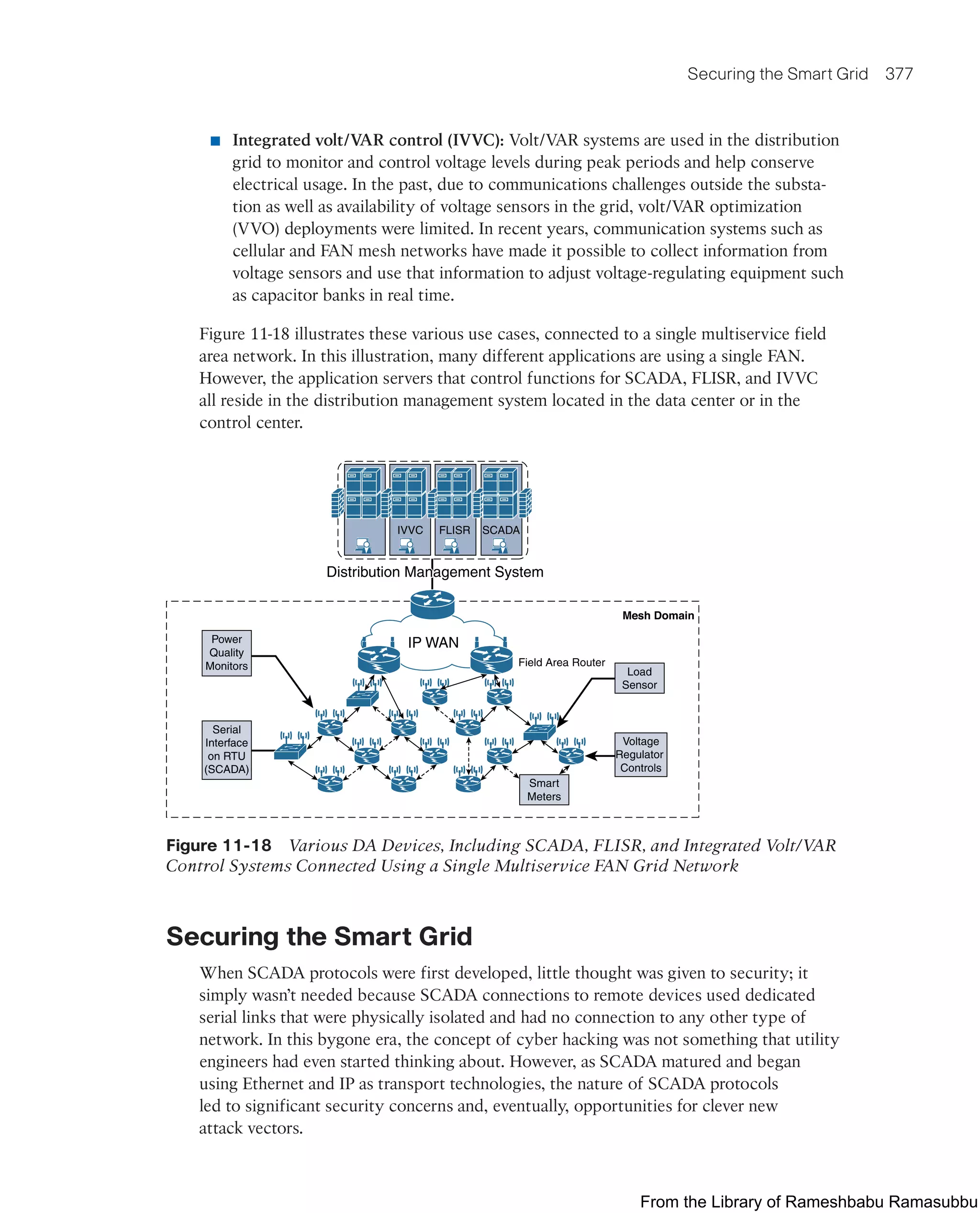
Figure 7-18 illustrates the analysis reported from the FNF records on a smart grid FAN.
In this example, the FNF collector is able to see the patterns of traffic for various applica-
tions as well as management traffic on the FAN.
280
260
240
220
200
180
160
140
120
100
80
60
40
20
0
13:15 16:15 19:15 22:15 01:15 04:15 07:15 10:15 13:15
Bandwidth
[Mbps]
Time
Daily Min
SCADA
CoAP
Meter Reads
Daily Max
Figure 7-18 FNF Report of Traffic on a Smart Grid FAN
Flexible NetFlow in Multiservice IoT Networks
In the context of multiservice IoT networks, it is recommended that FNF be configured
on the routers that aggregate connections from the last mile’s routers. This gives a global
view of all services flowing between the core network in the cloud and the IoT last-mile
network (although not between IoT devices). FNF can also be configured on the last-mile
gateway or fog nodes to provide more granular visibility. However, care must be taken in
terms of how much northbound data is consumed through reporting.
However, flow analysis at the gateway is not possible with all IoT systems. For exam-
ple, LoRaWAN gateways simply forward MAC-layer sensor traffic to the centralized
LoRaWAN network server, which means flow analysis (based on Layer 3) is not possible
at this point. A similar problem is encountered when using an MQTT server that sends
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-274-2048.jpg)













































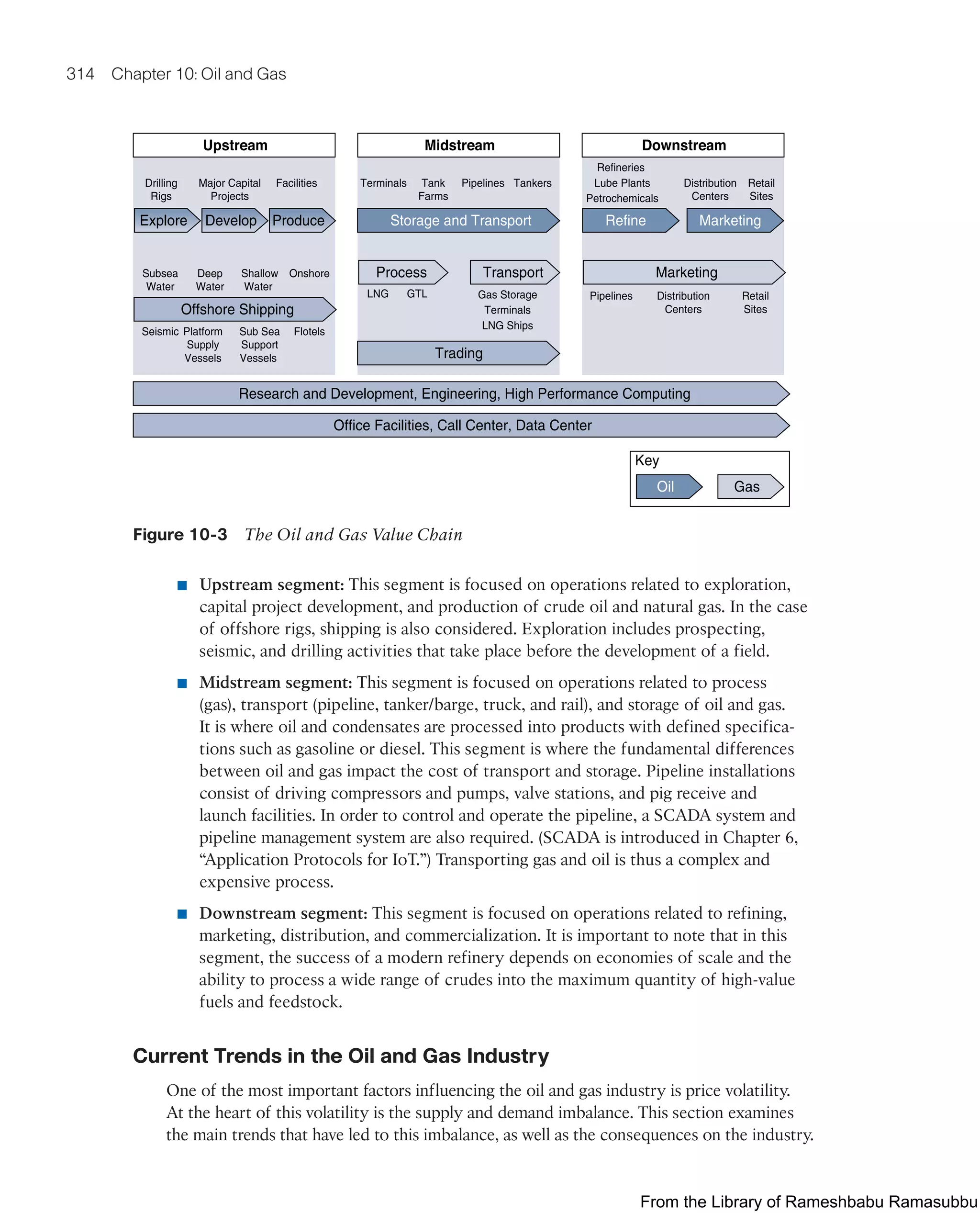
![An Introduction to the Oil and Gas Industry 311
Good Quality
Reservoirs
Poor Quality
Reservoirs
Tight Oils
Heavy and
Extra-Heavy Oils
Oil Shales
Immature Source Rock
Shale Oil
Mature Source Rock
Tar
Sands
Conventional
Oils
Non-
Conventional
Oils
Reservoir
Source
Rock
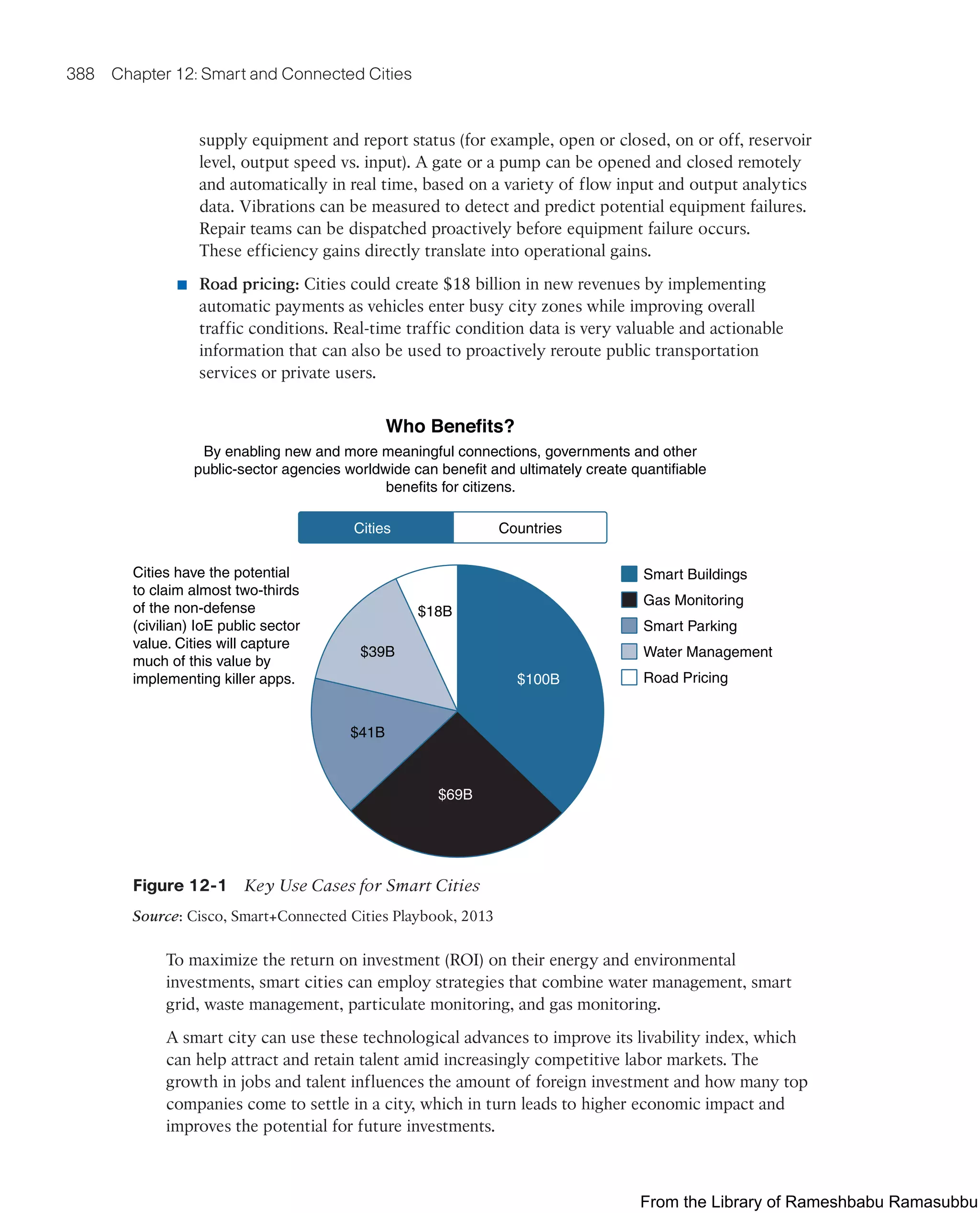
Figure 10-1 Conventional Versus Unconventional Oil and Gas
Source: Oil and Gas IoT Service Vertical, based on IFP Energies Nouvelles [IFPEN].
Oil has various compositions and types, such as rock oil, mineral oil, and crude oil, and is
usually classified based on its density, viscosity, and sulfur content. Some examples of oil
classification include the following (refer to Figure 10-1):
■ Tight oils: Tight oils are liquid hydrocarbons contained in reservoirs with very low
porosity and equally low permeability.
■ Heavy and extra-heavy oils: These resources are referred to as heavy because of
their high density and viscosity, which make it impossible for them to be extracted
in the traditional way.
■ Oil sands: These deposits are made up of sand and tar mixed together.
■ Oil shales: Shales are a source rock that has not yet been transformed into
hydrocarbon and needs to be heated to be recovered.
■ Shale oil: With shale oil, the source rock is sufficiently far below the surface that the
organic material it contains has been transformed into liquid hydrocarbons. However,
as a result of its very low porosity and impermeability, these liquid hydrocarbons
remain trapped in the source rock. The extraction of these trapped liquid hydrocar-
bons requires the use of horizontal drilling and hydraulic fracturing techniques to
artificially increase the permeability of the rock.
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-344-2048.jpg)
![312 Chapter 10: Oil and Gas
The following are four elements that must exist for oil and gas to accumulate in
“economic” quantities:
■ A source rock is needed to generate the hydrocarbons.
■ A suitable reservoir is needed to bear the hydrocarbons.
■ A trap with a seal is needed to contain the hydrocarbons.
■ All three elements must occur within a dynamic system where they can interact.
Figure 10-2 illustrates these four elements.
Deposit
Trap
Closed Structure in which
Hydrocarbons Accumulate
Seal
Impermeable Rock that Prevents
Hydrocarbons from Migrating
to the Surface
Reservoir
Porous, Permeable Rock in which
Hydrocarbons Can Accumulate
Source Rock
Rock Rich Hydrocarbon-Forming
Organic Matter
Increase in
Pressure and
Temperature
Migration
Expulsion
Generation
Source: IFP Energies Nouvelles (IFGEN)
Shale Top-Seal
Gas Cap
Source
Rock
Shale
Bottom-Seal
S
e
a
li
n
g
F
a
u
lt
Migration Path
Oil
Oil-Water Contact
Figure 10-2 From Organic Matter to Oil and Gas
Source: IFP Energies Nouvelles [IFPEN].
Unlike oil, gas has very low density and viscosity, and it cannot be transported at normal
temperature and pressure conditions. Raw natural gas from a well consists of methane
as well as many other smaller fractions of heavier hydrocarbons and various other
components, such as the following:
■ Ethane
■ Propane
■ Butane
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-345-2048.jpg)






















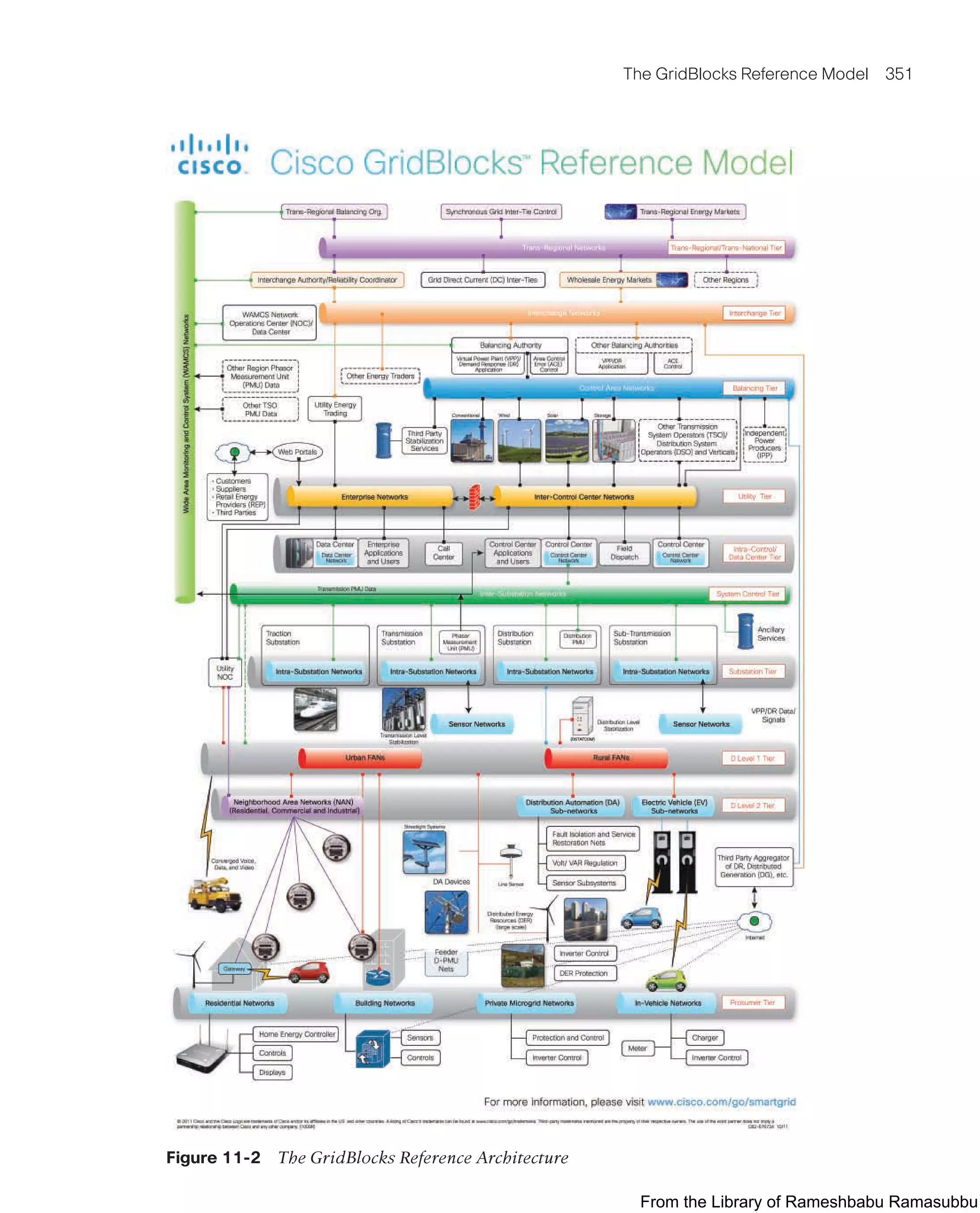


![354 Chapter 11: Utilities
■ Utility tier: This tier is home to the enterprise campus networks. (Although the name
implies that there is some grid-related function here, this is an IT-focused tier.) The
utility tier is the connection point between the control center and the enterprise
network, and it utilizes firewalls with the appropriate security policies to ensure that
only trusted traffic from the enterprise network enters into the control center.
(Note that firewalls are used throughout this architecture and between tiers, and this
is but one example.) It is also important to note that most utilities operate multiple
control centers and have highly dispersed enterprise networks, meaning that these
networks must be securely connected through either metro networks or WANs
(possibly reusing a WAN network as the system control tier).
■ Balancing tier: This tier supports connections between third-party power-generation
operators and balancing authorities (as well as connections to independent power
producers [IPPs]). In an electric utility, demand from customers may not always meet
the generation supply. To manage load and demand, most utilities are interconnected
with other utilities and can buy and sell electrical energy from each other when
necessary. At times, there may be an excess of power in one utility and a shortage
of electricity in another. The balancing authority has the delicate responsibility of
managing electrical demand versus supply on the grid. If electrical demand and sup-
ply fall out of balance, blackouts can occur. The sensitive nature of the balancing tier
highlights the need for a communications network that enables different parties to
collaborate effectively and securely.
■ Interchange tier: The network at this tier allows electricity to be bought and sold
between utility operators. In the utility world, electricity is transacted in much the
same way as other commodities, such as oil and gas. The sale or purchase of electric-
ity needs to happen in real time. Networks at this tier allow the utility to not only
buy electrical energy when needed but also make a profit by selling excess power to
other utilities when there is an opportunity to do so.
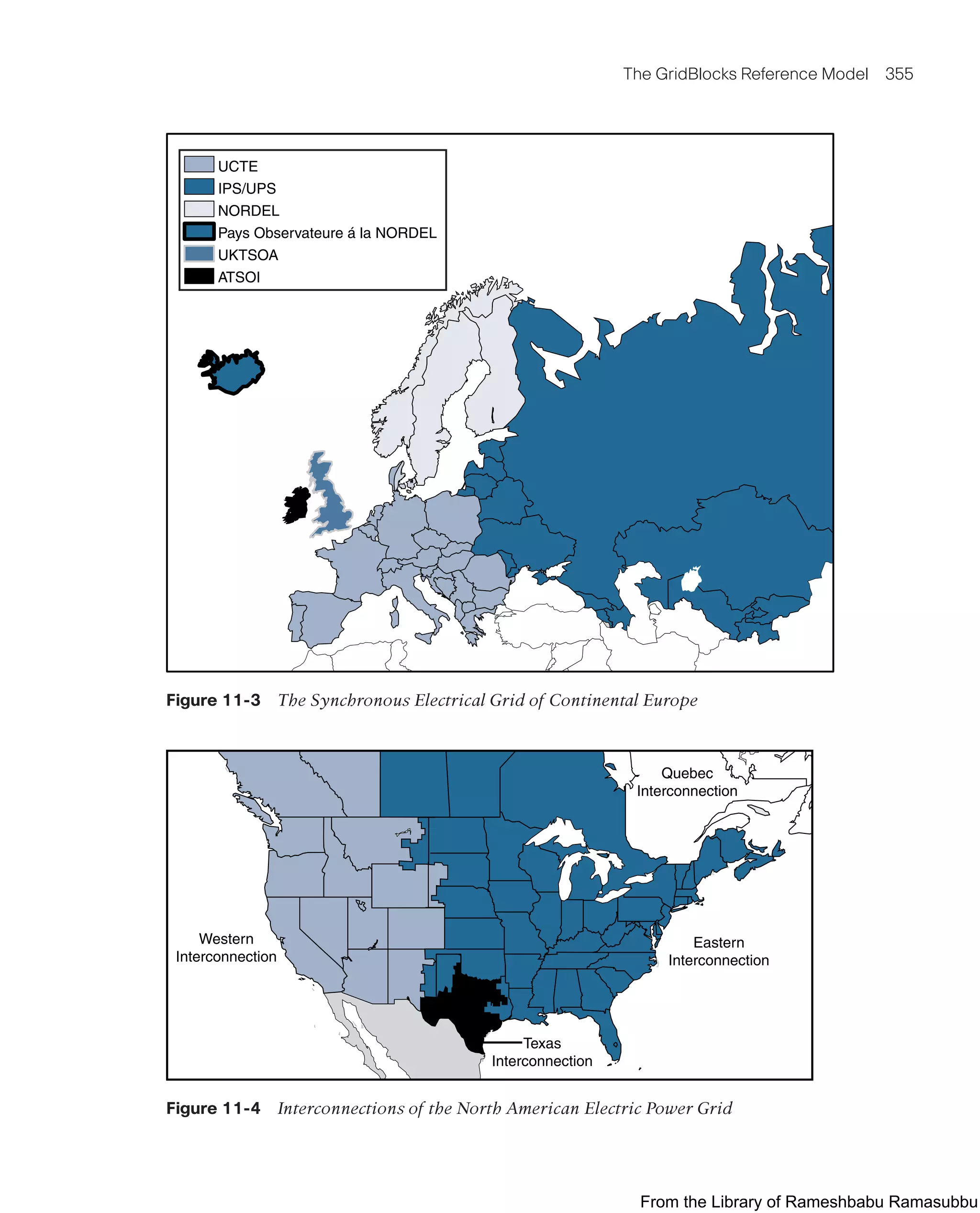
■ Trans-regional/trans-national tier: Most utility grids are interconnected with much
larger supergrids. For example, Figure 11-3 shows how the utilities in different
countries and regions are interconnected with one another to form what is known
as the Synchronous Grid of Continental Europe. In North America, this is known as
the North American Interconnection, and it is composed of interconnection points
between the Texas Grid, Western Interconnection, Eastern Interconnection, and
Quebec Interconnection, as shown in Figure 11-4. At this tier are the network con-
nections between synchronous grids for power interchange as well grid monitoring
and power flow management.
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-387-2048.jpg)





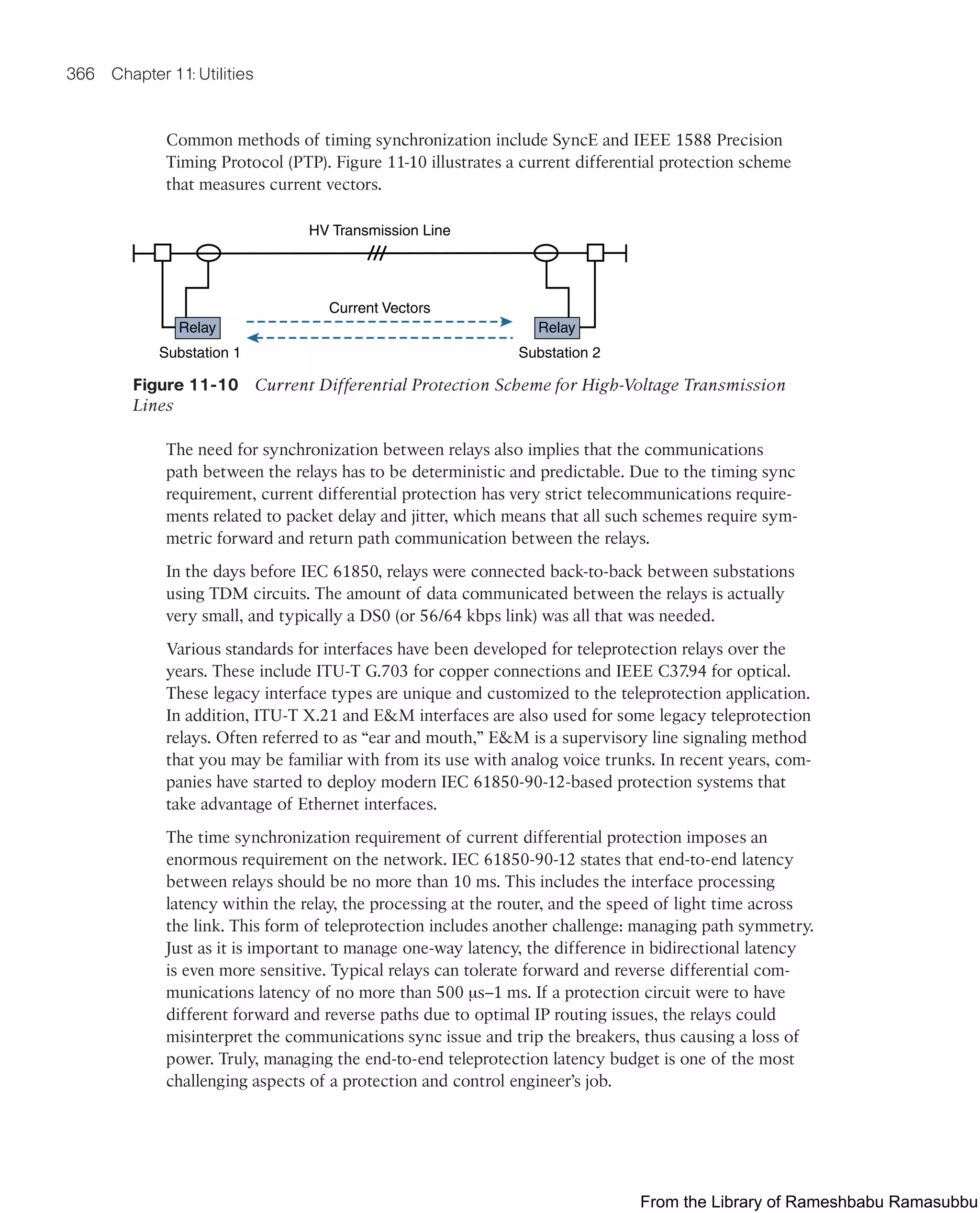

![368 Chapter 11: Utilities
MPLS-TP also supports APS by identifying a known backup LPS path in case of a prima-
ry LSP failure. In this case, the backup LSP is deployed such that it also has predictable
latency and path symmetry in case of failure.
One of the key benefits of MPLS-TP is that it supports end-to-end OAM. OAM allows
for fault detection of the pseudo-wire at any point and is used as the trigger mechanism
to fail over to a backup LSP. MPLS-TP implements in-band OAM capabilities using a
generic associated channel (G-ACh) based on RFC 5085 (Virtual Circuit Connectivity
Verification [VCCV]). The in-band OAM channel is like a point-to-point management/
control circuit that can detect link or node failures and can signal backup LSP failover
on the order of 50 ms or less. Figure 11-12 illustrates the G-ACh within the MPLS-TP
pseudo-wire.
G-ACh MPLS-TP
Tunnel
MPLS-
TP LSP
Figure 11-12 OAM Generic Associated Channel (G-ACh) Within an MPLS-TP Pseudo-wire
MPLS-TP is able to meet the requirements of teleprotection, but what about other simi-
lar MPLS modalities, such as MPLS–Traffic Engineering (MPLS-TE)? MPLS-TE was
developed many years ago to explicitly and dynamically define a label switch path (LSP)
through an MPLS network. As such, it has many similarities with MPLS-TP. However,
although MPLS-TE can be used to meet the predictable latency and path engineering
requirements of teleprotection, there is one downside: MPLS-TE does not have OAM
capabilities. With MPLS-TE, it is still possible to create deterministic and symmetrical
paths, as well as provide support for APS, but the implementation with MPLS-TP tends to
be much simpler and has more similarities to carrier Ethernet switching.
MPLS-TE does has one key advantage over MPLS-TP: Its ability for call admission
control (CAC). With CAC, the edge router is able to determine whether enough band-
width exists along the path to support the requested circuit. In most cases, this capability
is not critical for teleprotection traffic because the bandwidth requirements are minimal,
but in practice it is a useful capability.
A new MPLS variant called Flex-LSP combines the best of both of these. Flex-LSP
supports all the benefits of MPLS-TP, such as APS and OAM for pseudo-wires, while also
supporting CAC and Layer 3 traffic engineering, much like MPLS-TE. As technology
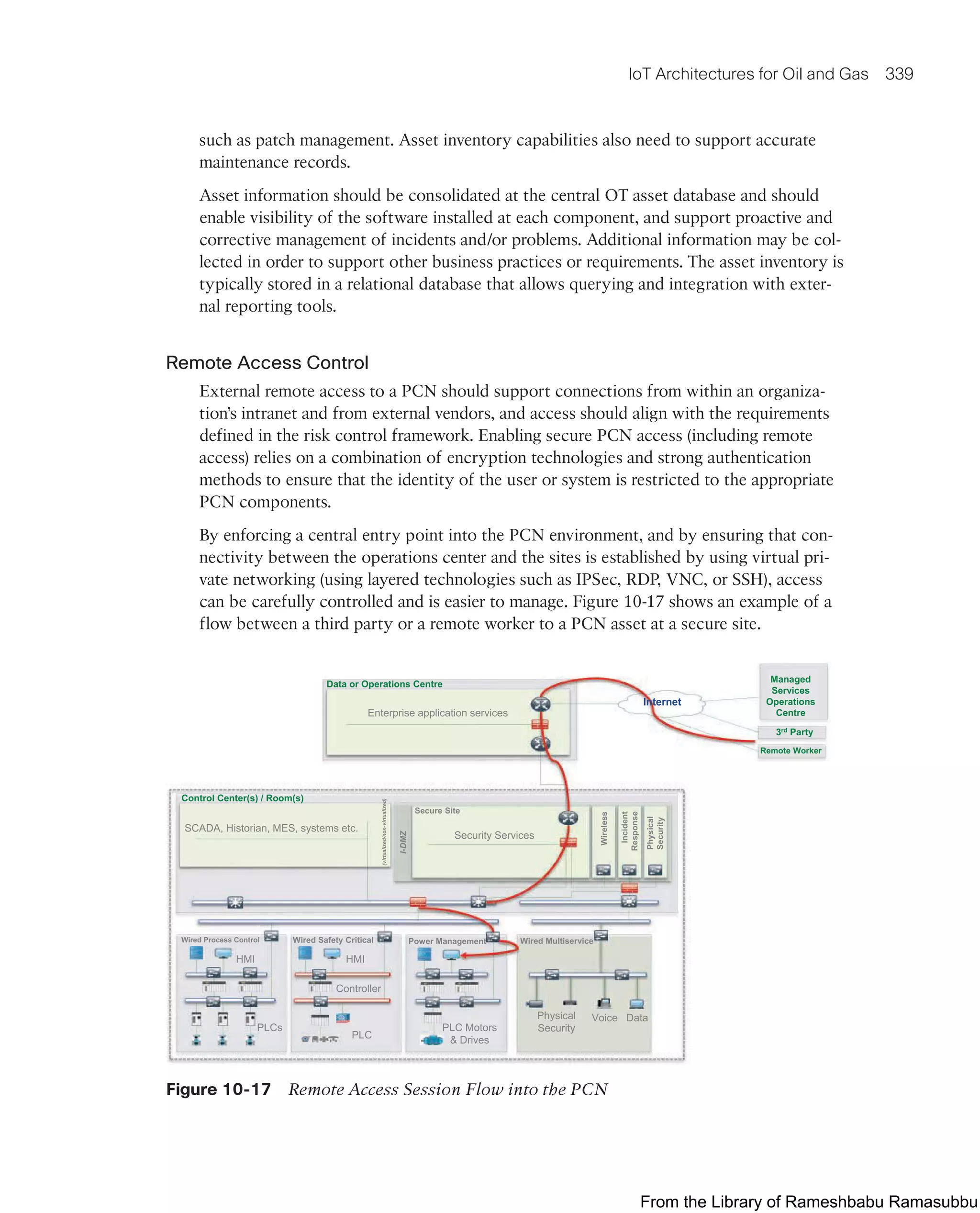
continues to improve, other MPLS modalities, such as segment routing, may also be
appropriate for teleprotection in the future.
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-401-2048.jpg)

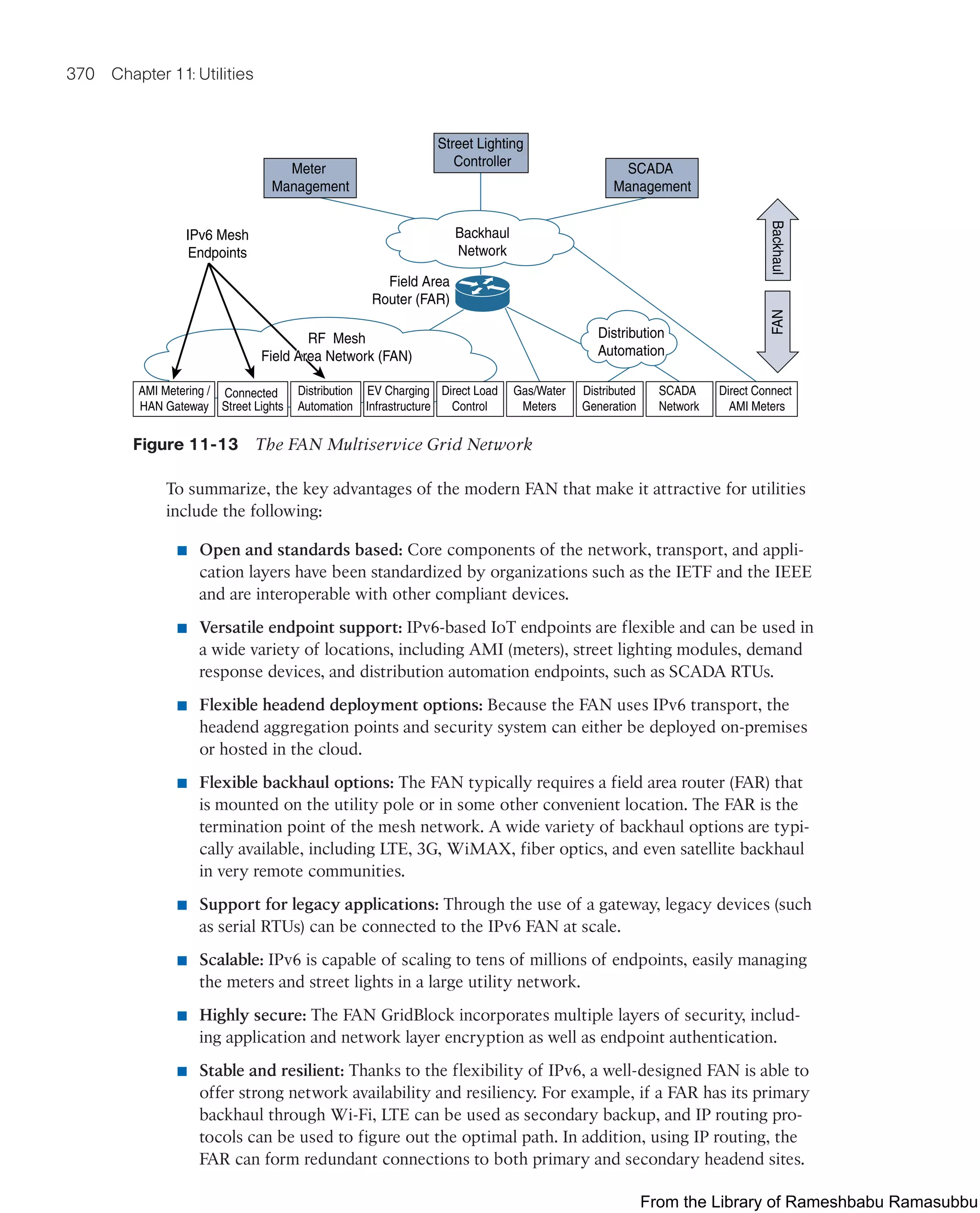





















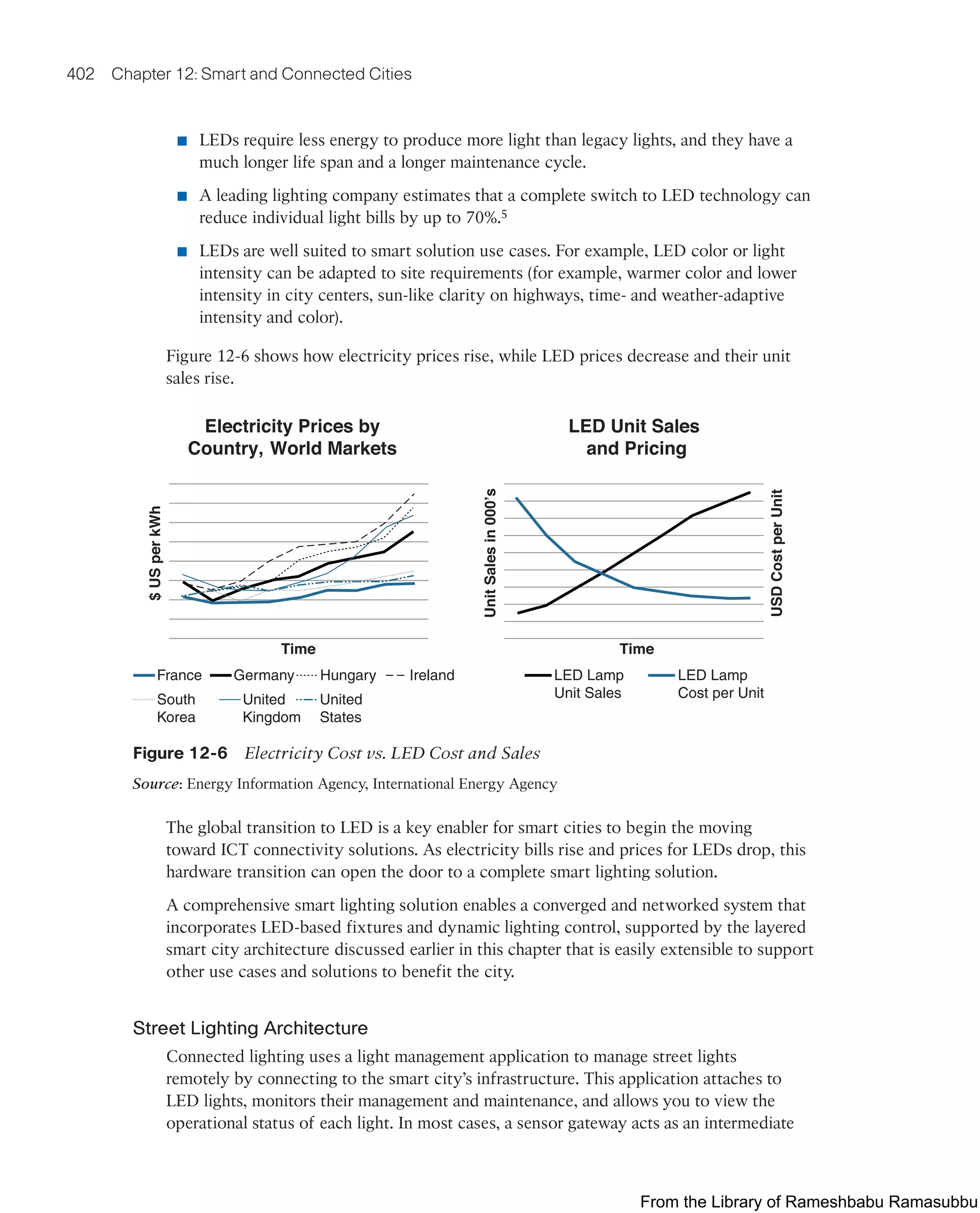
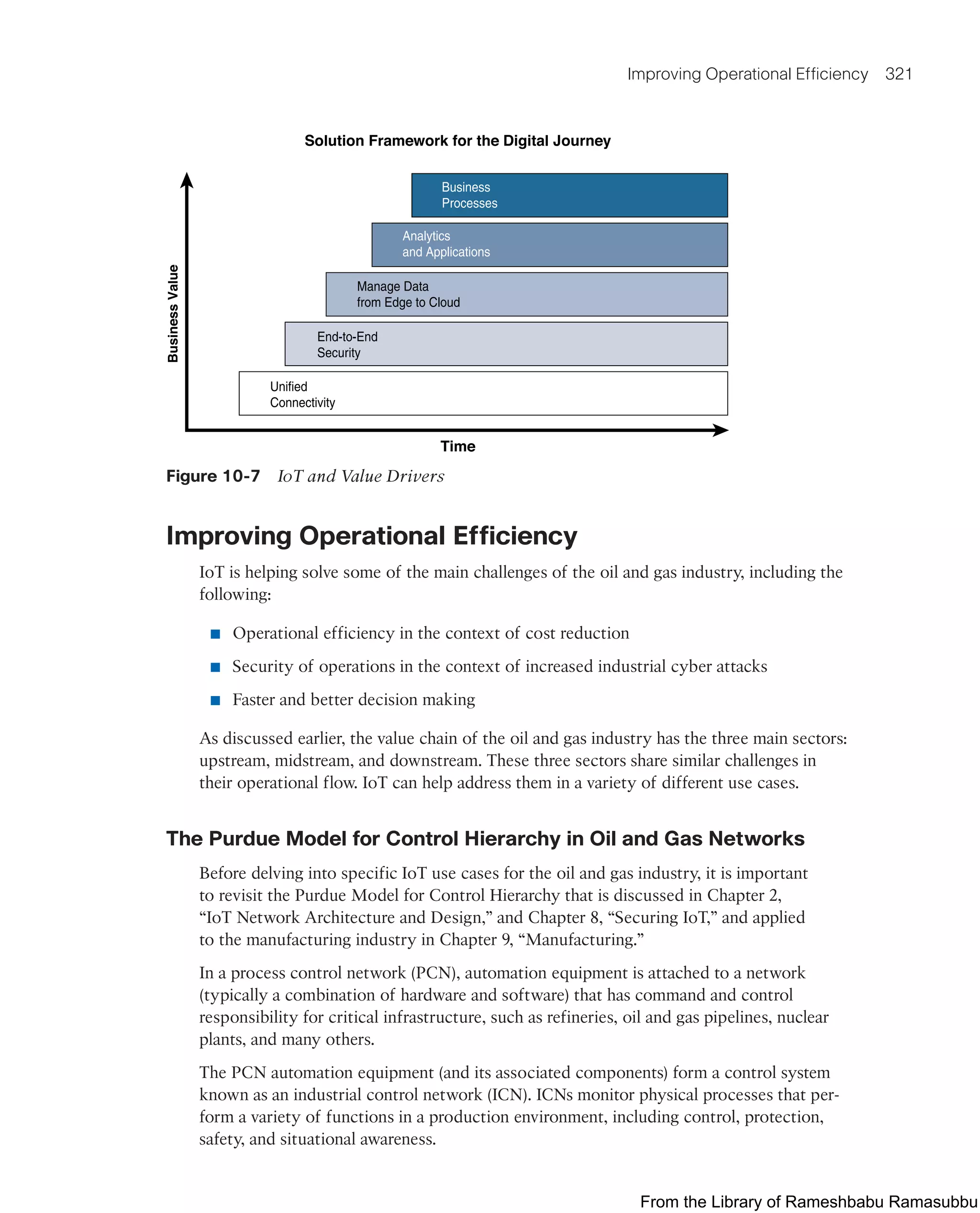
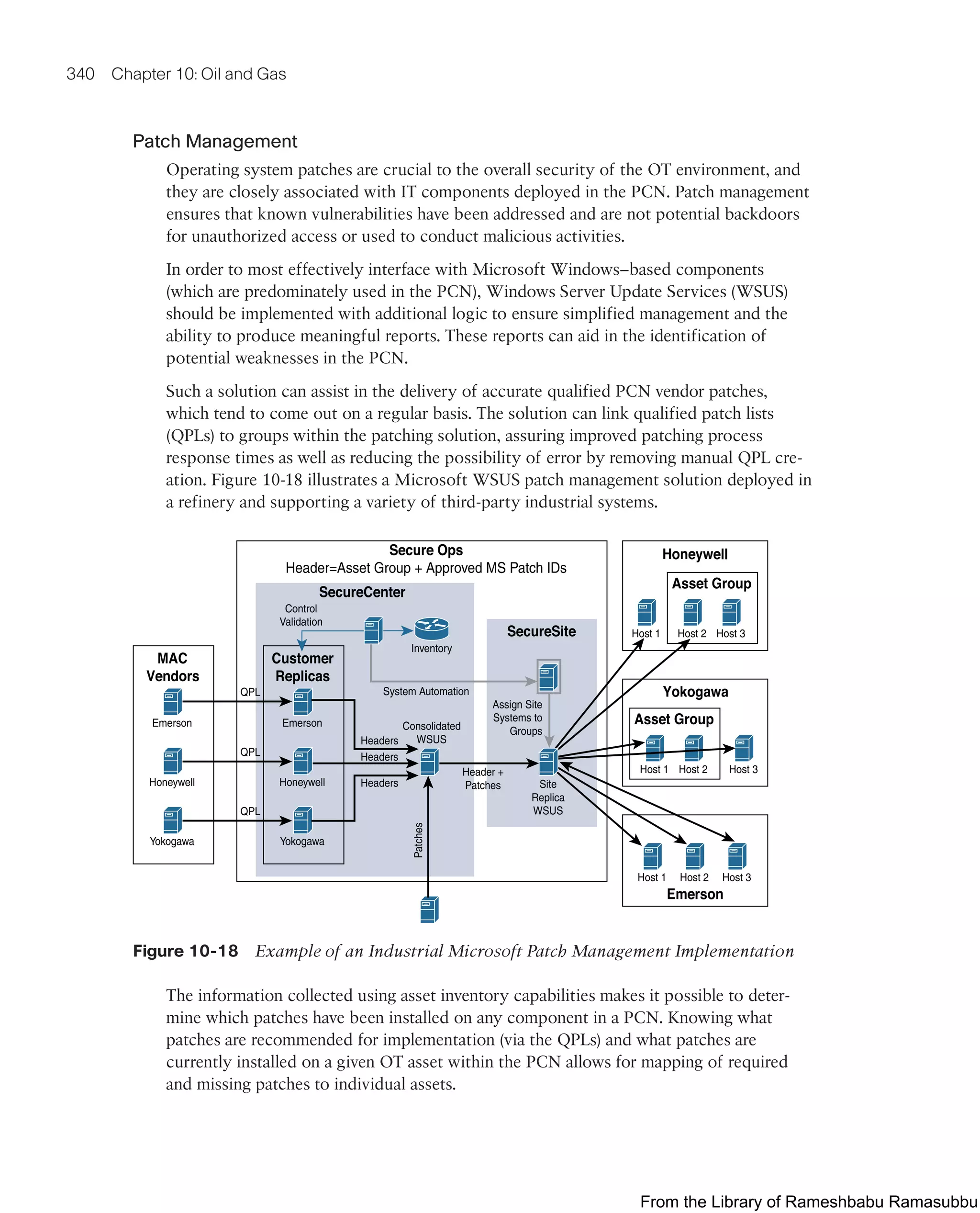
![Smart City Use-Case Examples 403
system between the application and the lights (light control nodes). The gateway relays
instructions from the application to the lights and stores the local lights’ events for the
application’s consumption. The controller and LED lights use the cloud to connect to
the smart city’s infrastructure, as shown in Figure 12-7.
Device Management
Cloud
Light Control
Node
RF Mesh
Light Control
Node
Wi-Fi
Device Management
Cloud
Device Management
Cloud
Light Actuation
and Events
Light Actuation
and Events
Light Actuation
and Events
Light Actuation
and Events
Operator
Dashboard
Light Management
Application
SOS App
Apps
Access Points
Access Switch
Sensor
Gateway
Cloud Layer
Figure 12-7 Connected Lighting Architecture
Source: Cisco, Smart+Connected Lighting
A human or automated operator can use a cloud application to perform automated sched-
uling for lights and even get light sensors to perform automated dimming or brightening,
as needed. The schedule can also impact the light intensity level and possibly the color,
depending on environmental conditions, weather, time of year, time of day, location
within the city, and so on.
Lighting nodes vary widely in the industry, especially with respect to elements such as
what communication protocol they use (for example, Wi-Fi, cellular, ZigBee, 802.15.4g
[Wi-SUN], LoRaWAN), level of ruggedization, and on-board sensor capabilities. These
features are optimized for different circumstances and conditions; no single lighting node
can support all environments ideally. For example, city centers may be locations where
Wi-Fi is easy to deploy (due to proximity to Ethernet or Internet backbones, ranges on the
order of 100 meters, and high urban furniture density offering a large choice of relays and
gateway points), whereas highways may mandate longer-range solutions such as cellular
or LoRaWAN. Many solutions leverage wired connectivity, either by using the existing
city cable infrastructure or by adding a cable adjacent to the power cable. In cases where
cabling is not practical, wireless technologies may bring interesting capabilities. For exam-
ple, 802.15.4g controllers can be used to form a mesh and extend the network. This exten-
sion is used not only to connect other light poles but also to connect smart meters from
From the Library of Rameshbabu Ramasubbu](https://image.slidesharecdn.com/iotfundamentals-230228003216-c4b6accc/75/IoT-Fundamentals-pdf-436-2048.jpg)